2014-01-21 - ANOTHER NEUTRINO EK EXAMPLE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
A quick post on traffic for a VM infected through Neutrino EK...
ALERTS
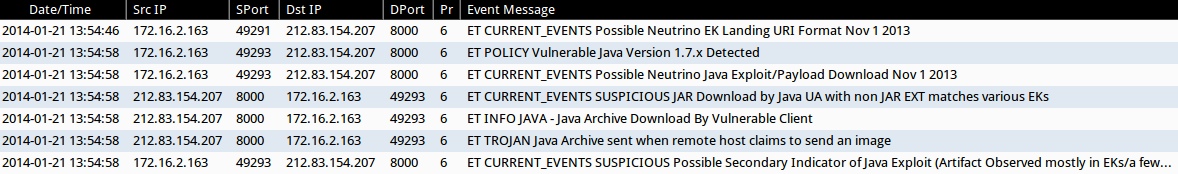
- ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS Possible Neutrino Java Exploit/Payload Download Nov 1 2013
- ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET TROJAN Java Archive sent when remote host claims to send an image
- ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps)
TRAFFIC
ASSOCIATED DOMAINS:
- www.exchangefreaks[.]com - infected website
- blueblack[.]com[.]tr - redirect domain
- iepheiph.bandrets[.]com - Neutrino EK domain
INFECTION CHAIN:
- 07:54:42 - 67.227.181[.]150 - www.exchangefreaks[.]com - GET /Delete-periodically-t142049.html
- 07:54:43 - 31.41.217[.]3 - a7euhl1i6c1ev2e1mrw13xg.blueblack[.]com[.]tr - GET /index.php?l=cXR6anhuPWR2cXhtaCZ0aW[long string of characters]
- 07:54:45 - 31.41.217[.]3 - a7euhl1i6c1ev2e1mrw13xg52265384c9da87b525c344c8704cd096a.blueblack[.]com[.]tr - GET /index2.php
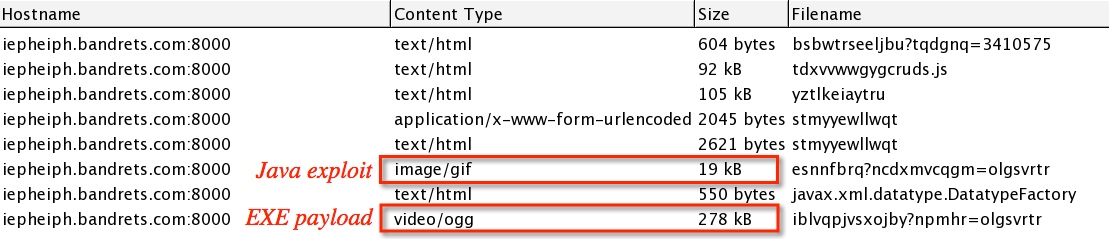
- 07:54:47 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - GET /bsbwtrseeljbu?tqdgnq=3410575
- 07:54:47 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - GET /tdxvvwwgygcruds.js
- 07:54:47 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - GET /yztlkeiaytru
- 07:54:50 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - POST /stmyyewllwqt
- 07:54:58 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - GET /esnnfbrq?ncdxmvcqgm=olgsvrtr
- 07:54:58 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
- 07:54:59 - 212.83.154[.]207 - iepheiph.bandrets[.]com:8000 - GET /iblvqpjvsxojby?npmhr=olgsvrtr
PRELIMINARY MALWARE ANALYSIS
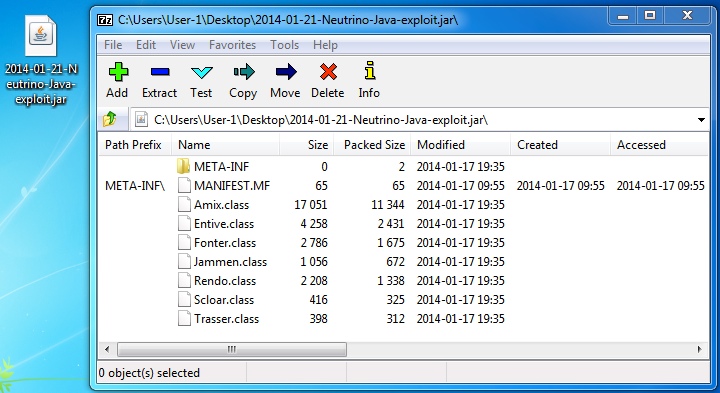
Java exploit from 212.83.154[.]207 port 8000 (iepheiph.bandrets[.]com):
https://www.virustotal.com/en/file/2a5ef17ea9eb2f29b14fc69086b5d7bc2425942ad0cdb83536e9cf6ab3f448f6/analysis/
File name: 2014-01-21-Neutrino-Java-exploit.jar File size: 19,264 bytes
MD5 hash: 37c2eb4f18306ecbec6c8035195684ea
Detection ratio: 4 / 50
First submitted: 2014-01-20 00:32:58 GMT
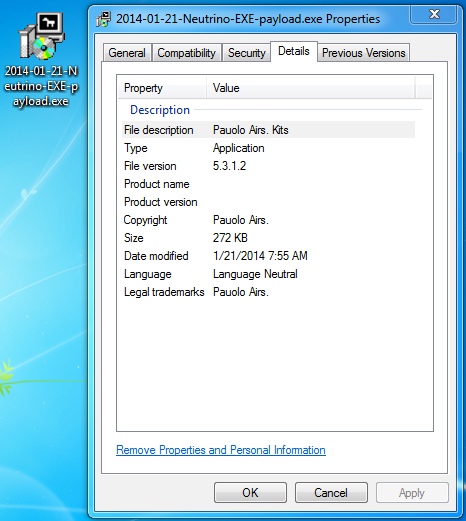
EXE payload from 212.83.154[.]207 port 8000 (iepheiph.bandrets[.]com):
https://www.virustotal.com/en/file/c5e42cba7d55770a96aae6d723f28b794736e7bb5513f133a322084ee540c76c/analysis/
File name: 2014-01-21-Neutrino-EXE-payload.exe File size: 278,729 bytes
MD5 hash: b34aa8ffa78b4b5adbd63cf8143fc93b
Detection ratio: 15 / 50
First submitted: 2014-01-21 14:41:38 GMT
Click here to return to the main page.