2013-10-24 - ANOTHER MALICIOUS EMAIL
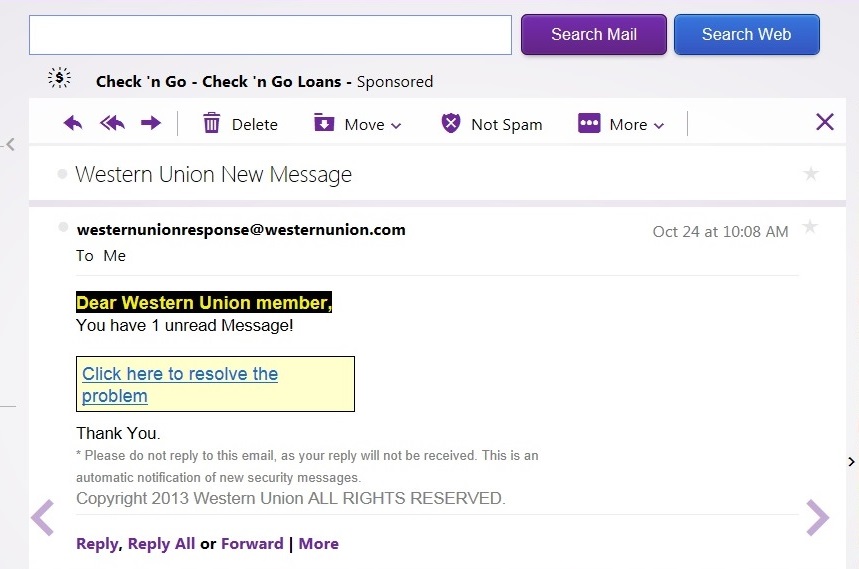
On Thursday 2013-10-24, a malicious email was sent to one of my Yahoo email addresses. It was a fake Western Union message.
A CLOSER LOOK
Normally, I just delete these; however, I wanted to look at another malicious email for this blog... Let's find the email headers, as shown below.
This gives us header information, which I'll copy and paste into a text file to examine more closely.
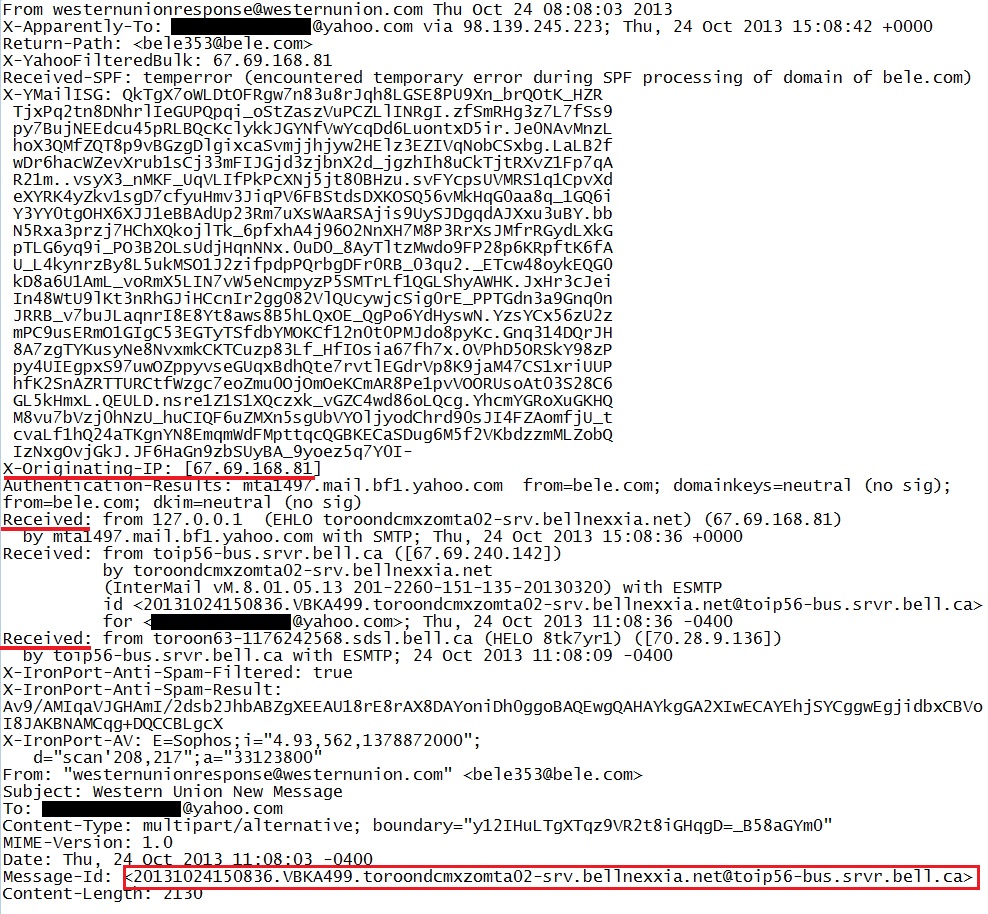
Based on the full header information shown below, the email came to the Yahoo mail servers from toroondcmxzomta02-srv.bellnexxia[.]net at 67.69.168[.]81. That much is fairly certain. However, if you look at the message ID header and the "Received:" lines, it looks like the message originated fromtoroon63-1176242568.sdsl.bell[.]ca at 70.28.9[.]136 which is a Canadian IP address. Either way, it's not from Western Union.
