2018-01-10 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-10-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.2 MB (2,150,270 bytes)
- 2018-01-10-Hancitor-malspam-9-examples.txt.zip 6.4 kB (6,438 bytes)
- 2018-01-10-malware-from-Hancitor-infection.zip 244.3 kB (244,267 bytes)
NOTES:
- Hancitor malspam is back from the holiday break!
- As usual, post-infection malware from Hancitor malspam includes the Zeus Panda banking Trojan.
- There's still Pony and Evil Pony (both file-less) also downloaded by Hancitor from the Word document macro.
- @James_inthe_box (link) and @MalwareBlueTeam (link) documented additional indicators that I've also included here in this blog post.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- chillionairenation[.]com
- chillionista[.]com
- frankisaac[.]net
- frankisaacjewelers[.]com
- giveaway.systems
- grapeleafcafe[.]com
- janmariejackson[.]com
- karymurdaneta[.]com
- melissamontalvo[.]com
- mindmastersalliance[.]com
- roadmastergroup[.]mobi
- roadmastergroup[.]net
- thechillionaireretreat[.]com
- thechillionairezone[.]com
- toxinfreeclub[.]com
- underwoodnurseryllc[.]com
- hxxp[:]//cantelco[.]net/wp-content/plugins/simple-map/11
- hxxp[:]//cantelco[.]net/wp-content/plugins/simple-map/22
- hxxp[:]//cantelco[.]net/wp-content/plugins/simple-map/3
- hxxp[:]//dpadistribuidora[.]com[.]br/wp-content/plugins/favicon-xt-manager/11
