2017-06-14 - TRICKBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-14-Trickbot-infection-traffic.pcap.zip 11.2 MB (11,247,705 bytes)
- 2017-06-14-Trickbot-malspam-tracker.csv.zip 1.3 kB (1,317 bytes)
- 2017-06-14-Trickbot-emails-and-malware.zip 2.1 MB (2,070,424 bytes)
TWEETS ABOUT TODAY'S #TRICKBOT ACTIVITY:
- @coldshell: #Trickbot payload delivery (campaign 14/06/17) (link)
- @James_inthe_box: Blank subject, IMG_XXXX.zip-> exe is more #trickbot (link)
OTHER NOTES:
- The first wave used PDF attachments with embedded .xlsm spreadsheets containing macros.
- Emails from the next wave had no subject, no message text, and ZIP attachments containing EXE files that had already been used the previous week.
- This blog post does not provide any copies of the emails or Trickbot malware from the second wave, since it is old malware.
EMAILS
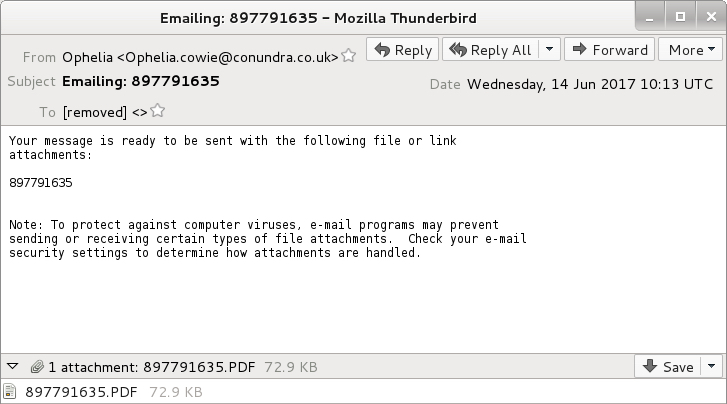
Shown above: An example of the emails.
8 EXAMPLES FROM THE FIRST WAVE:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME (PDF) -- EMBEDDED .XLSM FILE
- 2017-06-14 09:19:20 UTC -- "Kris" <Kris.waterton@ncacademy[.]co[.]uk> -- Emailing: 75064761 -- 75064761.PDF -- 0000850979953.xlsm
- 2017-06-14 09:23:49 UTC -- "Stacie" <Stacie.hastings@andyrh.globalnet[.]co[.]uk> -- Emailing: 364358435 -- 364358435.PDF -- 0000255379449.xlsm
- 2017-06-14 09:24:08 UTC -- "Wilfredo" <Wilfredo.burns@caterpillarparties[.]co[.]uk> -- Emailing: 855177611 -- 855177611.PDF -- 0000821029184.xlsm
