2017-08-29 - TERROR EK SEEN USING HTTPS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the Fiddler capture: 2017-08-29-Terror-EK-traffic.saz.zip 118.0 kB (118,011 bytes)
- 2017-08-29-Terror-EK-traffic.saz (121,469 bytes)
- Zip archive of the artifacts: 2017-08-29-Terror-EK-artifacts.zip 105.1 kB (105,132 bytes)
- 2017-08-29-Terror-EK-3Np2K9XwEp3C.txt (4,641 bytes)
- 2017-08-29-Terror-EK-8EUj3DVsJ3l6.txt (64,126 bytes)
- 2017-08-29-Terror-EK-QMxBnqBlgl4e.txt (11,582 bytes)
- 2017-08-29-Terror-EK-TyIPdwZ096Uf.swf (24,667 bytes)
- 2017-08-29-Terror-EK-Uhg2F49WHwXu.txt (12,638 bytes)
- 2017-08-29-Terror-EK-cZV9AQd9UyjN.txt (8,209 bytes)
- 2017-08-29-Terror-EK-mESH7HMjAcFA.swf (51,139 bytes)
- 2017-08-29-Terror-EK-showthread-php-id-7991937328.txt (4,938 bytes)
NOTES:
- Saw a "404 not found" in response to the URL requesting the payload.
- Thanks to @nao_sec, who saw this EK using HTTPS earlier today and let me know. Otherwise, I might not have noticed.
- Also thanks to @jeromesegura, who corrected me when I initially thought this was Disdain EK. (Disdain EK stole from Terror EK, but it's not Terror EK.)
TRAFFIC
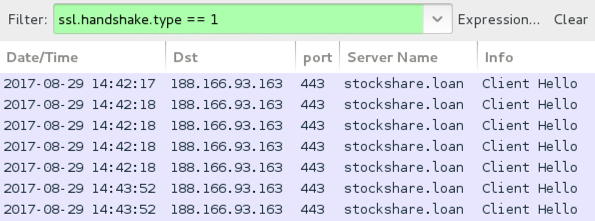
Shown above: Traffic from Terror EK on 2017-08-29 filtered in Wireshark.
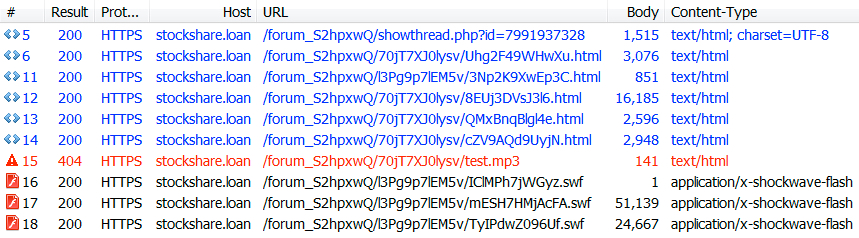
Shown above: Traffic from Terror EK on 2017-08-29 as recorded through Fiddler.
ASSOCIATED URLS:
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/showthread.php?id=7991937328
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/70jT7XJ0lysv/Uhg2F49WHwXu.html
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/l3Pg9p7lEM5v/3Np2K9XwEp3C.html
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/70jT7XJ0lysv/8EUj3DVsJ3l6.html
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/70jT7XJ0lysv/QMxBnqBlgl4e.html
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/70jT7XJ0lysv/cZV9AQd9UyjN.html
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/70jT7XJ0lysv/test.mp3
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/l3Pg9p7lEM5v/IClMPh7jWGyz.swf
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/l3Pg9p7lEM5v/mESH7HMjAcFA.swf
- 188.166.93[.]163 port 443 (HTTPS) - stockshare[.]loan - GET /forum_S2hpxwQ/l3Pg9p7lEM5v/TyIPdwZ096Uf.swf
FILE HASHES
TERROR EK FLASH EXPLOIT (1 OF 2):
- SHA256 hash: 0dbb15afb887069b2f75308d2cff947db56d08adf8ceb17bb39ccdc71db28db3
File size: 51,139 bytes
File description: Flash exploit used by Terror EK on 2017-08-29
TERROR EK FLASH EXPLOIT (2 OF 2):
- SHA256 hash: 7ff9703ac519fa05d323e032b16b2b55cbaf8e1f51d1e89a0a337c4125aebe97
File size: 24,667 bytes
File description: Another Flash exploit used by Terror EK on 2017-08-29
Click here to return to the main page.
