2016-07-21 - EMAILS PUSHING LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- I grabbed 10 examples of emails in pushing Locky ransomware on Thursday 2016-07-21.
- This time, the .js files did not download Locky ransomware from another site.
- Instead, these Locky ransomware samples were encoded as a base64 string in the .js files (see below).
ASSOCIATED FILES:
- 2016-07-21-Locky-ransomware-files.zip 5.9 MB (5,863,819 bytes)
- 2016-07-21-Locky-ransomware-email-tracker.csv (2,196 bytes)
- artifacts-from-infected-hosts / _0_HELP_instructions.html (8,763 bytes)
- artifacts-from-infected-hosts / _HELP_instructions.bmp (3,721,466 bytes)
- artifacts-from-infected-hosts / b15RNbhknZ.exe (180,858 bytes)
- artifacts-from-infected-hosts / jKbRCDxgE4hek.exe (180,859 bytes)
- artifacts-from-infected-hosts / l7AvRs5QJ3W7.exe (180,865 bytes)
- artifacts-from-infected-hosts / n3C1ILVOh.exe (180,861 bytes)
- artifacts-from-infected-hosts / ratJyJK4x.exe (181,388 bytes)
- artifacts-from-infected-hosts / syDWZqJJQl13HdH.exe (181,393 bytes)
- artifacts-from-infected-hosts / tKnJ5B7b9.exe (180,865 bytes)
- artifacts-from-infected-hosts / vihrdPXoQFaGC.exe (181,385 bytes)
- artifacts-from-infected-hosts / wfbBHGRBGzuOf.exe (181,394 bytes)
- artifacts-from-infected-hosts / Z7m4oNwPldS.exe (181,386 bytes)
- attachments / 35B1E9_linda.zip (143,190 bytes)
- attachments / alan_AFDE3.zip (141,383 bytes)
- attachments / B08422_will.zip (140,920 bytes)
- attachments / daniel_45914.zip (142,634 bytes)
- attachments / jake_676517D.zip (142,226 bytes)
- attachments / jane_63263.zip (142,185 bytes)
- attachments / laura_75351.zip (142,224 bytes)
- attachments / rhonda_330F92.zip (142,859 bytes)
- attachments / ronaldo_065.zip (142,175 bytes)
- attachments / susan_E1036.zip (142,607 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2118-UTC.eml (193,373 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2134-UTC.eml (195,022 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2139-UTC.eml (194,409 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2144-UTC.eml (194,487 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2146-UTC.eml (195,088 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2159-UTC.eml (194,450 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2202-UTC.eml (192,765 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2209-UTC.eml (195,362 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2217-UTC.eml (194,582 bytes)
- emails / 2016-07-21-Locky-ransomware-email-2226-UTC.eml (195,854 bytes)
- extracted-files / INV000 28ba.js (246,873 bytes)
- extracted-files / INV000 3648.js (246,981 bytes)
- extracted-files / INV000 4214.js (245,950 bytes)
- extracted-files / INV000 5cbd.js (246,079 bytes)
- extracted-files / INV000 6956.js (247,021 bytes)
- extracted-files / INV000 701.js (246,793 bytes)
- extracted-files / INV000 8159.js (246,315 bytes)
- extracted-files / INV000 a1e3.js (246,258 bytes)
- extracted-files / INV000 c79a.js (246,375 bytes)
- extracted-files / INV000 da0.js (246,775 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2134-UTC-email.pcap (19,173 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2139-UTC-email.pcap (20,897 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2144-UTC-email.pcap (19,734 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2146-UTC-email.pcap (20,576 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2159-UTC-email.pcap (18,980 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2202-UTC-email.pcap (18,167 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2209-UTC-email.pcap (20,681 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2217-UTC-email.pcap (21,038 bytes)
- pcaps / 2016-07-21-Locky-ransomware-infection-traffic-from-2226-UTC-email.pcap (19,606 bytes)
EMAILS
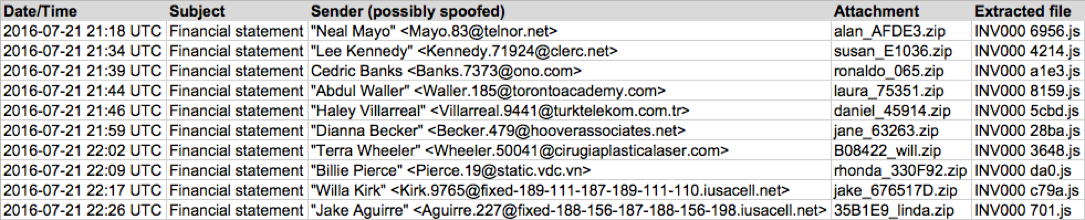
Shown above: Email data from the spreadsheet (part 1 of 2).