- 2017-06-14 09:25:06 UTC -- "Ora" <Ora.battle@macrosave[.]co[.]uk> -- Emailing: 010516440 -- 010516440.PDF -- 0000370369406.xlsm
- 2017-06-14 10:10:08 UTC -- "Seymour" <Seymour.grundy@g0slh.worldonline[.]co[.]uk> -- Emailing: 03049302 -- 03049302.PDF -- 0000896782173.xlsm
- 2017-06-14 10:11:14 UTC -- "Antony" <Antony.morley@leighcommunitytrust[.]co[.]uk> -- Emailing: 512339633 -- 512339633.PDF -- 0000806624686.xlsm
- 2017-06-14 10:12:25 UTC -- "Derick" <Derick.holloway@hutsby[.]co[.]uk> -- Emailing: 93122911 -- 93122911.PDF -- 000020640652.xlsm
- 2017-06-14 10:13:37 UTC -- "Ophelia" <Ophelia.cowie@conundra[.]co[.]uk> -- Emailing: 897791635 -- 897791635.PDF -- 0000145510097.xlsm
4 EXAMPLES FROM THE NEXT WAVE:
READ: DATE/TIME -- SENDING ADDRESS (SPOOFED) -- SUBJECT -- ATTACHMENT NAME (ZIP) -- EXTRACTED .EXE FILE
- 2017-06-14 12:25:35 UTC -- Susie <Susie@katheteriseren[.]nl> -- [no subject] -- img_1903.zip -- IMG_4892.exe
- 2017-06-14 12:47:16 UTC -- Pamela <Pamela@d-amelia[.]com> -- [no subject] -- img_3246.zip -- IMG_4892.exe
- 2017-06-14 13:14:03 UTC -- Etta <Etta@nodejobs[.]com> -- [no subject] -- img_5603.zip -- IMG_4892.exe
- 2017-06-14 13:33:52 UTC -- Rosalie <Rosalie@CMETravelResources[.]com> -- [no subject] -- img_8872.zip -- IMG_4892.exe
MALWARE
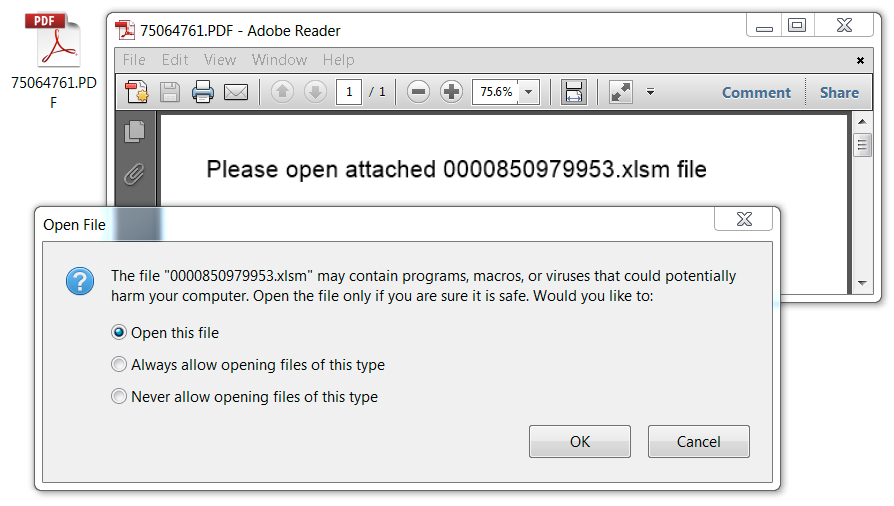
Shown above: An example of the PDF files attached to the malspam.
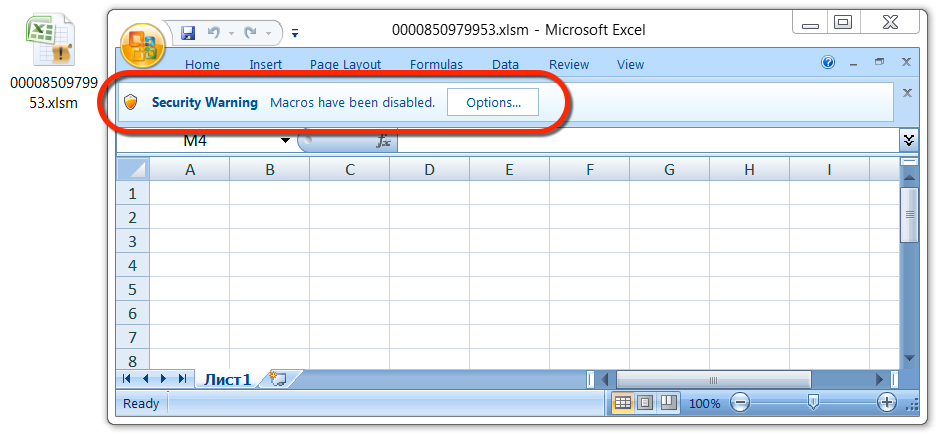
Shown above: An example of the embedded Excel spreadsheets seen when opening the PDF files.
