2017-07-04 - JAVA-BASED RAT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-04-Java-based-RAT-email-and-malware.zip 1.5 MB (1,506,906 bytes)
- 2017-07-04-malspam-0433-UTC.eml (946,555 bytes)
- INVOICE LIST.jar (578,829 bytes)
- _0.325390945828089142947081810060995233.class (247,088 bytes)
SCREENSHOT:
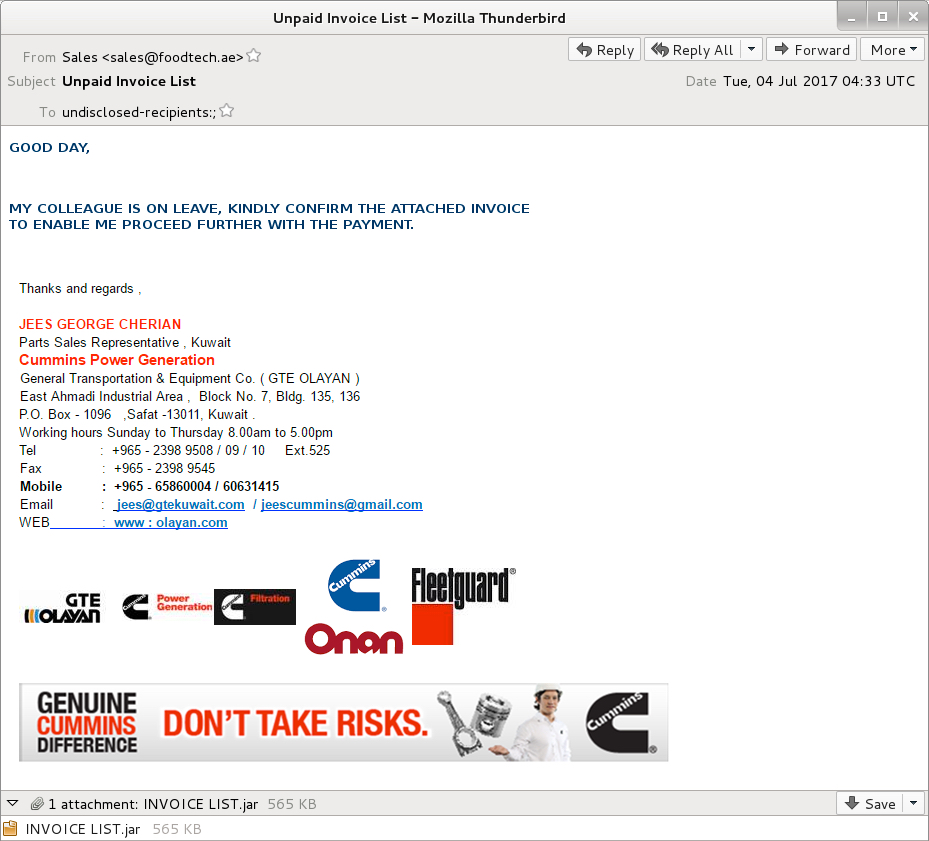
Shown above: Screenshot of the email.
