2016-10-24 - ".SHIT" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-24-Locky-ransomware-files.zip 2.1 MB (2,095,592 bytes)
- 2016-10-24-Locky-email-tracker.csv (1,965 bytes)
- Locky-ransomware-files-from-infected-hosts / KiOBUGxRvH1.dll (274,432 bytes)
- Locky-ransomware-files-from-infected-hosts / LjXiDmd1.dll (274,432 bytes)
- Locky-ransomware-files-from-infected-hosts / UrhgVhR1.dll (274,432 bytes)
- Locky-ransomware-files-from-infected-hosts / XebQkujR1.dll (274,432 bytes)
- Locky-ransomware-files-from-infected-hosts / YnDGHb1.dll (274,432 bytes)
- Locky-ransomware-files-from-infected-hosts / _WHAT_is.bmp (3,578,902 bytes)
- Locky-ransomware-files-from-infected-hosts / _WHAT_is.html (9,976 bytes)
- Locky-ransomware-files-from-infected-hosts / mIbqzP1.dll (274,432 bytes)
- attachments / Receipt 017-13644.zip (8,018 bytes)
- attachments / Receipt 15075-053619.zip (7,400 bytes)
- attachments / Receipt 46-2734.zip (7,438 bytes)
- attachments / Receipt 4845-83761.zip (7,977 bytes)
- attachments / Receipt 63-81684.zip (7,378 bytes)
- attachments / Receipt 77077-14409.zip (7,979 bytes)
- emails / 2016-10-24-email-1314-UTC.eml (10,899 bytes)
- emails / 2016-10-24-email-1322-UTC.eml (10,841 bytes)
- emails / 2016-10-24-email-1335-UTC.eml (10,862 bytes)
- emails / 2016-10-24-email-1356-UTC.eml (11,669 bytes)
- emails / 2016-10-24-email-1421-UTC.eml (11,686 bytes)
- emails / 2016-10-24-email-1434-UTC.eml (11,631 bytes)
- extracted-files / Receipt 15110-632446.wsf (29,186 bytes)
- extracted-files / Receipt 34469-690103.wsf (29,447 bytes)
- extracted-files / Receipt 43284-144137.hta (26,180 bytes)
- extracted-files / Receipt 53744-762732.wsf (31,424 bytes)
- extracted-files / Receipt 72645-990319.hta (27,938 bytes)
- extracted-files / Receipt 84603-492538.hta (25,635 bytes)
- pcaps / 2016-10-24-traffic-from-1314-UTC-malspam.pcap (120,026 bytes)
- pcaps / 2016-10-24-traffic-from-1322-UTC-malspam.pcap (184,925 bytes)
- pcaps / 2016-10-24-traffic-from-1325-UTC-malspam.pcap (209,376 bytes)
- pcaps / 2016-10-24-traffic-from-1358-UTC-malspam.pcap (177,510 bytes)
- pcaps / 2016-10-24-traffic-from-1421-UTC-malspam.pcap (262,724 bytes)
- pcaps / 2016-10-24-traffic-from-1434-UTC-malspam.pcap (160,647 bytes)
NOTES:
- This variant of Locky uses the file extension .shit for the encrypted files.
- That makes it suitable for all sorts of puns or jokes when reporting about it.
- My favorite so far is a BleepingComputer post titled: Locky ransomware's new .SHIT Extension shows that you can't polish a turd
EMAILS
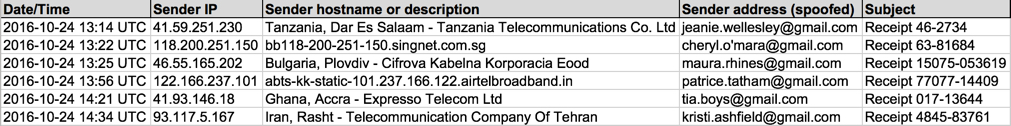
Shown above: Data from six emails pushing Locky ransomware (part 1 of 2).
