2016-07-14 - AFRAIDGATE NEUTRINO EK FROM 5.2.72[.]236 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-14-Afraidgate-Neutrino-EK-sends-Locky-ransomware-4-pcaps.zip 1.3 MB (1,305,786 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-sends-Locky-ransomware-example-1-of-4.pcap (350,674 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-sends-Locky-ransomware-example-2-of-4.pcap (313,210 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-sends-Locky-ransomware-example-3-of-4.pcap (353,909 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-sends-Locky-ransomware-example-4-of-4.pcap (375,592 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-and-Locky-ransomware-fiiles.zip 1.2 MB (1,183,485 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-1-of-4.swf (82,629 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-2-of-4.swf (82,724 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-3-of-4.swf (82,724 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-4-of-4.swf (82,724 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-landing-page-example-1-of-4.txt (2,233 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-landing-page-example-2-of-4.txt (2,221 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-landing-page-example-3-of-4.txt (2,233 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-landing-page-example-4-of-4.txt (2,295 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-1-of-4.exe (24,9346 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-2-of-4.exe (24,9346 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-3-of-4.exe (24,9346 bytes)
- 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-4-of-4.exe (24,9346 bytes)
- 2016-07-14-Locky-ransomware-decrypt-instructions.bmp (3,721,466 bytes)
- 2016-07-14-Locky-ransomware-decrypt-instructions.html (10,112 bytes)
NOTES:
- Background on the Afraidgate campaign can be found here.
- Looks like Afraidgate has switched back to sending Locky ransomware as its payload, at least for now.
TRAFFIC

Shown above: Traffic from the first pcap filtered in Wireshark.
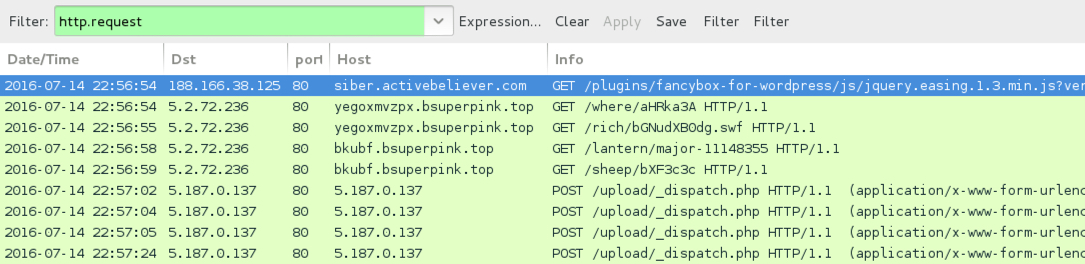
Shown above: Traffic from the second pcap filtered in Wireshark.

Shown above: Traffic from the third pcap filtered in Wireshark.