- hxxp[:]//dpadistribuidora[.]com[.]br/wp-content/plugins/favicon-xt-manager/22
- hxxp[:]//dpadistribuidora[.]com[.]br/wp-content/plugins/favicon-xt-manager/3
- hxxp[:]//expatrions-nous[.]com/wp-content/plugins/ultimate-wp-cache/11
- hxxp[:]//expatrions-nous[.]com/wp-content/plugins/ultimate-wp-cache/22
- hxxp[:]//expatrions-nous[.]com/wp-content/plugins/ultimate-wp-cache/3
- hxxp[:]//ricecitysonghong[.]com/wp-content/plugins/google-sitemap-plugin/includes/11
- hxxp[:]//ricecitysonghong[.]com/wp-content/plugins/google-sitemap-plugin/includes/22
- hxxp[:]//ricecitysonghong[.]com/wp-content/plugins/google-sitemap-plugin/includes/3
- hxxp[:]//tierspende[.]org/wp-content/themes/twentyfourteen/11
- hxxp[:]//tierspende[.]org/wp-content/themes/twentyfourteen/22
- hxxp[:]//tierspende[.]org/wp-content/themes/twentyfourteen/3
- henrenbilac[.]ru
- unhesrowrab[.]com
- disithedtse[.]com
EMAILS
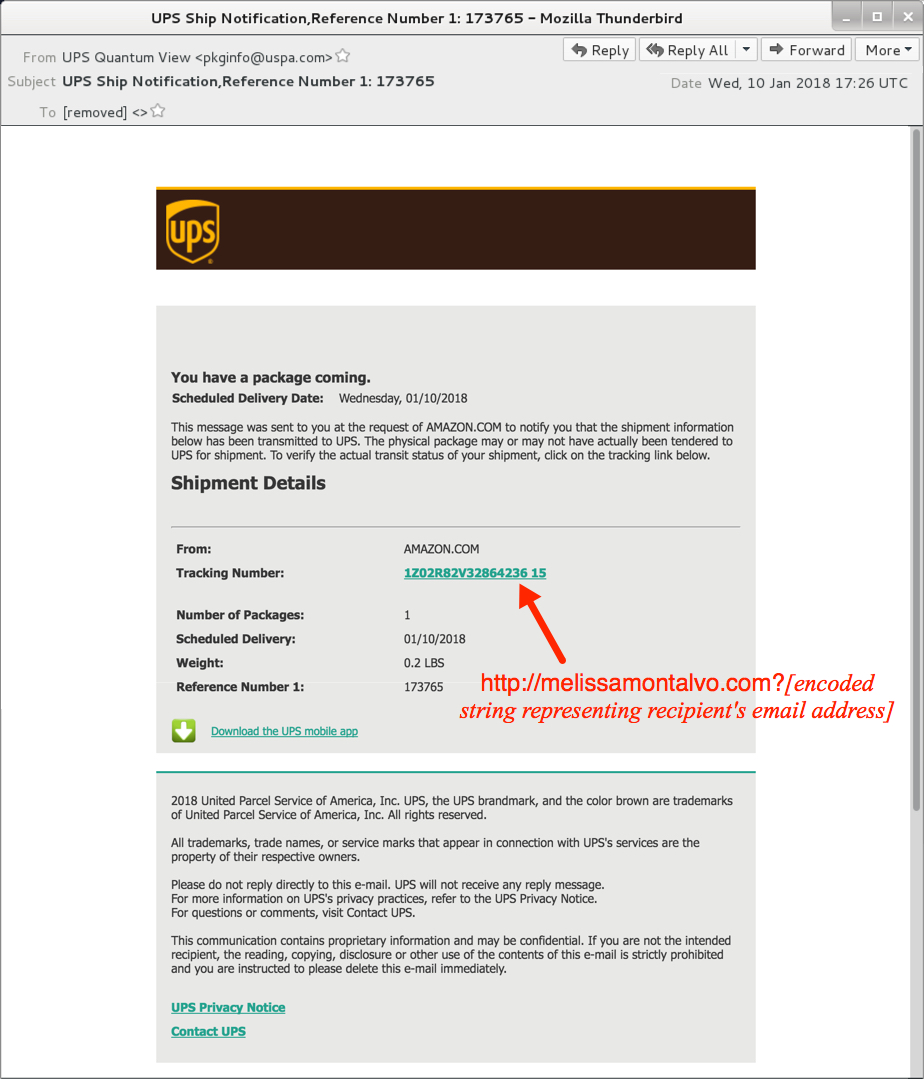
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2018-01-10 as early as 15:53 through at least 17:36 UTC
- Subject: UPS Ship Notification,Reference Number 1: 173765
- Subject: UPS Ship Notification,Reference Number 1: 207828
- Subject: UPS Ship Notification,Reference Number 1: 435037
- Subject: UPS Ship Notification,Reference Number 1: 515863
- Subject: UPS Ship Notification,Reference Number 1: 627164
