2017-05-09 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-09-Hancitor-infection-with-ZLoader.pcap.zip 7.6 MB (7,563,963 bytes)
- 2017-05-09-Hancitor-infection-with-ZLoader.pcap (7,938,967 bytes)
- 2017-05-09-Hancitor-malspam-2-examples.zip 2.5 kB (2,515 bytes)
- 2017-05-09-Hancitor-malspam-1637-UTC.eml (1,913 bytes)
- 2017-05-09-Hancitor-malspam-1728-UTC.eml (1,915 bytes)
- 2017-05-09-malware-from-Hancitor-infection.zip 300.7 kB (300,737 bytes)
- BNB3B4.tmp (194,048 bytes)
- scanned_subpoena_blake.reginald.doc (224,768 bytes)
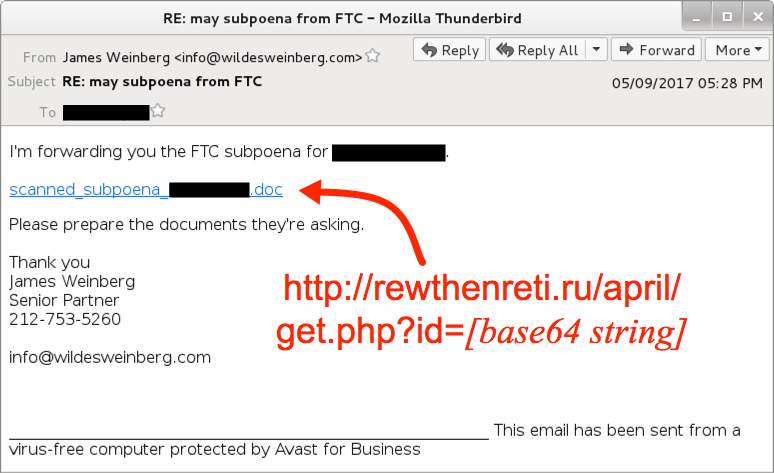
Shown above: Screen shot from one of the emails.
EMAIL HEADERS:
- Date: Tuesday 2017-05-09
- Subject: Completed: [domain] - Wire Transfer Instructions for [username] Document Ready for Signature
- From: "Cameron Smith via DocuSign" <dse@docusgn[.]com>
- Subject: RE: may subpoena from FTC
- From: "James Weinberg" <info@wildesweinberg[.]com>
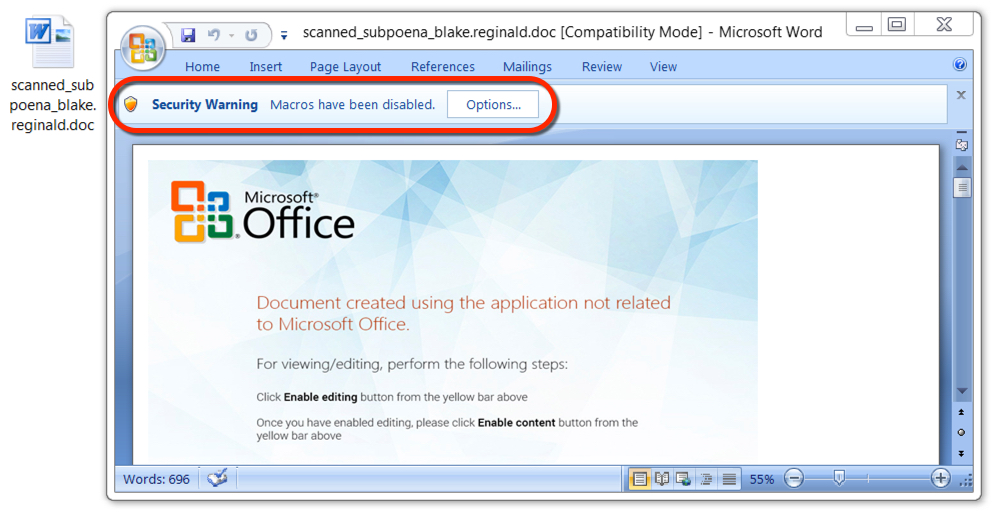
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
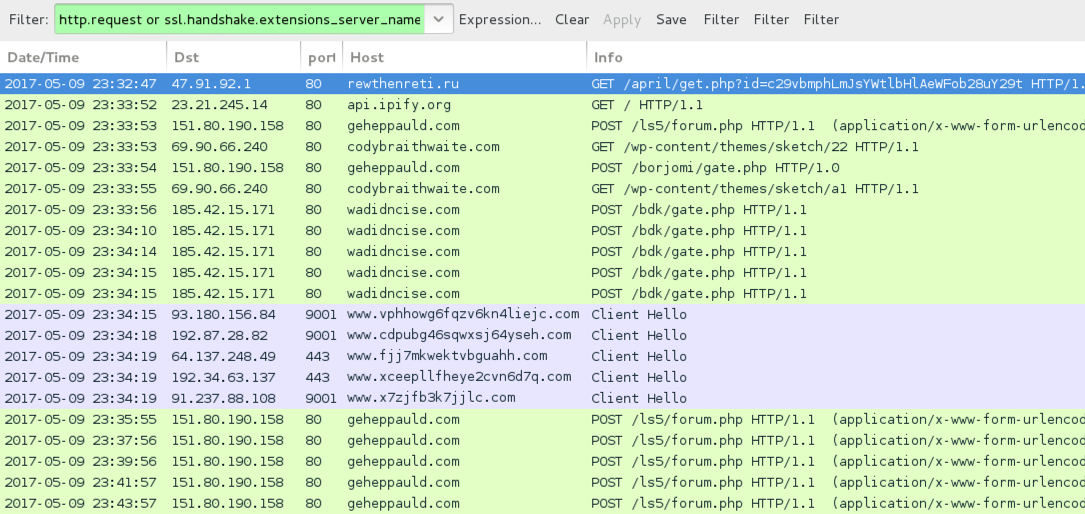
Shown above: Traffic from the infection filtered in Wireshark.
HTTP GET REQUESTS FOR THE WORD DOCUMENT:
- 47.91.92[.]1 port 80 - andsihowdint[.]ru - GET /april/get.php?id=[base64 string]
- 47.91.92[.]1 port 80 - andsihowdint[.]ru - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - boatingflagpole[.]com - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - godisimnot[.]com - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - hertretletan[.]ru - GET /april/get.php?id=[base64 string]