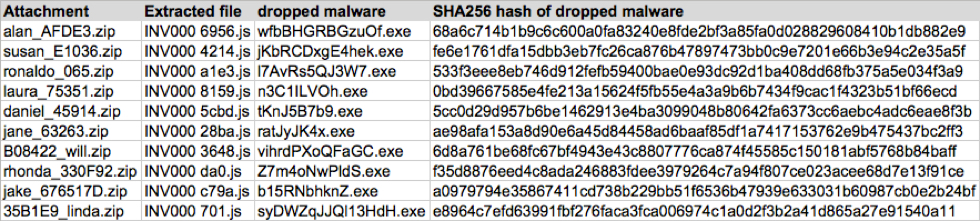
Shown above: Email data from the spreadsheet (part 2 of 2).
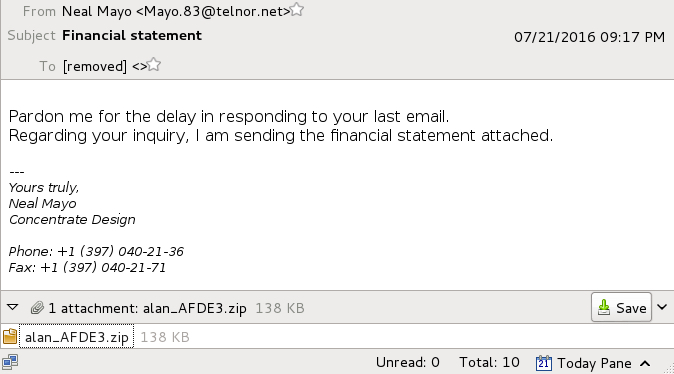
Shown above: Text of the emails (example 1 of 4).
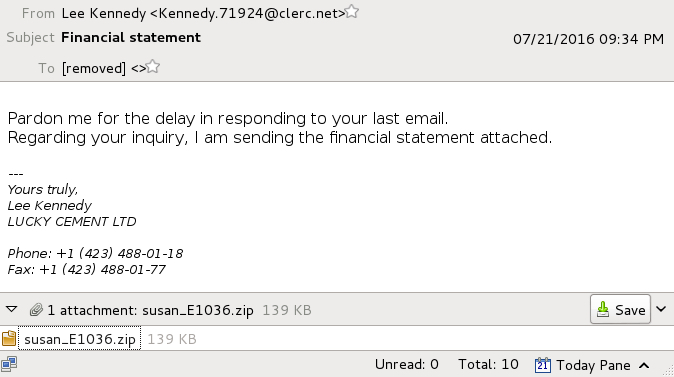
Shown above: Text of the emails (example 2 of 4).
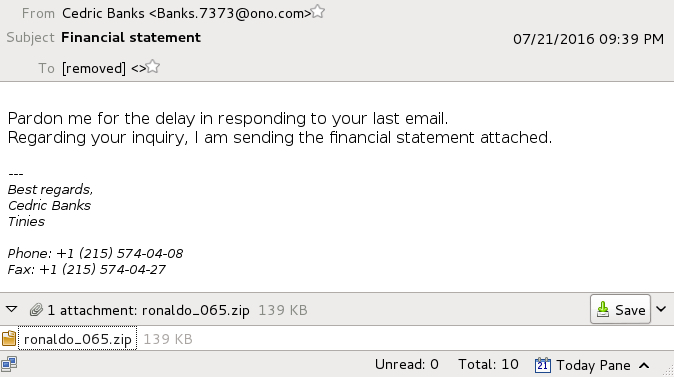
Shown above: Text of the emails (example 3 of 4).