- Subject: UPS Ship Notification,Reference Number 1: 652012
- Subject: UPS Ship Notification,Reference Number 1: 782653
- Subject: UPS Ship Notification,Reference Number 1: 844017
- Subject: UPS Ship Notification,Reference Number 1: 872177
- Received: from uspa[.]com ([24.151.24[.]40])
- Received: from uspa[.]com ([50.207.113[.]250])
- Received: from uspa[.]com ([50.250.168[.]165])
- Received: from uspa[.]com ([50.253.70[.]82])
- Received: from uspa[.]com ([66.11.73[.]209])
- Received: from uspa[.]com ([72.68.134[.]154])
- Received: from uspa[.]com ([188.39.111[.]250])
- Received: from uspa[.]com ([213.120.121[.]78])
- From (spoofed): "UPS Quantum View" <pkginfo@uspa[.]com>
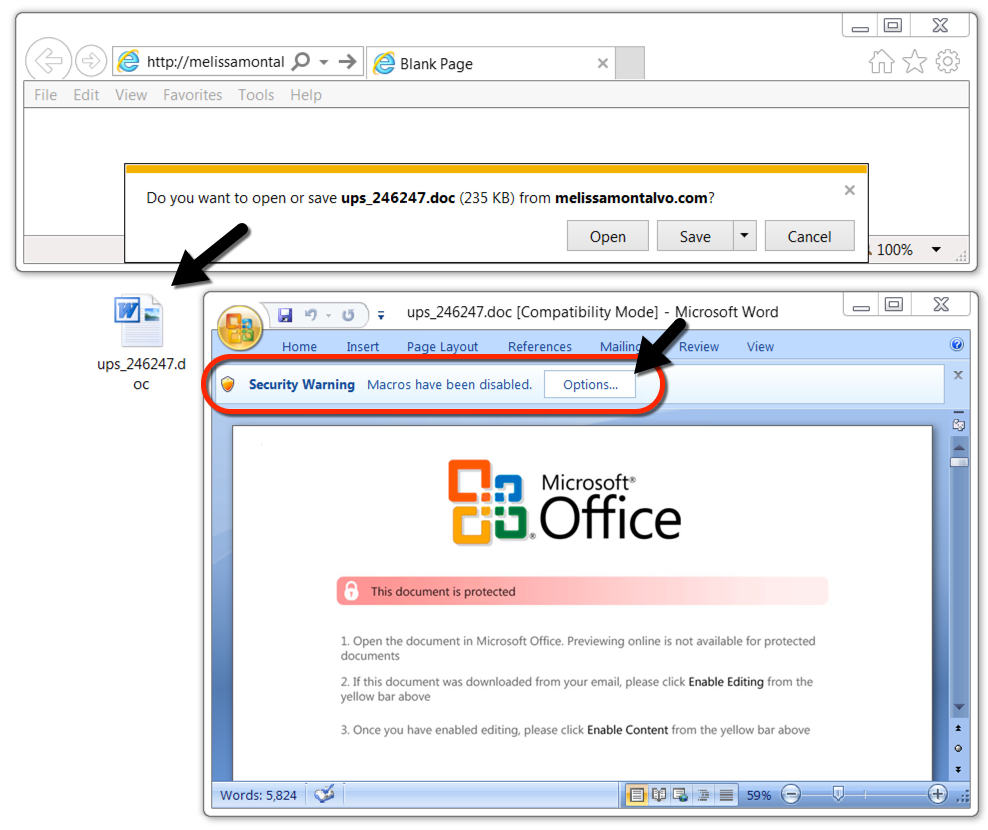
Shown above: Malicious Word document downloaded from a link in the malspam.
TRAFFIC
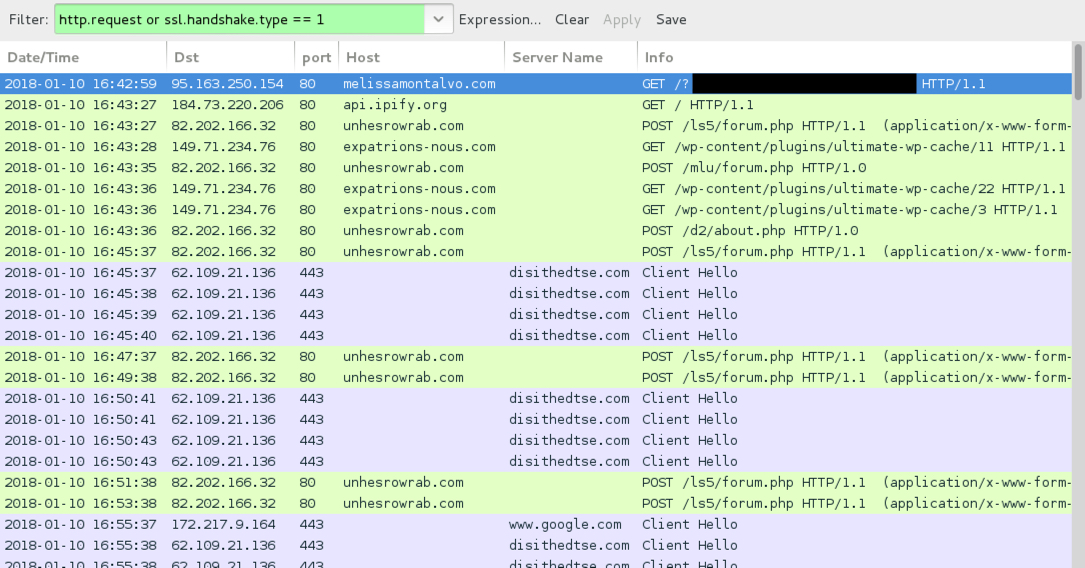
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//chillionista[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//janmariejackson[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//karymurdaneta[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//melissamontalvo[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//roadmastergroup[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//thechillionairezone[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//toxinfreeclub[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 95.163.250[.]154 port 80 - melissamontalvo[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- api.ipify[.]org - GET /
