2017-02-23 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-23-Hancitor-infection-with-ZLoader.pcap.zip 13.9 MB (13,917,157 bytes)
- 2017-02-23-Hancitor-infection-with-ZLoader.pcap (14,779,267 bytes)
- 2017-02-23-Hancitor-malspam-5-examples.zip 10.1 kB (10,120 bytes)
- 2017-02-22-Hancitor-malspam-1550-UTC.eml (4,863 bytes)
- 2017-02-22-Hancitor-malspam-1847-UTC.eml (4,932 bytes)
- 2017-02-23-Hancitor-malspam-1726-UTC.eml (3,933 bytes)
- 2017-02-23-Hancitor-malspam-1902-UTC.eml (3,985 bytes)
- 2017-02-23-Hancitor-malspam-1907-UTC.eml (3,979 bytes)
- 2017-02-23-malware-from-Hancitor-infection.zip 291.3 kB (291,269 bytes)
- BN87E4.tmp.exe (257,536 bytes)
- eFax_Harryrobershard.doc (179,200 bytes)
DESCRIPTION:
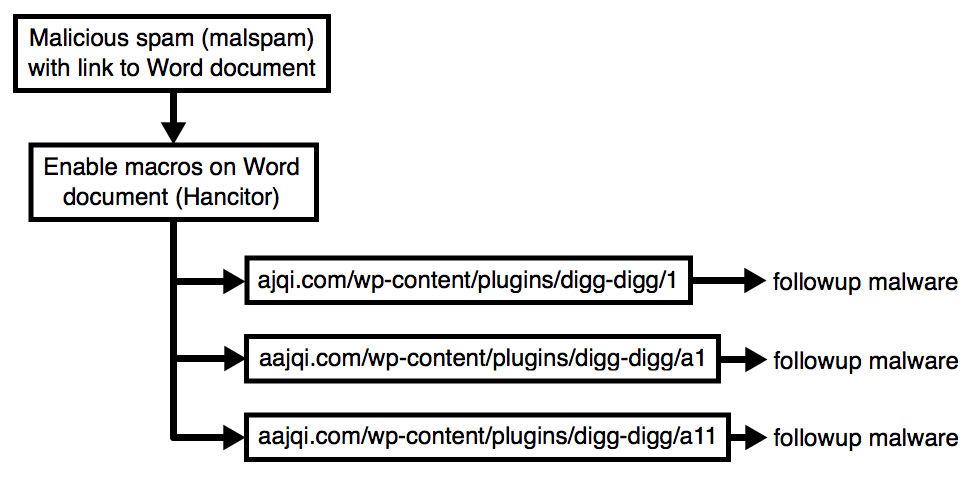
- Malicious spam (malspam) with link that downloaded a malcious Microsoft Word document (Hancitor). The Hancitor malware document is designed to download and infect Windows hosts with Pony and ZLoader (DELoader).
Shown above: Flow chart for today's traffic (Thursday 2017-02-23).
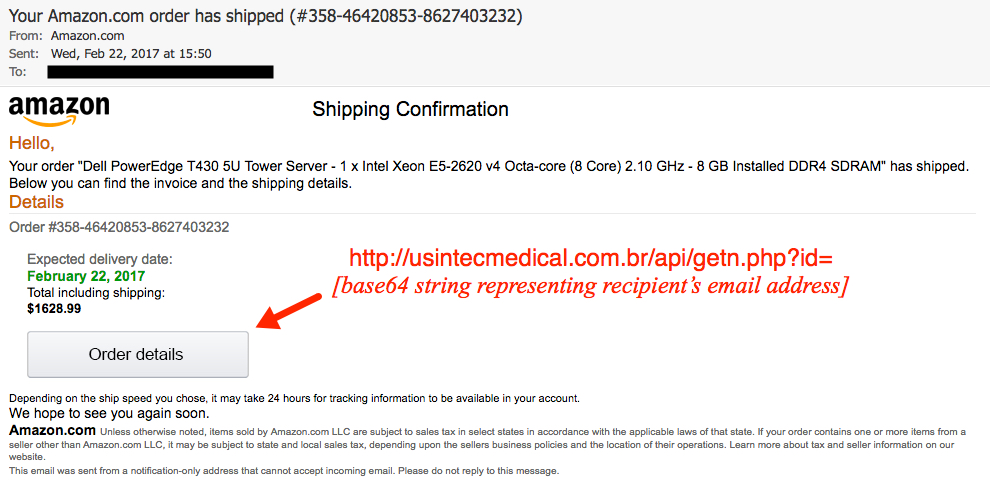
Shown above: Screenshot from one of the emails from yesterday (Wednesday 2017-02-22).
