2016-11-17 - RIG-E UPDATES PAYLOAD ENCRYPTION, SENDS CHIP RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-17-EITest-Rig-E-sends-CHIP-ransomware.pcap.zip 249.6 kB (249,581 bytes)
- 2016-11-17-EITest-Rig-E-sends-CHIP-ransomware.pcap (284,102 bytes)
- 2016-11-17-EITest-Rig-E-and-CHIP-ransomware-riles.zip 162.1 kB (162,066 bytes)
- 2016-11-17-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-11-17-Rig-E-flash-exploit.swf (10,636 bytes)
- 2016-11-17-Rig-E-landing-page.txt (3,418 bytes)
- 2016-11-17-Rig-E-payload-CHIP-ransomware.exe (223,744 bytes)
- 2016-11-17-cavallinomotorsport_com-with-injected-EITest-script.txt (18,804 bytes)
- 2016-11-17-CHIP_FILES.txt (790 bytes)
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary) The EITest campaign uses Rig standard to send CryptFile2 ransomware.
NOTES:
- Rig-related Flash exploit sizes dropped to around 10 kB to 11 kB today.
- Also today, it looks like Rig-E started using RC4 encryption for the payload just like Rig-V. Before today, Rig-E was using the older style XOR obfuscation on the payload.
- Rig-E still has the old style URL patterns in the traffic I'm seeing.
- With this new Rig-E, I had several crashes on Windows hosts using IE 10 or IE 11.
- I had to switch to an older Windows host using IE 8 to get a full infection cahin.
- Today's Rig-E payload is ransomware that uses .CHIP as the file extension for any encrypted files, which is why people (like me) are calling it CHIP ransomware.
- This ransomware seems to be a Filecoder variant (see the EmergingThreats alerts in the images section).
- You'll find a file named CHIP_FILES.txt in directories with any encrypted files. This file contains the decryption instructions.
- Someone has already posted initial information about CHIP ransomware on the Bleeping Computer forums earlier today (link).
Shown above: Chain of events for this infection.
TRAFFIC

Shown above: Injected script in a page from the compromised website.
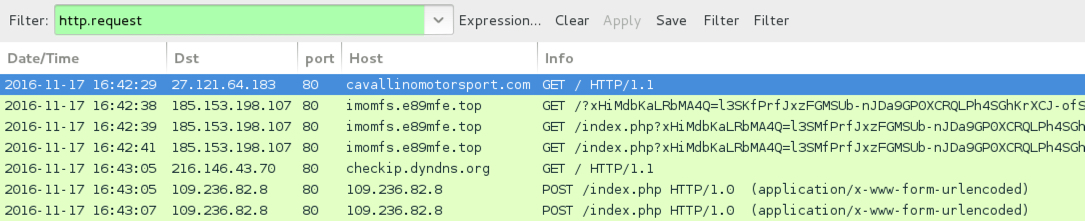
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- cavallinomotorsport[.]com - Compromised website
- 185.153.198[.]107 port 80 - imomfs.e89mfe[.]top - Rig-E (Empire Pack)
- checkip.dyndns[.]org - GET / [IP address check by the infected host]
- 109.236.82[.]8 port 80 - 109.236.82[.]8 - POST /index.php HTTP/1.0 [post-infection callback]
- mm6x57ri2coivya6[.]onion - Tor site for the decryption instructions
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: eeeea7799e64e233c189a5e3d36c40a1709bef14fc47ae083787cbda69b57b47
File name: 2016-11-17-Rig-E-flash-exploit.swf (10,636 bytes)
PAYLOADS (CHIP RANSOMWARE):
- SHA256 hash: aee03626b83a88b71b06899116cb7ce4b8092365103d69792b0c2d7153f24cb1
File name: C:\Users\[Username]\AppData\Local\Temp\rad46480.tmp.exe (223,744 bytes)
IMAGES
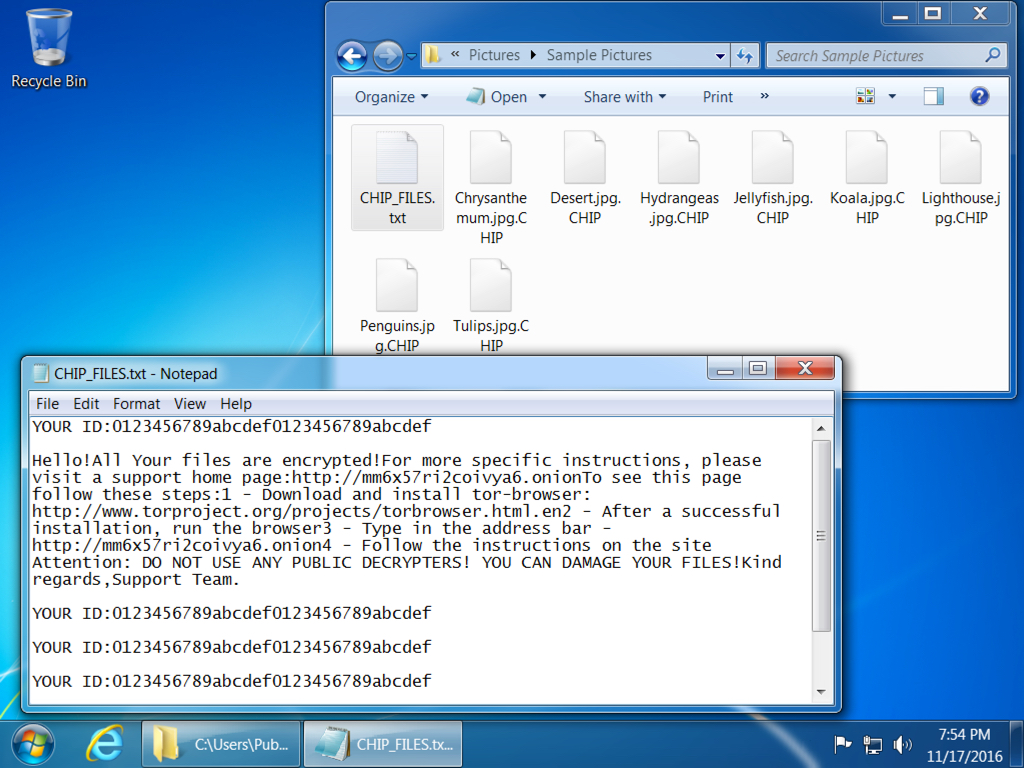
Shown above: An infected Windows host with a folder showing the encrypted files and CHIP_FILES.txt decryption instructions.