- 47.91.92[.]1 port 80 - hertretletan[.]ru - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - hudsonhughes[.]com - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - knoxvilleupholstery[.]com - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - partnersprojectinc[.]com - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - partnersprojectinc[.]net - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - precisionexposures[.]com - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - rewthenreti[.]ru - GET /april/get.php?id=[base64 string]
- 47.91.92[.]1 port 80 - rewthenreti[.]ru - GET /file.php?document=[base64 string]
- 47.91.92[.]1 port 80 - zariyamatrimony[.]com - GET /file.php?document=[base64 string]
NAMES FOR THE MALICIOUS WORD DOCUMENTS:
- Wire_Transfer_[username].doc
- scanned_subpoena_[username].doc
POST-INFECTION TRAFFIC FROM MY ONE INFECTED HOST:
- 151.80.190[.]158 port 80 - geheppauld[.]com - POST /ls5/forum.php
- 151.80.190[.]158 port 80 - geheppauld[.]com - POST /borjomi/gate.php
- 69.90.66[.]240 port 80 - codybraithwaite[.]com - GET /wp-content/themes/sketch/22
- 69.90.66[.]240 port 80 - codybraithwaite[.]com - GET /wp-content/themes/sketch/a1
- 185.42.15[.]171 port 80 - wadidncise[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- Various IP addresses on various TCP ports - Tor traffic
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 41b7ecafccc7f21966827c48c902c5d28d5ed5ac21f56c9978ccd2709ac8b797
File name: scanned_subpoena_blake.reginald.doc
File size: 224,768 bytes
File description: Hancitor maldoc
MALWARE FROM THE INFECTED HOST:
- SHA256 hash: 5b9fe396d66f13301d3ad0027e124f64258079d3e7401076581b9b5d6eefa826
File location: C:\Users\[username]\AppData\Local\Temp\BNB3B4.tmp
File size: 194,048 bytes
File description: DELoader/ZLoader
Click here to return to the main page.
