2017-05-15 - THE JAFF RANSOMWARE TRAIN KEEPS ON ROLLIN'
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-15-Jaff-ransomware-traffic.pcap.zip 150 kB (150,210 bytes)
- 2017-05-15-Jaff-ransomware-traffic.pcap (158,549 bytes)
- 2017-05-15-Jaff-ransomware-malspam-1035-UTC.eml.zip 55.1 kB (55,059 bytes)
- 2017-05-15-Jaff-ransomware-malspam-1035-UTC.eml (72,864 bytes)
- 2017-05-15-Jaff-ransomware-files.zip 260.1 kB (260,149 bytes)
- 001_8378.pdf (53,257 bytes)
- 2017-05-15-Jaff-decryptor-index.css (2,661 bytes)
- 2017-05-15-Jaff-decryptor.html (5091 bytes)
- 2017-05-15-Jaff-ransomware-ReadMe.bmp (3,145,782 bytes)
- 2017-05-15-Jaff-ransomware-ReadMe.html (1,431 bytes)
- 2017-05-15-Jaff-ransomware-ReadMe.txt (482 bytes)
- 2017-05-15-Jaff-ransomware-drefudre20.exe (176,128 bytes)
- HHU67.docm (55,129 bytes)
NOTES:
- More malspam pushing Jaff ransomware this morning...
- It's the same type of malspam we've seen before with PDF attachments --> embedded Word documents (with malicious macros) --> follow-up malware.
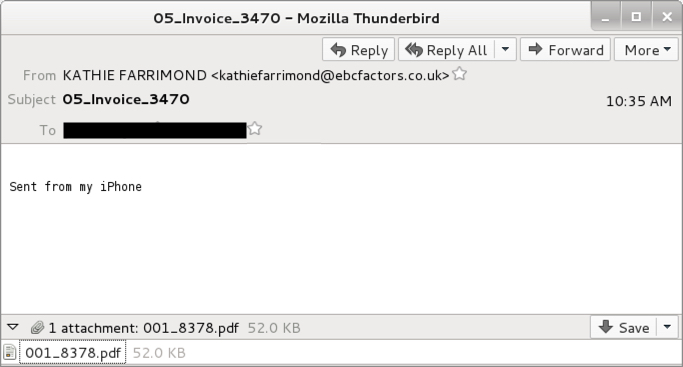
Shown above: An example of the emails.
EMAIL HEADERS:
- Date/Time: Monday 2017-05-15 at 10:35 UTC
- From: KATHIE FARRIMOND <kathiefarrimond@ebcfactors[.]co[.]uk>
- Subject: 05_Invoice_3470
- Attachment name: 001_8378.pdf
MALWARE
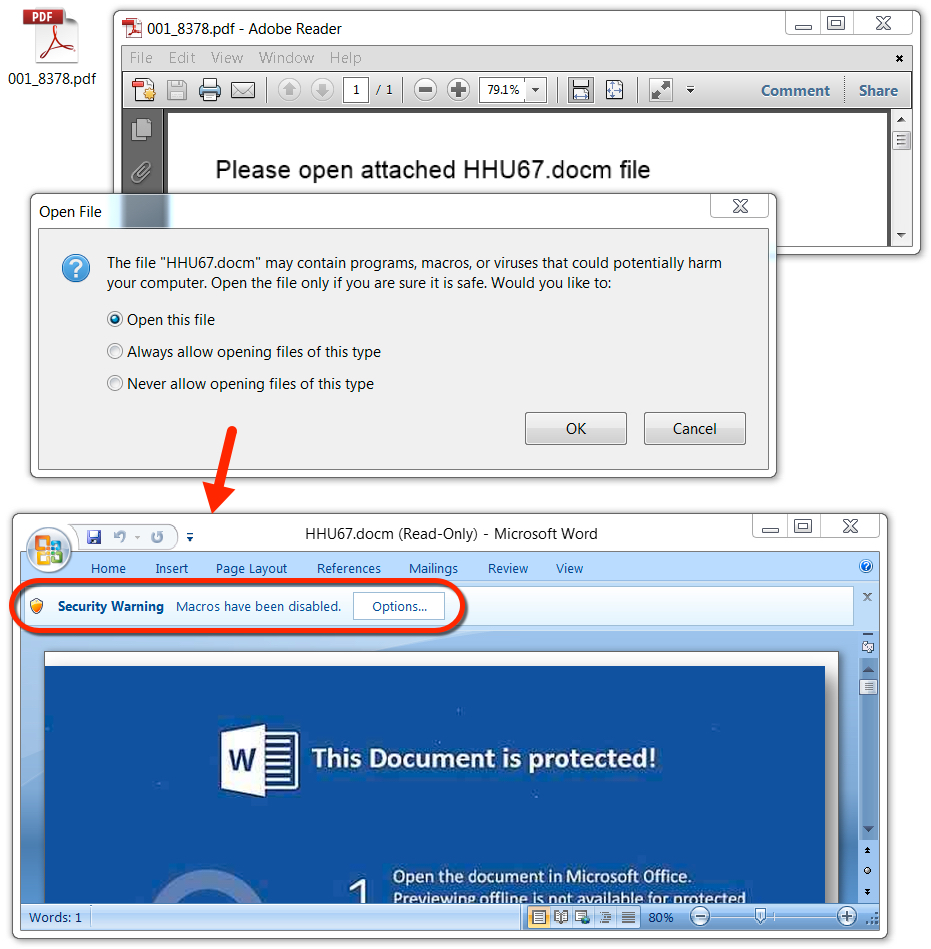
Shown above: The PDF attachment contains an embedded Word document with malicious macros.
