2014-01-02 - NEUTRINO EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TRAFFIC
ASSOCIATED DOMAINS:
- 67.225.214[.]94 - help.wugnet[.]com - Compromised web site
- 151.248.0[.]195 - mychicagohardwoodflooring[.]com - Redirect domain
- 212.83.191[.]176 - yaingeiy.aktinate[.]com - Nuetrino EK domain over port 8000
HTTP REQUESTS:
- 2014-01-02 22:55:49 UTC - help.wugnet[.]com - GET /office/delete-email-address-history-Outlook-ftopict977859.html
- 2014-01-02 22:55:49 UTC - 686dkfe4k74v8nu1adebdm7.mychicagohardwoodflooring[.]com - GET /index.php?f=[base64 string]
- 2014-01-02 22:55:51 UTC - 686dkfe4k74v8nu1adebdm753605381e72f85acfc63dadc05f1098ee.mychicagohardwoodflooring[.]com GET /index2.php
- 2014-01-02 22:55:52 UTC - yaingeiy.aktinate[.]com:8000 - GET /epuyq?tkimmjxilk=3410575
- 2014-01-02 22:55:53 UTC - yaingeiy.aktinate[.]com:8000 - GET /iixdorl
- 2014-01-02 22:55:54 UTC - yaingeiy.aktinate[.]com:8000 - GET /awc4kqo779pmy67a?wkfe4e2d=lv435&g7y1yz2b=r99&3qre8=jyxadlij&q3vsej9=fqa&84yc9=5vt&d3ddq=mddx6&oh7a=uea
- 2014-01-02 22:55:54 UTC - yaingeiy.aktinate[.]com:8000 - GET /a0nkzfy?h3icayg=a80cbs3&1qep34=tahzt7wn&8sbyrb=2d6cm7z&yg8fnqmnwo=aapa&oq2rr1a2=j22g
- 2014-01-02 22:55:54 UTC - yaingeiy.aktinate[.]com:8000 - GET /au2prjn9do?bmbfxpdtn7=o4wn4a9&wb9=v6xz&pdvv=lu8x63t
- 2014-01-02 22:55:54 UTC - yaingeiy.aktinate[.]com:8000 - POST /a5pbh7fqw0t
- 2014-01-02 22:55:54 UTC - yaingeiy.aktinate[.]com:8000 - POST /aox571g15dvr4001
- 2014-01-02 22:56:00 UTC - yaingeiy.aktinate[.]com:8000 - GET /al7w6yydrqhw7cn7?391=fjw1f&q7lo=za7&e3vq87ig=spb&ur62=zudn5yjjo5&i6m=5mq&nf7=lolg5z743s&04b=stvkn&qasrc=2mz
- 2014-01-02 22:56:00 UTC - yaingeiy.aktinate[.]com:8000 - GET /anffplgj1mkmk?3300=e2nyjd&3lx6mory3d=12u98px39k&xjm3p=i5wkbe&8paido99=ai0qx
- 2014-01-02 22:56:00 UTC - yaingeiy.aktinate[.]com:8000 - GET /avykvz483vt?3yp1=4feowf9&q6iq=mnjs290bbh&6sr=dri7c1bppy&7w0lp0iqh3=p7zza
- 2014-01-02 22:56:00 UTC - yaingeiy.aktinate[.]com:8000 - GET /ai1sh7uysd102?1a61=4b5z&7iyo7kmc=s4wsqyly&q6s=obbfw7im3&u9v6=lmc&r6bgjhewt=3whe1b&e87h=enrv9&dkyzrfy=irstoo
- 2014-01-02 22:56:00 UTC - yaingeiy.aktinate[.]com:8000 - POST /kvvzfuigyz
- 2014-01-02 22:56:00 UTC - yaingeiy.aktinate[.]com:8000 - GET /a2el04rtsc7abg5?qteaei=9p5iw2&6pon=p7x&7en=v4kfs&wgn1=juv&3cmw=i7mvx
- 2014-01-02 22:56:04 UTC - yaingeiy.aktinate[.]com:8000 - GET /fuuinwhzeew?zyxjzmwdfsu=jnorme
- 2014-01-02 22:56:05 UTC - yaingeiy.aktinate[.]com:8000 - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
- 2014-01-02 22:56:05 UTC - yaingeiy.aktinate[.]com:8000 - GET /hlwivhlwnb?zhkeerdiwz=jnorme
ARTIFACTS FROM EK DOMAIN IN THE PCAP:
MALWARE:
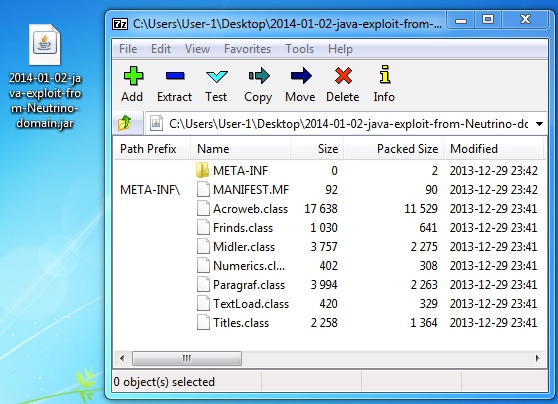
- Java exploit - 61888d05a5939f0ece034df87f64f1f7
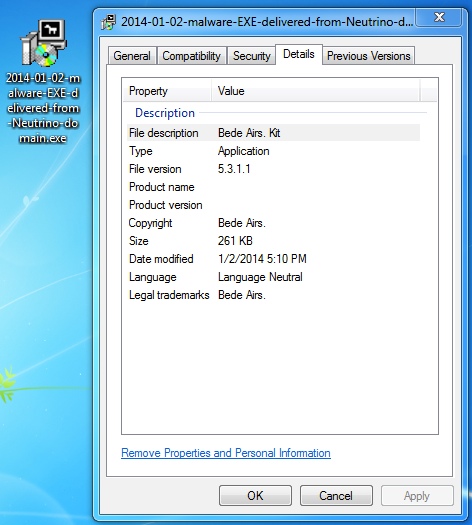
- EXE payload - f64ac300cab2bfe2f3a3f34c09ff1cbd
Click here to return to the main page.