2013-09-14 - EXAMINING TORRENT TRAFFIC
Although it isn't malware, torrenting falls under policy violations that a network traffic analyst occasionally need to investigate. If someone is torrenting on your organization's network, you should be able to investigate the network traffic and hopefully find out who it is.
Any organization has two big reasons that policy might prohibit torrent traffic on the organization's network. First, when you run a torrent client on a company's network, the torrent client normally shares any downloaded content with people all over the Internet, and you are using company resources. Second, this becomes a legal issue if someone has copyright-protected content that's being shared by the torrent client.
Other times, people use intentionally search for and illegally download copyright-protected content using bittorrent over on an organization's network, which may bring legal notices from representative of media companies.
SNORT EVENTS ON TORRENT TRAFFIC
Using Security Onion, I monitored a Windows host that installed two different torrent clients: qBitTorrent and uTorrent. I used the torrent clients to download ISO files of freely-available Linux distros, so I wasn't breaking the law. The following image shows the type of Torrent-related Snort events you might find:
EXAMINING TORRENT TRAFFIC IN WIRESHARK
PCAP files of network traffic with people actively torrenting can be somewhat large. However, you can easily filter traffic to find any torrent hashes of the files being downloaded or shared. Just use bittorrent.info_hash as a search filter, then you can easily use Wireshark's tree view to find the torrent hash as seen in the image below.
The first 8 bytes after the torrent hash indicate the torrent client that's being used. In this image below, M7-8-1-- is what we see when using the regular BitTorrent client for Windows.
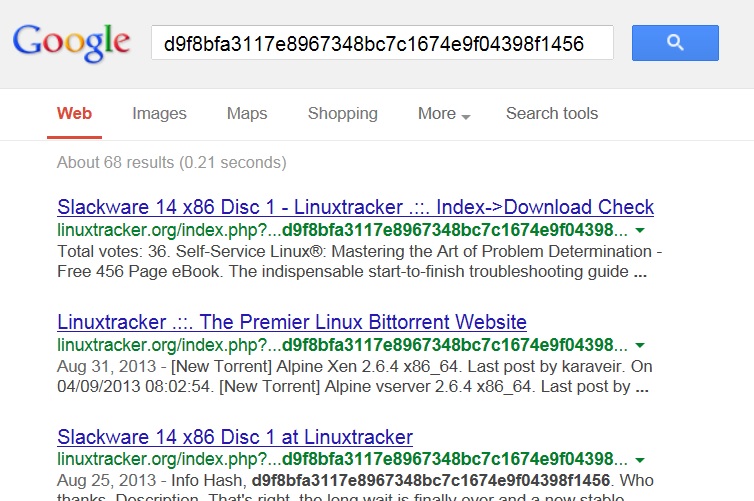
A Google search on the torrent hash will often tell you what the file is. In the tree view, select the line labeled "SHA1 Hash of info directory" and copy the value as shown below.
You'll have colons between every two bytes, so you'll need to remove those to search for the torrent hash on Google or any other search engine. The torrent hash from this traffic is for an ISO of Slackware as shown below:
I tried torrenting a different Linux ISO using another torrent client, which was uTorrent for Windows, version 3.3.1. The image below shows what the first 8 bytes of the Peer ID looks like on this machine.
If you cannot determine the torrent client in this fashion, you might be able to find some torrent scrape or torrent announce requests over HTTP by a torrent tracker. Use (torrent contains scrape or torrent contains announce) and http.request as a filter in Wirshark to check if there's any torrent tracker HTTP with a scrape or an announce. In the example below, we see both a scrape and an announce over HTTP hitting torrent.ubuntu.com over port 6969. In the tree view, we can expand the line with the HTTP GET request and find the user-agent. This confirms the torrent client is uTorrent 3.1.1.
FINAL NOTES
There's a great deal more to cover when investigating torrent traffic. This blog entry only shows how to find what's being shared (or downloaded) and what the torrent client is. At this point, you can determine the IP address, the file (or files) present in the torrent traffic, and the torrent client that's being used.
Next week, I'll cover some methods to determine who the user is and what the host might be. It's an important aspect of investigating Snort events that also applies to malware traffic, since you'll want to find out who got their computer infected.