ATTACHMENT:
- SHA256 hash: 5968b7a89e5d1db8447b5343f20362ab713551a94226fb905fff7a067c770c79
File size: 53,257 bytes
File name: 001_8378.pdf
EMBEDDED WORD DOCUMENT:
- SHA256 hash: a5008680100ec970009eb68b5e8bb98af5fb58aef5b8f043e1517390245e0edd
File size: 55,129 bytes
File name: HHU67.docm
JAFF RANSOMWARE:
- SHA256 hash: 41bce3e382cee06aa65fbee15fd38f7187fb090d5da78d868f57c84197689287
File size: 176,128
File location: C:\Users\[username]\AppData\Local\Temp\drefudre20.exe
TRAFFIC
URLS FROM THE WORD MACROS TO DOWNLOAD JAFF RANSOMWARE:
- 203.170.192[.]184 port 80 - urachart[.]com - GET /hHGFjd
- 185.2.31[.]189 port 80 - fotografikum[.]com - GET /hHGFjd
- 185.109.146[.]224 port 80 - 5hdnnd74fffrottd[.]com - GET /af/hHGFjd
- 185.109.146[.]224 port 80 - byydei74fg43ff4f[.]net - GET /af/hHGFjd
- 185.109.146[.]224 port 80 - sjffonrvcik45bd[.]info - GET /af/hHGFjd
JAFF RANSOMWARE POST-INFECTION TRAFFIC:
- 47.91.107[.]213 port 80 h552terriddows[.]com - GET /a5/
- rktazuzi7hbln7sy[.]onion - Tor domain for Jaff Decryptor (same as last week)
Traffic from the infection filtered in Wireshark.
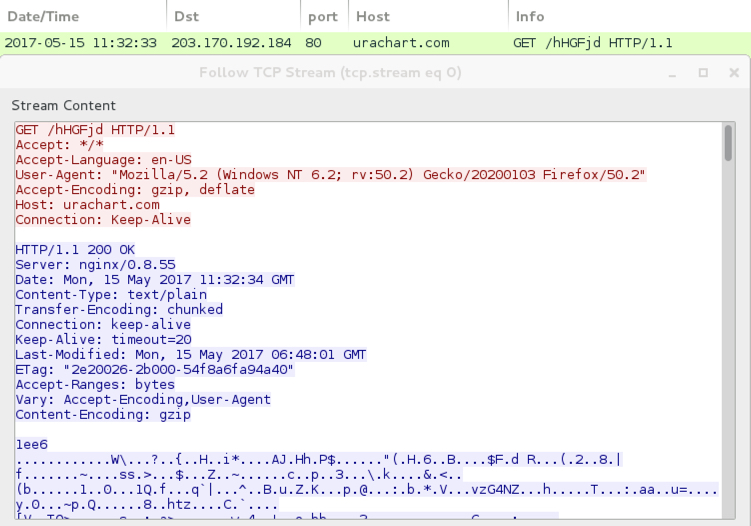
HTTP request for the Jaff ransomware.
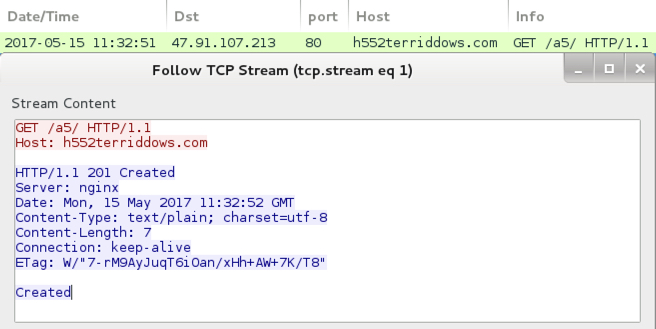
Post-infection traffic from the infected Windows host.
