2017-04-05 - TEAMVIEWER-BASED MALWARE PACKAGE (TEAMSPY)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-05-TeamSpy-infection-traffic.pcap.zip 3.1 MB (3,117,055 bytes)
- 2017-04-05-TeamSpy-infection-traffic.pcap (3,325,479 bytes)
- 2017-04-05-email-and-TeamSpy-malware.zip 3.2 MB (3,222,005 bytes)
- 2017-04-04-malspam-0617-UTC.eml (9,00 bytes)
- issue2014.js (23,316 bytes)
- 31195.exe (3,229,020 bytes)
INTRODUCTION
As a volunteer Handler for the Internet Storm Center (ISC), I receive emails sent to the ISC Handlers email alias. On Tuesday 2017-04-04, we received the following notification:
From: [redacted]
Sent: Tuesday, 2017-04-04 15:04 UTC
Subject: phish link to obfuscated Java script
Hi
The attached email links to [hxxp://]4safedrivers[.]link/orders/issue2014.php which drops an obfuscated java script. The URL 4safedrivers[.]link has anonymous whois out of Australia, but 4safedrivers[.]com appears to be a legit company. I haven't had time to deobfuscate it.
Thanks
John
[signature block, redacted]
The malware is TeamViewer packaged as spyware and a remote access tool. This is called "TeamSpy" as a nickname. Associated files had already been submitted to VirusTotal before I looked at it, so John wasn't the only one who received an email like this.