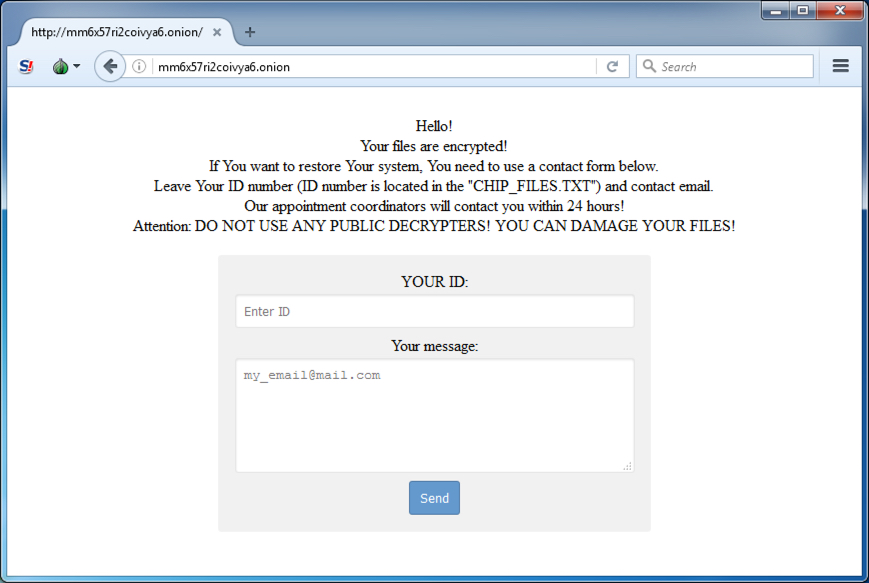
Shown above: Viewing the decryption instructions in a Tor browser.
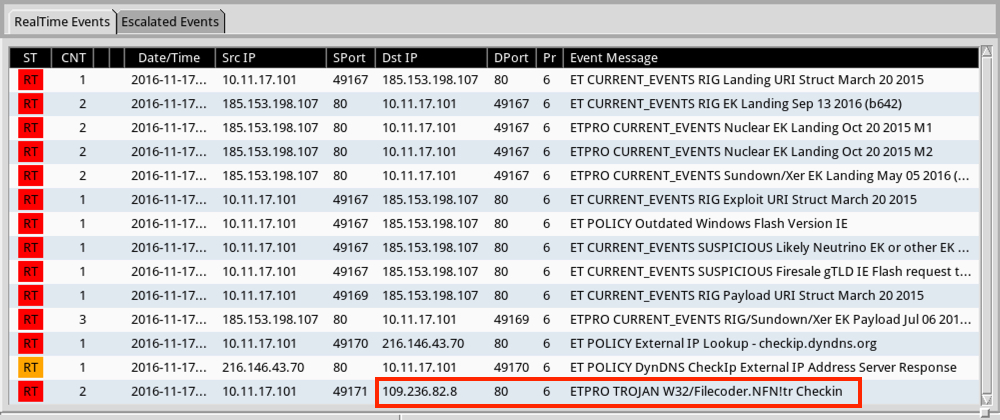
Shown above: Alerts using tcpreplay on the pcap with the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion.
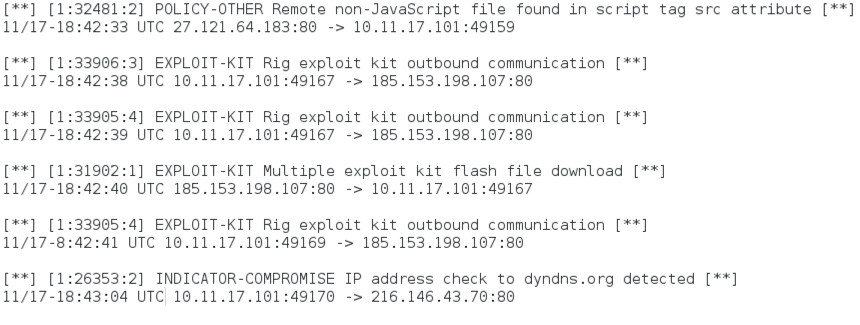
Shown above: Hits from Snort 2.9.8.3 using the Snort subscription ruleset.
Click here to return to the main page.