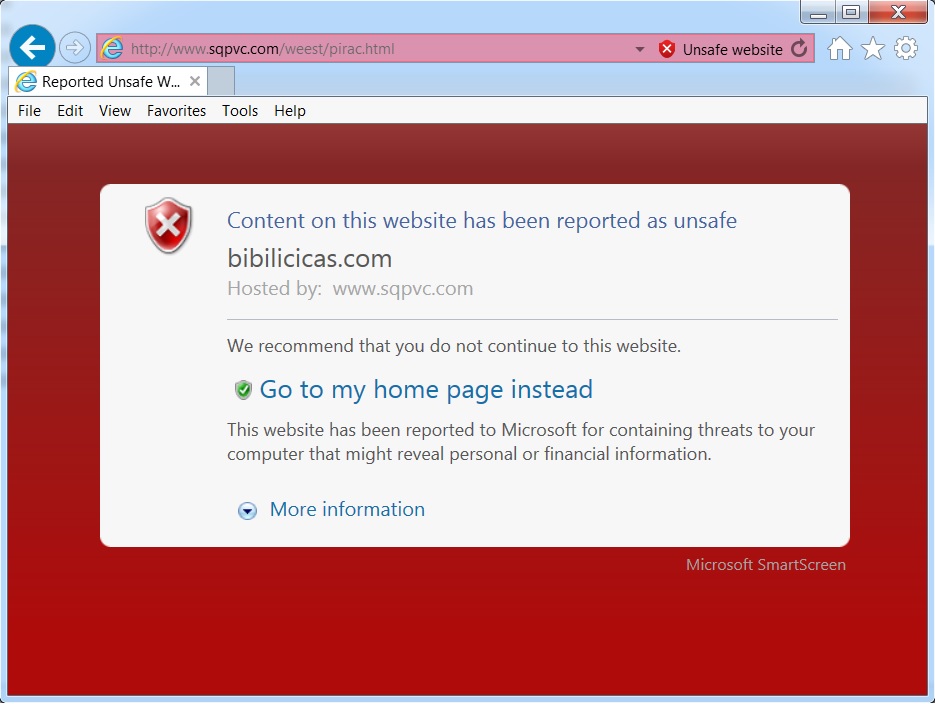
Hovering the mouse over the link for "Click here to resolve the problem" shows the following URL: hxxp[:]//www.sqpvc[.]com/weest/pirac.html. If we put this URL in a browser on a vulnerable VM, we get a warning screen stating bibilicicas[.]com has been reported as unsafe.
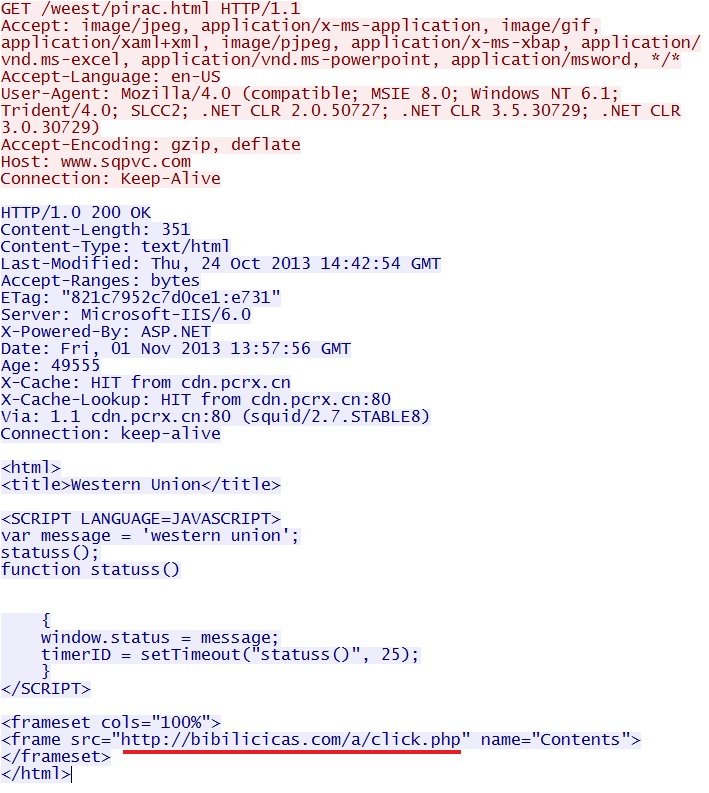
Why do we get that message? Because a URL for bibilicicas[.]com/a/click.php is embedded within an iframe in the HTML for that web page, as shown below:
Here's the traffic that's generated when you run the link in a web browser that doesn't have any protective settings enabled:
- 58.177.114[.]165 port 80 ( www.sqpvc[.]com ) - GET /weest/pirac.html
- 208.91.197[.]241 port 80 ( bibilicicas[.]com ) - GET /a/click.php
- 208.91.197[.]241 port 80 ( bibilicicas[.]com ) - GET /?fp=0kcjDNn[long string of characters]
- 107.14.36[.]17 port 80 ( i4.cdn-image[.]com ) - GET /__media__/js/min.js?v1.6
- 107.14.36[.]17 port 80 ( i4.cdn-image[.]com ) - GET /__media__/images/1316_biz-directi-3.jpg
- 107.14.36[.]139 port 80 ( i2.cdn-image[.]com ) - GET /__media__/pics/471/right-sidebar-bg.jpg
- 107.14.36[.]139 port 80 ( i2.cdn-image[.]com ) - GET /__media__/images/1314_biz-directi-1.jpg
- 107.14.36[.]17 port 80 ( i4.cdn-image[.]com ) - GET /__media__/pics/471/green-bg.gif
- 107.14.36[.]129 port 80 ( i3.cdn-image[.]com ) - GET /__media__/images/1315_biz-directi-2.jpg
- 107.14.36[.]129 port 80 ( i3.cdn-image[.]com ) - GET /__media__/images/1317_biz-directi-4.jpg
- 107.14.36[.]139 port 80 ( i2.cdn-image[.]com ) - GET /__media__/pics/471/gray-dot.gif
- 74.125.225[.]238 port 80 ( www.google-analytics[.]com ) - GET /ga.js
- 107.14.36[.]129 port 80 ( i3.cdn-image[.]com ) - GET /__media__/pics/471/left-sidebar-bg.jpg
- 58.177.114[.]165 port 80 ( www.sqpvc[.]com ) - GET /favicon.ico
The domain sqpvc[.]com was created on 2011-02-28 and is registered to a Chinese organization, with a POC email contact ending in 163[.]com. Emails using 163[.]com have been associated with actors related to China cyber espionage, as noted most recently in Mandiant's APT1 report.