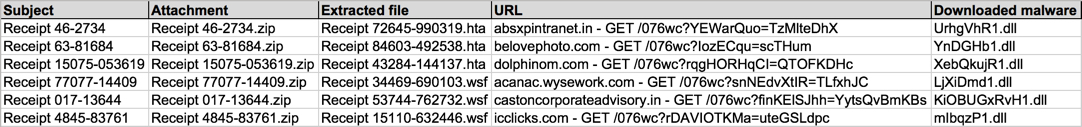
Shown above: ata from six emails pushing Locky ransomware (part 2 of 2).
TRAFFIC
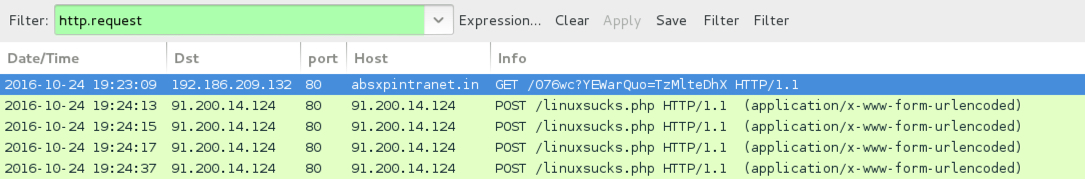
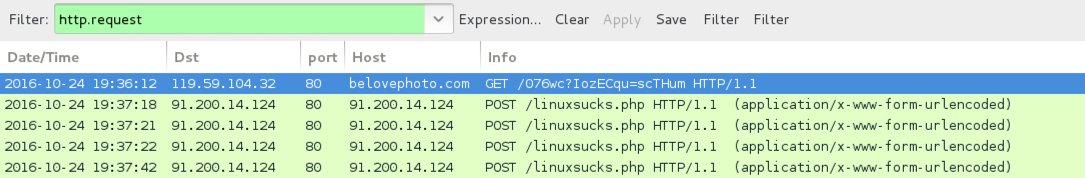
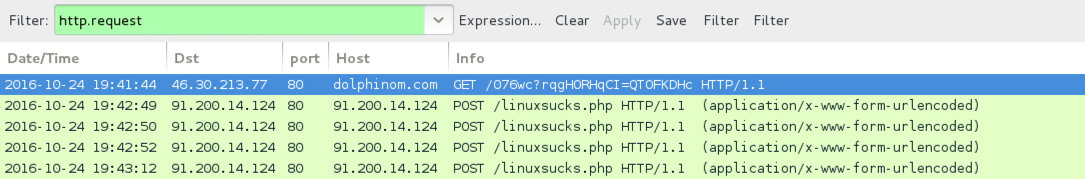
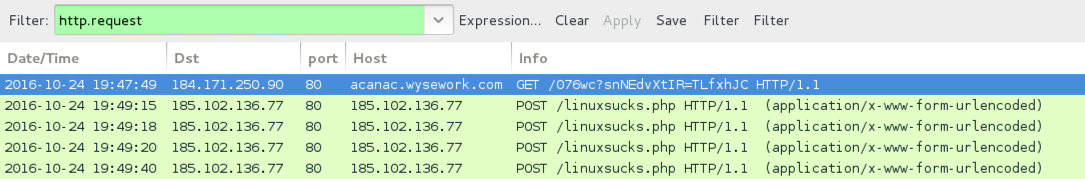
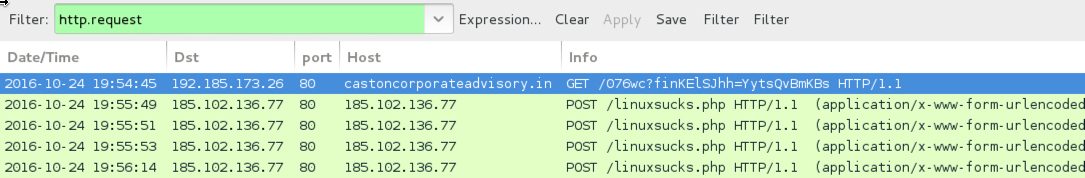
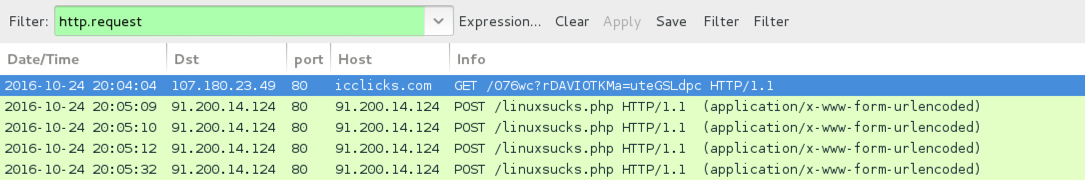
TRAFFIC FROM THE .HTA AND .WSF FILES (TO RETRIEVE THE LOCKY RANSOMWARE DLL):
- 192.186.209[.]132 port 80 - absxpintranet[.]in - GET /076wc?YEWarQuo=TzMlteDhX
- 119.59.104[.]32 port 80 - belovephoto[.]com - GET /076wc?IozECqu=scTHum
