2018-01-11 - RIG EK SENDS SMOKELOADER (SHARIK/DOFOIL) AND MONERO COIN MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2018-01-11-Rig-EK-sends-SmokeLoader-and-Monero-coin-miner.pcap.zip 2.8 MB (2,798,647 bytes)
- Zip archive of the malware and artifacts: 2018-01-11-Rig-EK-and-SmokeLoader-and-Monero-malware.zip 931.1 kB (931,093 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain and URL:
- saumottam[.]ru
- hxxp[:]//104.236.16[.]69/bprocess.exe
EMAILS
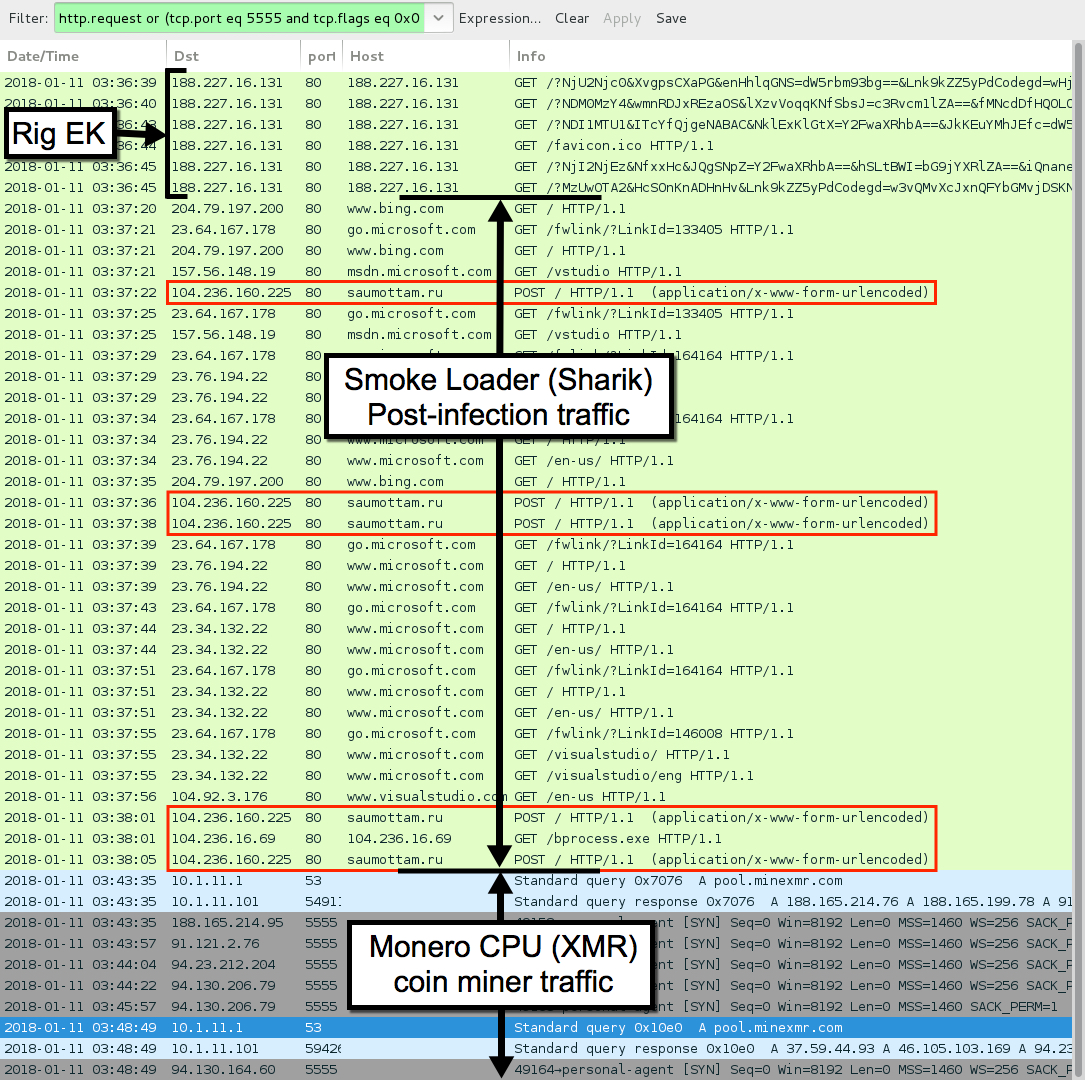
Shown above: Traffic from the infection filtered in Wireshark.
