2018-07-05 - TRICKBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-05-Trickbot-malspam-example.eml.zip 70.7 kB (70,736 bytes)
- 2018-07-05-Trickbot-infection-traffic.pcap.zip 16.5 MB (16,450,278 bytes)
- 2018-07-05-malware-from-Trickbot-infection.zip 613 kB (612,962 bytes)
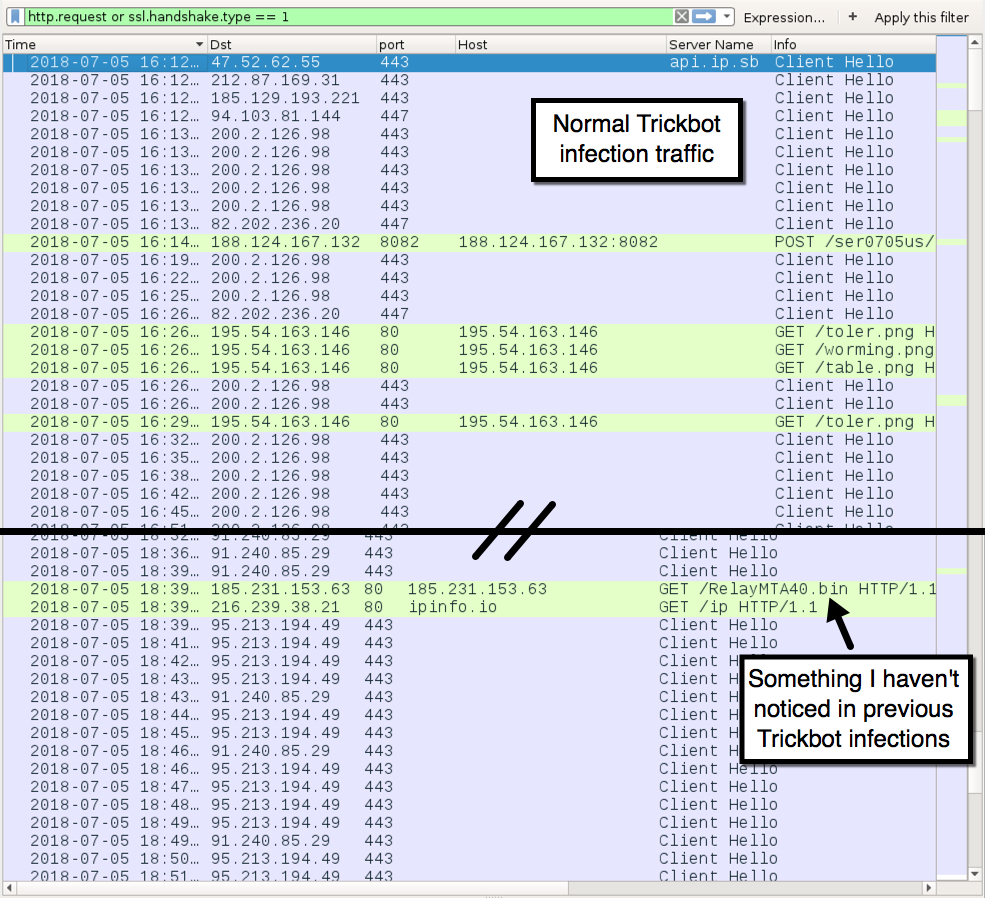
Shown above: Traffic from an infection filtered in Wireshark.
MALSPAM EXAMPLE: - Received: from unknown (HELO irsinvoice[.]com) ([95.211.148[.]193]) - Sender (spoofed): "IRS" <James.Broom@irsinvoice[.]com> - Date: Thursday, 2018-07-05 at 14:38 UTC - Subject: FW: Invoice - Attachment name: Invoice.doc DOWNLOAD LINKS USED BY MACRO FROM ATTACHED WORD DOC (NOT ACTIVE WHEN I LAST CHECKED): - hxxp[:]//theneonblonde[.]com/hu.hu - hxxp[:]//adultacnetreatmentreviews[.]com/hu.hu INFECTION TRAFFIC: - port 443 - api.ip.sb - IP address check over HTTPS by Trickbot-infected Windows host - 212.87.169[.]31 port 443 - SSL/TLS traffic - 185.129.193[.]221 port 443 - SSL/TLS traffic - 94.103.81[.]144 port 447 - SSL/TLS traffic - 200.2.126[.]98 port 443 - SSL/TLS traffic - 82.202.236[.]20 port 447 - SSL/TLS traffic - 188.124.167[.]132 port 8082 - 188.124.167[.]132:8082 - POST /ser0705us/[long string] - 195.54.163[.]146 port 80 - 195.54.163[.]146 - GET /toler.png - 195.54.163[.]146 port 80 - 195.54.163[.]146 - GET /worming.png - 195.54.163[.]146 port 80 - 195.54.163[.]146 - GET /table.png - 91.240.85[.]29 port 443 - SSL/TLS traffic - 185.231.153[.]63 port 80 - 185.231.153[.]63 - GET /RelayMTA40.bin - TCP connection to gmail-smtp-in.l.google[.]com, but it was immediately FIN-ed - port 80 - ipinfo[.]io - GET /ip - IP address check by Trickbot-infected Windows host - 95.213.194[.]49 port 443 - SSL/TLS traffic ASSOCIATED MALWARE MALWARE: - SHA256 hash: c3aa90539e8f86c7372a97c0ef2f2988c0199292209e4ee1ebceaaffd0a6b9a9 - File size: 89,088 bytes - Description: Attached Word doc with macro for Trickbot - SHA256 hash: 85f41612517a7e60582b9ee98f71a88203cd8941a31bc2d34ab5f42f89ee72e7 - File size: 273,408 bytes - Description: Trickbot malware binary downloaded by Word macro - SHA256 hash: 50bfe10f9d6685610b6453017fb6f58fe8b2efe287e55c5b95f8603775645006 - File size: 323,584 bytes - Description: Trickbot follow-up downloads (table.png, toler.png, and worming.png) - SHA256 hash: 5a554aa3bfcfec68948d3f4b4fcafbbfbce75e473eba1b28557373717f3941e6 - File size: 44,544 bytes - Description: Trickbot follow-up download (RelayMTA40.bin)
Click here to return to the main page.
