2017-03-30 - DRIDEX INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-30-Dridex-activity-2-pcaps.zip 1.1 MB (1,051,018 bytes)
- 2017-03-30-confirmation-letter-Dridex-infection.pcap (1,022,706 bytes)
- 2017-03-30-travel-booking-Dridex-infection.pcap (188,871 bytes)
- 2017-03-30-Dridex-malspam-tracking-spreadsheets.zip 3.8 kB (3,787 bytes)
- 2017-03-30-Dridex-confirmation-letter-malspam-tracker.csv (10,679 bytes)
- 2017-03-30-Dridex-travel-booking-malspam-tracker.csv (3,321 bytes)
- 2017-03-30-Dridex-travel-booking-emails-and-malware.zip 175.3 kB (175,348 bytes)
- 2017-03-30-Dridex-confirmation-letter-emails-and-malware.zip 5.5 MB (5,454,043 bytes)
NOTES:
- After a 6-month hiatus, Dridex malspam came back in January 2017 (link), but I hadn't personally run across any Dridex until Thursday 2017-03-30.
EMAILS
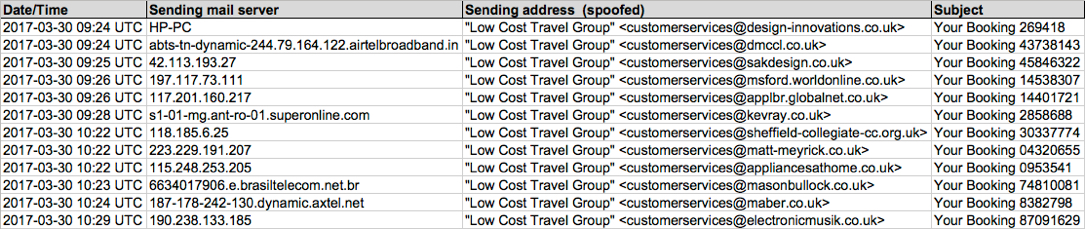
Shown above: Screen shot from the spreadsheet tracker for the first wave.
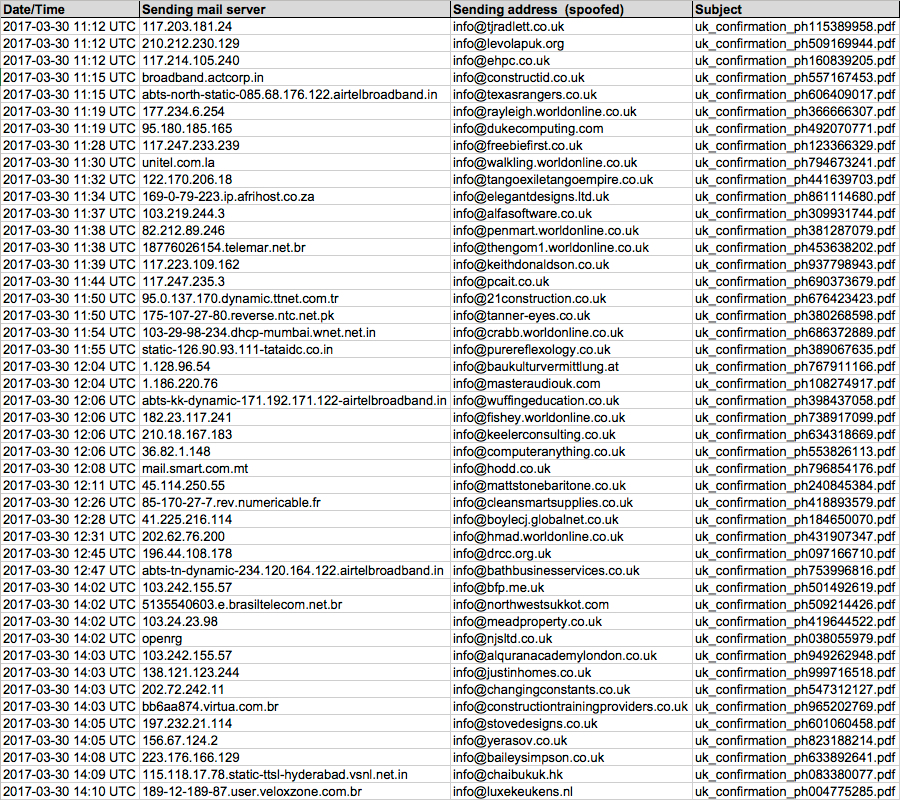
Shown above: Screen shot from the spreadsheet tracker for the second wave.
FIRST WAVE:
- Date/Time: Thursday 2017-03-30 from 09:24 thru 10:29 UTC
- From: "Low Cost Travel Group" <customerservices@[various domains]>
- Subject: Your Booking [6 to 8 digits]
- Attachment name: Direct-Documentation [6 to 8 digits]-1.zip
- Extracted file name (in all cases): Direct-Documentation 1530219.vbs
SECOND WAVE:
- Date/Time: Thursday 2017-03-30 from 11:12 thru at least 14:10 UTC (when I stopped collecting samples)
- From: info@[various domains]
- Subject: uk_confirmation_ph[9 digits].pdf
- Attachment name: uk_confirmation_ph[9 digits].zip
- Extracted file name (in all cases): uk_confirmation_ph954869378.exe
TRAFFIC
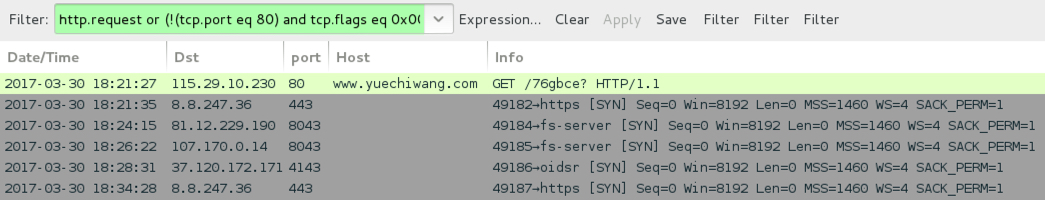
Shown above: Infection traffic from the first wave filtered in Wireshark.