RIG EK:
- 188.227.16[.]131 port 80 - 188.227.16[.]131
URLS TO NON-MALICIOUS DOMAINS GENERATED BY SMOKELOADER (SHARIK/DOFOIL):
- www.bing[.]com - GET /
- go.microsoft[.]com - GET /fwlink/?LinkId=133405
- msdn.microsoft[.]com - GET /vstudio
- msdn.microsoft[.]com - GET /vstudio
- www.microsoft[.]com - GET /en-us/
- www.microsoft[.]com - GET /visualstudio/eng
- www.visualstudio[.]com - GET /en-us
URLS TO MALICIOUS DOMAINS GENERATED BY SMOKELOADER (SHARIK/DOFOIL):
- 104.236.160[.]225 port 80 - saumottam[.]ru - POST /
- 104.236.16[.]69 port 80 - 104.236.16[.]69 - GET /bprocess.exe
MONERO (XMR) COIN MINER ACTIVITY:
- DNS queries for pool.minexmr[.]com
- 91.121.2[.]76 port 5555
- 94.23.212[.]204 port 5555
- 94.130.164[.]60 port 5555
- 94.130.206[.]79 port 5555
- 188.165.214[.]95 port 5555
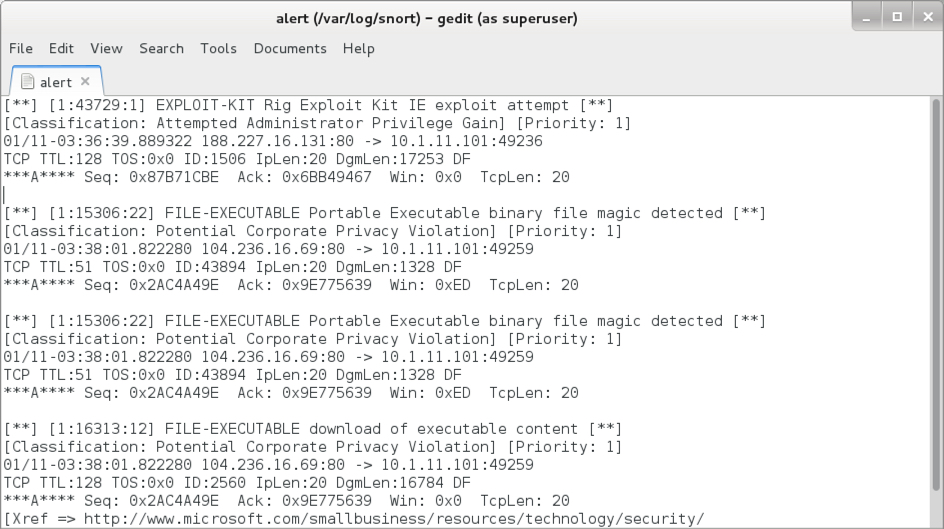
Shown above: Some alerts on the infection traffic from the Snort subscriber ruleset when reading the pcap with Snort 2.9.11.
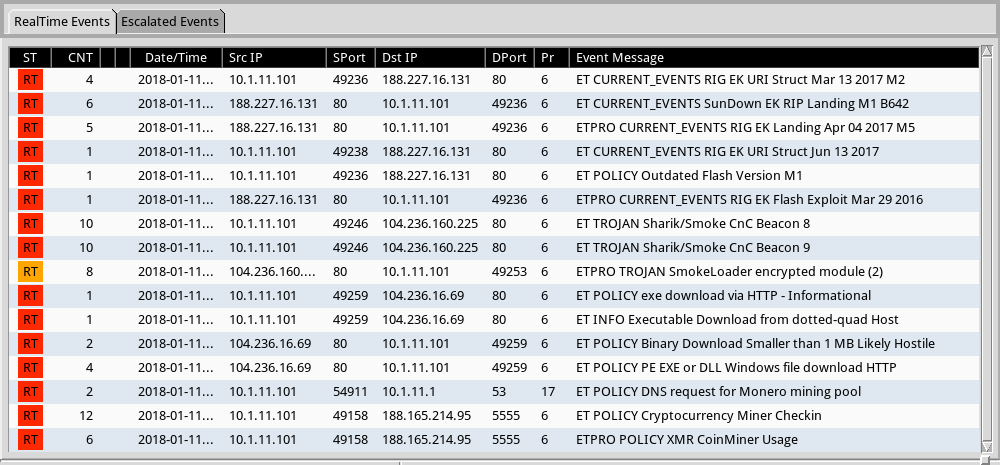
Shown above: Some alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
FILE HASHES
RIG EK FLASH EXPLOIT SEEN ON 2018-01-11:
- SHA256 hash: 535d02392f19fccc890133bc044fe17ef31500e17045c72458482e07b9aa37db
File size: 13,894 bytes
RIG EK PAYLOAD - SMOKELOADER (ALSO CALLED "SHARIK" OR "DOFOIL"):
- SHA256 hash: 178c444a11eab39295d8382a7f4e5814c491bd21d216df3ee04213116b118619
File size: 108,009 bytes
FOLLOW-UP MALWARE - MONERO (XMR) COIN MINER:
- SHA256 hash: f9c67313230bfc45ba8ffe5e6abeb8b7dc2eddc99c9cebc111fcd7c50d11dc80
File size: 828,929 bytes
Click here to return to the main page.
