2017-04-16 - EITEST CAMPAIGN: RIG EK OR HOEFLERTEXT CHROME POPUP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-16-EITest-activity-2-pcaps.zip 1.0 MB (1,036,186 bytes)
- 2017-04-16-EITest-HoeflerText-popup-sends-Spora-ransomware.pcap (201,890 bytes)
- 2017-04-16-EITest-Rig-EK-traffic.pcap (1,356,878 bytes)
- 2017-04-16-EITest-malware-and-artifacts.zip 500.4 kB (500,423 bytes)
- 2017-04-16-EITest-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-04-16-EITest-Rig-EK-flash-exploit.swf (19,110 bytes)
- 2017-04-16-EITest-Rig-EK-landing-page.txt (117,801 bytes)
- 2017-04-16-EITest-Rig-EK-payload-i4rcqon9.exe (237,568 bytes) -- I think this is Quant Loader
- 2017-04-16-EITest-Rig-EK-post-infection-follow-up-malware.exe (311,296 bytes)
- 2017-04-16-Spora-ransomware-decryption-instructions.html (12,326 bytes)
- 2017-04-16-Spora-ransomware.exe (79,872 bytes)
- 2017-04-16-page-from-tanaakk_net-with-injected-EITest-script-for-HoeflerText.txt (97,366 bytes)
- 2017-04-16-page-from-tanaakk_net-with-injected-EITest-script-for-RigEK.txt (51,084 bytes)
NOTES:
- As always, thanks to @nao_sec for routinely tweeting about compromised websites. I used that info to generate traffic for this blog post.
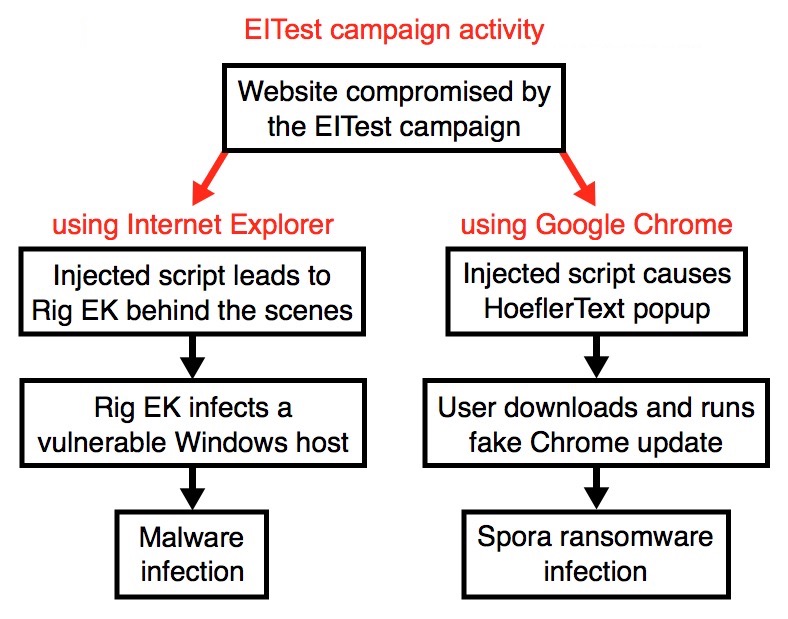
Shown above: Flowchart for this infection traffic.
TRAFFIC
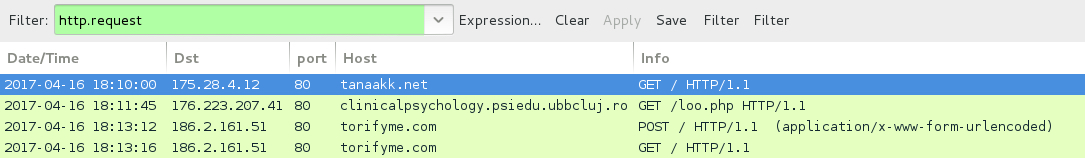
Shown above: EITest HoeflerText popup traffic when compromised site is viewed using Google Chrome.
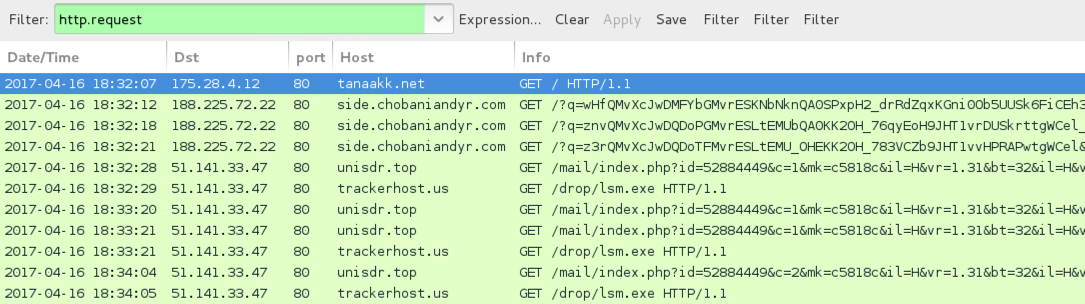
Shown above: EITest Rig EK traffic when compromised site is viewed using Internet Explorer.
ASSOCIATED DOMAINS:
- tanaakk[.]net - compromised site (viewed in Google Chrome)
- 176.223.207[.]41 port 80 - clinicalpsychology.psiedu.ubbcluj[.]ro - GET /loo.php - Spora ransomware download
- 186.2.161[.]51 port 80 - torifyme[.]com - POST / - Spora ransomware decryption site
- 186.2.161[.]51 port 80 - torifyme[.]com - GET / - Spora ransomware decryption site
- tanaakk[.]net - compromised site (viewed in Internet Explorer)
- 188.225.72[.]22 port 80 - side.chobaniandyr[.]com - Rig EK
- 51.141.33[.]47 port 80 - unisdr[.]top - post-infection traffic
- 51.141.33[.]47 port 80 - trackerhost[.]us - post-infection traffic
FILE HASHES
SPORA RANSOMWARE FROM HOEFLERTEXT POPUP:
- SHA256 hash: 8a2eafed0b59841f76b0c23bddeb9e3cadfebba4c04a7d24694273642ffec109
File name: Chrome Font.exe (with non-ASCII characters for some of the letters)
File description Spora ransomware from EITest campaign HoeflerText popup on 2017-04-16
ARTIFACTS FROM RIG EK:
- SHA256 hash: cd3a17defe0a5c0ff35f6fccdcb33080eb06c02a6a628e5acda3f909a0b58997
File description Rig EK Flash exploit seen on 2017-04-16
- SHA256 hash: 26134f16143eb1d5fc2a13f51929166db18a9e04ea381a9bd23cabea24508879
File description Rig EK payload from the EITest campaign on 2017-04-16 (possible Quant Loader)
- SHA256 hash: 7a7c25c5694ceecf589bbc30361f9bf249c3825f2334d7595b83cee23234f9a9
File description Follow-up malware after EITest Rig EK infection on 2017-04-16
Click here to return to the main page.