2016-09-12 - ZEPTO VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-12-Locky-ransomware-infection-traffic-3-pcaps.zip 2.2 MB (2,217,311 bytes)
- 2016-09-12-Locky-ransomware-infection-traffic-first-example.pcap (1,255,591 bytes)
- 2016-09-12-Locky-ransomware-infection-traffic-second-example.pcap (1,254,549 bytes)
- 2016-09-12-Locky-ransomware-infection-traffic-third-example.pcap (166,055 bytes)
- 2016-09-12-Locky-ransomware-data.zip 871.0 kB (871,013 bytes)
- 2016-09-12-Locky-ransomware-email-tracker.csv (1,578 bytes)
- files-from-infected-host / 2016-09-12-Locky-ramsomware-downloader-caused-by-wsf-file.exe (240,944 bytes)
- files-from-infected-host / 2016-09-12-Locky-ramsomware_HELP_instructions.bmp (3,578,902 bytes)
- files-from-infected-host / 2016-09-12-Locky-ramsomware_HELP_instructions.html (8,973 bytes)
- files-from-infected-host / 2016-09-12-Locky-ramsomware-caused-by-js-file.dll (134,779 bytes)
- files-from-infected-host / 2016-09-12-Locky-ramsomware-caused-by-wsf-file.dll (159,744 bytes)
- attachments / 3911fcc1e51.zip (22,780 bytes)
- attachments / 5a80587d100.zip (22,740 bytes)
- attachments / IG_20160830_9_9_01_Pro.zip (8,649 bytes)
- attachments / PH_20160830_3_14_53_Pro.zip (8,621 bytes)
- attachments / WP_20160830_11_61_3_Pro.zip (8,653 bytes)
- attachments / WP_20160830_1_63_5_Pro.zip (8,621 bytes)
- attachments / db475b3e2e.zip (22,416 bytes)
- attachments / fb1fe573a08d.zip (22,636 bytes)
- attachments / pm55D27DB7.zip (8,640 bytes)
- attachments / pm892.zip (8,276 bytes)
- attachments / pmBF2EE7B7.zip (8,640 bytes)
- attachments / pmE93.zip (8,272 bytes)
- emails / 2016-09-12-0931-UTC-malspam-attached-invoice.eml (12,939 bytes)
- emails / 2016-09-12-0933-UTC-malspam-attached-invoice.eml (12,928 bytes)
- emails / 2016-09-12-1232-UTC-malspam-attached-invoice.eml (13,430 bytes)
- emails / 2016-09-12-1235-UTC-malspam-attached-invoice.eml (13,433 bytes)
- emails / 2016-09-12-1320-UTC-malspam-Photo.eml (12,712 bytes)
- emails / 2016-09-12-1320-UTC-malspam-Photos.eml (12,758 bytes)
- emails / 2016-09-12-1321-UTC-malspam-Image.eml (12,765 bytes)
- emails / 2016-09-12-1357-UTC-malspam-budget-report.eml (31,588 bytes)
- emails / 2016-09-12-1401-UTC-malspam-Picture.eml (12,795 bytes)
- emails / 2016-09-12-1404-UTC-malspam-budget-report.eml (31,789 bytes)
- emails / 2016-09-12-1419-UTC-malspam-budget-report.eml (31,773 bytes)
- emails / 2016-09-12-1420-UTC-malspam-budget-report.eml (31,294 bytes)
- extracted-files / 00HwYy2rv25.wsf (34,276 bytes)
- extracted-files / 03agU52Nk02.wsf (34,293 bytes)
- extracted-files / 05omKt2S13.wsf (35,947 bytes)
- extracted-files / 14YQg739.wsf (35,976 bytes)
- extracted-files / 22P5R06.wsf (35,984 bytes)
- extracted-files / 28SShQBR04.wsf (35,935 bytes)
- extracted-files / 68BE96D1 Budget_report_xls.js (133,582 bytes)
- extracted-files / 863AEEA3 Budget_report_xls.js (133,324 bytes)
- extracted-files / AD3F36C4 Budget_report_xls.js (132,185 bytes)
- extracted-files / FA6F211A Budget_report_xls.js (133,341 bytes)
NOTES:
- It's been so long since I looked into Locky ransomware, I didn't realize it's now a malicious DLL instead of an EXE.
- Lawrence Abrams from BleepingComputer first reported about Locky ransomware DLLs last month on 2016-08-26 ( link ).