The domain bibilicicas[.]com was created on 2013-10-05 less than 3 weeks before this email. The registrant is supposedly a person named Lyne Tremblay from Canada.
Monitoring the traffic with Security Onion, I got the following two alerts:
- ET CNC Zeus Tracker Reported CnC Server UDP (group 11)
- ET CNC Zeus Tracker Reported CnC Server UDP (group 12)
As seen below, these alerts both triggered on 208.91.197[.]241, which is the IP address bibilicicas[.]com is using. I think there's some overlap in the list of IP addresses, so this should probably only be one signature, not two.
alert udp $HOME_NET any -> [199.79.63[.]102,2.133.128[.]98,202.29.230[.]198,203.170.193[.]23,204.188.238[.]141,204.188.238[.]142,204.93.211[.]115,208.117.43[.]74,
208.73.211[.]28,208.84.134[.]132,208.91.197[.]241] any (msg:"ET CNC Zeus Tracker Reported CnC Server UDP (group 11)"; reference:url,doc.emergingthreats[.]net/bin/view/Main/BotCC; reference:url,zeustracker.abuse[.]ch; threshold: type limit, track by_src, seconds 3600, count 1; classtype:trojan-activity; flowbits:set,ET.Evil; flowbits:set,ET.BotccIP; sid:2404171; rev:3259;)
alert tcp $HOME_NET any -> [208.84.134[.]132,208.91.197[.]241,208.91.198[.]194,209.59.216[.]46,210.211.108[.]215,212.225.213[.]253,213.57.77[.]220,216.107.154[.]205,
216.176.100[.]240,216.215.112[.]149,31.148.219[.]85] any (msg:"ET CNC Zeus Tracker Reported CnC Server TCP (group 12)"; flags:S; reference:url,doc.emergingthreats[.]net/bin/view/Main/BotCC; reference:url,zeustracker.abuse[.]ch; threshold: type limit, track by_src, seconds 3600, count 1; classtype:trojan-activity; flowbits:set,ET.Evil; flowbits:set,ET.BotccIP; sid:2404172; rev:3259;)
These signatures trigger on IP addresses related to command and control (CnC) servers for Zues-infected hosts, which is for computers that are already infected and calling back to a CnC server. In this case, these alerts are a false positive, because we're looking at HTTP traffic that was generated when purposefully viewing a website.
FINAL NOTES
I couldn't find anything actully harmful in the link, although the traffic is extremely suspicious. My previous examination of a malicious email in July 2013 revealed some actual malware, but not so in this case.
Click here to return to the main page.