SHA256 HASHES FOR THE PDF ATTACHMENTS:
- 0b0aeccdb275ad0477836d7ea9ba827af765dcba67a48742e871fae1c9043f9e - 512339633.PDF
- 443765dd952be1dca6b33ca8f1914b25b243f4f44f3fb6173e77fd225dd5126e - 897791635.PDF
- 58d3013f2712d5f20403441a270edf46a94b7e47e16d6859bd3cdd16954e3219 - 93122911.PDF
- 59a758567b264d674ce0dd0aa9b3d70218bd3740b68d65428695c1e55f7d4205 - 03049302.PDF
- 7d9dc623befec47ad98e760109dcc16a26a3b8eba2d8455e5a163699e0ca1ce2 - 75064761.PDF
- d6fd3a6396d96cd3932c0c2e20878175612e95ab9933f17fd95fc80cbd40b7c6 - 010516440.PDF
- d7d7a0c220a5877cf21712a0e672d277d092ccf22f9a9df55161aa245615d7a8 - 855177611.PDF
- e7890a3765ba8900fb75243845477575b27d5d2fb738b2dea91ed413aa86b221 - 364358435.PDF
SHA256 HASHES FOR THE EXTRACTED .XLSM FILES:
- 04fda74df457a0f5bc311823d0ba80f4a1742a2722ff19617a67b672e33b6927 - 0000255379449.xlsm
- 314d13fdb3ebc1836b39c7cbcbb2106f9023040d99d72f353a3bfcd2dcac83f0 - 000020640652.xlsm
- 38650bc9607386a1e54b63c6d5a18f65da184cb93586803347f82b563d163a71 - 0000370369406.xlsm
- 4ebe0627e66c6c3f02f599fdbcc00418cb7add2205157383ed7177859142cd3e - 0000145510097.xlsm
- 4f9d90fc3ba8bfe49bdcbf6b5c444c6801d9f9514d1e0490ba1b2bac26fcac2d - 0000850979953.xlsm
- 6413b501d3b464b94f896e9dd34458b8e2a7bb95703c4915aae660ec619a0661 - 0000821029184.xlsm
- abc4555ad061e1aaefb96c57c68089f59e524ca14d2e762588c83dc38c278ebb - 0000896782173.xlsm
- b8e4524202afd14538bda968f45b15a1e06b056972068b3c0b0865794426ea6e - 0000806624686.xlsm
MALWARE RETRIEVED FROM INFECTED HOST:
- SHA256 hash: 1ee95d04939a30d43c45b0a26eb175cb87c862690078645336e9e437cc668452
File size: 342,016 bytes
File location: C:\Users\[uysername]\AppData\Local\Temp\fungedsp8.exe
File description: Windows EXE for Trickbot
TRAFFIC
URLS FROM THE EXCEL MACROS FILES TO DOWNLOAD TRICKBOT:
- 56530006[.]com - GET /98tf77b
- 78tguyc876wwirglmltm[.]net - GET /af/98tf77b
- altisso[.]pl - GET /98tf77b
- apagmar[.]pl - GET /98tf77b
- cclimoji[.]com - GET /98tf77b
- ctinfotech[.]com - GET /98tf77b
- loantm[.]com - GET /98tf77b
- mahovik-bg[.]com - GET /98tf77b
- milchdieb[.]com - GET /98tf77b
- randomessstioprottoy[.]net - GET /af/98tf77b
- sandat-bali[.]com - GET /98tf77b
- sharuindustries[.]com - GET /98tf77b
- snnftp[.]com - GET /98tf77b
- www.montostroj[.]eu - GET /98tf77b
TRICKBOT POST-INFECTION TRAFFIC:
- port 80 - wtfismyip[.]com - GET /text - IP address check
- 186.103.161[.]204 port 443 - encrypted post-infection traffic
- 195.69.196[.]77 port 447 - encrypted post-infection traffic
- 94.140.121[.]174 port 443 - attempted TCP connections, but no response from the server
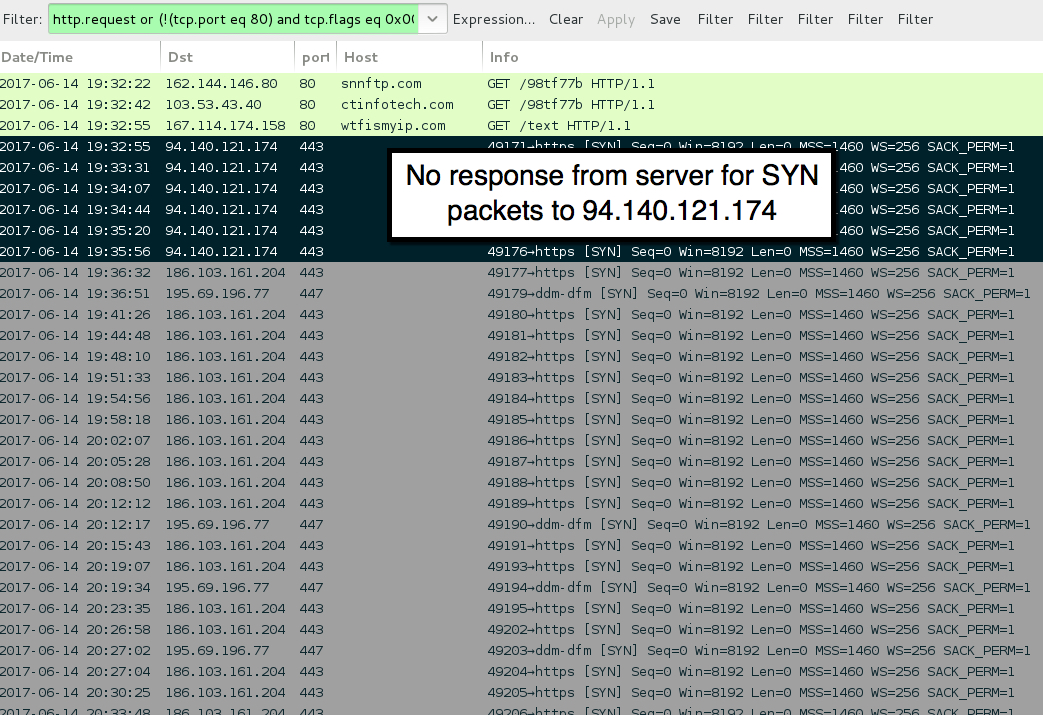
Shown above: Traffic from the infection filtered in Wireshark.