- Today I saw the following patterns during infection traffic when I looked into Locky ransomware:
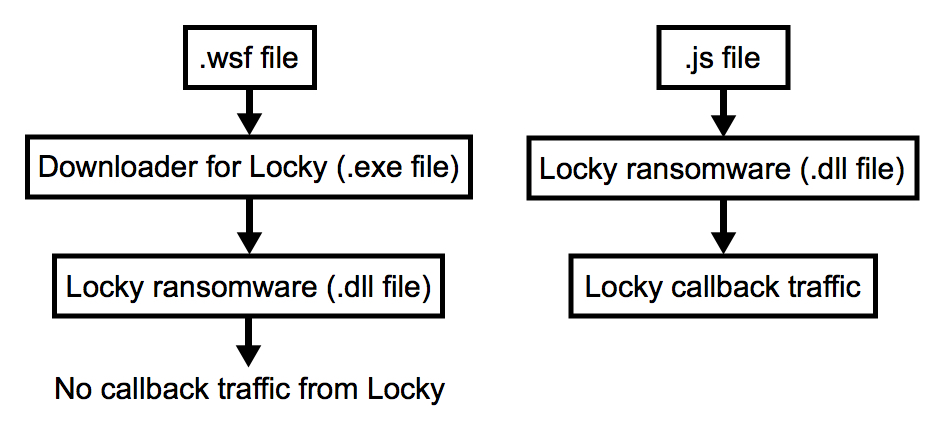
Shown above: Flow chart for two different examples of Locky ransomware infections from today's emails.
EMAILS
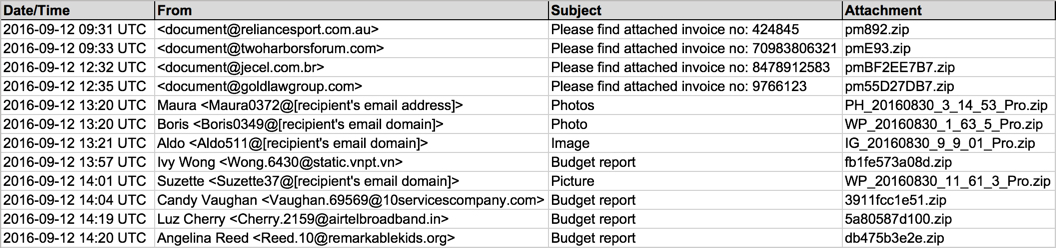
Shown above: Email data from the spreadsheet (part 1 of 2).
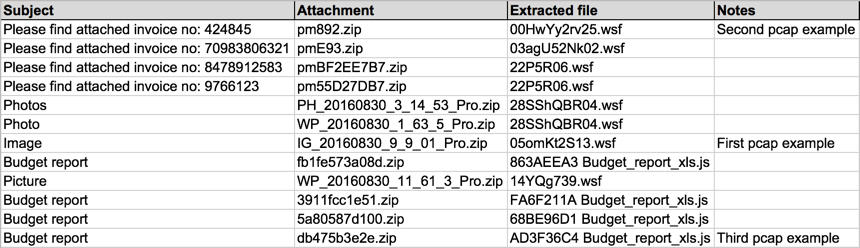
Shown above: Email data from the spreadsheet (part 2 of 2).
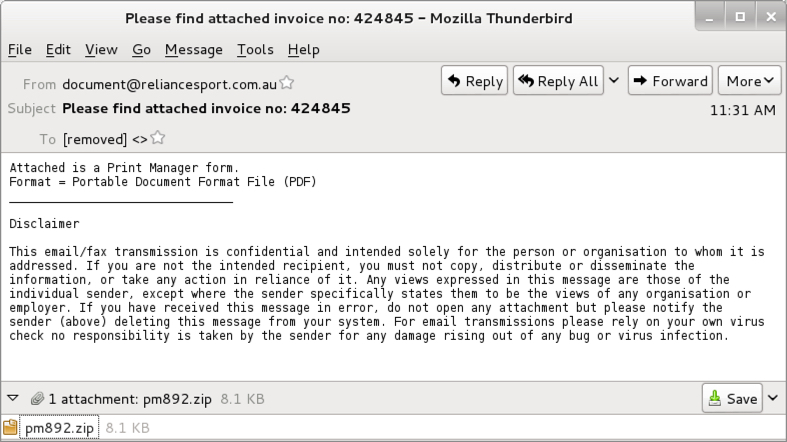
Shown above: Text of the emails (example 1 of 3).
