2013-06-18 - NEUTRINO EK FROM 199.195.249[.]188 - 1208B83B81C141ECD6F05E24.WEBHOP[.]ORG:8000
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
PCAP AND MALWARE:
- Zip archive of the pcap: 2013-06-18-Neutrino-EK-traffic.pcap.zip 117 kB (117,019 bytes)
- ZIP archive of the malware: 2013-06-18-Neutrino-EK-malware.zip 74.6 kB (74,590 bytes)
NOTES:
- This was my first blog entry, back when I began documenting exploit kit (EK) traffic, and I didn't realize this was Neutrino EK.
- The malware payload was obfusated, XOR-ed with the ASCII string: nylhvw (something I hadn't figured out yet).
- This pcap is dated 2013-06-19 in UTC, which was 2013-06-18 Central time in the US (which is why this blog entry is dated 2013-06-18).
- On 2014-09-20, I updated this blog entry with more information, and changed the format to how I now report on EK traffic.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- [information redacted] - Compromised website
- 173.247.253[.]210:80 - www.insightcrime[.]org - malicious javascript pointing to Neutrino gate
- 93.171.172[.]220 - 93.171.172[.]220 - Neutrino gate
- 199.195.249[.]188 - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - Neutrino EK
INFECTION TRAFFIC:
- 00:25:23 UTC - www.insightcrime[.]org - GET /media/system/js/jquery-1.6.5.min.js
- 00:25:23 UTC - 93.171.172[.]220 - GET /?1
- 00:25:24 UTC - 93.171.172[.]220 - GET /?2
- 00:25:24 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /aotyprvqvj?hash=6a4c601e0802b403736ff29f3ceaa7c0&qspot=4012736
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /zbtsnshkxph.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /lllpy.css
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /gzfkzixuudb.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /vctvkgszlijgkz.css
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /mfgvlykftmyoxe.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /aimwofqjubqlvuzy.css
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /gmjgrxnqdx.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /mvkhymxmmyg.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /scripts/js/plg.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /ynxvcejiqt.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /ircyuaohvzo.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /pznggodm.css
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /urdacn.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /wqqfwaf.js
- 00:25:25 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /jvjskjfrp.css
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /mgylmdxkq.png
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /szqbqjq.png
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /txvu.jpg
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /plrjx.gif
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /obzmmphsihjjxs.gif
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /tutoogrerinpmdl.gif
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /koqavj.gif
- 00:25:26 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - POST /boezkexoxrlbjwxii
- 00:25:30 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /cbsthcfq?mimsrws=nshbdaiqnay
- 00:25:30 UTC - 1208b83b81c141ecd6f05e24.webhop[.]org:8000 - GET /drddbg?mebhqtwycgg=nshbdaiqnay
PRELIMINARY MALWARE ANALYSIS:
JAVA EXPLOIT:
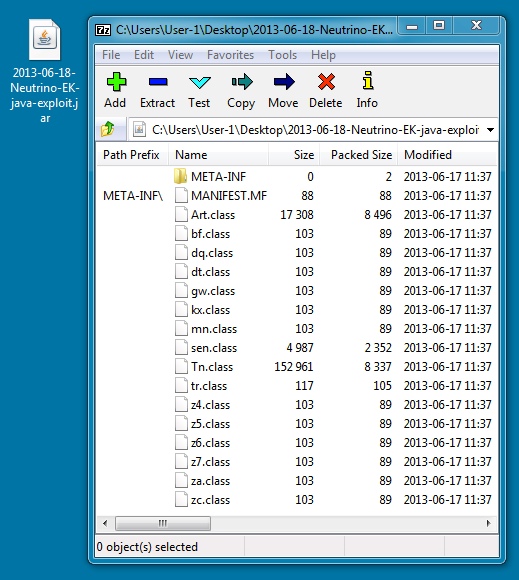
File name: 2013-06-18-Neutrino-EK-java-exploit.jar
File size: 21.9 KB ( 22452 bytes )
MD5 hash: 19d60c47854e35aa5aae8a5fe77ba11a
Detection ratio: 15 / 54
First submission: 2013-06-18 19:14:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/4cda1350264757b684e73f00f0a616384e83a675deb9bbc3d9f41325e3a5b5a1/analysis/
MALWARE PAYLOAD:
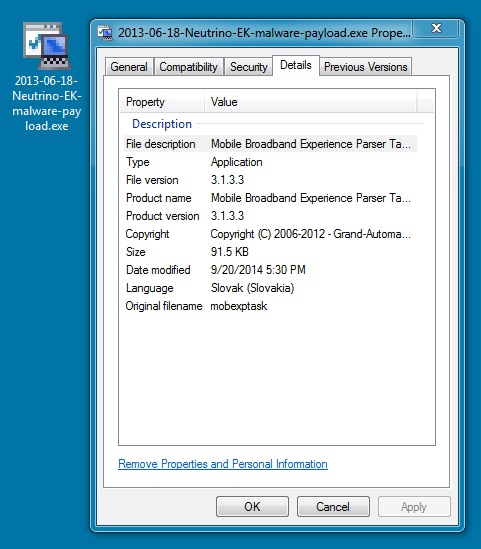
File name: 2013-06-18-Neutrino-EK-malware-payload.exe
File size: 91.5 KB ( 93696 bytes )
MD5 hash: 2dc3fbd737281eb93f1df205d12a69e0
Detection ratio: 39 / 52
First submission: 2013-06-18 22:39:00 UTC
VirusTotal link: https://www.virustotal.com/en/file/a8dafaa2bd5a43fb44b5c626f72bbc969cc6e4a28cbf0d1a0417173b06e83dab/analysis/
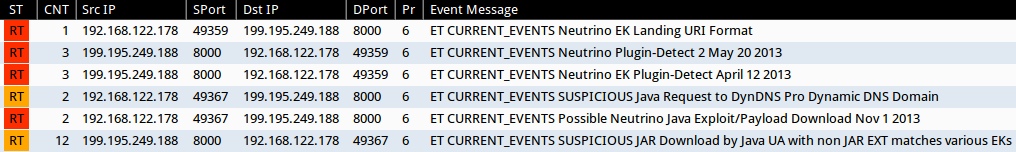
ALERTS
Screenshot of Emerging Threats signature hits from Sguil on Security Onion (without ET POLICY or ET INFO events):
FINAL NOTES
Once again, here's the pcap of the traffic and zip archive of the malware:
- Zip archive of the pcap: 2013-06-18-Neutrino-EK-traffic.pcap.zip 117 kB (117,019 bytes)
- ZIP archive of the malware: 2013-06-18-Neutrino-EK-malware.zip 74.6 kB (74,590 bytes)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
Click here to return to the main page.