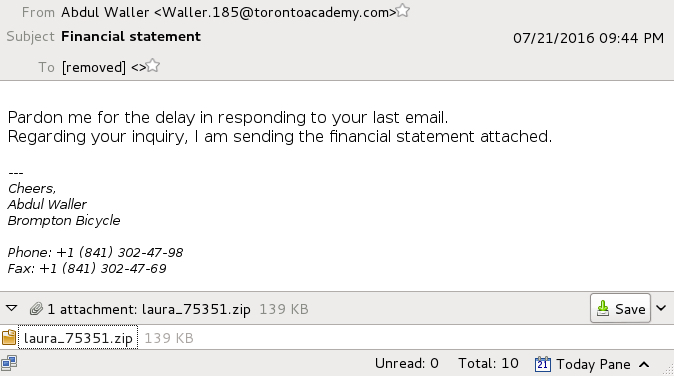
Shown above: Text of the emails (example 4 of 4).
ATTACHMENTS
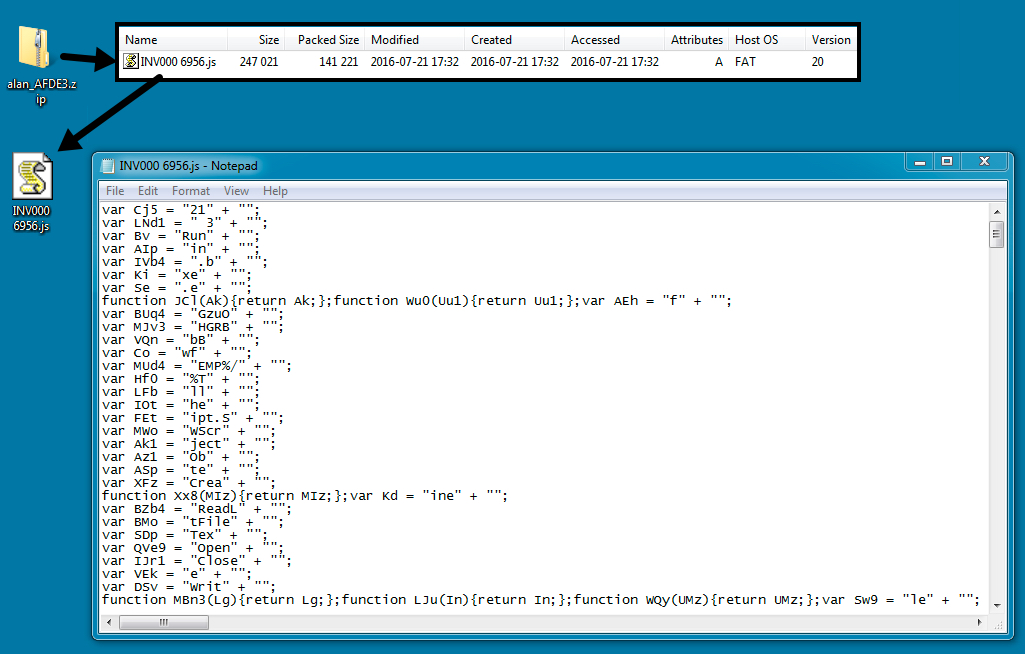
Shown above: An example of the email attachments.
If you scroll down in the .js file using a text editor, you'll find a large base64 string that represents the Locky ransomware binary. For these files, there was no obfuscation, and you can use an online tool to convert the string into the binary.
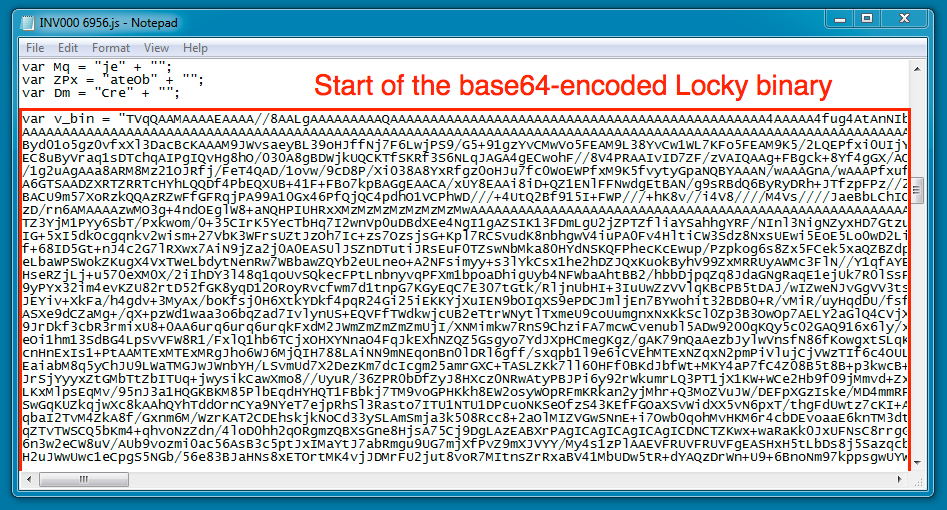
Shown above: Start of the Locky ransomware binary stored as a base64 string the the .js file.