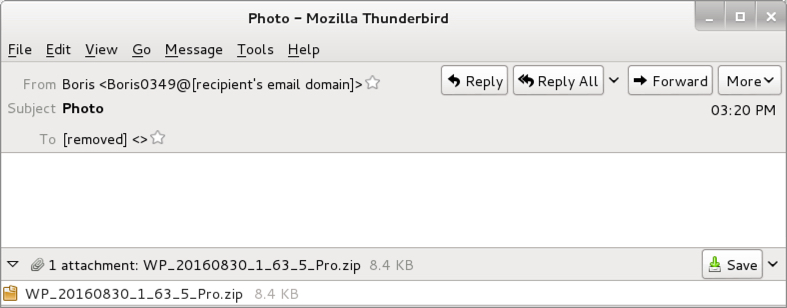
Shown above: Text of the emails (example 2 of 3).
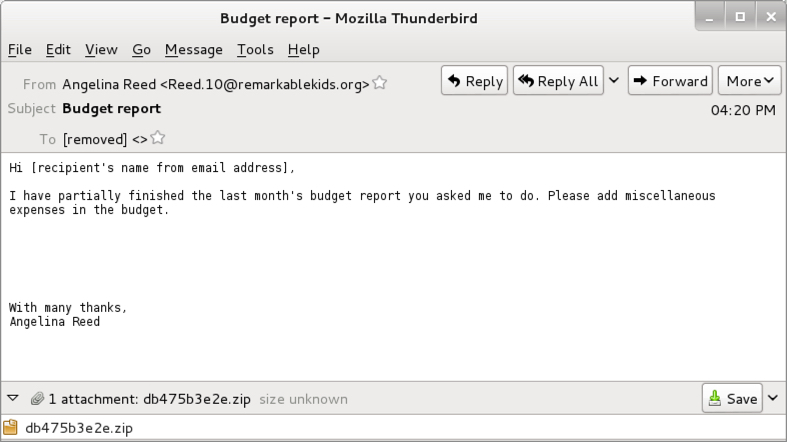
Shown above: Text of the emails (example 3 of 3).
FROM ADDRESSES / SUBJECT LINES:
- <document@reliancesport[.]com[.]au> - Subject: Please find attached invoice no: 424845
- <document@twoharborsforum[.]com> - Subject: Please find attached invoice no: 70983806321
- <document@jecel[.]com[.]br> - Subject: Please find attached invoice no: 8478912583
- <document@goldlawgroup[.]com> - Subject: Please find attached invoice no: 9766123
- "Maura" <Maura0372@[recipient's email address]> - Subject: Photos
- "Boris" <Boris0349@[recipient's email domain]> - Subject: Photo
- "Aldo" <Aldo511@[recipient's email domain]> - Subject: Image
- "Suzette" <Suzette37@[recipient's email domain]> - Subject: Picture
- "Ivy Wong" <Wong.6430@static.vnpt[.]vn> - Subject: Budget report
- "Candy Vaughan" <Vaughan.69569@10servicescompany[.]com> - Subject: Budget report
- "Luz Cherry" <Cherry.2159@airtelbroadband[.]in> - Subject: Budget report
- "Angelina Reed" <Reed.10@remarkablekids[.]org> - Subject: Budget report
TRAFFIC
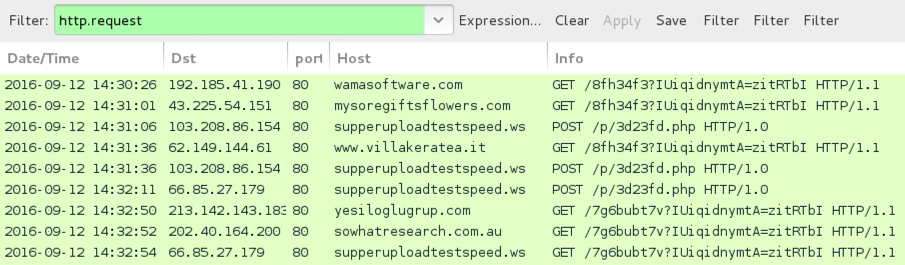
Shown above: Traffic from the first example (caused by .wsf file), filtered in Wireshark.