EMAIL HEADER INFO:
- Received: from [162.144.89[.]147] ([162.144.89[.]147:36560] helo=server.joshmachines[.]com)
by [removed] (envelope-from <sales@foodtech[.]ae>)
[removed]; Tue, 04 Jul 2017 01:42:30 -0400 - Received: from [127.0.0.1] (port=45926 helo=harshangzaveri[.]com)
by server.joshmachines[.]com with esmtpa (Exim 4.89)
(envelope-from <sales@foodtech[.]ae>)
id 1dSFWO-0008CV-Tu; Tue, 04 Jul 2017 04:33:09 +0000
- MIME-Version: 1.0
- Date: Tue, 04 Jul 2017 04:33:08 +0000
- From: Sales <sales@foodtech[.]ae>
- To: undisclosed-recipients:;
- Subject: Unpaid Invoice List
- Reply-To: sales@foodtech[.]ae
- Mail-Reply-To: sales@foodtech[.]ae
- Message-ID: <a01dfe55b97e7efd3c75d28a9286ec40@foodtech[.]ae>
- X-Sender: sales@foodtech[.]ae
- User-Agent: Roundcube Webmail/1.2.4
- Attachment: INVOICE LIST.jar
TRAFFIC
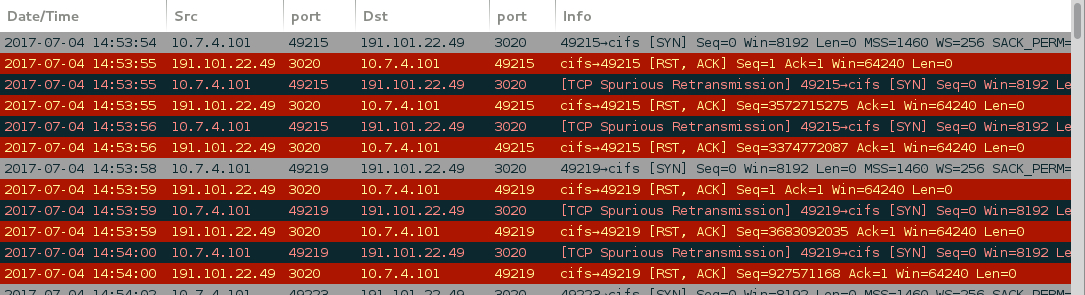
Shown above: Traffic from an infection filtered in Wireshark.
POST-INFECTION TRAFFIC:
- 191.101.22[.]49 port 3020 - attempted TCP connections, but RST from the server.
FILE HASHES
EMAIL ATTACHMENT:
- SHA256 hash: 9863c850c213dee716dc5954bb0f28a1c480cf0435e93110824cb083fd4bdda5
File name: INVOICE LIST.jar
File size: 578,829 bytes
ARTIFACT FOUND IN USER'S APPDATA\LOCAL\TEMP DIRECTORY:
- SHA256 hash: 97d585b6aff62fb4e43e7e6a5f816dcd7a14be11a88b109a9ba9e8cd4c456eb9
File name: _0.325390945828089142947081810060995233.class
File size: 247,088 bytes
IMAGES
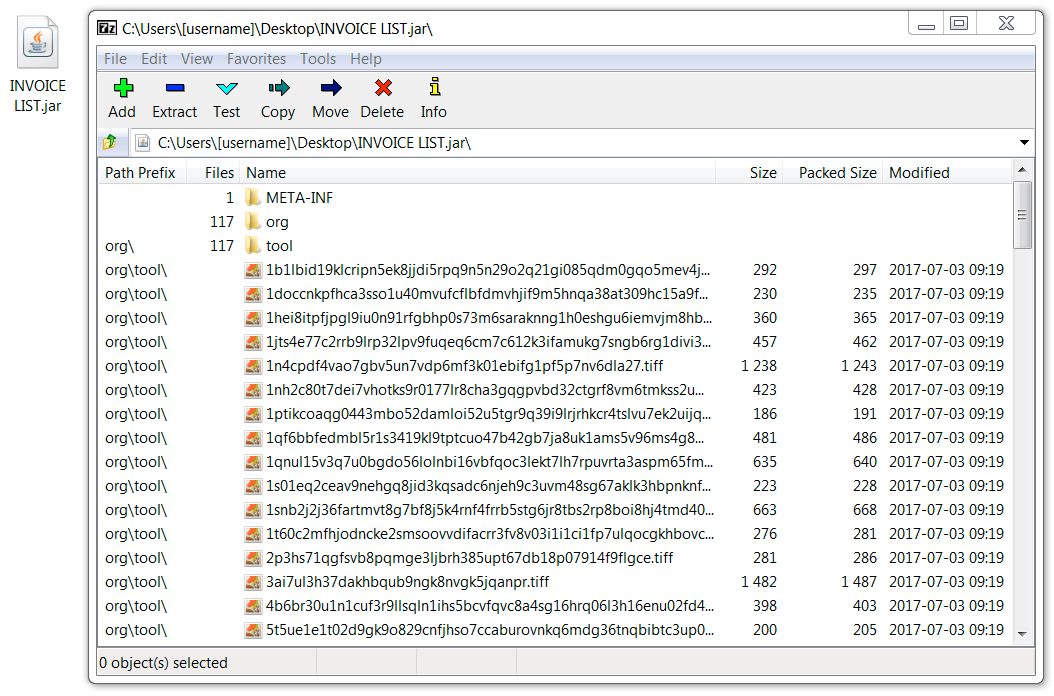
Shown above: Contents of the email attachment.