- 82.202.166[.]32 port 80 - unhesrowrab[.]com - POST /ls5/forum.php
- 82.202.166[.]32 port 80 - unhesrowrab[.]com - POST /mlu/forum.php
- 82.202.166[.]32 port 80 - unhesrowrab[.]com - POST /d2/about.php
- 149.71.234[.]76 port 80 - expatrions-nous[.]com - GET /wp-content/plugins/ultimate-wp-cache/11
- 149.71.234[.]76 port 80 - expatrions-nous[.]com - GET /wp-content/plugins/ultimate-wp-cache/22
- 149.71.234[.]76 port 80 - expatrions-nous[.]com - GET /wp-content/plugins/ultimate-wp-cache/3
- 62.109.21[.]136 port 443 - disithedtse[.]com - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- www.google[.]com - HTTPS traffic, probably a connectivity check by infected Windows host
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 85d2ba3f12877bf7e531ec1970909f2ea20f55ba17d27f4a5b65e8e8dc493909
File size: 240,640 bytes
File name: ups_[6 random digits].doc
File description: Word document with macro for Hancitor
- SHA256 hash: a63a22c351534a42d6b9c66988103589a12c5be6eaa209b8b301c524f756cf99
File size: 174,592 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
IMAGES
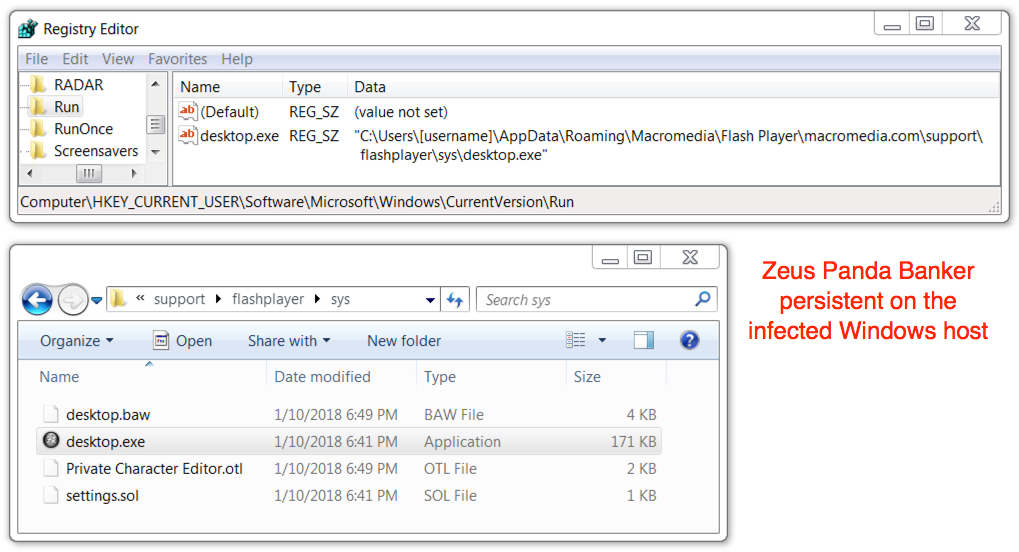
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.