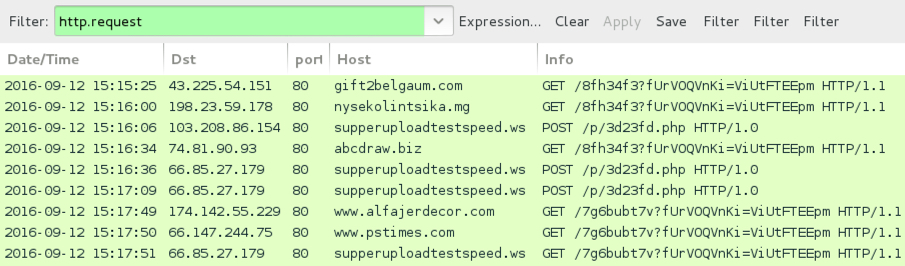
Shown above: Traffic from the first example (also caused by .wsf file), filtered in Wireshark.
Shown above: Traffic from the first example (caused by .js file), filtered in Wireshark.
FIRST PCAP:
- 192.185.41[.]190 port 80 - wamasoftware[.]com - GET /8fh34f3?IUiqidnymtA=zitRTbI - Request for Locky ransomware downloader caused .wsf file
- 43.225.54[.]151 port 80 - mysoregiftsflowers[.]com - GET /8fh34f3?IUiqidnymtA=zitRTbI - Request for Locky ransomware downloader caused .wsf file
- 62.149.144[.]61 port 80 - www.villakeratea[.]it - GET /8fh34f3?IUiqidnymtA=zitRTbI - Request for Locky ransomware downloader caused .wsf file
- 103.208.86[.]154 port 80 - supperuploadtestspeed[.]ws - POST /p/3d23fd.php HTTP/1.0 - Post-infection callback by Locky ransomware downloader
- 66.85.27[.]179 port 80 - supperuploadtestspeed[.]ws - POST /p/3d23fd.php HTTP/1.0 - Post-infection callback by Locky ransomware downloader
- 213.142.143[.]183 port 80 - yesiloglugrup[.]com - GET /7g6bubt7v?IUiqidnymtA=zitRTbI - Request for Locky ransomware by the downloader
- 202.40.164[.]200 port 80 - sowhatresearch[.]com[.]au - GET /7g6bubt7v?IUiqidnymtA=zitRTbI - Request for Locky ransomware by the downloader
- 66.85.27[.]179 port 80 - supperuploadtestspeed[.]ws - GET /7g6bubt7v?IUiqidnymtA=zitRTbI - Request for Locky ransomware by the downloader
SECOND PCAP:
- 43.225.54[.]151 port 80 - gift2belgaum[.]com - GET /8fh34f3?fUrVOQVnKi=ViUtFTEEpm - Request for Locky ransomware downloader caused .wsf file
- 198.23.59[.]178 port 80 - nysekolintsika[.]mg - GET /8fh34f3?fUrVOQVnKi=ViUtFTEEpm - Request for Locky ransomware downloader caused .wsf file
- 74.81.90[.]93 port 80 - abcdraw[.]biz - GET /8fh34f3?fUrVOQVnKi=ViUtFTEEpm - Request for Locky ransomware downloader caused .wsf file
