2013-09-21 - IDENTIFYING A HOST ON THE NETWORK
If your investigation of an IDS event reveals that a computer is infected, you'll need to find the host and remove it from the network. In many cases, if you're looking at an IDS, you'll only have an IP address to identify the host name with. If you're using Security Onion to monitor the network, you'll find pcap files of the traffic in the following directory:
/nsm/sensor_data/HOSTNAME-INTERFACE/dailylogs/
If you have PCAP files of the network traffic, you may be able to find the host name. You might also discover who the user is.
HOST NAME
For infected machines, we're probably talking about a Windows host. Regardless of the type of host, it will likely use DHCP to get an IP address on the network. If you're lucky, you might find some DHCP traffic after the host has acquired an IP address when it's renewing the DHCP lease.
In this example, we have a host on 192.168.1.105. We can use the filter in Wireshark to see if there's any DHCP traffic from this IP address. In Wireshark, type ip.addr==192.168.1.105 && udp.port==67 in the filter box. In this case, we find there is DHCP traffic, so we scroll down in the tree view to see if there's a host name in the traffic. Luckily, there is:
You could also check NBNS traffic (NBNS = NetBIOS Name Service), because Windows (and sometimes other) hosts will register their hosts through NBNS after they connect to the network. In Wireshark, type ip.addr==192.168.1.105 && nbns in the filter box, and scroll through the NBNS traffic until you find the NBNS registration traffic, as seen below:
You could also find a Windows host name by using ip.addr==192.168.1.105 && netbios or ip.addr==192.168.1.105 && smb if there is no DHCP or NBNS traffic.
At this point, we have a MAC address (00:1b:21:ca:fe:d7), and IP address (192.168.1.105), and Wizzard-PC as a host name. Sometimes, the host name is based on the person's first or last names. Some organizations have a naming scheme that makes it easy to identify the user when you've found the host name. In this case, we're not so lucky.
USER NAME
If your network uses Kerberos as an authentication method for some of its servers, you might find a username by using kerberos in the Wireshark filter and doing a string search on Client Name. LDAP traffic is another source that may provide a username. If you can't find any type of authentication traffic for a username, then you could search through the HTTP traffic and see if the user has signed into any web sites. Hopefully, the user name is close to the user's real name.
If the user visits their Yahoo webmail, you're in luck, because Yahoo webmail traffic is normally unencrypted. Signing in to the webpage is encrypted through HTTPS, but after you're signed in, it's regular HTTP traffic by default. In the example for this blog entry, I used a throw-away Yahoo email account, and signed into Yahoo webmail. Looking at a pcap of the traffic, you can filter on http.host contains mail.yahoo.com and see the all the unencrypted HTTP after logging in:
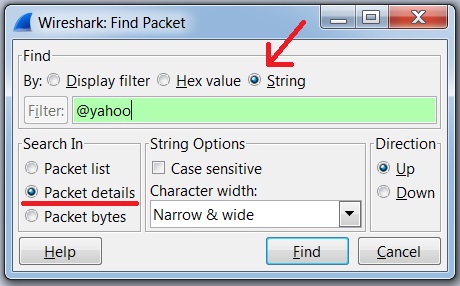
If the user is in Yahoo webmail, we can search the pcap for @yahoo and maybe find an email address. From Wireshark's Edit menu, select Find Packet as shown below:
In the window that pops up, do a string search in the packet details for @yahoo as seen in this example:
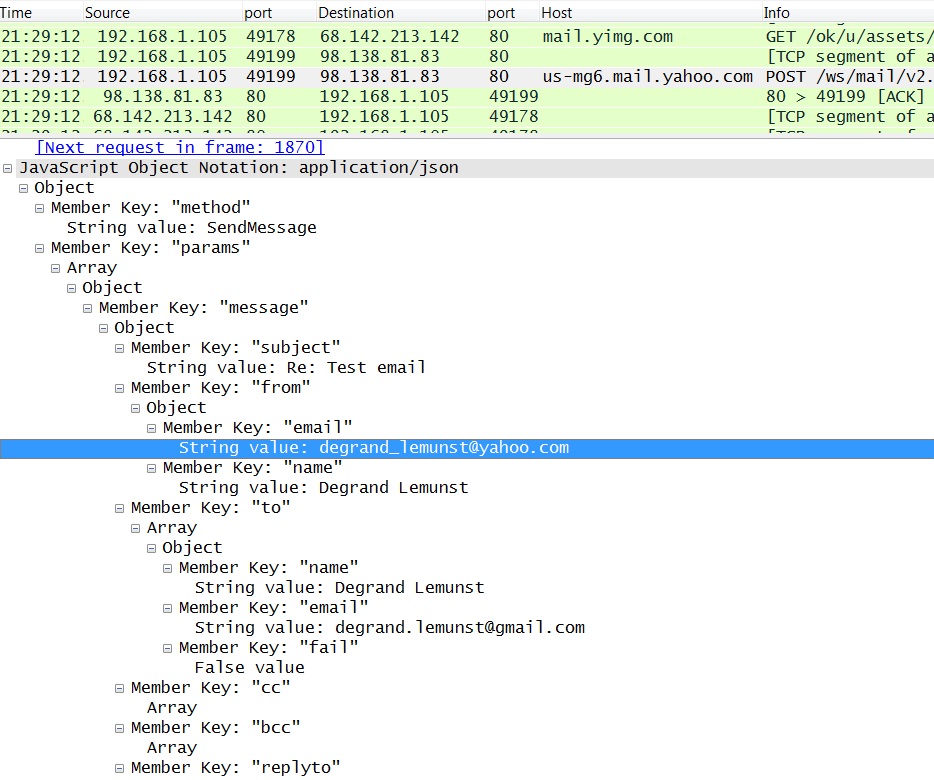
You might also try it again using "Packet bytes" instead of "Packet details". I normally search through both. While logged into Yahoo webmail, I sent a letter from my throwaway Yahoo account to another throwaway account. Because this was unencrypted, my search finds an email sent by degrand_lemunst@yahoo.com as shown below:
Once you have a possible username, you can search to see if it pops up anywhere else in the traffic. Searching for email addresses like this is not a full-proof method--it's one of many ways to searching through traffic and find some clues on who the user is.
FINAL NOTES
This was a general overview on how I occasionally search through traffic to find a host name or user name. In many work environments, there are additional ways to track hosts and users. Active Directory and other types of logs make the process much quicker. An enterprise-level anti-virus solution will also track hosts.
However, analysts can (and probably should) use network traffic to verify any host names or users when investigating suspicious activity.