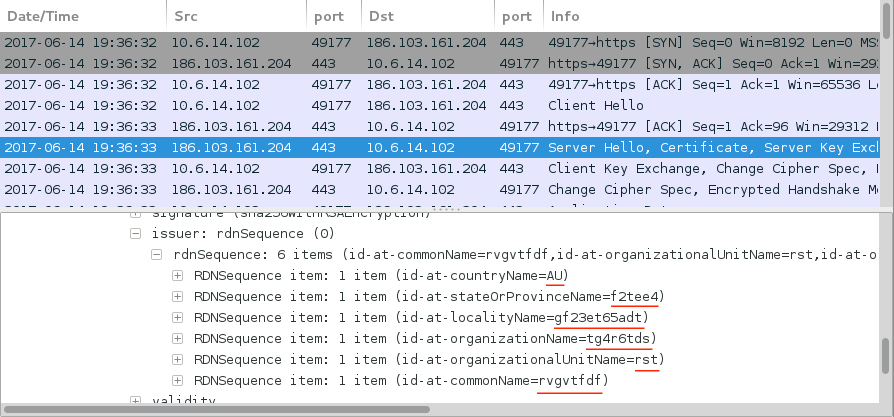
Shown above: Certificate data from traffic to 186.103.161[.]204 port 443.
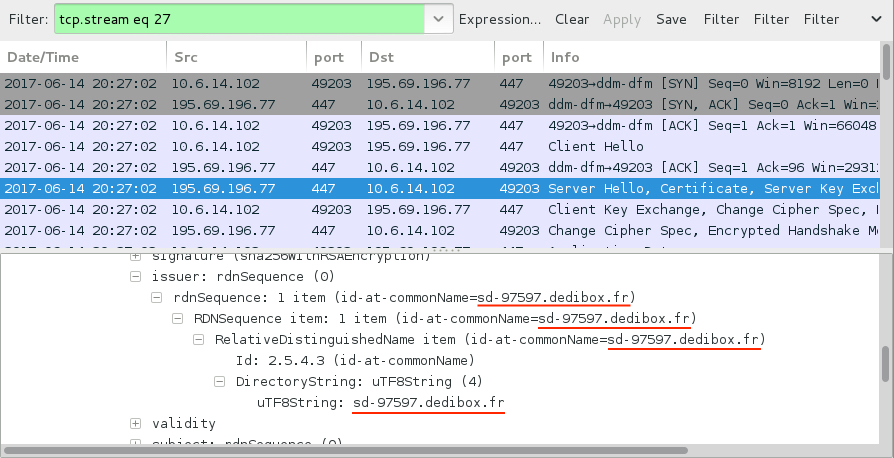
Shown above: Certificate data from traffic to 195.69.196[.]77 port 447.
IMAGES
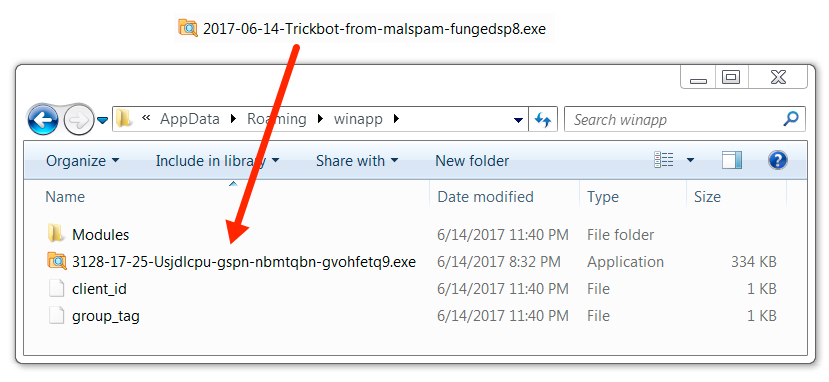
Shown above: Malware copies itself and does a ROT1 on the filename (minus the .exe file extension).
Click here to return to the main page.
