2013-08-31 - ANDROID APPS
In reviewing alerts from an IDS, the majority of the events will be false positives--network traffic that triggers events, but it's not actually malicious. I occasionally see false positives on signatures for Windows-based malware that are triggered by traffic from iPhones or Android devices.
A few weeks back, while reviewing some random Snort-based events, I ran across an HTTP POST requests to cashort.weixin.qq[.]com from an Android phone. Curious about this, I investigated further. Although it was a false positive for malware, the results provide some good insight for a blog post.
Keep in mind this is not malware. As far as I know, it's a legitimate app. If you're curious about traffic seen when installing a normal Android app, read on...
TRAFFIC DETAILS
Let's review what network traffic looks like when someone downloads and installs an app from Google's official Android marketplace, play.google[.]com.
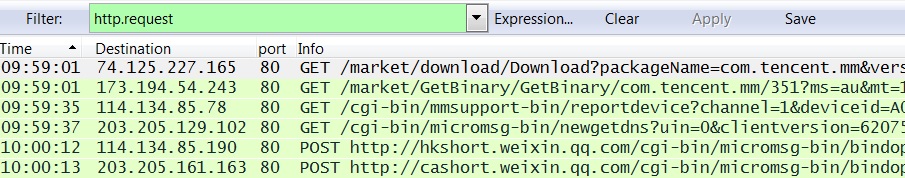
I installed the app responsible for the traffic to cashort.weixin.qq[.]com to a Nexus 4 Android phone that had been reset to factory default settings. With Wireshark monitoring a wireless access point, I recorded the traffic and the results are shown below (filtered to http.request):
The initial HTTP GET request for the app is in the first line:
GET /market/download/Download?packageName=com.tencent[.]mm&versionCode=351&token=[a long string of characters follows]
The package name for the app is com.tencent[.]mm. A quick Google search shows this app is known as "WeChat".
Now you can find out more about WeChat on Google Play.
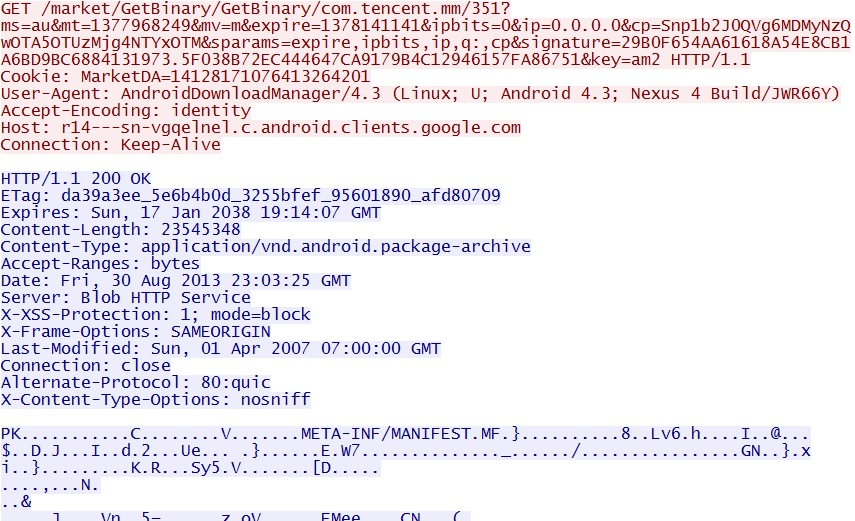
According to Google Play, WeChat provides "Free texting, voice messages, and video calls" that will work on "your phone's existing data plan or any WiFi connection." Here's what the HTTP GET request looks like when getting the actual binary:
Note the User-Agent will show the Android version, and it will usually have the model number of the device. Android apps are packaged as .APK files (Android package archive) which starts with a PK in the TCP stream like you would see with .JAR files (Java archive), .ZIP files, and maybe some other types of archives.
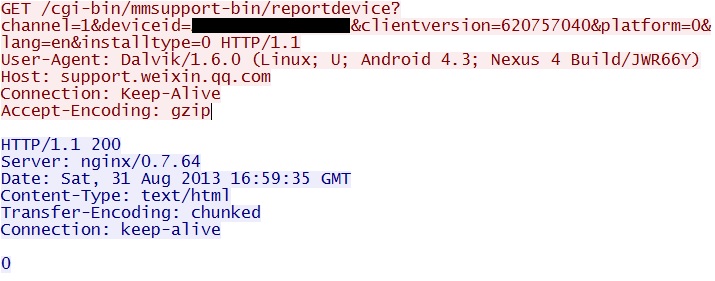
After the app is installed, the device reports some information to support.weixin.qq[.]com as shown below:
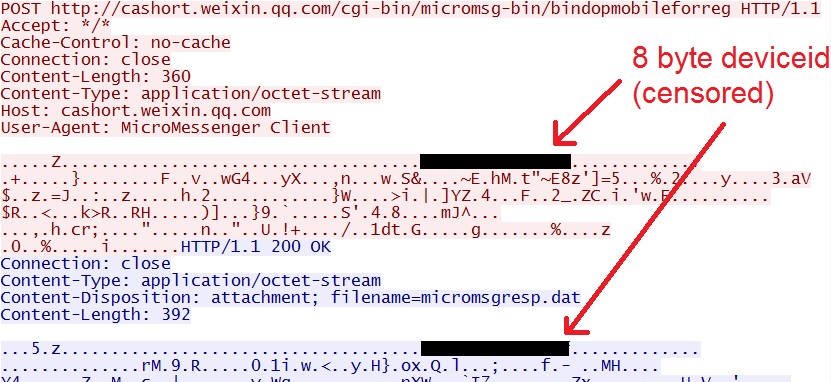
I'm not sure what the deviceid is in the above image. From what I can tell, it's not the IMEI, serial number, Wi-Fi MAC address, or based on the host name. It's an 8-byte string of hex, which I've censored in the image.
The next HTTP GET request shows the User-Agent as MicroMessenger Client.
We see two HTTP POST requests that may be registering the deviceid. One is to cashort.weixin.qq[.]com and the other this to hkshort.weixin.qq[.]com.
Finally, we see some traffic on port 8080 to 203.205.166[.]148, which is registered to Tencent (the company that makes the app).