TRAFFIC
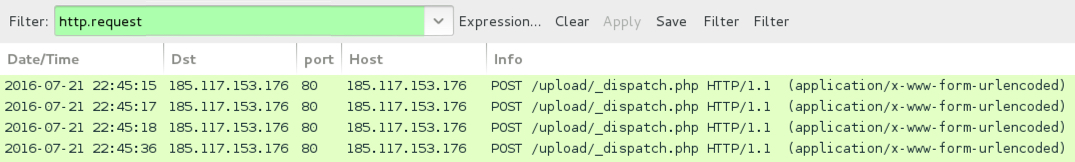
Shown above: An example of Locky ransomware post-infection traffic using one of the email attachments.
ASSOCIATED DOMAINS:
- 77.222.54[.]202 port 80 - 77.222.54[.]202 - POST /upload/_dispatch.php
- 176.111.63[.]51 port 80 - 176.111.63[.]51 - POST /upload/_dispatch.php
- 185.117.153[.]176 port 80 - 185.117.153[.]176 - POST /upload/_dispatch.php
- 194.1.236[.]126 port 80 - 194.1.236[.]126 - POST /upload/_dispatch.php
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- mphtadhci5mrdlju[.]tor2web[.]org
- mphtadhci5mrdlju[.]onion[.]to
- NOTE: These are the same post-infection domains found in a previous wave of emails pushing Locky ransomware I blogged about on 2016-07-12.
IMAGES
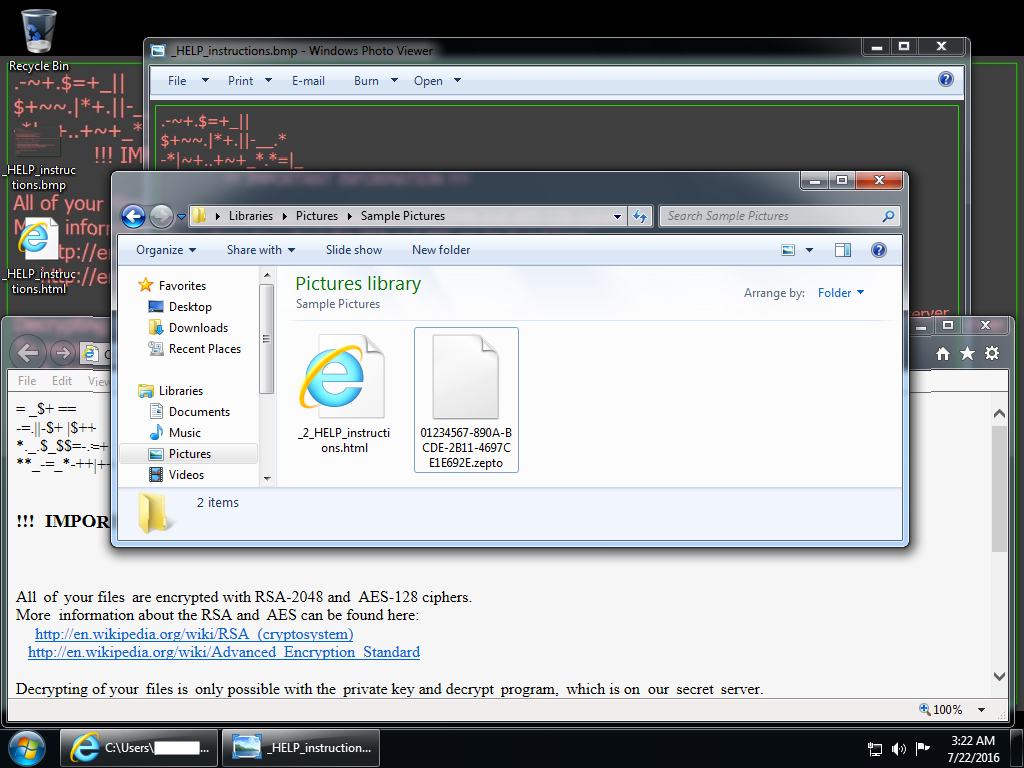
Shown above: Infected Windows desktop from one of the emails.
Click here to return to the main page.