- 103.208.86[.]154 port 80 - supperuploadtestspeed[.]ws - POST /p/3d23fd.php HTTP/1.0 - Post-infection callback by Locky ransomware downloader
- 66.85.27[.]179 port 80 - supperuploadtestspeed[.]ws - POST /p/3d23fd.php HTTP/1.0 - Post-infection callback by Locky ransomware downloader
- 174.142.55[.]229 port 80 - www.alfajerdecor[.]com - GET /7g6bubt7v?fUrVOQVnKi=ViUtFTEEpm - Request for Locky ransomware by the downloader
- 66.147.244[.]75 port 80 - www.pstimes[.]com - GET /7g6bubt7v?fUrVOQVnKi=ViUtFTEEpm - Request for Locky ransomware by the downloader
- 66.85.27[.]179 port 80 - supperuploadtestspeed[.]ws - GET /7g6bubt7v?fUrVOQVnKi=ViUtFTEEpm - Request for Locky ransomware by the downloader
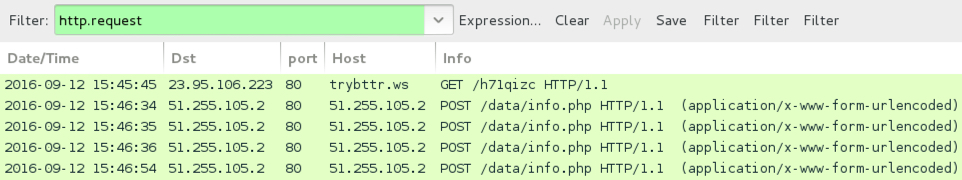
THIRD PCAP:
- 23.95.106[.]223 port 80 - trybttr[.]ws - GET /h71qizc - Request for Locky ransomware caused by .js file
- 51.255.105[.]2 port 80 - 51.255.105[.]2 - POST /data/info.php - Post-infection callback by the Locky ransomware
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- 5n7y4yihirccftc5[.]tor2web[.]org
- 5n7y4yihirccftc5[.]onion[.]to
FILE HASHES
ARTIFACTS FROM THE INFECTED HOSTS:
- SHA256 hash: b88e84d9c7c407c7bad40777e87413628d8786af643d1581aa9aa82209751fd7
File name: 2016-09-12-Locky-ransomware-downloader-caused-by-wsf-file.exe
- SHA256 hash: bbfb4c0bbae915cc719325970c0cc9e9bf144d96043b9cc7c18a328a2e69a2c5
File name: 2016-09-12-Locky-ramsoware-caused-by-wsf-file.dll
- SHA256 hash: 76438fc9c86c57bf0fb8028a3a6290cfce8b305e21fca5ae15feaf2e73681a27
File name: 2016-09-12-Locky-ramsoware-caused-by-js-file.dll
IMAGES
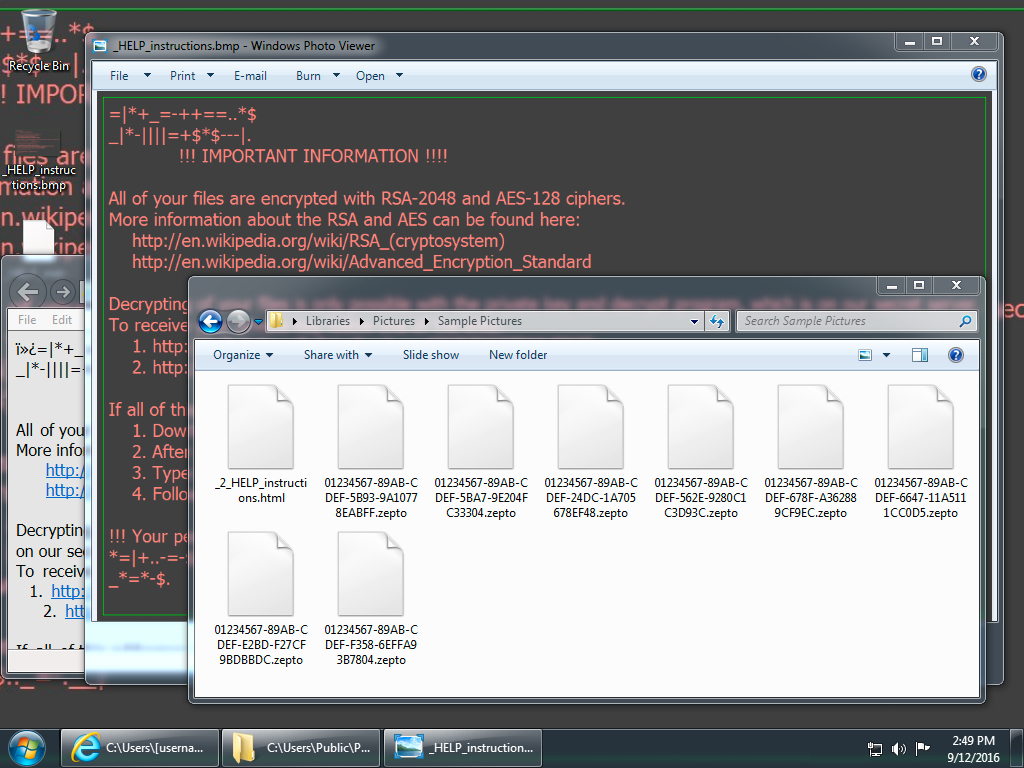
Shown above: Infected Windows desktop from one of the .wsf emails.

Shown above: Going to the decrypt instructions using a Tor browser.
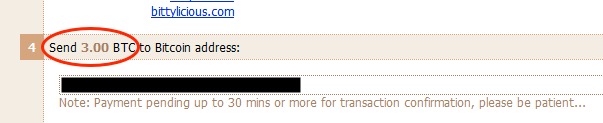
Shown above: Looks like my Locky ransomware sample (caused by the .wsf file) wants 3 bitcoins for ransom.
Click here to return to the main page.