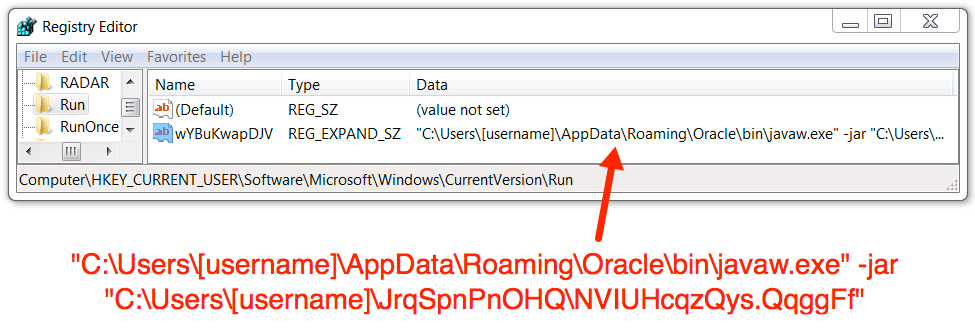
Shown above: Windows registry change to make the malware persistent after a reboot.
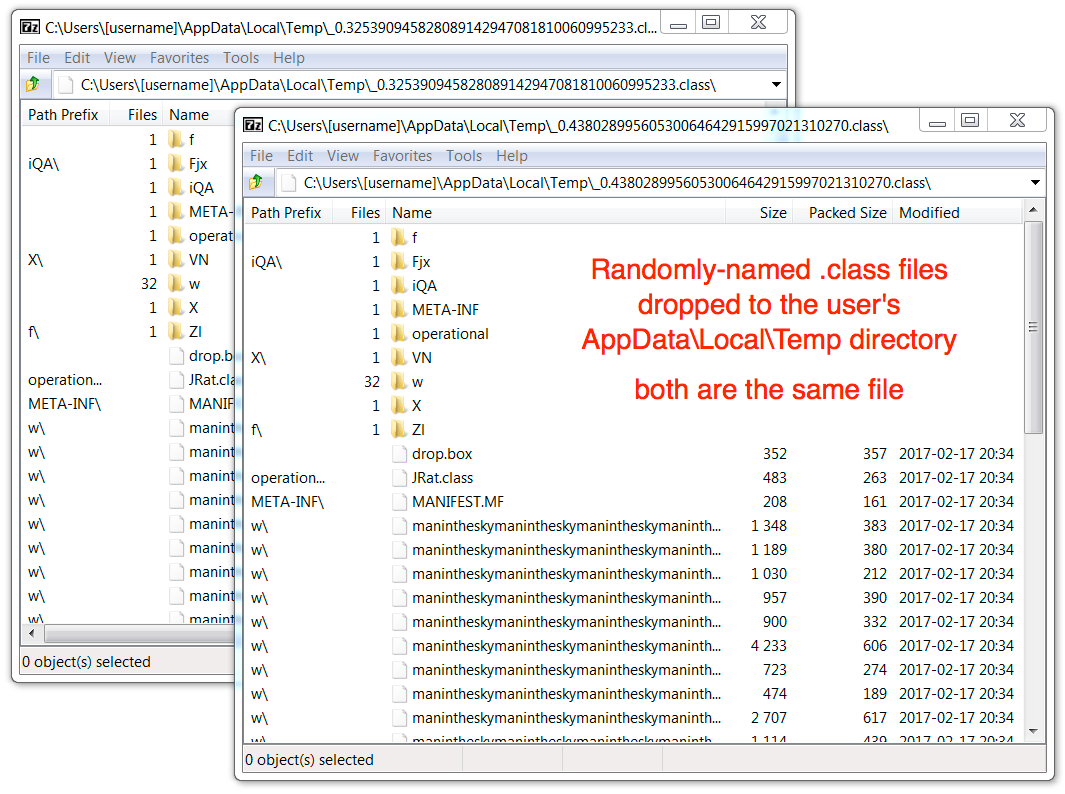
Shown above: Two .class files with the same file hash found in the user's AppData\Local\Temp directory after this infection.
Click here to return to the main page.