IMAGES
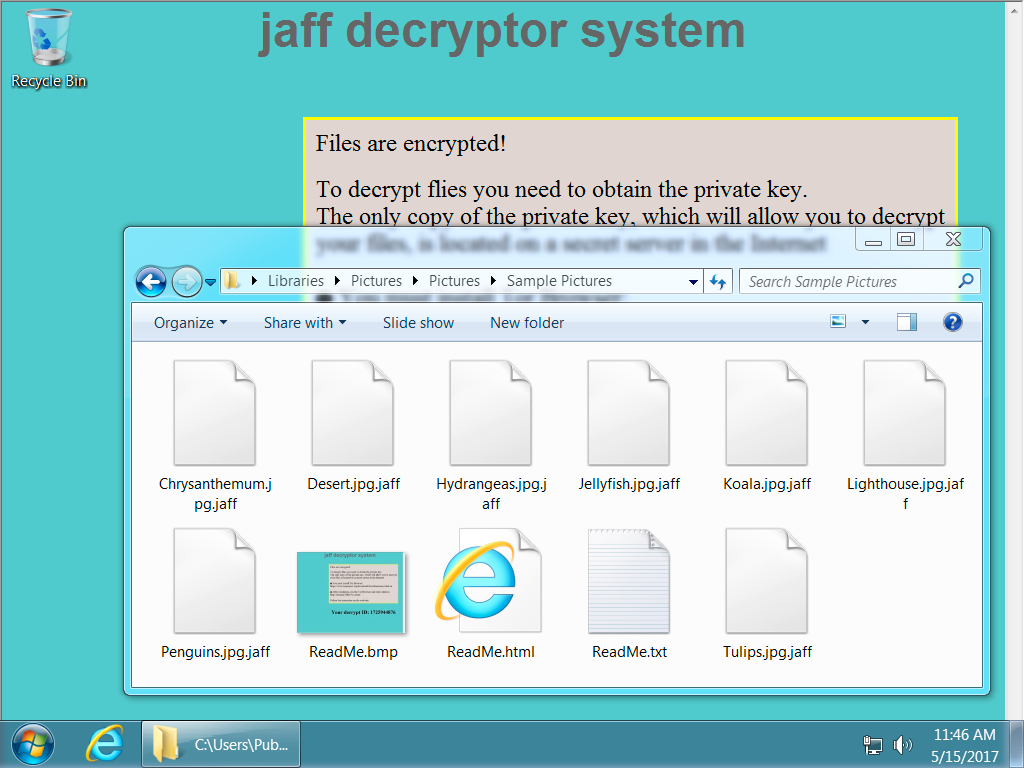
Shown above: Desktop of an infected Windows host.
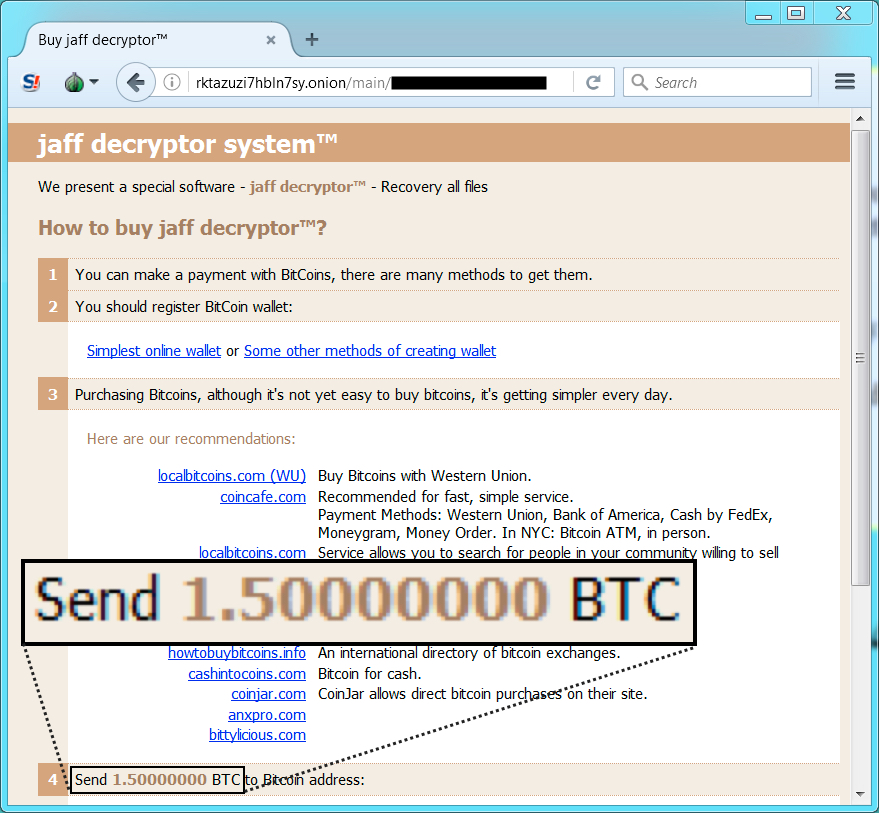
Shown above: Going to the Jaff Decryptor.
FINAL NOTES
Click here to return to the main page.
