2014-02-01 - BIZCN GATE ACTOR FIESTA EK USES CVE-2013-0074 (SILVERLIGHT EXPLOIT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-02-01-Fiesta-EK-traffic.pcap.zip
- 2014-02-01-Fiesta-EK-malware.zip (Silverlight exploit and EXE payload)
UPDATE:
- In April 2015, I started calling the actor behind this campaign the "BizCN gate actor" for reasons described here.
- This blog post's title has been updated to reflect the newer info.
DETAILS
ALERTS ON 2014-02-01
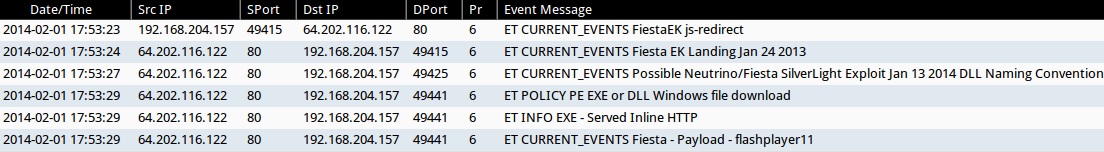
- 17:53:23 UTC - 64.202.116[.]122:80 - ET CURRENT_EVENTS FiestaEK js-redirect
- 17:53:24 UTC - 64.202.116[.]122:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 17:53:27 UTC - 64.202.116[.]122:80 - ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit Jan 13 2014 DLL Naming Convention
- 17:53:29 UTC - 64.202.116[.]122:80 - ET POLICY PE EXE or DLL Windows file download
- 17:53:29 UTC - 64.202.116[.]122:80 - ET INFO EXE - Served Inline HTTP
- 17:53:29 UTC - 64.202.116[.]122:80 - ET CURRENT_EVENTS Fiesta - Payload - flashplayer11
ASSOCIATED DOMAINS
- 69.167.155[.]134 - www.excelforum[.]com - Compromised website
- 190.123.47[.]198 - valeriesn[.]com - Redirect domain
- 64.202.116[.]122 - utrust[.]in[.]ua - Fiesta EK domain
- 217.23.3[.]113 - no domain name - Post infection malware callback IP (Netherlands, Worldstream)
INFECTION CHAIN OF EVENTS
- 17:53:21 UTC - 69.167.155[.]134 - www.excelforum[.]com - GET /excel-programming-vba-macros/
- 17:53:23 UTC - 190.123.47[.]198 - valeriesn[.]com - GET /fmoilzp.js?e177721626572749
- 17:53:23 UTC - 64.202.116[.]122 - utrust[.]in[.]ua - GET /isj60tz/?3
- 17:53:27 UTC - 64.202.116[.]122 - utrust[.]in[.]ua - GET /isj60tz/?267c7f3cc1f7d39e5b535b58045d005202070258030403580704520704525256
- 17:53:27 UTC - 64.202.116[.]122 - utrust[.]in[.]ua - GET /isj60tz/?11aafa7410845021425d175a555a04050100545a5203070f0403040555555601;5061118
- 17:53:29 UTC - 64.202.116[.]122 - utrust[.]in[.]ua - GET /isj60tz/?75be7ff74e73bd92524d075e045d55060704575e0304560c0207070104520702;1;6
- 17:53:29 UTC - 64.202.116[.]122 - utrust[.]in[.]ua - GET /isj60tz/?75be7ff74e73bd92524d075e045d55060704575e0304560c0207070104520702;1;6;1
- 17:53:32 UTC - 217.23.3[.]113 - no domain name - POST /
PRELIMINARY MALWARE ANALYSIS
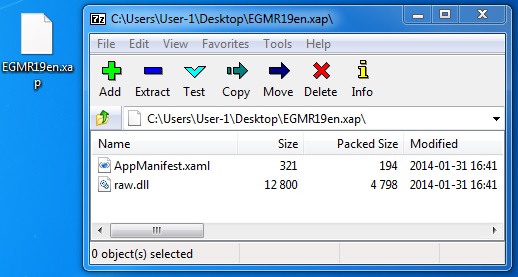
File name: EGMR19en.xap
File size: 5,212 bytes
MD5 hash: f3a69e3db600df458fc9b897697b1657
Virus Total link: https://www.virustotal.com/en/file/0c4de8b76633caaf571bef1e72eb4310847f0f95d7dd12dec7997061ab25aa27/analysis/
Detection ratio: 1 / 50
First submitted: 2014-02-01 23:50:38 UTC
NOTE: Identified by F-Secure as CVE-2013-0074
- https://www.cve.org/CVERecord?id=CVE-2013-0074
- https://malware.dontneedcoffee.com/2013/11/cve-2013-0074-silverlight-integrates.html
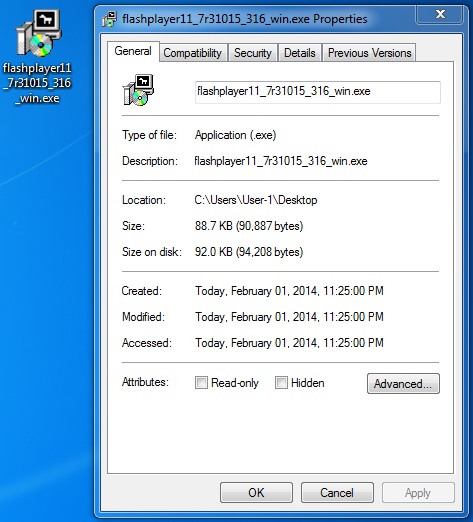
File name: flashplayer11_7r31015_316_win.exe
File size: 90,887 bytes
MD5 hash: 590fbb20aaf46e1242dd642fc49cb117
Virus Total link: https://www.virustotal.com/en/file/8d701cde9ba5734590c1932ab8b3394007b5a18d6acdf8d190267340e960cd90/analysis/
Detection ratio: 13 / 50
First submitted: 2014-02-01 16:02:41 UTC
Click here to return to the main page.