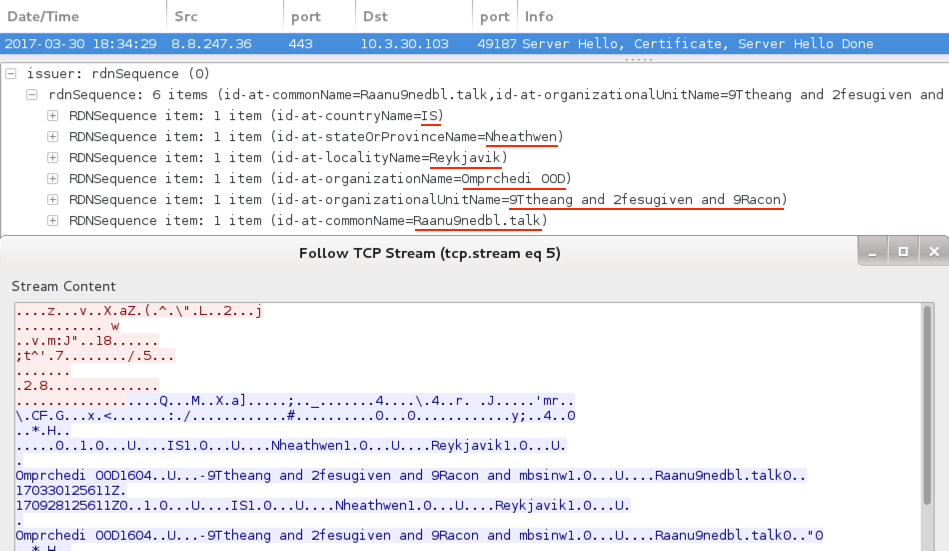
Shown above: SSL certificate info associated with Dridex.
HTTP REQUESTS TO DOWNLOAD THE DRIDEX BINARY FROM FIRST WAVE'S VBS FILES:
- 162.210.101[.]93 port 80 - kapil.50webs[.]com - GET /76gbce?
- 93.184.165[.]10 port 80 - mkcslava[.]ru - GET /76gbce?
- 208.113.152[.]209 port 80 - newohioreview[.]com - GET /76gbce?
- 159.253.37[.]153 port 80 - omurongen[.]com - GET /76gbce?
- 47.90.77[.]250 port 80 - pk10kaijiang[.]com - GET /76gbce?
- 208.109.181[.]224 port 80 - roylgrafix[.]com - GET /76gbce?
- 192.107.41[.]200 port 80 - signwaves[.]net - GET /76gbce?
- 162.210.102[.]98 port 80 - testsite.prosun[.]com - GET /76gbce?
- 158.69.245[.]78 port 80 - trumppsdetroit[.]com - GET /76gbce?
- 95.131.50[.]14 port 80 - ww.visual[.]hu - GET /76gbce?
- 115.29.10[.]230 port 80 - www.yuechiwang[.]com - GET /76gbce?
- NOTE: The binaries are encrypted when sent over the network and decrypted on the local host.
POST-INFECTION HTTPS/SSL/TLS TRAFFIC - DRIDEX FROM FIRST WAVE:
- 8.8.247[.]36 port 443
- 37.120.172[.]171 port 4143
- 81.12.229[.]190 port 8043
- 107.170.0[.]14 port 8043
ADDITIONAL CONNECTIONS OR ATTEMPTED CONNECTIONS - DRIDEX FROM SECOND WAVE:
- 23.95.23[.]219 port 443
- 66.214.155[.]189 port 443
- 86.3.169[.]110 port 443
- 86.4.149[.]217 port 443
- 88.177.240[.]182 port 443
- 90.219.218[.]80 port 443
- 95.145.161[.]76 port 443
- 101.165.141[.]2 port 443
- 109.170.219[.]19 port 443
- 110.143.61[.]115 port 443
- 117.120.7[.]82 port 443
- 134.170.165[.]249 port 443
- 174.104.208[.]57 port 443
- 175.32.140[.]13 port 443
- 179.108.87[.]11 port 443
- 213.214.50[.]60 port 443
SHA256 HASHES
VBS FILES:
- 34884ec18d6bbc8262812ee5ecc8803b771fcd4c554d76bee9254278effe0b48
- 84c9028a1d25e5f171c170179f2f1ea3e1eab9514812ab9e4b617de822b46e69
- d21c83b527627d0a64beb28a5a72ca21228c438861de893618ffdf46d7ef8d1c
DRIDEX BINAIRES (PE FILES):
- 1814d47adfe7a34cd2e5b2a9d6841a32677764c8498012f3ff13a5772ba9107e
- 6adda664e3ab2936a8dbe8e95e10d33e34d13fbe375123c69abf3ac5fbf52fcd
- 898e44e0ebb73dcf8fc3b667baa6db930119d1979d8269437ab89e49633ff983
- ac4d02637e1e01b16062f368658275cb8400b21f6592819d3a09dbee31cb5cc1
Click here to return to the main page.