Shown above: Traffic from the 4th pcap filtered in Wireshark.
AFRAIDGATE REDIRECTS:
- 188.166.38[.]125 port 80 - siber.activebeliever[.]com - GET /plugins/fancybox-for-wordpress/js/jquery.easing.1.3.min.js?ver=1.3
- 188.166.38[.]125 port 80 - zine.polatoglumimarlik[.]com - GET /scripts/jquery.sliderkit.1.9.2.pack.js
- 188.166.38[.]125 port 80 - zine.polatoglumimarlik[.]com - GET /html5shiv.js
- 188.166.38[.]125 port 80 - zine.polatoglumimarlik[.]com - GET /to_top.js
NEUTRINO EK DOMAINS:
- 5.2.72[.]236 port 80 - avukytj.oautumnyellow[.]top
- 5.2.72[.]236 port 80 - azbepfasz.yintored[.]top
- 5.2.72[.]236 port 80 - bkubf.bsuperpink[.]top
- 5.2.72[.]236 port 80 - mxoug.yintored[.]top
- 5.2.72[.]236 port 80 - yegoxmvzpx.bsuperpink[.]top
POST-INFECTION TRAFFIC FROM THE LOCKY RANSOMWARE:
- 5.187.0[.]137 port 80 - 5.187.0[.]137 - POST /upload/_dispatch.php
- 77.222.54[.]202 port 80 - 77.222.54[.]202 - POST /upload/_dispatch.php
- 185.5.250[.]135 port 80 - 185.5.250[.]135 - POST /upload/_dispatch.php
- 185.118.66[.]83 port 80 - 185.118.66[.]83 - POST /upload/_dispatch.php
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- mphtadhci5mrdlju[.]tor2web[.]org
- mphtadhci5mrdlju[.]onion[.]to
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: aba7ef7d8b6eb54945bebda597b74a2f40c7e73380f4f485e4a5bc7d6da452be
File name: 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-1-of-4.swf
- SHA256 hash: 60a0537e7dfedbbf781b912dfe77f7aa804da54453cd58cb2130a750520c9d35
File name: 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-2-of-4.swf
- SHA256 hash: 117d41a97b7f170233edf66ff04a35e948f3dd3eaad53a548745fe4c32aff816
File name: 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-3-of-4.swf
- SHA256 hash: f2d28ef0c4ce015ef3d9943d60405565323cbc2261904b4bb250cc68dd3e92ad
File name: 2016-07-14-Afraidgate-Neutrino-EK-flash-exploit-example-4-of-4.swf
PAYLOADS:
- SHA256 hash: c42c9b2ab7f8f4a0f3c3554f199bf62a75382447c98b7dc430e33a616e60ce65
File name: 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-1-of-4.exe
- SHA256 hash: 844555caf160300f82e2bd08a3ee84aac093f40f7223177ef89f1f2bb55761cc
File name: 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-2-of-4.exe
File name: 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-3-of-4.exe
File name: 2016-07-14-Afraidgate-Neutrino-EK-payload-Locky-ransomware-example-4-of-4.exe
IMAGES
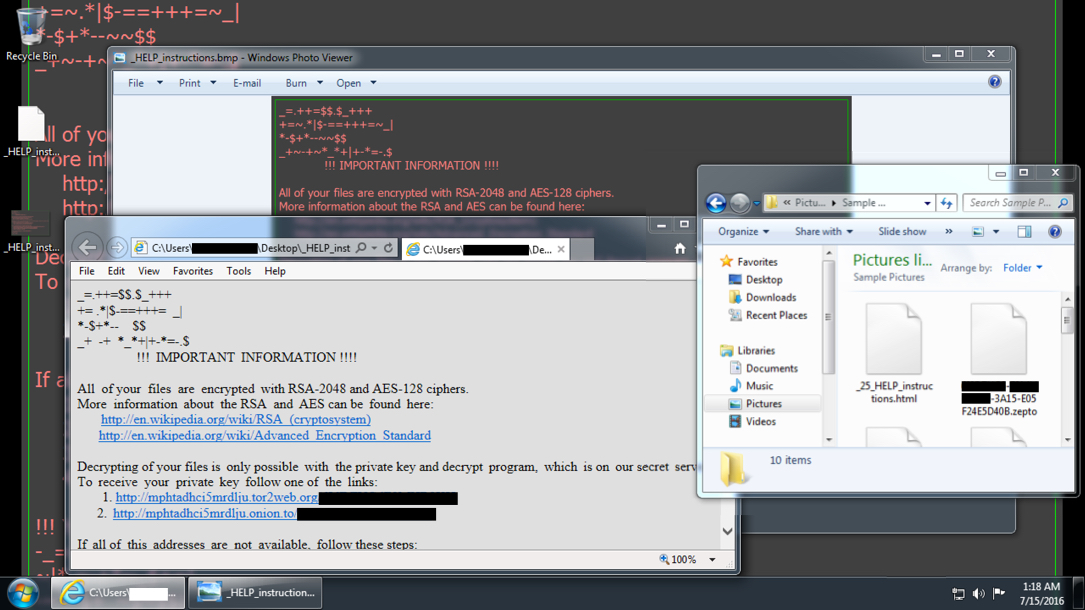
Shown above: Infecting a Windows host with one of the Locky ransomware samples.
Click here to return to the main page.