- 46.30.213[.]77 port 80 - dolphinom[.]com - GET /076wc?rqgHORHqCI=QTOFKDHc
- 184.171.250[.]90 port 80 - acanac.wysework[.]com - GET /076wc?snNEdvXtIR=TLfxhJC
- 192.185.173[.]26 port 80 - castoncorporateadvisory[.]in - GET /076wc?finKElSJhh=YytsQvBmKBs
- 107.180.23[.]49 port 80 - icclicks[.]com - GET /076wc?rDAVIOTKMa=uteGSLdpc
POST-INFECTION LOCKY RANSOMWARE CALLBACK TRAFFIC:
- 91.200.14[.]124 port 80 - 91.200.14[.]124 - POST /linuxsucks.php
- 185.102.136[.]77 port 80 - 185.102.136[.]77 - POST /linuxsucks.php
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- jhomitevd2abj3fk.tor2web[.]org
- jhomitevd2abj3fk[.]onion[.]to
FILE HASHES
LOCKY RANSOMWARE DLL:
- SHA256 hash: b54802e6f6430c75d0683140ef0529c6603418b4ef602d80e85aaa88fe730c79
File name: C:\Users\[username\AppData\Local\Temp\KiOBUGxRvH1.dll (and various other names for the DLL)
IMAGES
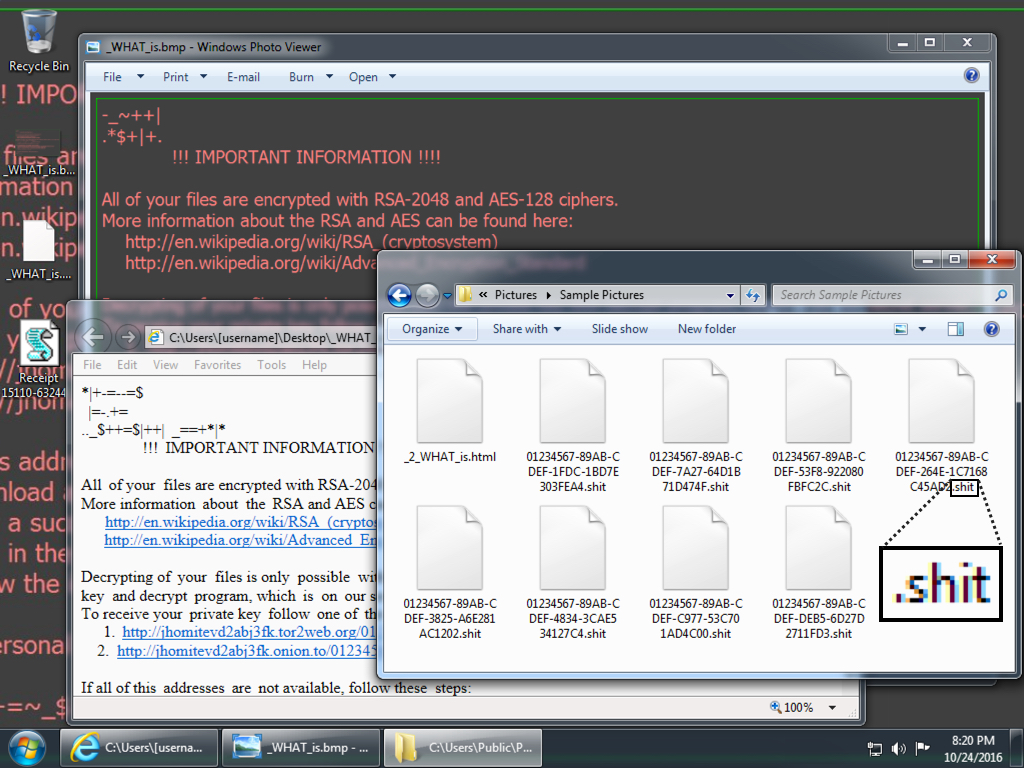
Shown above: Screen shot from an infected Windows desktop. Note the .shit file extension.
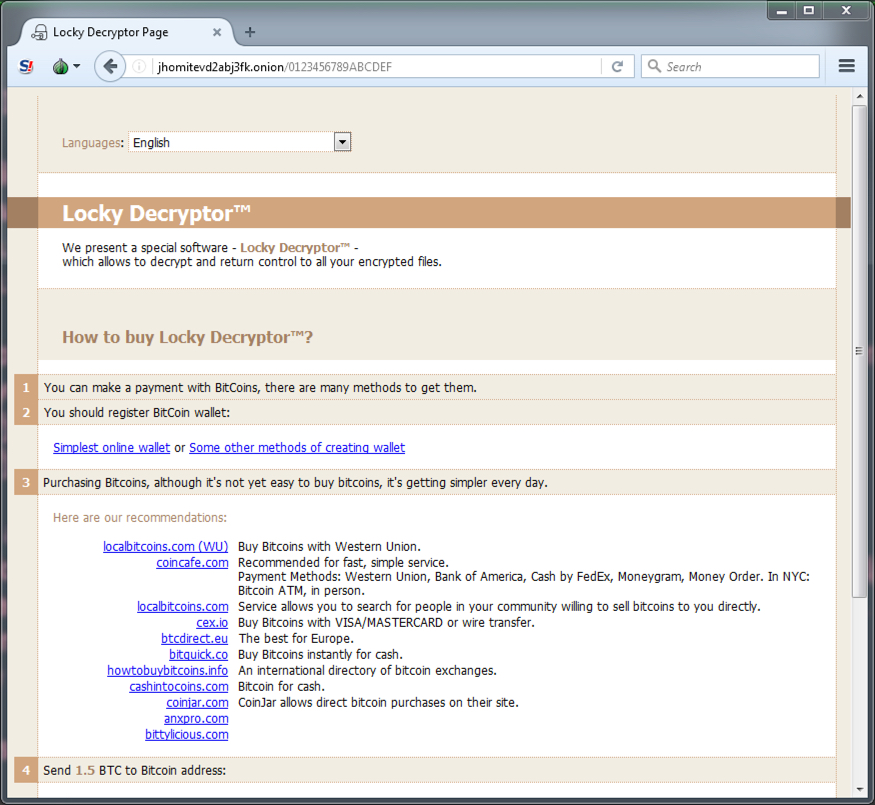
Shown above: Ransom payment is 1.5 bitcoin, just like most samples of the previous Locky ransomware variant I've seen.
Click here to return to the main page.