This blog post is dedicated to John and others who notify the ISC about malicious spam (malspam) and other suspicious network activity. If you run across anything interesting, let us know through our contact form. We may not always have time to investigate every notification, but they're always appreciated.
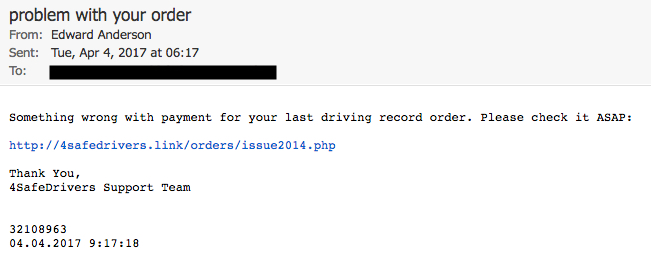
Shown above: Screen shot of the malspam John provided us.
EMAIL HEADERS:
- Date/Time: Tuesday 2017-04-04 at 06:17 UTC
- From: (possibly spoofed) "Edward Anderson" <post@glen[.]com>
- Subject: problem with your order
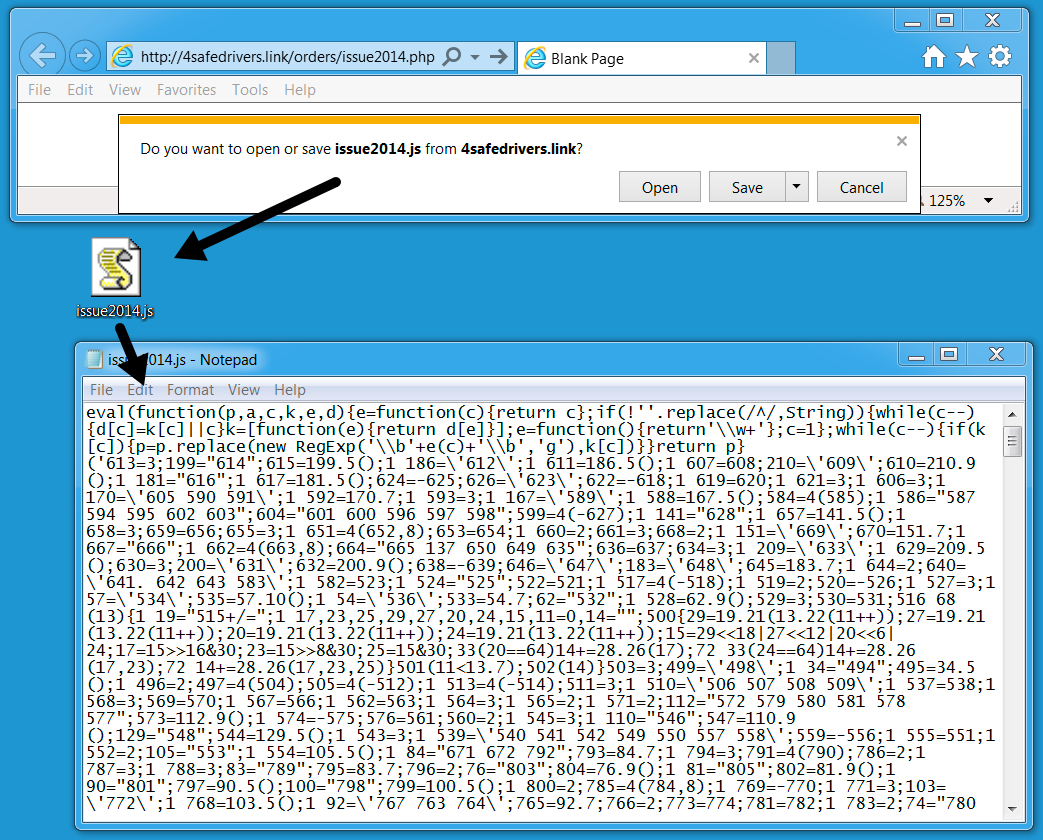
Shown above: .js file returned from link in the malspam.
TRAFFIC
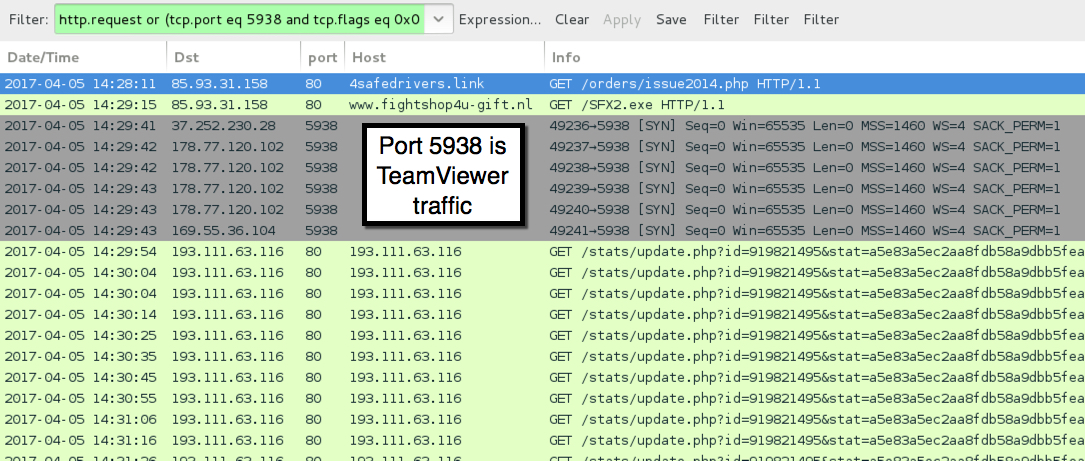
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 85.93.31[.]158 port 80 - 4safedrivers[.]link - GET /orders/issue2014.php
- 85.93.31[.]158 port 80 - www.fightshop4u-gift[.]nl - GET /SFX2.exe
- 193.111.63[.]116 port 80 - 193.111.63[.]116 - GET /stats/update.php?id=[9-digit number]&stat=[string of alphanumeric characters]
- 37.252.230[.]28 port 5938 - ping3.teamviewer[.]com [TeamViewer traffic - not inherently malicious]
- 178.77.129[.]102 port 5938 - master13.teamveiwer[.]com [TeamViewer traffic - not inherently malicious]