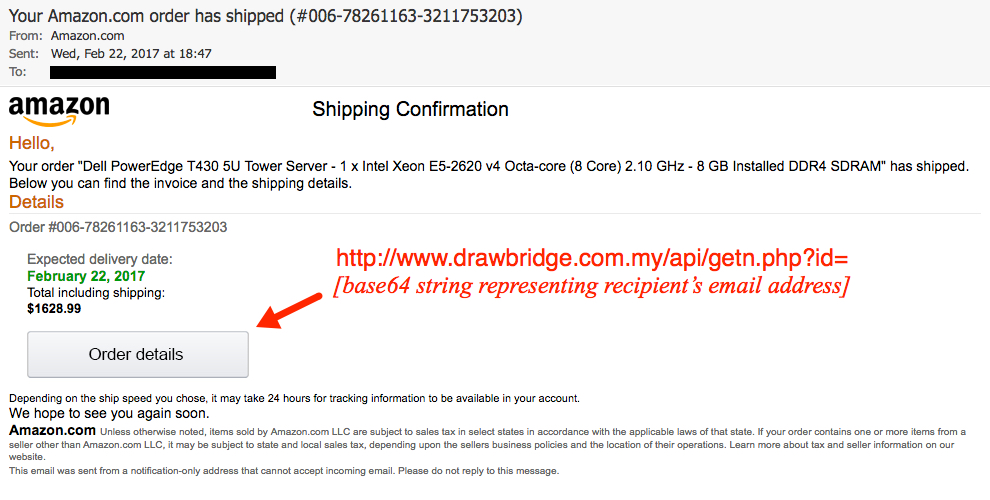
Shown above: Screenshot from another one of the emails from yesterday (Wednesday 2017-02-22).
Shown above: Screenshot from one of the emails today (Thursday 2017-01-23).
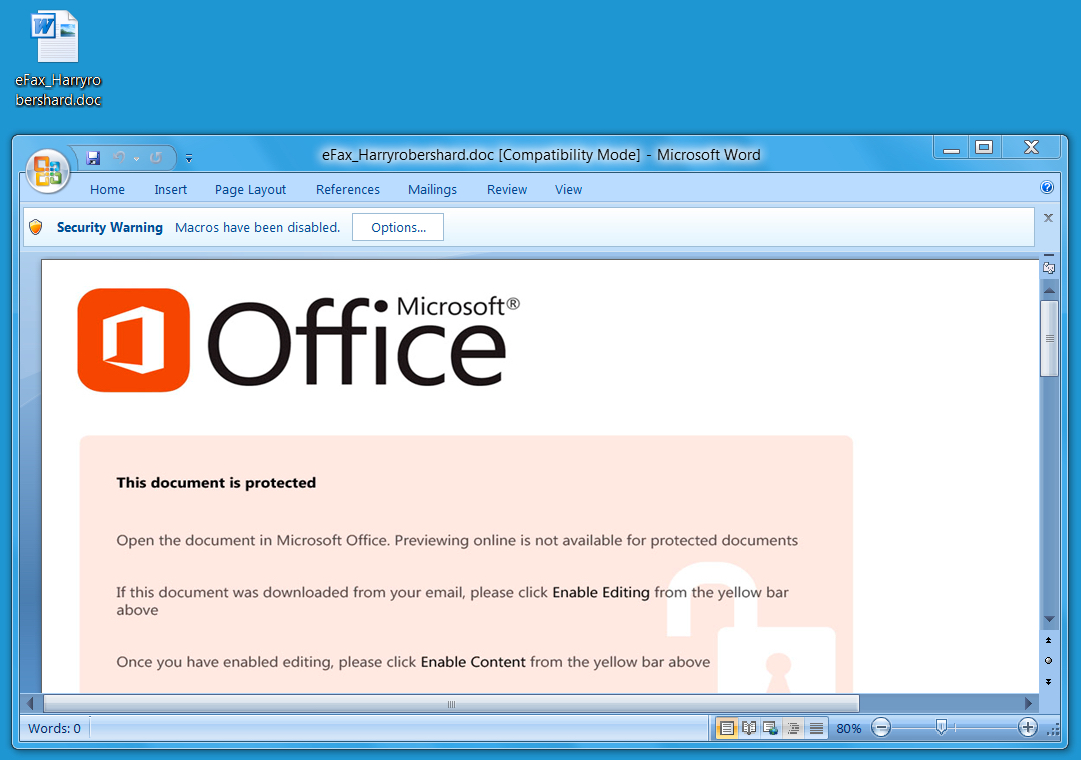
Shown above: Malicious Word document (Hancitor) seen today (2017-01-23).
