2014-01-20 - ANOTHER STYX EK EXAMPLE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
Here's a quick post for the pcap and malware on a Styx EK infection, very similar to the traffic I covered on 2013-12-27.
TRAFFIC
The original referer was the result of a Google search:
- 15:44:18 UTC - 184.168.172[.]1:80 - www.nuisancecalls[.]org[.]uk - GET /showthread.php?22477-01933441081-Read-this-if-had-calls-from-01933441081
- 15:44:19 UTC - HTTP/1.1 302 Moved Temporarily
A series of redirects:
- 15:44:19 UTC - 93.170.131[.]2:80 - gqillqigqilqigqiqlqiigqilqiiiqgg.esmtp[.]biz - GET /1.php
- 15:44:19 UTC - HTTP/1.1 302 Found
- 15:44:20 UTC - 93.170.131[.]2:80 - gqgqgqgql1iqli1lil1qgiql.ocry[.]com - GET /i1gqgqilil1/all4.php
- 15:44:20 UTC - HTTP/1.1 302 Found
- 15:44:20 UTC - 50.63.75[.]1:80 - jogaming[.]com - GET /templates/beez/1.php?uid=11860
- 15:44:21 UTC - HTTP/1.1 302 Moved Temporarily
- 15:44:21 UTC - 188.116.34[.]246:80 - www3.vhreqzbb9so750.4pu[.]com - GET /?g0r5z0=i6DbmbdjnN3bya6rk5pvo5WjqG2UYpip7pyzm6PGp92SmnKrn5pZ&f93f6c56=%08%04%02%05%08%09%02%08%04
- 15:44:22 UTC - HTTP/1.1 302 Moved Temporarily
Goes to a landing page:
- 15:44:22 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /xkfd8mp?y7t45=[[base64 string
- 15:44:22 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /20b363d.js
- 15:44:22 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /pictures/fl.swf
- 15:44:23 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - POST /
- 15:44:23 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /f434312.js
- 15:44:23 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /i.html
- 15:44:26 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /VYqFiT.html
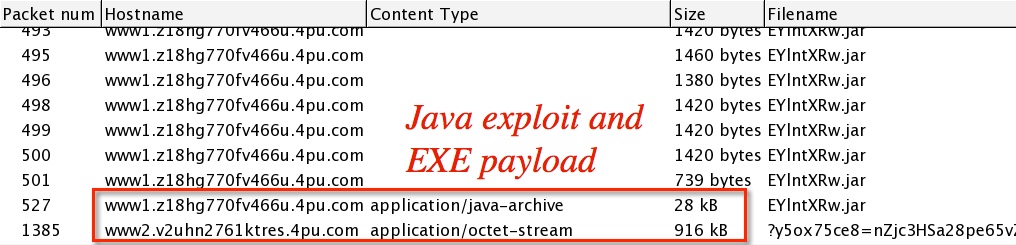
After various HTTP GET requests for images from www1.z18hg770fv466u.4pu[.]com, the exploit traffic folows:
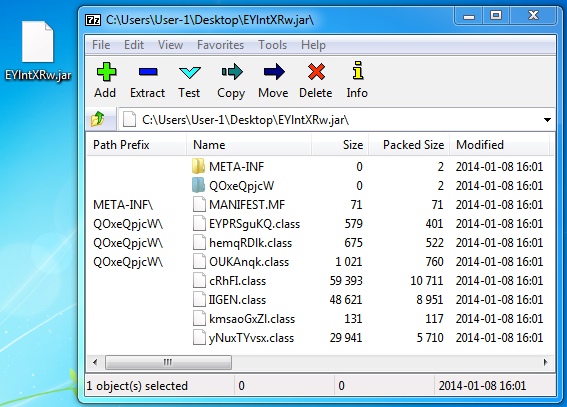
- 15:44:29 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /EYlntXRw.jar
- 15:44:30 UTC - 188.116.34[.]246:80 - www1.z18hg770fv466u.4pu[.]com - GET /EYlntXRw.jar
- 15:44:30 UTC - 188.116.34[.]246:80 - www2.v2uhn2761ktres.4pu[.]com - GET /?y5ox75ce8=[base64 string&h=16
MALWARE
File name: EYlntXRw.jar
File size:&bnsp; 28,515 bytes
MD5 hash: 89e470fcc466d648c205a91daac17aa8
VirusTotal link: https://www.virustotal.com/en/file/79c63c54ba9e911a808a72ea418e079932029eb48c199b183471fbfcbfe0904b/analysis/
Detection ratio: 4 / 49
First submission: 2014-01-20 23:33:20 UTC
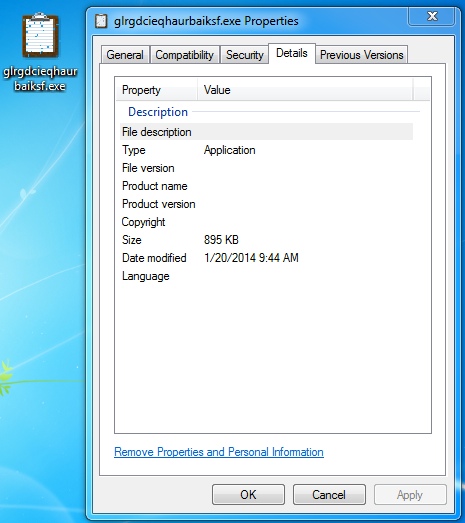
File name: glrgdcieqhaurbaiksf.exe
File size:&bnsp; 916,480 bytes
MD5 hash: 956ca1c210e24c6168a84ea2733f7508
VirusTotal link: https://www.virustotal.com/en/file/da365d911bed34e66c5335ad1413e4f0b4cfd1d244e0fd03331359b77aeef1ad/analysis/
Detection ratio: 17 / 48
First submission: 2014-01-20 23:33:31 UTC
Click here to return to the main page.