- 169.55.36[.]104 port 5938 - server18106.teamviewer[.]com [TeamViewer traffic - not inherently malicious]
FILE HASHES
.JS FILE FROM LINK IN THE MALSPAM:
- SHA256 hash: 346294859086cb4d0e1fce0ae50cb5cfa64647cca5a4a882b38b9d9444c5ab92
File name: issue2014.js
File size: 23,316 bytes
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 28d47f653cda2699e54ed54809af2587dd1de04df5cec184c0c5f9dc15bf26d7
File location: C:\Users\[username]\AppData\Local\Temp\[5 random digits].exe
File size: 3,229,020 bytes
File description: TeamSpy malware
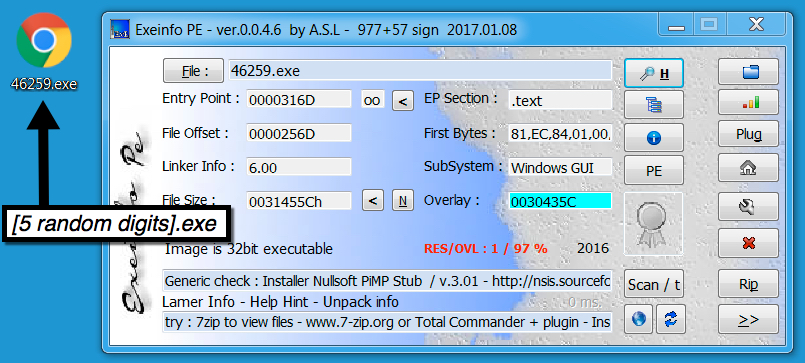
Shown above: The TeamSpy EXE downloaded by the .js file.
IMAGES
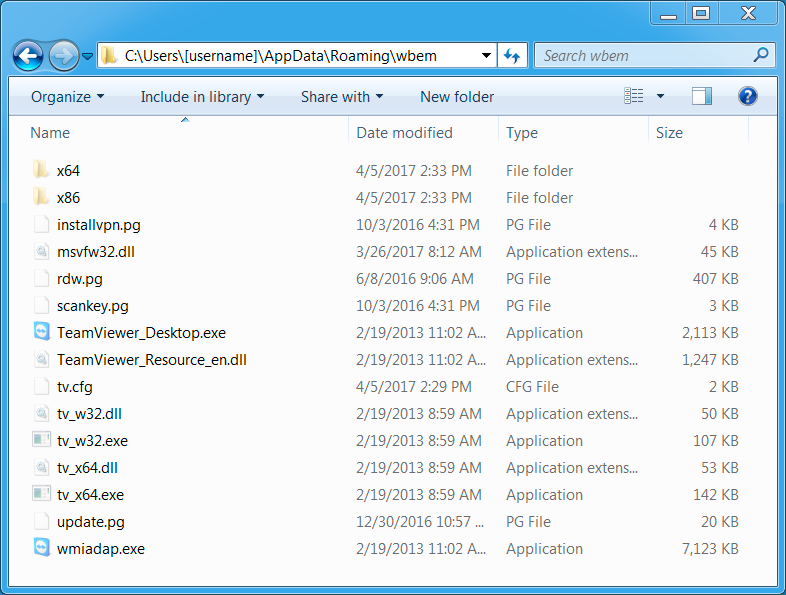
Shown above: TeamViewer files in a hidden directory on my infected lab host.
FINAL WORDS
This TeamSpy malware package is nothing new. For example, Kaspersky published a report in 2013 on how TeamViewer was abused for Cyber Espionage (link).
I don't think this particular malspam is associated with actual cyber espionage (though I could be wrong about that). The non-TeamViewer callback IP address 193.111.63[.]116 belongs to a Ukrainian hosting provider. To me, this example feels more like commodity malware used in crimeware campaigns.
Click here to return to the main page.