TRAFFIC
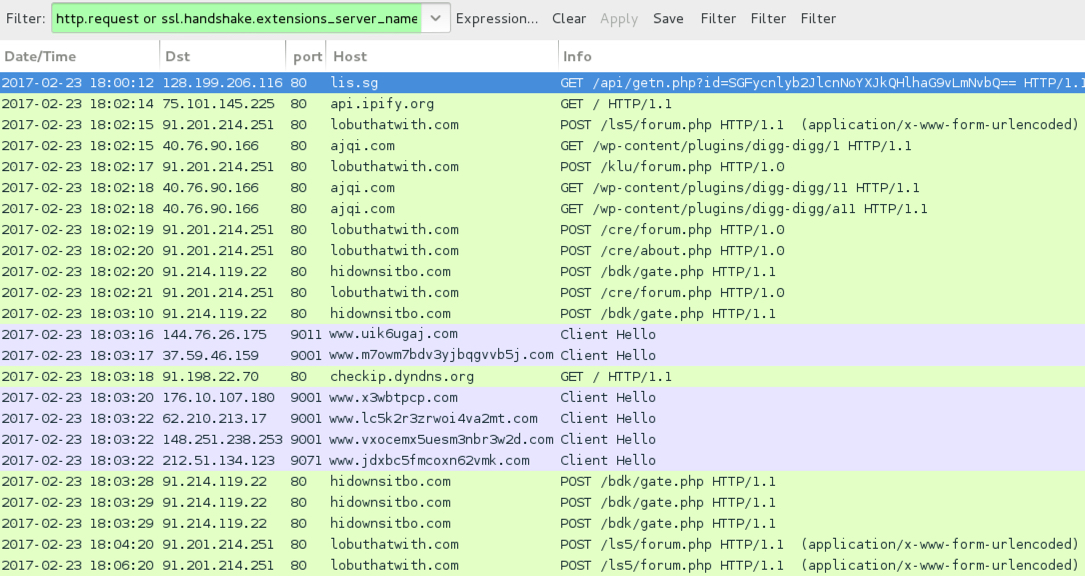
Shown above: Traffic from the infection today (Thursday 2017-02-23) filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS FROM THURSDAY 2017-02-23 INFECTION:
- 128.199.206[.]116 port 80 - lis[.]sg - GET /api/getn.php?id=[base64 string]
- 91.201.214[.]251 port 80 - lobuthatwith[.]com - POST /ls5/forum.php
- 91.201.214[.]251 port 80 - lobuthatwith[.]com - POST /klu/forum.php
- 91.201.214[.]251 port 80 - lobuthatwith[.]com - POST /cre/forum.php
- 91.201.214[.]251 port 80 - lobuthatwith[.]com - POST /cre/about.php
- 40.76.90[.]166 port 80 - ajqi[.]com - GET /wp-content/plugins/digg-digg/1
- 40.76.90[.]166 port 80 - ajqi[.]com - GET /wp-content/plugins/digg-digg/11
- 40.76.90[.]166 port 80 - ajqi[.]com - GET /wp-content/plugins/digg-digg/a11
- 91.214.119[.]22 port 80 - hidownsitbo[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses on various ports - Various domains - Tor traffic
NOTE: I was unable to grab any Word documents from the emails yesterday (2017-02-22), so I don't have any traffic for that day.
FILE HASHES
HANCITOR MALDOC:
- SHA256 hash: 9b925854b37b5f305327147e54198e44859c21dd57a8f4ac93b882d43fec01e7
- File name: eFax_Harryrobershard.doc
DELOADER (ZLOADER):
- SHA256 hash: ea4f8674d9cf4305c5c7d384bc5b90883de22e8c8e6bf8b1ec52312751e59de8
- File location: C:\Users\[username]\AppData\Local\Temp\BN87E4.tmp
Click here to return to the main page.